We continue the “Deep Dive” series. In it you might find the answers to some of your technical questions. The industry experts will provide their insights on several topics and research some new features of most popular applications. Don’t miss out on the article about Administrative Audit Logging. The first article of the series can be found here. Also, read more about Exchange 2013 CAS configuration (Part 1, Part 2) and using PowerShell for RBAC permission customization! You are welcome for comments and discussion!
Mailbox auditing is a very interesting feature of Exchange 2013 and it is one of the most important components of Exchange organization. Mailboxes may contain information which may be sensitive, personal, business or critical. Many of us, including me, do not have mailbox auditing enabled on our mailboxes in the organization. Often there is a need to investigate what action had taken place on the mailbox but there may be no logs. To avoid this kind of situation, we need to enable auditing needs on the required mailbox or on the set of mailboxes.
The need to perform mailbox auditing may vary depending on several situations. However, some of those instances have been described below:
- Your VIP/Execute Mailbox was hacked and some crucial information has leaked out. It is important to determine who has accessed your mailbox and what action has been taken.
- You have multiple delegates on the VIP mailbox, and if some messages had been deleted, and there is an investigation on which delegate deleted the messages.
- If there is a group mailbox, and many people have access to the group mailbox, and in case someone has deleted the folder, and there is an enquiry as to check on who could have deleted it.
- It can also be a regulatory, compliance, and litigation requirements
Mailbox Audit logging has 3 levels:
- AuditOwner – Information about operations performed by the mailbox owner.
- AuditDelegate – Information about operations performed by other recipients/delegates for a specific mailbox, which includes : Update, SoftDelete, HardDelete, SendAs, Create
- AuditAdmin – Information about operations performed by the administrator for a specific mailbox, which includes : Update, Move, MoveToDeletedItems, SoftDelete, HardDelete, FolderBind, SendAs, SendOnBehalf, Create
Remember that by default, the Mailbox audit is not enabled and therefore, it needs to be enabled. Once enabled, Mailbox audit logs are generated for each mailbox and stored in the recoverable Items folder, in the Audits subfolder. Logs are retained even if you move the mailbox to the different DB on the same server or different server
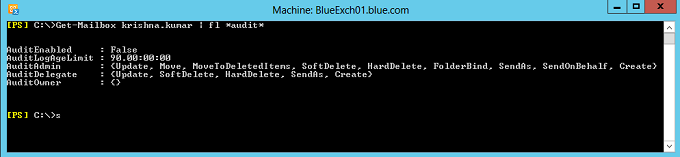
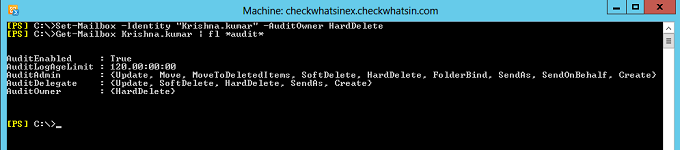
Below is the command which lets you verify the audit enabled mailbox properties
Get-Mailbox Krishna.kumar | fl *audit*
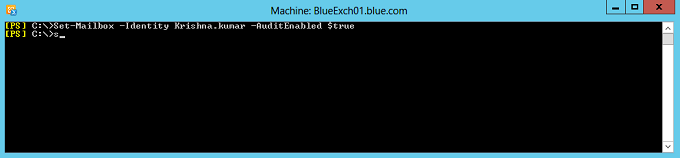
Mailbox auditing can be enabled using the cmdlet set-mailbox with the parameter AuditEnabled as $true.
Set-Mailbox –Identity Krishna.kumar –AuditEnabled $true
Auditing on every user mailbox in the exchange organization can be enabled by using the below PowerShell command.
$UserMailboxes = Get-Mailbox -Filter {(RecipientTypeDetails -eq ‘UserMailbox’)}
$UserMailboxes | Set-Mailbox -AuditEnabled $True
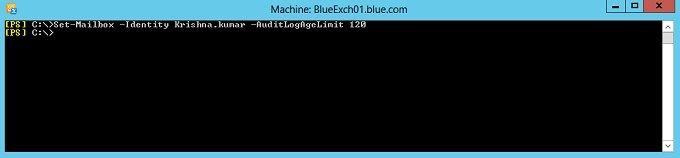
By default, logs are retained at the mailbox for 90 days and this retention period can be modified using the cmdlets set-mailbox with parameter AuditLogAgeLimit.
Set-mailbox –identity Krishna.Kumar –AuditlogAgelimit 120
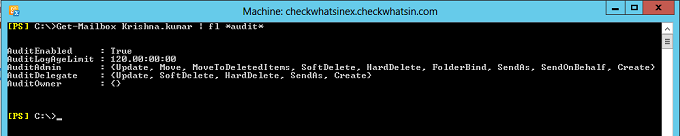
Auditing of mailbox owner actions can generate a large number of mailbox audit log entries and is therefore disabled by default. Below snap has the default logging settings for AuditAdmin, AuditDelegate and AuditOwner. AuditOwner logging is set to blank by default.
It is recommended to enable auditing only for the specific owner actions which are needed to meet the business or security requirements. Below is the PowerShell command to audit “HardDelete” for Auditowner. Below snap is the execution and verification of the same.
Set-Mailbox -Identity “Krishna.kumar” -AuditOwner HardDelete
Mailbox Audits are logged for the following mailbox actions:
- Copy of the items/messages to another folder.
- Any message sent or received.
- Mailbox folder access.
- Soft delete and hard delete of email items
- Moving of email from one folder to another or deleted items folder.
- Message is sent using send AS or Send on Behalf permission.
- Changes on Items properties.
Mailbox audit log data is stored in a folder named Audits under the ‘Recoverable Items’ folder of the mailbox, so it is hidden from the user. Once auditing is enabled, you can perform search synchronously on the single mailbox or asynchronously searchon multiple mailboxes at a time. Search can be performed using the PowerShell or using Exchange Admin Central (EAC).
Auditing mailbox audit logs using PowerShell
- Below PowerShell command allows to search all the logs for Admin and Delegate between the specified time period
Search-MailboxAuditLog -Identity Krishna.Kumar -LogonTypes Admin,Delegate -StartDate 4/1/2014 -EndDate 4/30/2014 -ResultSize 4000
- Below PowerShell command allows to search the “SendAS” email logs for Admin and Delegate on the mailbox krishna.kumar and Rajesh.kumar.
Search-MailboxAuditLog -Identity Krishna.kumar,rajesh.kumar -LogonTypes Admin,Delegate -ShowDetails -StartDate 4/1/2012 -EndDate 4/1/2014 | Where-Object {$_.Operation -eq “sendas”}
- Below is the PowerShell command that allows to search Hard Delete logs for the owners
Search-MailboxAuditLog -Identity Krishna.kumar -LogonTypes Owner -ShowDetails -StartDate 4/1/2014 -EndDate 3/1/2012 | Where-Object {$_.Operation -eq “HardDelete”}
Auditing Mailbox logs using Exchange Admin Central (EAC)
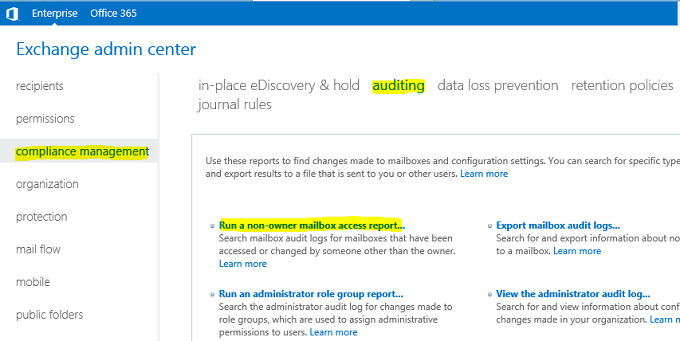
1. Login to the EAC console and then click on “Compliance Management” -> “Auditing” and then click on “Run a non-owner mailbox access report”
2. Specify the date and the mailbox to audit and click on search button.
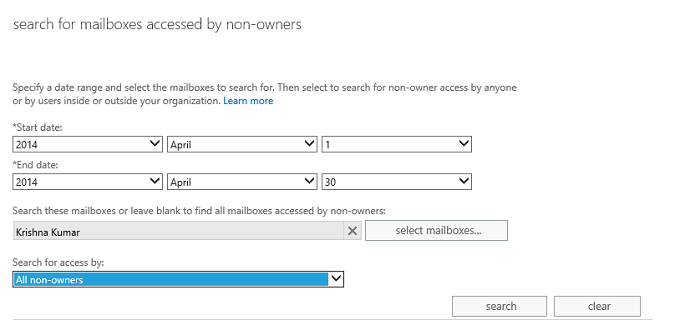
As an administrator, you now have what you need for investigating the culprit.
Hope you like this article and find the content helpful in tackling a real life situation.


