Are your employees or colleagues caught up in the Pokémon GO craze? Surely, most of them are. However, in the hunt to “catch ‘em all,” Pokémon GO users expose themselves to a variety of security risks. Moreover, playing the game presents major security risks for corporate information. In this blog post, I’ve listed potential risks that Pokémon GO players face as well as possible ways to avoid these risks while still participating in the game.
1. “Full Account Access”
The issue here is one of access. When a user wants to play Pokémon GO, he or she must create an account. Many users sign in using a corporate account, i.e. using corporate credentials. Doing so means that users, despite only intending to provide access to an email address and name, end up granting the Pokémon GO app full access to their Google account! This can be verified by looking at the permissions granted to the game upon logging in. What does this actually mean?
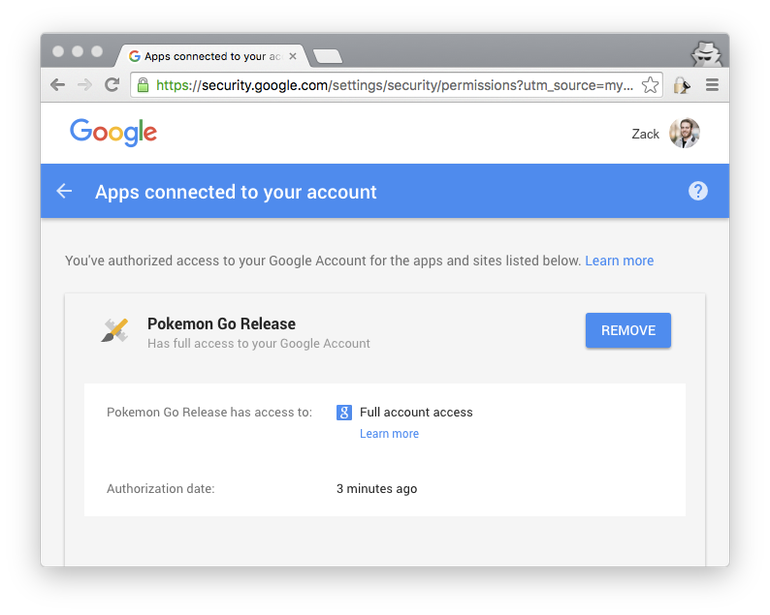
Granting “Full account access” (see the screenshot above) lets the app your emails, send emails from your account, access your Google Docs and see your photos, among many other things.
Security Tip:
Android users can edit and remove the app’s “Full account access” to their Google account by going to the permissions page (check your permissions here: https://security.google.com/settings/security/permissions). For iOS users, the situation becomes a little thornier. These users must sign in using different credentials
2. Spammy Pokémon GO Apps
Fake Pokémon GO apps are currently being heavily promoted on social media and in internet forums. It is easy to detect such fake apps because they release user information to third parties. The malicious software in these fake apps contains a script that evaluates and tracks the “victim’s” online behavior. This information is then used by advertising firms to serve highly-targeted ads to the “victim.”
Security Tip:
Only download the game from official sources, such as Apple’s App Store or Google Play.
3. Trojanized Pokémon GO App
Hackers continue to create new malicious software and seed this software into mobile apps. In a report on Trojanized apps, Kaspersky Lab writes that this malicious software lets an attacker “bypass in-app billing to get free coins for in game items or spoof GPS locations to access areas they are not physically near.” Trojanized apps may even allow attackers to remotely control a device’s camera or microphone, which, in turn, could be used to enable remote recording.
Security Tip:
CheckPoint advises running security on devices that use MDM in order to detect malware or malicious apps before they embed themselves and steal data.
Naturally, these security issues will not keep people from playing the most popular mobile game in history. Nevertheless, it is very important that companies educate their employees and that people educate their colleagues about the game’s potential risks. Remember, once you’re empowered with caution and security consciousness, you’re free to “catch ‘em all!”


