Today we are going to talk about finding “lost” files with File Server auditing. But first, how many of you are aware that users have a lot in common with a five year old?
Now, before I start getting hate mail, before folks start driving by my house and shooting at it (warning, I shoot back) or before I start getting the stink eye, let me defend what I just said. I had a ticket cross my desk today that essentially boiled down to “Where did this file go, and who moved/deleted it”. I can imagine the interrogation on that one. If I got all the users together, and used my well-honed criminal investigation tools, every user would say the same thing my children said when they broke something. All together now, and you have to say with a piercing wail: “I DIDN’T DO IT!” Does that sound familiar?
Finding the file was simple; I just set up a search for it. But it was time consuming: a search through 2.5 TBs of disk took about 12 hours. I eventually found the file, and of course it had simply been moved.
The way most folks would do it is simple: just open your server, and start a search. What you’re looking for is the name of the file. If you don’t have that, at least type in the extension and get as close as you can to what it was called, and use wildcards for the parts you don’t know. Select where you think it might be and usually, you’re going to find it in an adjacent directory. People get mouse happy and drag it over, often times without realizing it. That little tip can help you a lot because people do things by accident. And just knowing how people make mistakes can make your search easier.
But sadly there wasn’t a tool in place to answer the question of who moved it, much less where the file went. From here, short of a confession, I wasn’t going to get a conviction. You have to have file auditing and part of it is simply giving better customer service.
Now without a means to find the file, or sometimes just the inability to find it, we’re headed for the backups. We can restore the file, but now chances are we have two or more copies of the same file floating about. Do this enough, and you start eating up a few GBs. But the files represent money. Each file, no matter how simple or complex, represent X amount of man hours or work. In short, time is money, and if we can save time spent by finding the lost, latest and greatest file, isn’t it worth it?
I don’t care to audit files to nail people because they forgot how to use a mouse, though when it comes to SOX auditing (the previous articles on this topic can be found here and here), I’ve been asked about monitoring the files for deletions, moves, and so forth, what I have found is that the Netwrix Auditor for File Servers helps not only to find the guilty party, but 99% of the time is faster and easier for finding the missing file. One thing I’d better point out is that implementing Netwrix Auditor for File Servers is not retroactive. It means, that it can only deal with what happens after it’s installed.
Let’s look at the product. Like all things, you have to set it up properly. This screenshot shows a properly configured Netwrix File Server auditing tool. It has the UNC paths I want to watch, email addresses etc.
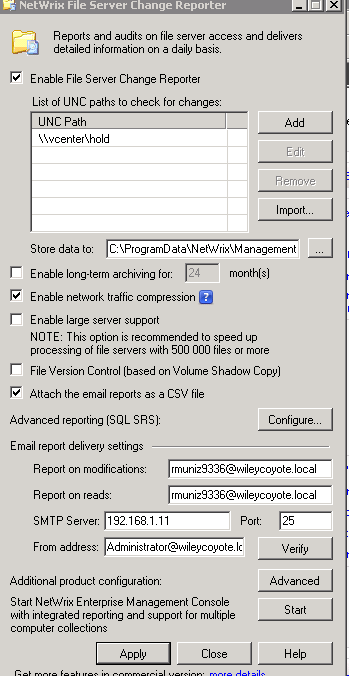
Click the image for full view
Increasingly, email servers are requiring some kind of login, and probably support encryption. If you click on the “Advanced” button, you can set those settings there. Here’s how mine is set up.
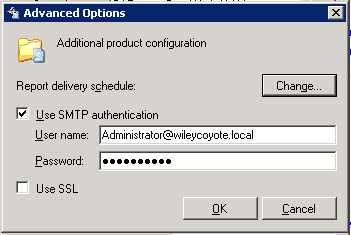
Click the image for full view
Setting up Netwrix Auditor for Files Server is almost too simple. But like all simple things, there’s a hard part to it, and that’s getting your auditing right. The troubleshooting manual is worth its weight in gold here. It tells you what you need to audit and so forth. And don’t forget to set up auditing for failures. Successes are important, failures are even more important, especially if we start talking security.
Every morning, you get a report in your email. When changes happen, there will be a zipped CSV file attached. Just open it in Excel, click Find, and type in your search parameters.
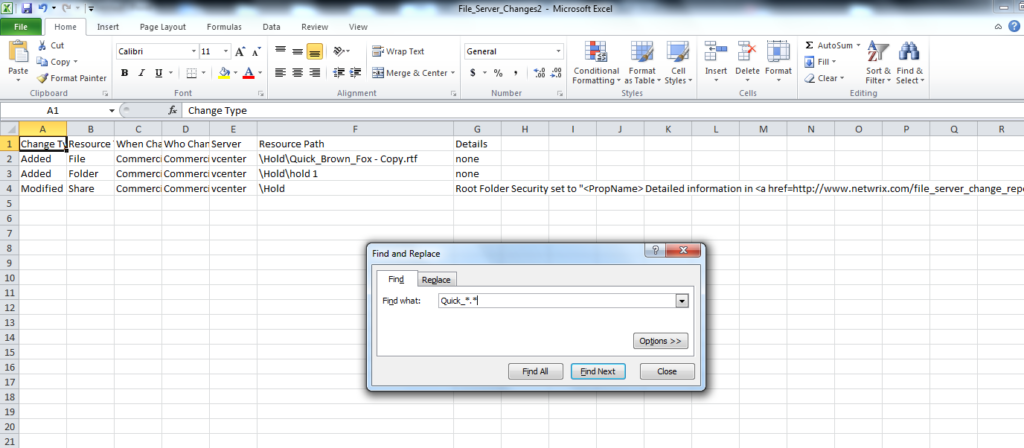
Click the image for full view
And it will find the file just fine for you. The good news is, you did it in less than 12 hours (try minutes).
Final word, since this is a file auditing tool, and SOX and HIPAA auditors can get very interested in what it has to say, make sure you save your results. I always keep my results on the File Server in a folder called Security Audits. It’s broken down by year, month, and what’s being audited. For example, Firewall logs go into a folder under the correct month and year called “Firewall”. File audit results have their own folder as does AD auditing and so forth. Remember, these are documents that can be asked for. Any gaps in the files saved might require an explanation.
And that’s how you become a rock star! And if you want to yell at the guy who “lost” it, don’t!
If you have any feedback, please, share your opinion in the comments section below!

