Accidental or malicious changes to Organizational Units (OU) and groups in Active Directory can turn into pain in the neck for IT admins. For instance, if an OU that contains “User Accounts” is deleted, users will not be able to log in. There could be multiple scenarios like that…
This how-to will show you two ways of detecting changes to OUs & groups in Active Directory and help you timely respond to unwanted ones.
Native Auditing Tool
- Run GPMC.msc (url2open.com/gpmc) -> Create a new GPO and edit it -> Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Audit Policy:
- Audit account management -> Define -> Success
- Audit directory service access -> Define -> Success.
- Return to the Security Settings level -> Event Log:
- Maximum security log size -> Define to 4gb
- Retention method for security log -> Define to Overwrite events as needed.
- Link the new GPO: Go to “Group Policy Management” -> Right-click domain or OU -> Choose Link an Existing GPO -> Choose the GPO that you created.
- Force the group policy update: In “Group Policy Management” right-click on the defined OU -> Click “Group Policy Update”.
- Open ADSI Edit (url2open.com/adsi) -> Right-click ADSI Edit -> Connect to Default naming context -> Right-click DomainDNS object with the name of your domain -> Properties -> Security (Tab) -> Advanced (Button) -> Auditing (Tab) -> Add Principal “Everyone” -> Type “Success” -> Applies to “This object and Descendant objects” -> Permissions -> Select all check boxes by clicking on “Full Control”, except the following: Full Control, List Contents, Read all properties, Read permissions -> Click “OK”.
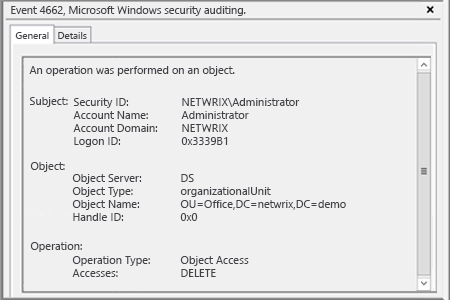
- Open Event viewer and filter Security log to find event id’s (Windows Server 2003/2008-2012):
- 4727, 4731, 4754, 4759, 4744, 4749 – Group created
- 4728, 4732, 4756, 4761, 4746, 4751 – Member added to a group
- 4729, 4733, 4757, 4762, 4747, 4752 – Member removed from a group
- 4730, 4734, 4758, 4748, 4753, 4763 – Group deleted
- 4735, 4737, 4745, 4750, 4755, 4760 – Group changed
- 4662 – An operation was performed on an object (Type: Directory Service Access).
Netwrix Auditor for AD
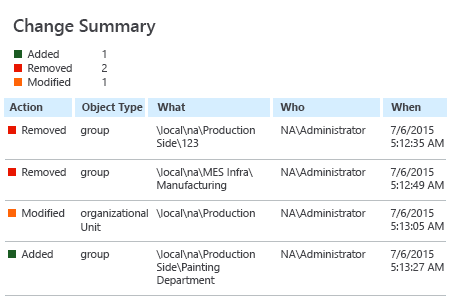
Netwrix Auditor for Active Directory can audit all changes made to groups and OUs in Active Directory and it can quickly reverse unauthorized modifications by restoring Active Directory objects.
Run Netwrix Auditor ->Click “Search” -> Choose “Advanced” -> Set up the following filters:
- Audited system = Active Directory
- Object type = Group
- Object type = Organizational Unit.
Then click “Modify” and “Search”.