In 2017,two former Miami-Dade School District students discovered that their Social Security numbers, test scores and other personal information was posted on one of the district’s public web pages. In fact, the personal information of hundreds of students was published online and was very easy to find simply by Googling their names. The two students have sued the school board and reported the incident to authorities, and now the school faces a thorough audit from U.S. Department of Education regarding its possible breach of FERPA (Family Educational Rights and Privacy Act).
In 2018, the Palo Alto Unified School District discovered that an employee was storing the names, addresses and Social Security numbers of area residents on his personal laptop. This was especially shocking because that same employee had already had a laptop with sensitive data stolen — despite that earlier incident, he had failed to change his bad habit of putting data at risk of compromise.
Notice the similarity in these two data security breaches? In both cases, insiders were involved. The insider threat is by no means limited to educational institutions, but it is more pressing there than in other industries, for several reasons. First, a high number of employees have access to sensitive information about employees and students. Second, those people are often less informed about cyber threats and therefore are more relaxed about sharing sensitive data; school employees disclose names, job roles and contact information more readily than employees in other verticals. In fact, the Verizon’s 2018 Data Breach Investigation Report found that the education sector has the second highest percentage of insider problems among surveyed industries, with personal data compromised in 72% of the incidents.
Meanwhile, the Netwrix 2018 Cloud Security: In-Depth Report found that 87% of respondents from the education sector store sensitive data in the cloud, so we decided to find out what their biggest security concerns were about the cloud and what plans they have for addressing them. We discovered that many educational entities actively using cloud-based storage share the pressing issues: mitigating the insider threat and ensuring data security.
Poor visibility puts data and systems at risk
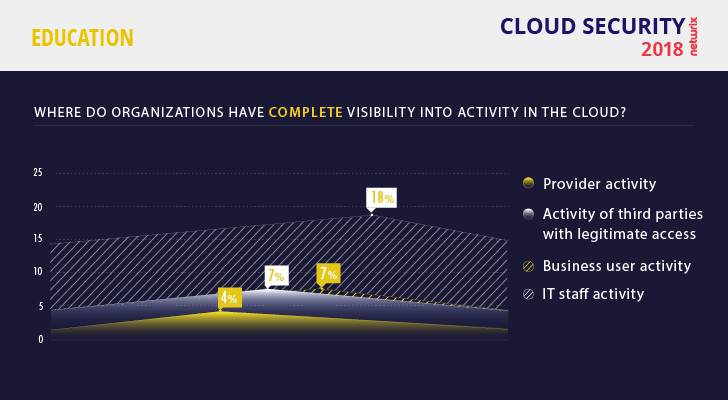
The uncertainty educational institutions have around data stored in the cloud is rooted in their low level of visibility into user activity. Among all 93 educational entities surveyed, only 18% of IT teams have visibility into the activity of IT staff, and only 7% can monitor the activity of users. This result is the worst among all industries that participated in the survey.
Knowing what is going on in your IT infrastructure is essential to any data-centric security approach. After all, if you don’t know who has access to your sensitive data and when that data is being used, how can you possibly ensure that data access is limited to authorized personnel only, and these employees deal with the data in an appropriate manner?
Only 18% of educational entities have visibility into the activity of IT staff
The situation gets worse when sensitive data is stored in the cloud. Companies in all sectors are often unsatisfied with the poor controls offered by cloud providers and the limited ability to track data access. Therefore, it’s no surprise that the inability to monitor user activity in the cloud was one of the top three cloud security concerns for educational institutions (mentioned by 35% of respondents). Lack of visibility prevents them from detecting security incidents in their early stages and responding promptly, which makes data breaches more likely.
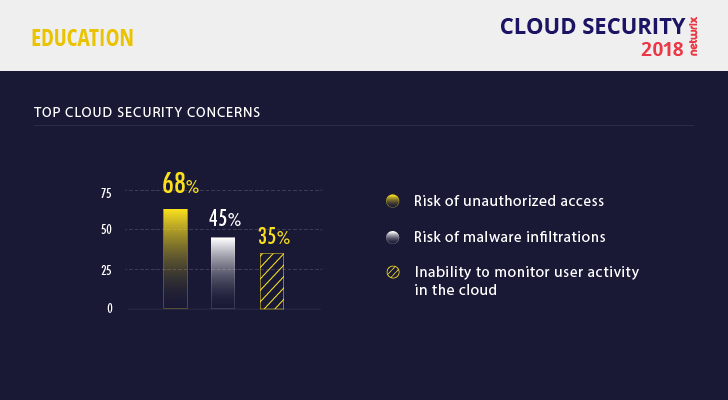
Poor visibility into user activity also creates fertile ground for malware attacks. It’s no wonder that 45% of educators were worried about being at high risk for malware infiltrations. Hackers are eager to get their hands on the personally identifiable information (PII) that schools have in abundance, as well as valuable intellectual property (IP), such as research findings. I wish I could say they had to be creative to achieve their goals, but all too often they can get in simply by using tried and true exploits of Windows XP, which is no longer supported by Microsoft but many educational institutions still run. They also take advantage of lax BYOD policies to inject malware to create botnets and distribute cryptocurrency mining software.
Insiders pose a bigger threat than anyone else
Although the Verizon DBIR report found that external actors initiated the majority (81%) of security incidents, our respondents believe that insiders pose a bigger threat to data security. After all, hackers often use social engineering techniques like phishing to trick employees, so how a single employee responds to a scam email can dramatically impact the security of the entire organization.
In this regard, one of the cloud’s main advantages — enabling access to data and services by anyone from anywhere at any time — becomes an obstacle to effective data protection, because it increases the chance of insiders misusing sensitive data and gives attackers an easier path to sensitive data, especially if they can compromise a valid account, which likely has extensive access rights.
62% of educational institutions named employees as their main security risk
As a result, 62% of educational institutions named employees as their main security risk. This was higher than any other industry surveyed; in second place was the healthcare industry, with 55% of respondents naming employees as their main cloud security problem.

Cloud future: positive but not over-enthusiastic
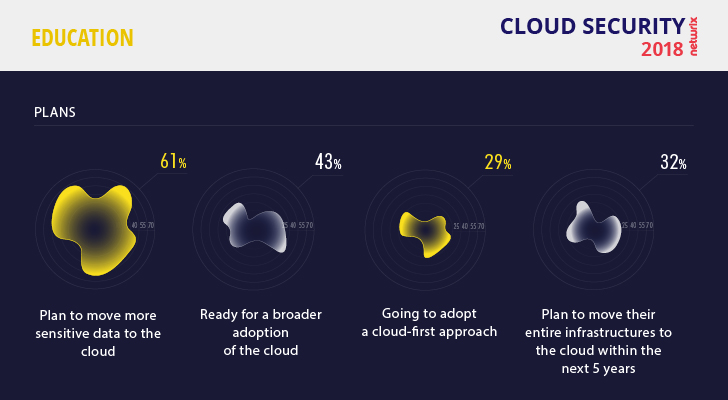
The people who are responsible for IT security in educational institutions also have to keep the IT infrastructure up and running 24/7 for e-learning initiatives, as well as regularly prepare for compliance audits. When the IT team consists of just a couple of people, this can be a tough challenge. As a result, many educational organizations have begun looking to the cloud to simplify IT tasks like software license maintenance and load balancing, and eliminate issues with legacy hardware and software. Educators are optimistic about broader cloud adoption. Roughly 43% of respondents support the idea of getting more applications as cloud-based services. This is not a record result compared to other verticals, but it is far more optimistic than healthcare that has only 23%.
When it comes to moving more sensitive data to the cloud, educational organizations are positive but not too enthusiastic. Just 61% of respondents support this idea, the lowest result of all industries surveyed, in large part due to concerns about poor visibility into user activity. As the technology evolves, however, the benefits of the cloud — flexibility, lower costs and overall convenience — will outweigh the fear of security incidents. Until then, IT teams would more likely to embrace the cloud if they had better visibility into activity there, whether through security services offered by the cloud provider or a third-party solution.
Insiders are both the problem and the solution
Despite its growing need for cloud technologies, the educational vertical is not yet equipped to address the security challenges. To improve cloud security, almost half (46%) of respondents plan to implement stricter security policies, and 39% are going to better educate their employees about cybersecurity issues.

These steps are basic to any security program, and they can be of tremendous help in combating the insider threat. To be effective, security policies must be regularly revised to address the evolving threat landscape, and they must provide rules and procedures that everyone accessing the company’s systems and data can understand and follow.
Training materials should be tailored to the employees’ level of responsibility and knowledge. To make them engaging, you can use multiple formats, from videos and live presentations to role-playing games. Your goals should be to raise security awareness, explain how to identify potential issues and encourage reporting to IT.
However, without visibility into user activity, these efforts will be of limited help. You need visibility to determine whether your updated security policies are being followed and employees learned the right lessons during the training sessions. If not, you’re able to identify the users who need special attention and offer them additional, tailor-made training. This approach will make your security strategy adaptive and help to raise security awareness to mitigate the insider threat.
View the full infographics (click on the image to open a high resolution version in a new tab)
Summary
Huge networks, unpatched legacy systems, loads of PII and IP, and careless users with broad access rights make educational institutions a tempting target for hackers. While cloud technologies can help unburden tiny IT departments, they also increase the organization’s attack surface area. Tighter security policies and better user training are essential strategies for improving security, but the fact is, no organization can guarantee that no insider will fall for phishing scams or go deliberately misuse their own privileges. To minimize risk, IT teams must have insight into both the environment and user activity, so they can minimize data overexposure and spot suspicious behavior before it results in a data breach.