Performing a data protection impact assessment (DPIA) is a complex but critical task to ensure your data is safe from security gaps and vulnerabilities. Moreover, DPIAs are mandated by many regulations. In particular, conducting regular data protection impact assessments is a key stipulation of the General Data Protection Regulation (GDPR), a comprehensive data privacy law that applies to all organizations that store or process the data of European Union (EU) residents. DPIAs are also required by the UK GDPR.
Read on to learn what DPIA means, key DPIA GDPR requirements, the cases that require DPIAs, and how to perform data protection impact assessments.
What is a data protection impact assessment?
Data protection impact assessments, sometimes called privacy impact assessments (PIAs), are performed to identify, analyze and minimize the data protection risks of a project or plan involving personally identifiable information (PII) or, as the GDPR calls it, “personal data.”
Risks to personal information can include anything from unauthorized access by internal or external actors to not handling personal data according to the wishes of the data subject. A DPIA should always result in a list of measures the organization will take to address the identified risks.
What are the benefits of a DPIA?
The benefits of conducting DPIAs extend far beyond GDPR compliance. They include:
- Lower likelihood of data breaches for systems, cookies, apps, and websites
- Reduced risk of failing to meet legal obligations
- Less risk of hefty expenses for data breach recovery, fines, lawsuits, and lost business
- Easier compliance with other data protection regulations
When should my organization conduct a DPIA?
The GDPR does not require organizations to conduct a DPIA for every processing operation related to privacy. Rather, they must conduct a DPIA whenever their data processing is likely to result in high risk to the rights and freedoms of individuals (the GDPR term is “natural persons”).
Failure to perform a DPIA when required by the official guidelines can result in legal enforcement actions, including steep fines from the European Data Protection Board.
When is a DPIA required?
Use the following criteria from The Guidelines on Data Protection Impact Assessment to determine whether a DPIA is mandatory:
- Evaluation or scoring — You must conduct DPIAs when profiling people, especially their work performance, economic situation, health, personal preferences or interests, behavior, location, or movement. The GDPR also requires DPIAs for credit score determinations, genetic testing to assess health risks and behavioral-based marketing profiling.
- Automated decision-making — DPIAs are necessary when enacting processes that automate legal decision-making. You must ensure that such processing doesn’t exclude or discriminate against an individual.
- Systematic monitoring — You must conduct DPIAs when observing, monitoring or controlling data subjects, including when they are in public areas. Examples include remote security monitoring like doorbell camera apps.
- Sensitive data handling — DPIAs are needed any time you deal with highly personal data, such as a patient’s health data.
- Large-scale data processing — DPIAs are required when you exercise large-scale data processing. Criteria for determining whether data processing occurs on a large scale include the number of data subjects and the duration and geographical extent of the activity.
- Matching or combining datasets — You must conduct a DPIA when merging or comparing two or more sets of data collected for different purposes.
- Vulnerable data subjects — DPIAs are required when there is a power imbalance between data subjects and the data controller, since that could lead to harm to the data subject. DPIAs are required for data subjects who cannot oppose the processing of their data, such as children, employees, and people with mental illnesses or cognitive issues.
- Innovative use — DPIAS are required for newer technologies, such as IoT devices, fingerprint scanners and facial recognition systems.
- Transfer of data outside the EU or UK — You must perform DPIAs when transferring data outside of the EU or UK. This helps ensure that appropriate safeguards are in place.
- Handling applicant data — When you carry out processes that prevent data subjects from exercising a right or using services or contracts, you must conduct a DPIA. One example is when a bank performs credit checks for loan applications.
When is a DPIA not required?
You are not required to conduct a DPIA under the following circumstances:
- You are meeting legal obligations — If you are processing data based on a legal obligation or on behalf of the public, you don’t have to conduct a DPIA. However, this exception applies only when data processing meets at least one of the following circumstances:
- You have a statutory basis for processing the data.
- A legal provision or statutory code regulates the processing operation.
- You are not subject to DPIA obligations as laid out in applicable legislation.
- A data protection risk assessment was conducted as part of the impact assessment when the GDPR was adopted in May 2018.
- You’ve already conducted a similar DPIA — If you have completed a DPIA and can prove that the nature, design, scope, context and purpose of the current situation are all similar, you may be exempt from performing a new DPIA.
When should a DPIA be conducted?
You should incorporate DPIAs in new projects involving personal data from the start and use them throughout planning and development. For instance, if you want to make an IoT app, consider DPIA obligations during the first stages of the planning process and through to completion.
What about processes that were in place before the GDPR took effect?
The DPIA requirement applies to processes that started on or after May 25, 2018, and to processes that started before that date and have changed in a way that affects compliance requirements.
Although you may technically be exempt from carrying out DPIAs, most compliance experts recommend conducting DPIAs for risk-processing operations that were already underway before the GDPR went into effect.
What should be included in a DPIA?
Unlocking the full benefits of DPIAs and ensuring you comply with the GDPR requires a comprehensive approach. The following checklists can help you avoid missing critical information or context.
DPIA Awareness Checklist
An awareness checklist will help you understand your company’s current DPIA processes and establish a culture in which all employees are vigilant of DPIA needs, reducing the likelihood of human error. Awareness checklists include:
- Employee training — Instruct employeeson how DPIAs protect personal data and when they are necessary.
- Procedural and policy management — Review how well your company policies match up with DPIA requirements.
- Implementation guidelines — Document what circumstances require a DPIA.
DPIA Screening Checklists
A screening checklist provides a more thorough analysis that outlines criteria for when a DPIA is necessary for specific projects. Screening checklists include:
- Understanding the data in question — Create documents that ask questions about how much data is involved, the vulnerability of the data subjects, and how personal and private the data is. Also provide guidelines to distinguish high-risk from low-risk data.
- Details on data processing — Specify how long the data will be processed, the storage locations and oversight, who has access, what security measures are in place, and how to notify data subjects of processing. Also document how you plan to consult privacy professionals and regulators.
- Clear statement about why a DPIA was or was not deemed necessary — If you decide to greenlight a DPIA, you should have a clear, written statement of purpose. If you decide against a DPIA for a project, always include documentation on why a DPIA was decided against.
DPIA Processing Checklist
The processing checklist directs processors on their exact conduct once the DPIA begins, which supports your ability to comply with GDPR requirements from start to finish. Failing to use a process checklist significantly increases the chances of human error and other issues during the processing stage. A processing checklist includes:
- Risk identification — Define how you plan to consult with processors to understand risks before processing commences. Ensure that the extent of processing matches the overall purpose. Once risks are assessed, include written measures on how you plan to measure and mitigate them.
- Stakeholder list — Identify all key stakeholders and your plans to communicate and update them at various stages.
- Decision-making records — Include detailed documentation on who you consult before and during processing, as well as everyone who has been given access to the data. Additionally, document all processing methods, any technology used and any changes in methodology.
- Review processes — As you carry out a DPIA, create a schedule to constantly review your project status and alterations. Remember, any changes in the assessment’s nature, context, scope or design may require you to start the process from the beginning.
What steps should I take to perform a DPIA?
Here are the steps you need to take in the impact assessment DPIA process to comply with the General Data Protection Regulation.
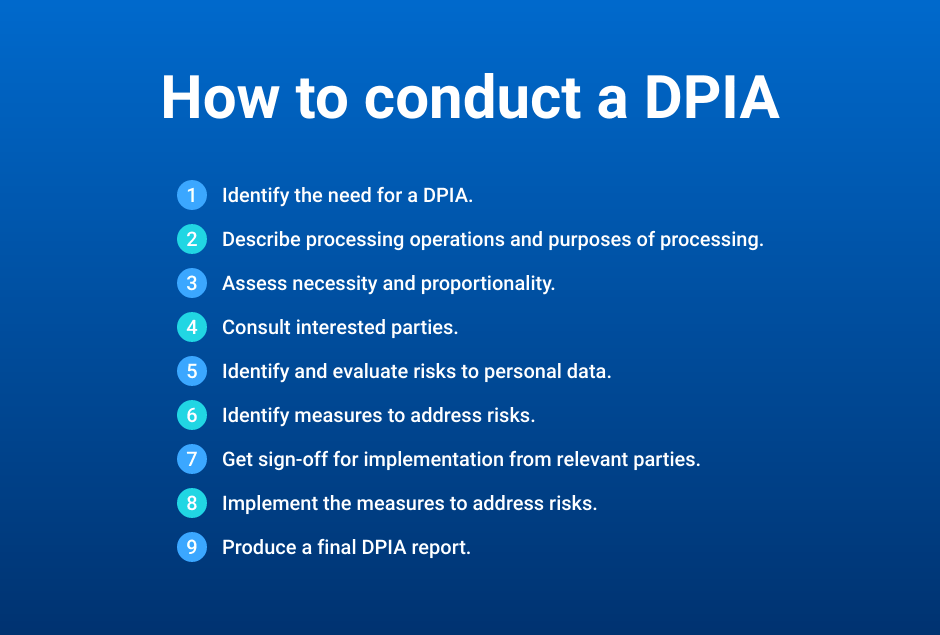
1. Identify the need for a DPIA.
Use the information above to determine whether a DPIA is required. Be sure to document the following aspects of the processing:
- Nature — What you plan to do with the data
- Scope — What data will be processed
- Context — Internal and external factors that could affect expectations or impact
- Purpose — Why your organization wants to process the data
2. Describe processing operations and their purpose.
Document how data will be processed throughout the project and the scope of the data. Answer the following questions:
- How is data being collected and used?
- Where and how is data being stored?
- Where is data being collected from?
- Is the data stored with any third parties?
- Are there any high-risk data categories involved?
- How much data is being collected, and how many data subjects are impacted?
- Where data processing activities are taking place?
- What are the data retention requirements?
Next, describe the purpose of the data processing activities as it relates to the project’s objectives. Describe each data processing activity, how it will impact the consumer and how it will be leveraged for the project.
3. Assess necessity and proportionality.
An important aspect of a DPIA is justifying the data processing activities that occur by explaining what is actually required for the objectives and outcomes of the project. Start by answering these questions:
- Is there a legal basis for collecting this data?
- Are appropriate consent measures in place?
- Are vulnerable data subjects involved?
- Have previous projects of a similar nature performed similar processing? If so, were security flaws identified and remediated?
- Is data processing necessary to achieve the objectives of the project?
- How are consumer rights being upheld?
- Are there ways to minimize the use of consumer data?
4. Consult interested parties.
You should consult several key parties throughout the course of the DPIA. These include:
- Data Protection Officer (DPO) — The organization’s DPO is responsible for monitoring compliance with the GDPR and other data protection laws, training staff involved in data processing, and acting as a contact point for the data subjects. Consulting a DPO can help you demonstrate compliance, increase accountability and obtain feedback on project risks.
- Project stakeholders — Involving all stakeholders will help you fully understand the extent and necessity of data processing activities, as well as devise appropriate strategies to address risks.
- Data subjects and their representatives — Data subjects and their representatives can give you feedback on how their data is being processed and ensure the legality of your processing activities.
- Outside experts — For data privacy expertise, consider engaging outside experts such as information security professionals, lawyers, technicians, security analysts and sociologists.
5. Identify and evaluate risks to personal data.
Create a prioritized list of your assets and identify potential vulnerabilities. For example, if one of your assets is a server where you store client data, risks to that data could include natural disasters, hardware failures and malicious attacks.
In your risk analysis, consider:
- Data whose loss or exposure would impact operations
- Key business processes that use those data assets
- Whether data is being anonymized
- Whether data retention policies are applicable
- Whether data is being stored in unsafe locations or could possibly be moved to such locations
- Whether the scope of data processing will change throughout the course of the project
- Whether appropriate access controls are being applied
- Threats that could impair the organization’s ability to operate, and the severity and likelihood of each threat
6. Identify measures to address risks.
Once you have a good idea of the potential risks involved in the project, strategically formulate and implement appropriate risk mitigation measures. Data security solutions can help you ensure that:
- The necessary security measures are in place to prevent unauthorized access to personal data by internal or external actors.
- Data retention policies are in place to remove data that is no longer required.
- Discovery and monitoring technologies provide visibility into where personal data exists, who is accessing it, how it is being used and how it is moving throughout the organization.
- Remediation actions (such as deleting unnecessary data and cleaning up access) can be automated and performed at scale.
You must document which information protection risks a specific mitigation measure will help address and how. Here are two examples:
Example 1
Risk: The organization retains PII longer than necessary.
Solution: Use an automated data retention tool to ensure data is deleted as required.
Example 2
Risk: Unauthorized users might access the server and access regulated data.
Solution: Increase security testing and monitoring of the server to prevent and detect suspicious activity.
7. Get sign-off.
Once all risks are identified and an appropriate security strategy is devised, obtain sign-off for implementation from relevant parties. The list will depend on the organization and specific project but often includes the Data Protection Officer and members of the management team.
8. Implement measures to address risks.
Next, deploy the solutions and other measures you have identified to reduce risks.
9. Produce a final DPIA report.
Last but not least, you must produce a final DPIA report. It must include the following information:
- A detailed description of the project and its purpose
- An assessment of data processing needs and scope
- An assessment of data protection and consumer privacy risks
- An explanation of how the organization will mitigate risks and comply with GDPR requirements
It’s best practice to publish DPIAs in full or in part, even if the GDPR does not require it. This helps to foster trust in your processing operations and demonstrates accountability and transparency to all stakeholders.
How can Netwrix help with data protection impact assessments?
Performing a DPIA can be time-consuming, especially for organizations with limited IT staff. Fortunately, Netwrix is here to help. We offer compliance audit solutions that strengthen security, satisfy auditors and secure organizations of all sizes. With our services, you can:
- Identify regulated data and lock down access to it — Pinpoint what regulated content your organization has and ensure it is stored only in secure locations.
- Control access to your data — Strictly enforce the least privilege principle with automated access request and approval workflows, regular review and attestation by data owners, effective Group Policy management, secure system configurations, and strong password policies. Moreover, detect threats in their early stages and respond quickly to shut them down.
- Slash audit preparation time from weeks or days to minutes — Quickly produce hard evidence of regulatory compliance with predefined reports on system configurations, data access, user accounts and more.
FAQ
1. Are DPIAs mandatory?
Article 35 of the GDPR requires a DPIA whenever you conduct processes likely to increase the risk to individual rights or freedoms. The DPIA requirement applies to processes that started on or after May 25, 2018, and to processes that started before that date and have changed in a way that affects compliance requirements.
2. Are there any exceptions?
A DPIA might not be required if you are processing data based on a legal obligation or on behalf of the public, or if you conducted a similar DPIA already.
3. Who is responsible for performing DPIAs?
A DPIA should involve your Data Protection Officer if you have one, as well as the person leading the project that triggered the DPIA and any relevant data processors.
4. When should DPIAs be conducted?
Organizations should incorporate DPIAs from the start of any new project and conduct them throughout the planning and development process.
5. What should a DPIA contain?
The Information Commissioner’s Office (ICO) describes what to include in a DPIA assessment. In particular, be sure to document the following factors about the data processing:
- Nature — What you plan to do with the data
- Scope — What the processing covers
- Context — Internal and external factors that could affect expectations or impact
- Purpose — Why the organization wants to process the data


