With cyberattacks exploding worldwide, it’s more important than ever for organizations to have a robust password policy. Hackers often gain access to corporate networks through legitimate user or admin credentials, leading to security incidents and compliance failures.
This article explores Active Directory password policy settings, how to check password complexity requirements in Active Directory, Active Directory password policy best practices, and more. After covering these topics, we will answer some frequently asked questions.
How Attackers Compromise Corporate Passwords
Adversaries use various techniques to compromise corporate passwords, including the following:
- Phishing: A hacker pretends to be a trustworthy party and tries to get you to reveal your personal information. For example, you receive a text from what looks like your bank asking you to reset your online banking password, but it is actually from a hacker. If you “reset your password” with the link in the text, the hacker will steal your credentials.
- Man-in-the-Middle attack: These happen when a hacker or compromised system sits in between two uncompromised systems or people and deciphers the data they are sending to each other, such as passwords and bank account numbers.
- Keylogging: Keyloggers are malicious software for tracking users’ keystrokes and reporting them back to hackers. Users may download keyloggers when installing software they believe to be legitimate.
- Brute force attack: Hackers run programs that enter various potential passwords for a particular user account until they hit the right one.
- Dictionary attack: This is a specific form of brute force attack that involves trying words found in the dictionary as possible passwords.
- Password spraying attack: Adversaries try common passwords against multiple user accounts to see if they work.
- Credential stuffing attack: Hackers use automated tools to enter lists of credentials against various company login portals.
- Spidering: Adversaries collect as much information as possible about a hacking target and then try out passwords created using that data.
How to View and Edit Active Directory Password Policy
To defend against these attacks, organizations need a strong Active Directory password policy. Password policies define rules for password creation, such as minimum length, complexity (like whether a special character is required), and when the password expires before it must be changed to a different one.
To configure a domain password policy, admins can use Default Domain Policy, a Group Policy object (GPO) that contains settings that affect all objects in the domain. To view or edit this GPO, follow these steps:
- Open the Group Policy Management Console (GPMC).
- Expand the Domains folder, choose the domain whose policy you want to access and choose Group Policy Objects.
- Right-click the Default Domain Policy folder and click Edit.
- Navigate to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Password Policy.
Alternatively, you can access your domain password policy by executing the following PowerShell command:
Get-ADDefaultDomainPasswordPolicy
Remember, any changes you make to a domain’s default password policy apply to every account in that domain.
AD Password Policy Settings
Here are the six AD password policy settings and their default values:
- Enforce password history: The default is 24. This setting specifies the number of unique passwords users must create before reusing an old password. Keeping the default value is recommended to reduce the risk of users having passwords that have been compromised.
- Maximum password age: The default is 42. This setting establishes how long a password can exist before the system forces the user to change it. Users typically get a pop-up warning when they reach the end of their password expiration period. You can check this setting through PowerShell by executing the command net user USERNAME/domain. Keep in mind that forcing frequent password changes can lead to users writing their passwords down or simply appending the month to a stem word they reuse, practices that actually increase security risks. Setting “Maximum password age” to 0 means that passwords never expire (which is generally not recommended).
- Minimum password age: The default is 1 day. This setting specifies how long a password must exist before the user is permitted to change it. Setting a minimum age keeps users from resetting their password repeatedly to circumvent the “Enforce password history” setting and reuse a favorite password immediately.
- Minimum password length: The default is 7. This setting establishes the fewest number of characters a password can have. While shorter passwords are easier for hackers to crack, requiring really long passwords can lead to lockouts from mistyping and to security risks from users writing down their passwords. Best practices recommend a minimum password length of at least 8.
- Complexity requirements: The default is Enabled. This setting details the types of characters a user must include in a password string. Best practices used to recommend leaving this setting enabled, but password length is now seen as a better strategy than complexity or frequent changes. Complexity requirements typically require the password to include a mix of:
- Upper or lowercase letters (A through Z and a through z)
- Numeric characters (0–9)
- Non-alphanumeric characters like $, # or %
- No more than two symbols from the user’s account name or display name
- Store passwords using reversible encryption: The default is Disabled. This setting offers support for apps that require users to enter a password for authentication. Admins should keep this setting disabled because enabling it would allow attackers to break this encryption to log into the network once they compromise the account. As an exception, you can enable this setting when using Internet Authentication Services (IAS) or the Challenge Handshake Authentication Protocol (CHAP).
Fine-Grained Policy and How It’s Configured
Older versions of AD allowed the creation of just one password policy for each domain. Thanks to the introduction of fine-grained password policies (FGPP), admins can now create multiple password policies to better meet business needs. For example, you might want to require admin accounts to use more complex passwords than regular user accounts. It’s vital to define your organizational structure thoughtfully so it maps to your desired password policies.
While you define the default domain password policy in a GPO password policy, FGPPs are set in password settings objects (PSOs).
You can create and manage fine-grained password policies using the Active Directory Management Center (ADAC) in Windows Server: Open ADAC, click on your domain, navigate to the System folder, and click on the Password Settings container.
NIST SP 800-63 Password Guidelines
The National Institute of Standards (NIST) is a federal agency charged with issuing controls and requirements for managing digital identities. Special Publication 800-63B covers standards for passwords. Revision 3 of SP 800-63B, issued in 2017 and updated in 2019, is the current standard.
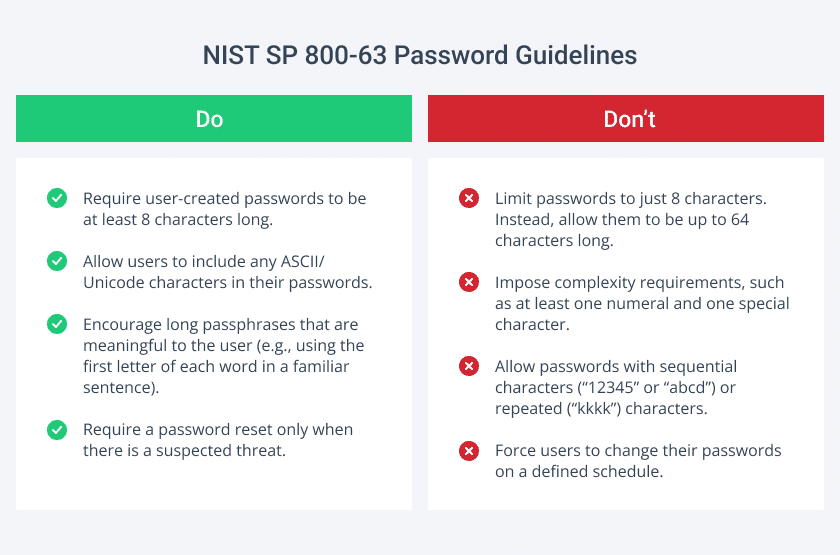
These guidelines provide organizations with a foundation for building a robust password security infrastructure. NIST recommendations include the following:
- Require user-generated passwords to be at least 8 characters long (6 for machine-generated ones).
- Allow users to create passwords up to 64 characters long.
- Allow users to use any ASCII/Unicode characters in their passwords.
- Disallow passwords with sequential (“12345” or “abcd”) or repeated (“kkkk”) characters.
- Do not require frequent password changes. Although for years, many organizations have required users to change their passwords frequently, this policy often leads to users making incremental changes to a base password, writing their passwords down or experiencing lockouts because they forget their new passwords. Accordingly, the latest NIST 800-63B standards call for using password expiration policies carefully. More recent research suggests alternatives such as using banned password lists, requiring longer passphrases and enforcing multi-factor authentication (MFA) for additional security.
AD Password Policy Best Practices
AD password policy best practices are professional or commercial procedures that are prescribed or accepted as being the most effective or correct. Here’s a summary of AD password policy best practices and user training.

Summary of Best Practices
The best practices for setting and changing your password policy in Active Directory include the following:
- Set a minimum password length of at least 8 characters.
- Enforce a password history policy that looks back at the last 10 passwords of a user.
- Make the minimum password age 3 days to keep users from quickly rotating through historical passwords and re-using a previous one.
- Check proposed new passwords against banned password lists, lists of breached passwords and password dictionaries.
- Reset local admin passwords every 180 days (consider using the free Netwrix Bulk Password Reset tool for that).
- Reset device account passwords at least once per year.
- Require passwords for Domain Admin accounts to be at least 15 characters long.
- Set up email notifications to let users know passwords are about to expire (the free Netwrix Password Expiration Notifier tool can help).
- Consider creating granular password policies to link with specific organizational units instead of editing the Default Domain Policy settings.
- Consider using password management tools to store passwords.
- Enable users to change their passwords via a web browser and help them pick compliant new passwords.
- Set up account lockout policies to avoid brute force attacks.
For more information, read our password policy best practices for strong security in AD.
User Training
User training is as crucial as your password policy. You must educate your users on the following rules of behavior:
- Don’t write down passwords. Instead, pick strong passwords or passphrases you can recall easily, and use a password management tool.
- Don’t type your password when anyone is watching.
- Understand that URLs beginning with “HTTPS://” are more secure than those that begin with “HTTP://”.
- Don’t use the same password for multiple websites that provide access to sensitive information.
How Netwrix Can Help
Besides setting and managing a robust Active Directory password policy, you should also implement a comprehensive Active Directory security solution like Netwrix’s end-to-end Active Directory Security Solution. This powerful tool can protect your IT infrastructure and critical data by:
- Identifying and fixing security gaps: Netwrix’s Active Directory assessment tools can help you assess your security posture and prioritize risk mitigation efforts. It can also identify weak passwords, spot shadow admin accounts and excessive access rights that put your AD at risk, and ensure your AD infrastructure has a secure configuration.
- Spotting and responding to threats: The Netwrix solution can help you identify and respond to threats by managing the properties and membership of groups, protecting against identity theft, reducing your attack surface, protecting credentials from advanced threats, and blocking potentially dangerous AD and GPO changes.
- Mitigating the impact of AD security incidents: Netwrix empowers cybersecurity teams to respond quickly by automating responses to expected threats and providing actionable insights. For instance, you can disable or lock an account, escalate an incident to your ITSM, SIEM or another cybersecurity program, or reset passwords in bulk or individually.
Interested in learning more about how Netwrix’s Active Directory Security Solution can help with auditing and protecting your data? Download a free trial today.
FAQ
How do I find and edit my Active Directory password policy?
You can find your applied Active Directory password policy location for a specific domain in two ways:
- By navigating to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Password Policy via the management console
- By using the PowerShell command Get-ADDefaultDomainPasswordPolicy
Are passwords encrypted in Active Directory?
Yes. Passwords created by a user go through a hashing algorithm that encrypts them.
What is Active Directory password complexity?
AD password complexity requirements control the characters that cannot or cannot be included in a password. For example, users might be prevented from using sequential characters or digits. They may also be required to include at least one number and one lowercase letter in the password.
What is Windows Server password policy?
Windows Server password policy controls passwords for accessing machines running the Windows Server operating system.
How do I find, edit, or disable a password policy in Windows Server?
Locate the GPO through the Group Policy Management Console and click Edit.
What is a good password policy?
Best practices for Active Directory password requirements include the following:
- Make users create at least 10 new passwords before reusing an old one.
- Compare proposed new passwords against lists of breached passwords and password dictionaries.
- Apply a minimum password age of 3 days.
- Make users create passwords that are at least 8 characters long.
- Disable reversible encryption.
What is the password policy in Active Directory?
The password policy in Active Directory is a set of rules that define what passwords are allowed in a company. The password policy should establish standards for password length, complexity and the frequency of changing account passwords. The purpose of the password policy is to make it difficult for a cyber attacker to capture or brute-force passwords over a network.
Note that the default password policy applies to all your domain’s computers. You should use a fine-grained password policy if you want to apply different password policies to a group of users.
What is the password policy age in Active Directory?
The password policy age in Active Directory determines how long a password must be used before the user can change it. The default value is 42 days.
What is the password size limit in Active Directory?
The maximum length of a password in Active Directory is 256 characters. However, human users can type only 127 characters to log in due to the Windows graphical user interface (GUI).
How do I configure the password policy in Active Directory?
Changing the password policy in Active Directory requires you to do the following:
- Open the Group Policy Management Console.
- Expand Domains and click on your domain and Group Policy Objects.
- Right-click on the default domain policy and click Edit.
- Go to Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies\Password Policy.

 of ENG [Free Guide] short-384x406.jpg)
