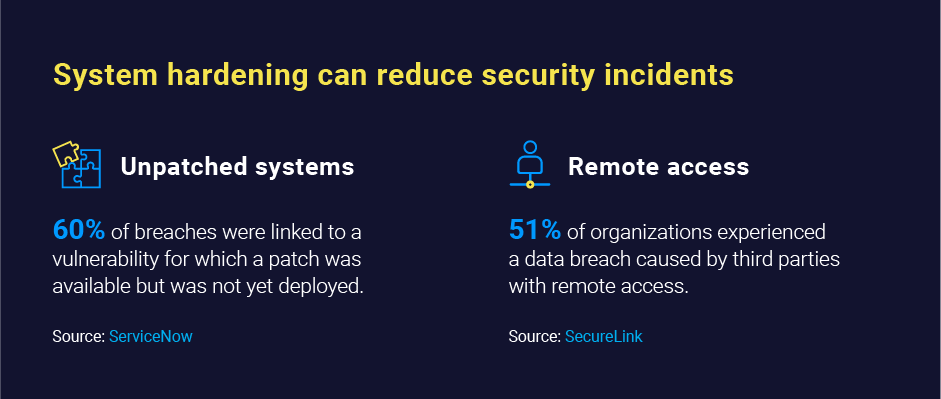
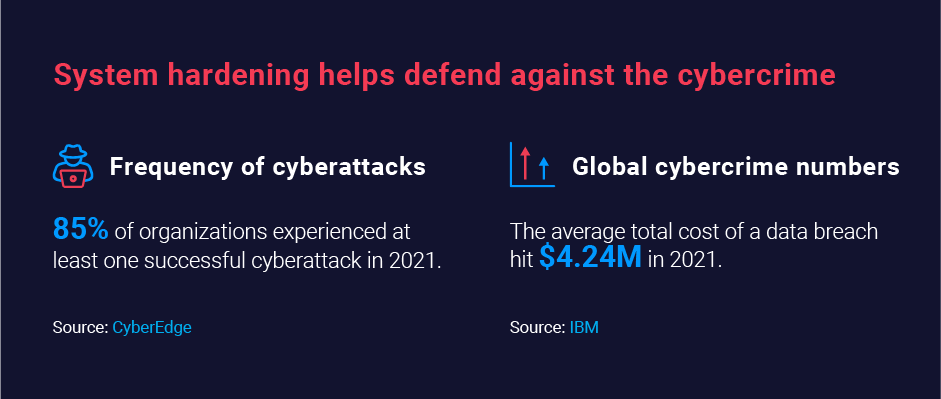
Complex cyberattacks dominate the headlines, making breaches seem sophisticated. However, most hacks are relatively straightforward, with attackers exploiting well-known security vulnerabilities in configurations. In fact, cyberattacks are rather common. According to IBM, 83% of companies have experienced more than one breach while in operation.
System hardening is a cybersecurity approach that can significantly enhance your company’s defense against cyber threats. System hardening involves a range of techniques, tools, and methodologies aimed at minimizing vulnerabilities in servers and computers to remove unnecessary services and applications and enable built-in security features. This process reduces potential attack vectors, thus limiting opportunities for cyber attackers to infiltrate your information technology environment.
System hardening demands a systematic approach to identify, audit, control, and mitigate potential cybersecurity vulnerabilities across your IT infrastructure. Key focus areas for system hardening efforts include:
- Operating systems: Reduce vulnerability in operating systems on servers and endpoints by removing unnecessary services, disabling dormant accounts, and adjusting security settings to meet industry best practices.
- Network infrastructure: Enhance network infrastructure security by configuring both hardware and software firewalls, implementing intrusion detection and prevention systems, and conducting routine vulnerability assessments.
- Databases: Boost database security by enforcing access controls, encrypting confidential data, and fine-tuning security settings.
- Applications: Enhance the security of applications such as Microsoft Exchange or Microsoft 365 by modifying settings to protect against exploitation through macros or other scripting attacks.
- Remote systems: Safeguard remote devices and systems by enforcing secure access controls and protocols, along with vigilant monitoring for vulnerabilities and threats.
This article will delve into the system security hardening process and why it’s essential to harden your systems. It covers the techniques, components, varieties, and best practices for effective system hardening.
Why Is It Essential to Harden Your Systems?
Beyond safeguarding your data and systems against cyber threats, hardening plays a crucial role in ensuring compliance with legal and regulatory frameworks. By implementing robust security measures and hardening techniques, organizations can meet stringent requirements set forth by regulatory compliance, industry standards, and guidelines. This not only helps in avoiding legal penalties and fines but also builds trust with customers and partners by demonstrating a commitment to data protection and cybersecurity.
Several regulations specify system hardening requirements, including:
- The North American Electric Reliability Corporation Critical Infrastructure Protection (NERC requires authorizing and documenting deviations from baseline configurations.
- Payment Card Industry Data Security Standard (PCI DSS) V4 mandates secure configurations for all system components to achieve a proper balance between security and functionality regarding an organization’s security policy.
- Health Insurance Portability and Accountability Act (HIPAA) sets security rule standards for safeguarding electronic personal health information (ePHI) through technical, administrative, and physical measures to preserve its integrity, confidentiality, and security.
In addition to regulatory and industry requirements, some of the popular security frameworks also prescribe system hardening to bolster security:
- The Center for Internet Security (CIS) Control 4 mandates the secure configuration of enterprise assets and software.
- NIST Special Publication 800-53 Revision 5:
- CM-2 “Baseline Configuration” requires developing and maintaining a documented baseline configuration of your system, covering operational and connectivity aspects, among others.
- CM-3 “Configuration Change Control” involves documenting and approving configuration changes, retaining records, and overseeing related activities.
- The Defense Information Systems Agency’s (DISA) Security Technical Implementation Guides (STIGs) provide best practices for securely setting up and maintaining IT assets, with each STIG focusing on specific types of assets and outlining necessary configuration practices for security.
Types of System Hardening
Server Hardening: Server Hardening means securing the ports, access points, permissions and functions of a server to fortify security. Some usual practices for server hardening include imposing multiple authorizations and authentications, enforcing strong passwords, and disabling USD ports.
Software Application Hardening: Software Application Hardening means deploying updates and patches to the server to maintain a secure environment. Some common practices for software hardening include using antiviruses, malware safety applications, and early threat-detecting programs.
Operating System Hardening: Operating System Hardening means safeguarding the system on which the computer is running. This can be done by uninstalling unnecessary drivers and apps from the OS that could pose security risks.
Network Hardening: Network Hardening means securing communication channel to make sure that there are no intruders with the network. This can be done through encryption and firewalls. It is also a good practice to use an intrusion detection system, which would detect a potential attack in advance ensuring that the network is safe and secure.
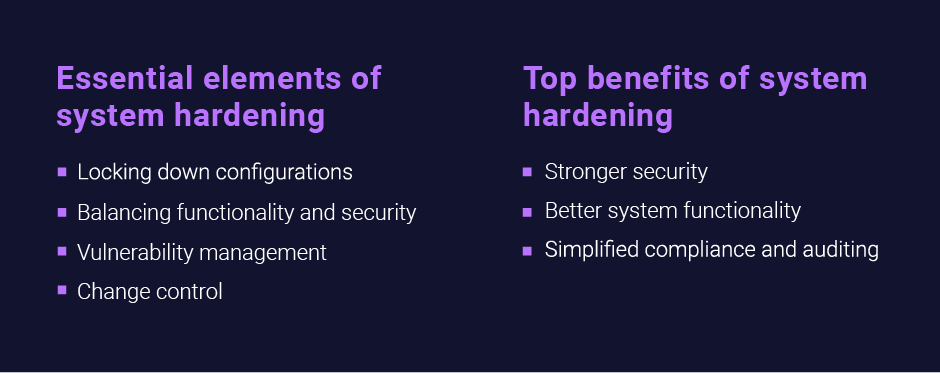
Elements of System Hardening
The hardening process begins by evaluating the system and network to understand primary needs. Don’t overlook components such as the BIOS, firmware, and installed software, as attackers target all these to find the weak link that will get them in. Once the evaluation is complete, you can then begin the process of locking down configurations using standards such as NIST, CIS, and DISA’s STIGs to reduce threats. Maintaining a balance between functionality and security is crucial. While security is paramount, the hardening policy must address cybersecurity needs in a way that the IT team can realistically implement as a proper balance between functionality and security. Incorporate vulnerability management to identify and address security weaknesses, prioritizing threats to lessen the attack surface. Ensure all changes are documented to allow for potential reversal in the future if needed. A systematic approach to managing system changes ensures smooth transitions for system and application upgrades or services.
System Hardening Best Practices
System hardening involves multiple layers and aspects within your IT infrastructure. Following these practices will help you protect against vulnerabilities and cyber threats
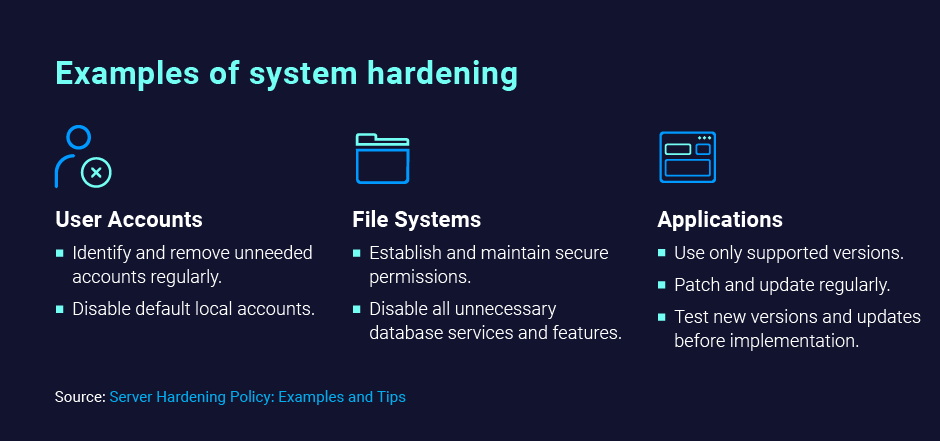
User Accounts
Cyberattackers often exploit vulnerabilities in user accounts to gain access to IT systems. User account hardening reduces cybersecurity risk by identifying and removing unnecessary user accounts. It also involves:
A common target for threat actors is user accounts, with privileged accounts being the keys to the kingdom. Effective user account hardening is crucial for minimizing cybersecurity risks. Some suggested key strategies include the following:
- Create and implement a user account policy that defines the types of accounts that are allowed, such as administrator, standard user, and local accounts. It is highly recommended that you disable all guest accounts.
- Creating secure password policies that enforce the latest password complexity recommendations and prevent passwords that are easy to guess.
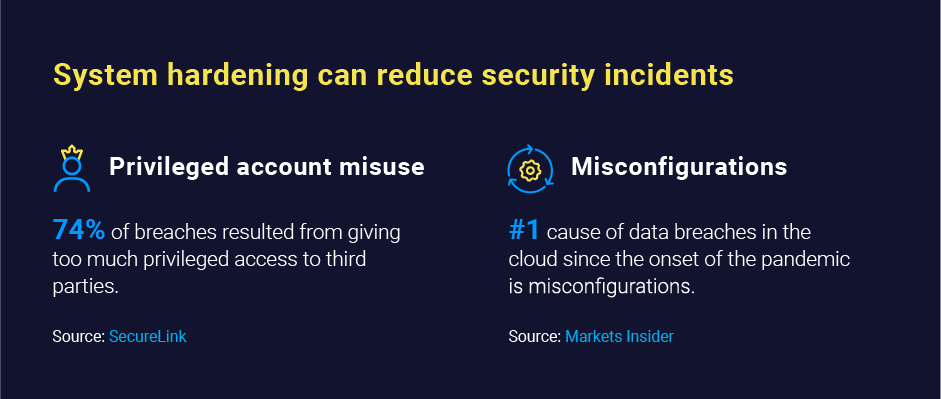
- Enforce the principle of least privilege by limiting the number of users with administrator access to the system. Using a Privileged Access Management (PAM) solution can streamline this enforcement.
- Restrict access to privileged functions such as user account management and system configuration to reduce the risk of unauthorized changes to systems.
- Monitor the privileges assigned to groups and built-in accounts carefully to ensure only authorized users can access sensitive information and systems.
File Systems
Enhance system security by setting secure permissions on files and directories, allowing only authorized users to access sensitive information. Protect data by encrypting it both in transit and at rest and limit access to potentially harmful file types, like executables, to minimize the attack surface. Employ file integrity monitoring to detect unauthorized changes and implement robust access controls, such as role-based access control (RBAC) or identity governance and administration (IGA) solutions, to ensure users can only access necessary resources and information for their job functions.
Applications
Application hardening, or software hardening, combats common cybercriminal tactics by securing applications from unauthorized tampering and reverse engineering to significantly reduce attack vectors. Key strategies include:
- Application whitelisting to block unapproved software.
- Only using supported software versions with security patches.
- Regularly applying patches and updates to fix vulnerabilities using some type of patch management system.
- Eliminating unnecessary software and services
While it’s crucial to apply patches to all systems and software, it’s equally important to test these updates to make sure they don’t disrupt normal operations or bring in new security vulnerabilities.
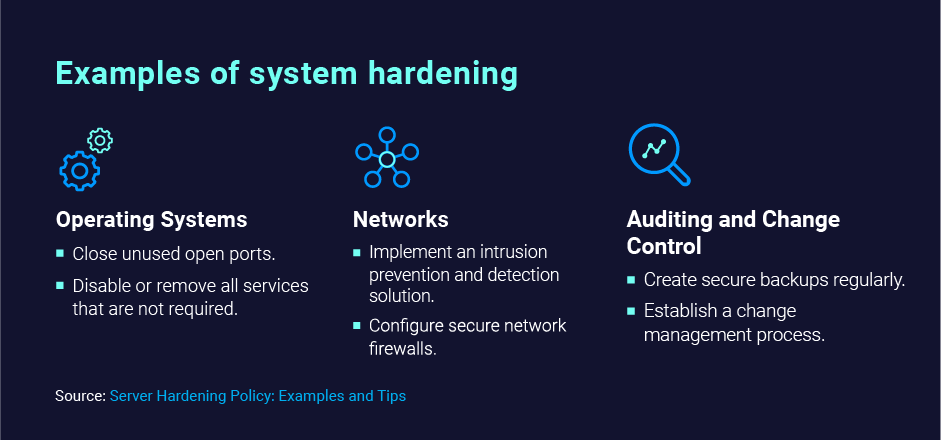
Operating Systems (OS)
As the name suggests, hardening operating systems (OS) involves enabling or adding security features to your OS to make it more secure. OS hardening typically involves the following:
- Closing any network ports that are not required for the system’s intended purpose to reduce the attack surface and prevent unauthorized access.
- Disabling or removing services and drivers that are not required.
- Installing security patches and updates as soon as they become available to address newly discovered vulnerabilities.
- Testing new versions and updates before implementation to ensure theydo not introduce new vulnerabilities.
- Applying advanced security measures such as firewalls, intrusion detection/prevention systems, and antivirus software to safeguard your OS. Examples include Windows security features like Secure Boot, which prevents malicious software from loading when your computer starts to ensure that only trusted software can run on the system.
- Enforcing timeouts that lock out the screen if it is left unattended can help prevent unauthorized access to the system.
Network Devices and the Network Stack
You can bolster the security of your servers and networking stack by implementing a series of strategic measures. Introducing an intrusion prevention and detection system (IPS) significantly enhances protection by detecting and thwarting unauthorized access attempts. Configuring secure network firewalls ensures that only necessary traffic is allowed, greatly reducing the attack surface. Removing superfluous IP routes and DNS elements from servers helps in diminishing potential entry points for threats. Implementing DHCP snooping acts as a safeguard between trusted DHCP servers and untrusted hosts, effectively screening suspicious DHCP messages and regulating DHCP traffic. Enforcing the use of secure encrypted protocols like HTTPS and SFTP on servers will prevent attackers from intercepting and deciphering network communications.
BIOS and Firmware
Firmware is a specific computer software that provides low-level control for a device’s specific hardware. BIOS, short for Basic Input/Output System, is software stored on a memory chip on the motherboard. It provides runtime services for programs and OS and performs initialization during the booting process. A compromised BIOS can allow an attacker to gain unauthorized access to a system, change system settings, or even install malware or other malicious software. Steps to harden the BIOS include the following.
- Enable password protection to prevent unauthorized access to the system’s low-level settings.
- Disable unnecessary features to reduce the attack surface.
- Regularly update the BIOS or firmware to address newly discovered vulnerabilities.
- Enabling Secure Boot to verify that the firmware, operating system, and other software are signed with a cryptographic key to ensure that only trusted software can run on the system.
- Enabling TPM (Trusted Platform Module),a hardware component that provides cryptographic functions to secure sensitive data such as encryption keys, passwords, and digital certificates.
Auditing and Change Control
Auditing and change control are used to track and manage changes to a system and ensure that they are authorized, documented and meet auditing compliance. Auditing helps to identify and track any unauthorized changes to a system, while change control is used to manage and document any necessary changes to a system. Auditing in system hardening encompasses several crucial activities, including:
- The regular review of system and network logs to identify unauthorized access or unusual activity.
- The monitoring of system performance and capacity to detect any potential issues.
- Maintaining up-to-date records of software versions and updates
Change control involves overseeing and documenting critical changes to the system, ensuring each change request is reviewed and approved before implementation, verifying that modifications do not introduce new vulnerabilities or affect system performance negatively, and tracking alterations to the system’s configuration and software.
Legacy Systems
While legacy systems might be deemed more secure when disconnected from the cloud, they are actually more vulnerable to cyberattacks as they typically lack protection by modern, industry-standard security protocols. Hardening these systems can be challenging due to their poor integration with modern technologies and limited flexibility. If typical hardening strategies cannot work due to configuration limitations in legacy systems, you may want to consider isolating them from the internet.

Benefits of System Hardening
System hardening presents three main benefits:
- Stronger security: A smaller attack surface means a lower risk of unauthorized access, data breaches, spoofing, ransomware, or malware.
- Better system functionality: System hardening removes unneeded programs, lowering the risk of misconfigurations, operational issues, compromise, and incompatibilities.
- Simplified compliance and auditing: System hardening translates to fewer accounts and programs and a simpler IT environment. As a result, auditing is much less time and resource-consuming.
- Better resource management: Hardening the system can mean that resources are used more efficiently, which can lead to better performance and lower costs.
- Improved incident response: Hardening the system means that there are fewer attack vectors, which can make it easier to detect and respond to an incident.
System Hardening Checklist for Enhanced Security
As you can see, the system hardening process provides many benefits, including better security, simplified auditing and compliance, and improved system functionality. Use this checklist of best practices to harden your system:
- Create and maintain an inventory record for each asset, as this practice will help you identify and remove unnecessary hardware and software. Remember to include each asset’s baseline configuration and record every change.
- Thoroughly test and validate suggested changes to ensure that all changes are authorized before validating them.
- Harden your systems using industry-standard security frameworks like CIS benchmarks and Controls. Reliable hardening standards like CIS Controls provide actionable and specific ways to stop dangerous and pervasive cyberattacks.
- Perform regular risk assessments to identify cybersecurity threats, analyze risks, and decide on measures to reduce or remove them. This approach aids in focusing on vital system hardening tasks while avoiding the less significant ones.
- Develop a configuration management plan that outlines the policies, responsibilities, roles, and procedures that apply when managing your systems’ configuration or when they deviate from the baseline.
- Perform regular software patching in a timely manner to prevent cybercriminals from exploiting security gaps.
- Adhere to the least privilege principle by granting users, applications, or processes only the minimum access needed for their tasks. For instance, software developers do not need privileged access to financial records. Enforcing the least privilege will result in proven security through a reduced attack surface and the elimination of standing privileges. It will also go a long way in reducing the threat of malware and lateral movement attacks. Auditing efforts are also streamlined as the audit scope is smaller. Implementing the least privilege principle enhances security by narrowing the attack surface and removing standing privileges. This significantly lowers the risk of malware infections and lateral movement attacks. The practice of least privilege also simplifies the auditing processes as the scope of review becomes more focused.
- Encrypt sensitive data that is both in transit and at rest if data is compromised.
- Harden your network by implementing firewall hardening strategies to limit open ports to essential traffic only. Further measures include deploying web application firewalls, using secure protocols such as HTTPS and SFTP for transferring data and employing network segmentation to contain any potential security breaches.
- Lastly, backup vital data and crucial configuration settings to enable restoration following a cyber incident. Recovery and restoration processes are frequently the most expensive consequences of an attack.
How Netwrix Can Help
In today’s cybersecurity landscape, threats are evolving rapidly, and system hardening emerges as a crucial defense mechanism to safeguard critical IT infrastructure. This is where Netwrix Change Tracker comes in, empowering organizations to enhance their system hardening processes effectively.
Netwrix Change Tracker simplifies server hardening and configuration management by streamlining the process of establishing and maintaining secure baseline configurations aligned with standards such as the Center for Internet Security (CIS) and the US Department of Defense’s Security Technical Implementation Guide (STIG). By using an advanced system and file integrity monitoring technology, it adeptly identifies any deviation from these baselines, ensuring your configurations remain in compliance. In addition to this, by seamlessly integrating with IT service management (ITSM) solutions, Netwrix Change Tracker promptly alerts administrators about unexpected configuration changes, significantly accelerating incident response with complete change details. Moreover, Netwrix Change Tracker simplifies compliance audits by offering reports that meet the requirements of NIST, PCI DSS, CMMC, STIG, and NERC CIP, making it an indispensable tool for securing servers and streamlining compliance efforts.
Frequently Asked Questions
What is hardening?
Hardening is a cybersecurity strategy that involves strengthening the security of a network component by reducing its vulnerability to attacks. This process includes removing unnecessary software, disabling unused services, applying security patches, and configuring settings to enhance protection. By minimizing potential entry points for attackers, hardening makes it more difficult for unauthorized access to occur.
What is system hardening?
System hardening, a specific form of hardening, focuses on strengthening the security of system infrastructure and internal operating systems. It is a crucial step in safeguarding information technology systems against cyber threats to ensure a higher level of data integrity and confidentiality.
What is hardening in cybersecurity?
In cybersecurity, hardening refers to the practice of securing a system by minimizing its vulnerability surface. The goal is to make the system more resilient to attacks and unauthorized access by minimizing potential weak points that could be exploited by cyber threats. Hardening can be applied to operating systems, applications, networks, and databases to protect against potential cyberattacks.
What is security hardening?
Security hardening involves implementing measures to protect against unauthorized access, data breaches, and other cyber threats. Techniques include updating software, restricting access controls, disabling unnecessary services, and applying security patches, all aimed at making the system more resilient against potential security risks.
What is device hardening?
Device hardening refers to the process of securing computing devices (such as smartphones, tablets, laptops, and servers) by reducing their vulnerability to cyberattacks. This involves implementing security measures that limit potential attack surfaces using techniques such as updating and patching, disabling unused services and features, installing security software, enforcing strong password policies, and encrypting data stored on the device. The goal of device hardening is to protect the device from unauthorized access and ensure the integrity and confidentiality of the data it contains.
What is software hardening?
Software hardening is the process of making software more secure by identifying and mitigating vulnerabilities within it. This involves modifying the software’s configuration settings to strengthen and increase its resilience against cyberattacks. Some of the possible steps include removing unnecessary code, functions, and services; applying security patches; using secure coding practices; encrypting sensitive data; and implementing access controls. The aim of software hardening is to minimize the potential for exploitation and prevent unauthorized access, data breaches, and other security incidents.

