When Windows Server has issues, the first place we go to are the event logs. We want to know what was going on when the trouble began, what applications were running and might have caused it, etc. We are masters at figuring this stuff out.
Now take the same event logs and try to sort them out by what they mean from a security stand point, and most of us wind up looking like a monkey trying to solve a quadratic equation. But there are a lot of things that go on, and you need to know about many of them. In some cases, you might not want to know about tomorrow. You need to know about them right now.
For instance, there’s a very special subset of employees that we need to watch, and that’s our Sysadmins. In most out fits, Sysadmins will have two accounts. There’s the daily “let’s log in and check e-mail” password that we use for routine stuff. Then there’s the privileged account that usually has all kinds of power and authority built in (like being a domain admin for example). It’s these that we might want to keep an eye on. We might want to know what events get triggered by them, and so we’ll take a handful and then show you how to set things up to watch for them.
A couple of events to watch for:
EVENT 4663 – This one is generated when you have a high number of files being deleted. Chances are it’s innocent. It can also be someone who is dumping crucial information and wants to make life difficult for you and/or the company.
EVENT 4724 – Password reset. Again, probably innocent enough. But then it depends on the account having the password reset. Resetting service account passwords is a nice way for an upset sysadmin to spread havoc through the infrastructure.
EVENT 4704 & 4717 – Changes to user rights assignments. Normally we’d expect to see this associated with a ticket request. However, if someone is planning something underhanded, there’s a really good chance they won’t follow protocol to do it. An event like this will often tell you what rights were assigned to a user or account, but it probably won’t tell you who did it. This is one to watch for because a hacker on the inside might try to elevate a service account or an ordinary user account with permissions that will give them access to the system and help them cover their tracks doing it.
EVENT 4719 & 4739 – If you see these, start thinking someone has altered the Audit and Account policies in the system. Often a good prelude to an internal hack.
EVENT 1102 – This is often a big one to watch for and can be a really big smoking gun. This means that someone has just cleared the security log. Again, this can be innocent, but it can also mean someone is trying to cover his tracks. This is a good tripwire that could easily mean that an attack on the network is coming, or it’s already winding down.
So, how do you find out about these events, beyond combing event logs afterwards (which you’ll want to do anyway)? Well, more than a few companies make some great system log monitors, and it will watch for events you tell it to watch for, and will even notify you in real time should certain event occur.
Windows 2008 (and later versions) comes with its own built in means of alerting of certain events. To take advantage of this, just open Windows and go to Task Scheduler. In there, create a Basic Task.
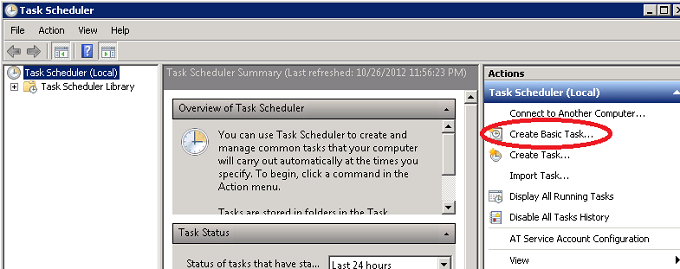
Give your task a name and a short description of what it’s supposed to do:
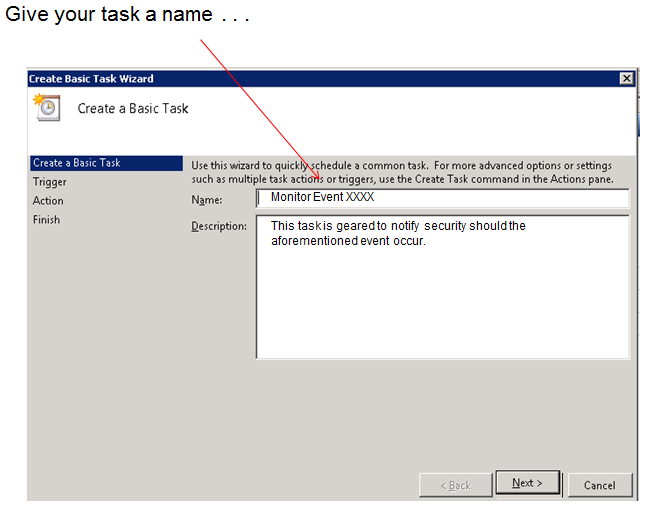
You want to know when a certain event is logged:
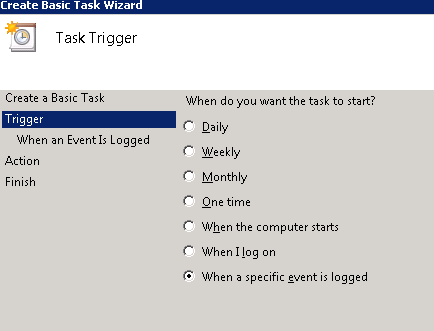
You’ll then want to know what log to look at. Don’t forget to enter the ID of the event you’re watching for:
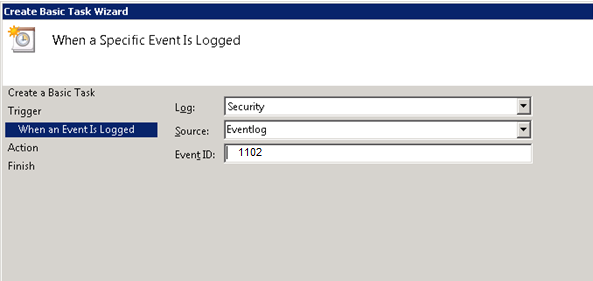
You probably want it to at least send you an email:
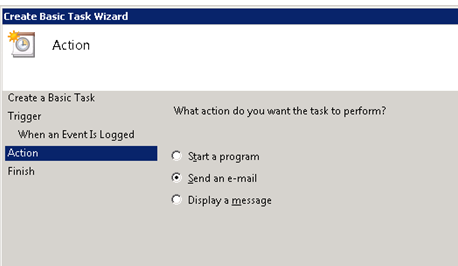
And remember to set things up so the message is correct:
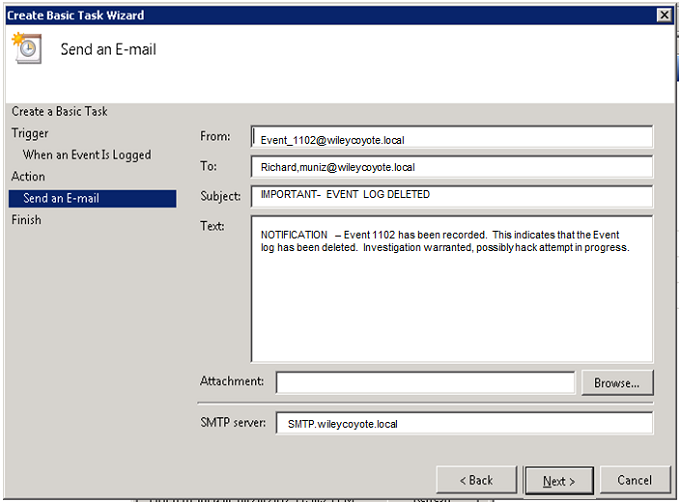
Click “Next” and you’re done.



