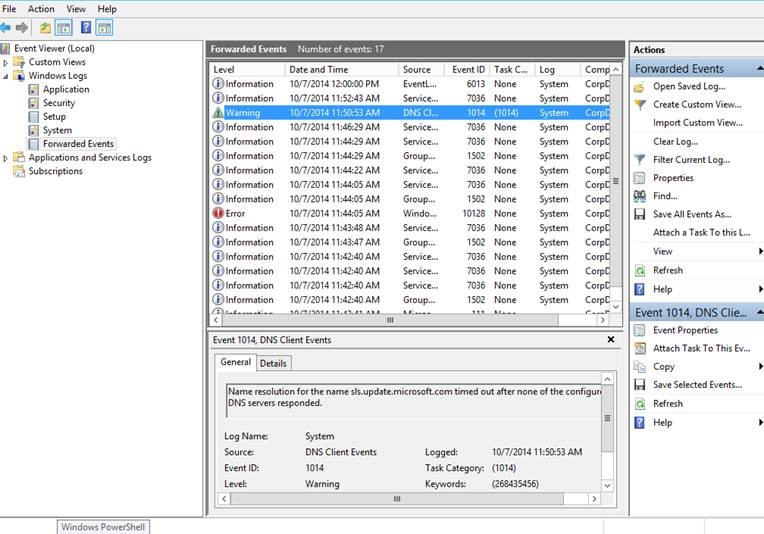
I love Active Directory auditing. I love it because with just a couple clicks of the mouse I can easily create a policy that immediately gets applied to 500 servers that begins recording useful information on about everything that goes on involving those servers. What I hate about AD auditing is that this useful information is stored in 500 different locations; in the Security event log of each server. There’s no good way to retrieve all of these events all at once unless you write a PowerShell script or use some other product to do so. We need a way to bring all of these events into a single place. Luckily, we have the free feature that comes with Windows known as Event Log Forwarding.
Introduced in Windows Server 2008, event log forwarding brought forth a native and automagical way to get events from multiple computers (event sources) into one or more machines called collectors. The concept is simple. The collector collects or pulls events from a number of source computers into a central event log called Forwarded Events.
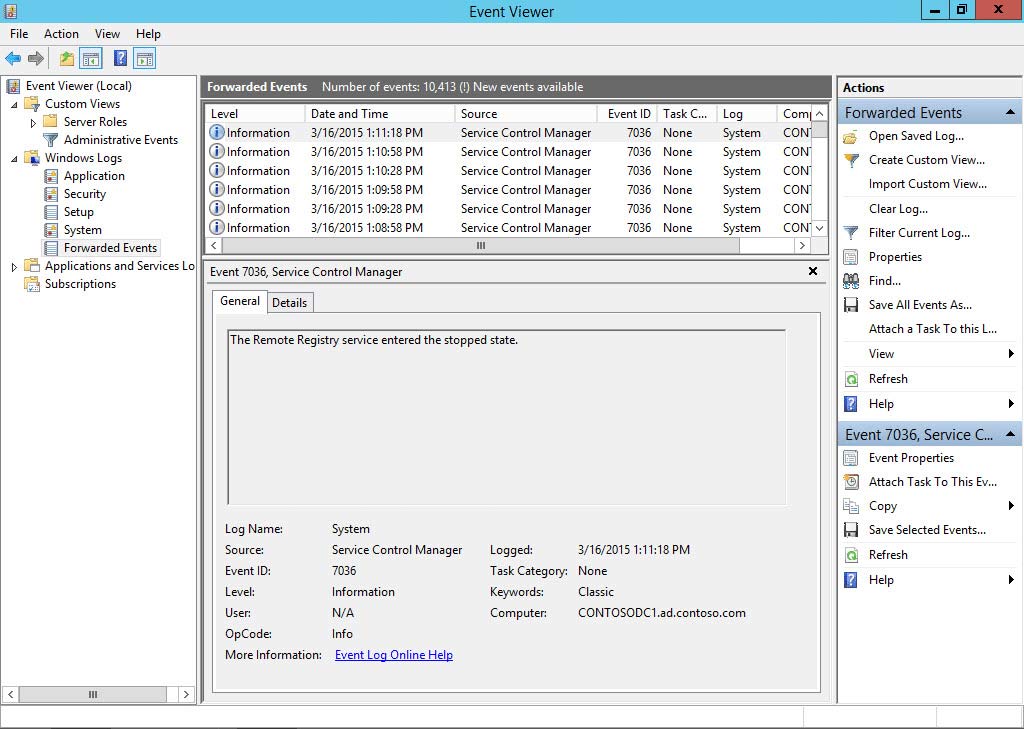
Let’s check out how to get a single event collector to collect logs from a single source computer. I’ll leave it up to you to get this rolled out enterprise-wide.
Enable WinRm on Source Computers
First and foremost, you’ll need to ensure WinRM is enabled on the source computers. There are many ways to do this such as via GPO or by simply doing a winrm quickconfig on the source. Either way, you’ll need to ensure it’s enabled and the appropriate firewall exceptions are added. That’s it for the source computer. No more configuration needed!
Allow the Event Collector to do it’s Job
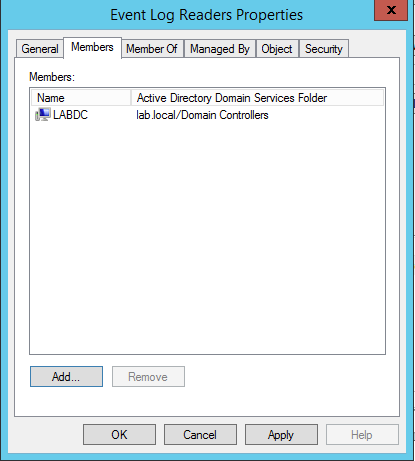
Next, you’ll need to ensure your collector’s computer account is in the Event Log Readers group in AD.
Set the Windows Event Collector service to Auto-Start
Since Windows Event Collector service is disabled by default. We need to ensure it’s running and set to autostart. To do this, we can simply run wecutil qc which will do both for us quickly.

Create the Subscription
Next, we’ll need to create the subscription on the collector. Fire up the event log viewer, right-click on the Subscriptions node and click on Create Subscription.
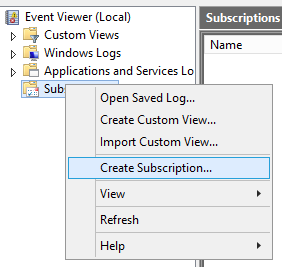
You will then be to a spot to where you can add the source computers.
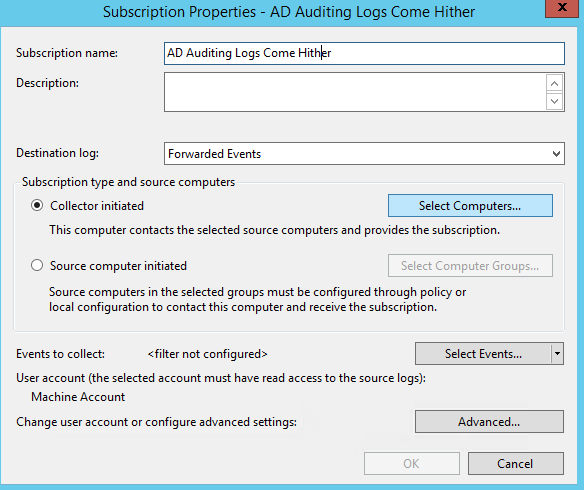
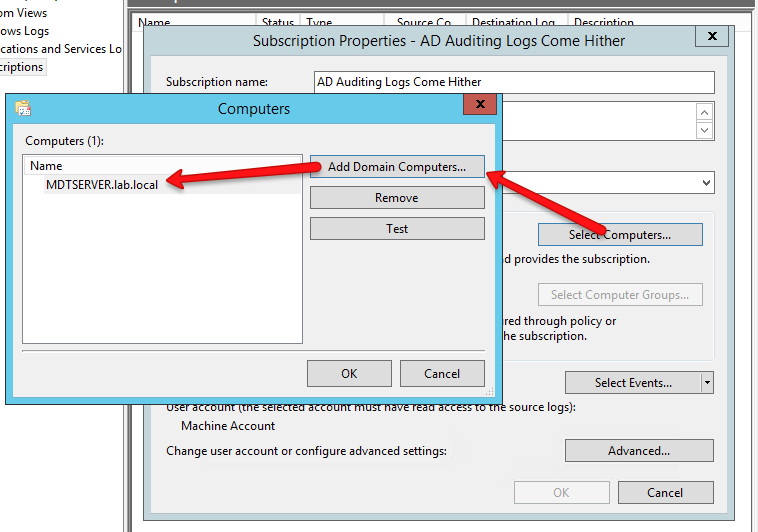
You’ll then select all the source computers you’d like to collect events from.
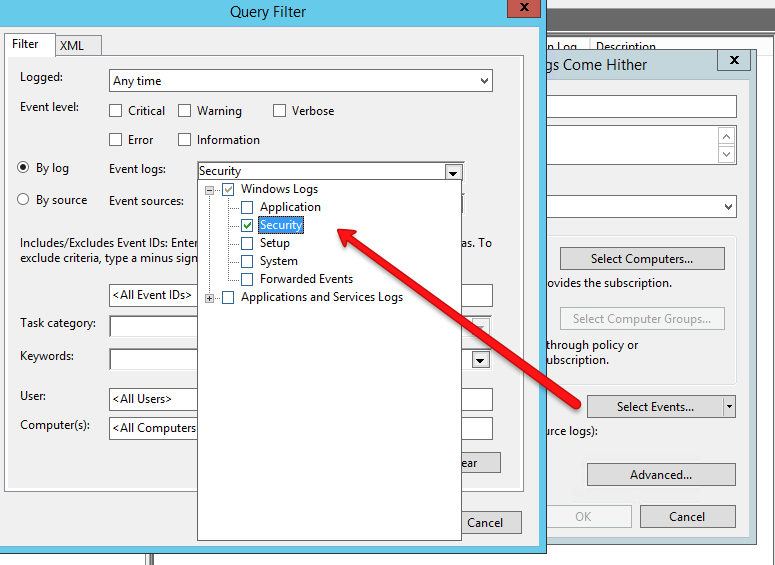
Now, let’s say you don’t want all of the events from the source computers. Maybe you just want some of them. In my case, I want to only bring in my AD auditing events and these are only logged in the Security event log. To do this, you’d click on Select Events and build your filter.
Once you’re done, click OK a couple times and you’ll see your subscription created in the Subscriptions node.
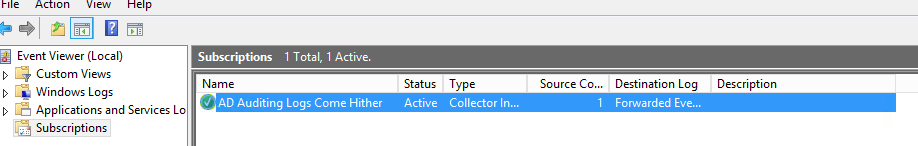
That’s it! If everything goes as planned you should now start to see your events showing up in the Forwarded Events event log.