In 2015, Gartner predicted that 95% of security failures in the cloud through 2020 will be the customer’s fault. The new Netwrix 2018 Cloud Security Report supports this prediction, noting that employees were considered responsible for 58% of security breaches in 2017, even though most attacks were external. More broadly, the report explores the current state of security in the cloud and the tactics organizations use to mitigate risks. Here are some of the most interesting findings.
Cloud security threats: insiders take the stage
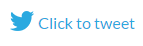
88% of the 853 survey respondents store customer, employee, financial, and other sensitive data and intellectual property in the cloud. Organizations weighed the pros and cons, and decided that the benefits of the cloud were sufficiently compelling.
45% of organizations see their employees as the main threat to cloud security
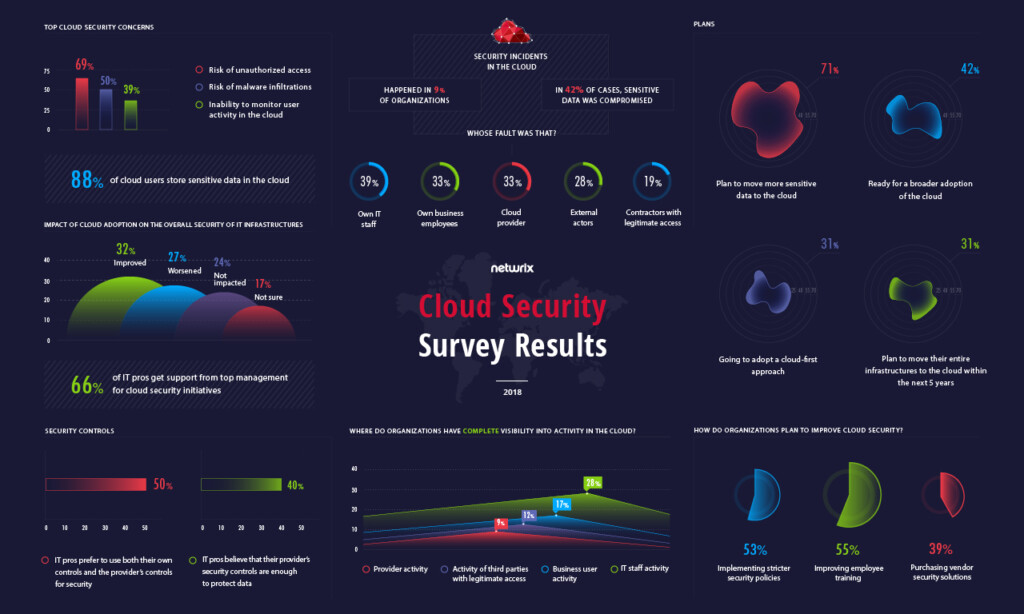
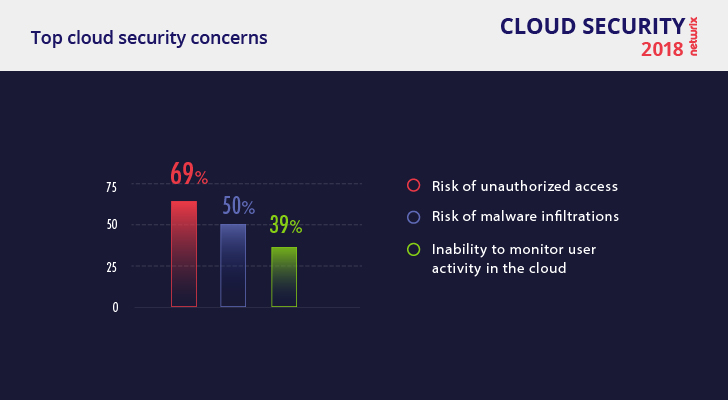
However, cloud security is a burning issue. About 88% of respondents believe that a data breach in the cloud would impact their business. Just like last year, cloud customers are most concerned about the risks of unauthorized access (69%) and malware infiltrations (50%). But the inability to monitor employee activity in the cloud (39%) replaced DDOS attacks as the third most common security concern.
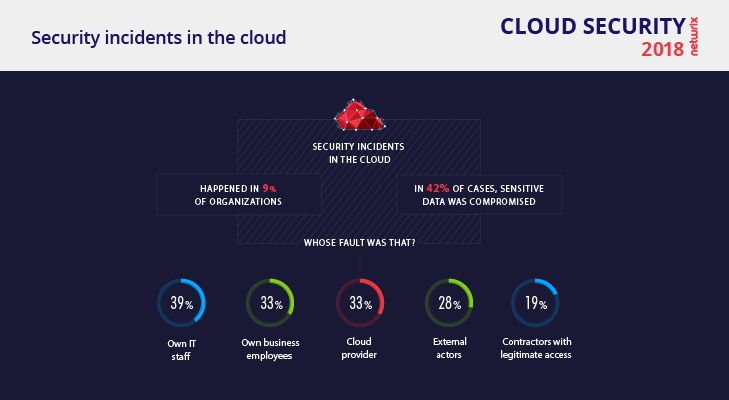
Fear of insiders is nothing new. However, it received more attention in 2017. Almost 58% of organizations that had security incidents over the year blamed them on insiders. It is a curious finding at first blush, since the majority of organizations (78%) fell victim to attacks that were initiated externally, including malware. But it actually makes sense, because a successful attack needs favorable conditions: vulnerabilities, knowledge about weaknesses, or just a negligent or unaware insider. Ransomware installed through phishing is a simple example of such attacks.
Another interesting finding is that about a half of all respondents (45%), whether or not they experienced a security incident, still see their own employees as the biggest threat to security.
Preferred cloud security controls
Even though most organizations are well aware of the insider threat, they are still not prepared to deal with it.
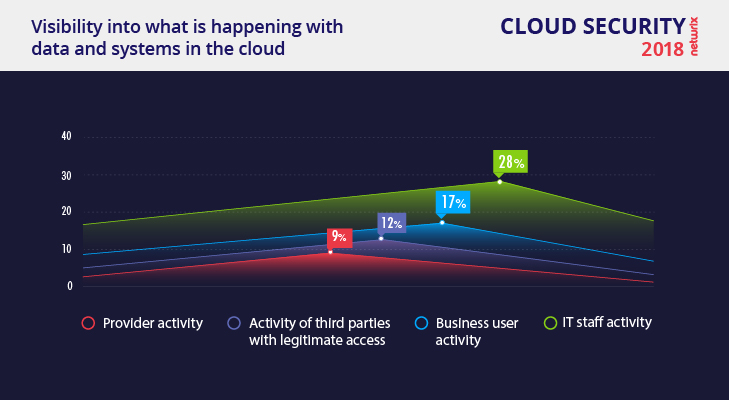
Only 28% of organizations have complete visibility into IT staff activity
The majority of respondents have only partial visibility into what is happening in the cloud, and only 28% of organizations have visibility into IT staff activity. Even fewer organizations can verify the activity of business users, third parties with legitimate access and cloud providers. The saddest part is that some organizations are not even trying to get any visibility, especially on the cloud provider or contractor side.
What security measures organizations are organizations taking to secure their assets in the cloud? What controls do they rely on? Although most respondents (75%) say that their cloud provider’s security controls are equal to or better than their own on-premises controls, they are in no rush to blindly trust their provider’s controls. On average, 50% of respondents use both their provider’s controls and their own controls for incident prevention, detection, investigation and response. Provider-based controls for incident investigation and response are least trusted, with more organizations preferring either their own controls or both their own controls and their provider’s controls for these areas.
A small number (5%) of organizations do not use controls for each of the four stages of dealing with a security incident (prevention, detection, investigation and response), and 2% of respondents do not use any of the controls at all, which is much less than the share of organizations that do not store any sensitive data in the cloud (12%). This means that organizations tend to take security measures regardless of the sensitivity of the data they store in the cloud. This practice may be the first step to broader cloud adoption in the future or a sign of good IT hygiene.
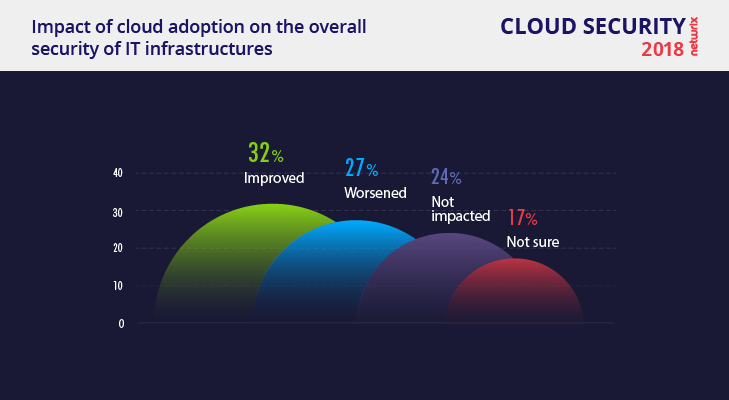
Although the majority of organizations have been trying to improve security and address the most common issues, respondents disagree about whether cloud adoption had a positive or negative impact on the security of their IT environments. While 32% of IT pros claim it made their IT infrastructures more protected (41% in 2016), almost as many (27%) complain it reduced overall security (11% in 2016).
Cloud security: key initiatives in 2018
The problem of poor security is not in the lack of necessary controls. Providers offer hundreds of security controls (for instance, AWS offers 1,800 to choose from). The cloud requires organizations to take a new approach to security and make additional efforts. What works on premises may not be applicable or sufficient in the cloud. To properly protect data in the cloud, IT departments may need extra budget and skilled human resources. However, only 66% of our respondents have support of the top management to achieve their cloud security goals.
Employee training (55%) and enforcement of stricter security policies (53%) top the list of urgent measures aimed at strengthening security
With or without support from top management, IT departments have to ensure data security. There are many ways to do it, but the most popular are:
- Holding employee training
- Tightening security policies
- Deploying security software
- Hiring new IT security staff
Most companies (55%) start with employee training. IT pros understand that the human factor cannot be eliminated. Therefore, they do their best to educate business users and IT team members. The best advice here is to focus on current threats and explain how not to fall into the common traps of attackers, whether they are outsiders or colleagues.
Almost the same number of companies (53%) plan to toughen their existing security policies. Education alone is not enough. Companies should regularly update their policies with best security practices as the threat landscape evolves, and make sure employees at all levels of the organization follow them.
Other steps will include deploying security automation solutions offered by software vendors (39%) or using in-house solutions (36%). Some companies (17%) see hiring more security professionals as a key initiative for 2018. Finally, 16% of IT pros are satisfied with the state of things and are not going to introduce any new security measures right now, and a fraction of respondents are going to move their data back on premises, as they turned out to be unprepared for the challenges of cloud adoption.

How to improve cloud security
Clearly, this list is not exhaustive. It’s wise to also consider these steps:
- Devote some of your security efforts to the insider threat. Make sure you are aware of what is happening in your environment and can spot malicious and suspicious activity, as well as mistakes and failures to follow established security policies. Regular monitoring and activity analysis will give you more control over the IT environment so you can better protect it.
- Communicate the security risks and their impact to top management. Surprisingly, top managers do not always understand the possible consequences of security breaches. They may think this is up to IT to maintain security and deal with business users, while they focus on cutting expenses or raising stock prices. But in fact, this attitude makes realization of security initiatives more difficult and may have dire consequences, both for the business and for them personally. In the wake of several recent data breaches, such as Equifax and Yahoo, C-level managers like the CISO, the CIO and even the CEO had to resign. Your manager may find this fact interesting and change their mind about their responsibility for cyber security.
View the full 2018 Cloud Security Risks infographics:
View the full infographics (click on the image to open a high resolution version in a new tab).
Want to know more about cloud security? Check out the full version of the Netwrix 2018 Cloud Security Report!