We continue the “Deep Dive” series. In it you might find the answers to some of your technical questions. The industry experts will provide their insights on several topics and research some new features of most popular applications. The first article of the series can be found here. Also, read more about Exchange 2013 CAS configuration (Part 1, Part 2) and using PowerShell for RBAC permission customization! You are welcome for comments and discussion!
Every Exchange organization has multiple exchange administrators where most of them have full control over the exchange organization. It is extremely difficult to trace out who made changes and what changes have been made on the Exchange organization. Recently, I faced a situation where someone had created a new authoritative accepted domain without informing anyone and this had obstructed the mail flow between two forests. We could not trace the source since Administrator auditing had not been enabled.
Admin Audit Logging Configuration:
In Exchange 2013, Administrator Audit logging is enabled by default and it logs all the cmdlets executed directly on the Exchange Management Shell (EMS) and Exchange Admin Center (EAC), except the cmdlets starting with Get- and Search- . This is because the objective of the Admin audit logging is to audit the modified objects in an Exchange organization rather than just view or search.
Shown below is the command to verify the Admin audit logging settings on Exchange 2013 EMS
Get-AdminAuditLogConfig | fl *log*
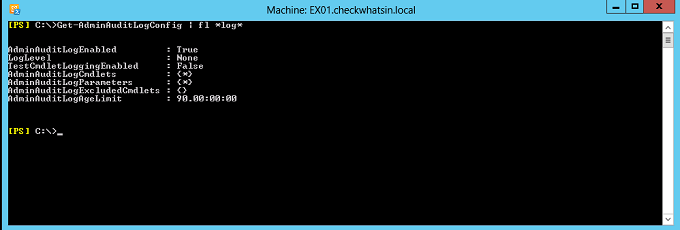
Given below are a few details of each of the Admin Audit log configuration:
AdminAuditLogEnabled: It is enabled by default and set to $true. To disable the Admin audit logging, it needs to be set as $false.
LogLevel: This parameter is used to define the logging entries level. It has two values, ‘none’ and ‘verbose’. By default, it is set to ‘none’, which only logs the cmdlets name, cmdlets parameter, who ran the cmdlets, when the cmdlets had been run and executed, along with details of the server. If the ‘verbose’ mode is set, then it logs both the old and new values in the log entries. In addition to the default logging, it also logs the properties including their old and new values.
TestCmdletLoggingEnabled: This parameter is to define whether or not to log Test- cmdlets. By default, Test- cmdlets is not logged. Examples of test cmdlets: Test-Outlookconnectivity or Test-Activesyncconnectivity. It is recommended to enable it only for the short duration when required, since it can generate too many logs.
AdminAuditLogCmdlets: This parameter is to define which admin executed cmdlets can be logged. By default, it is set to log all the cmdlets executed by the administrator and it set by the value “*”.
AdminAuditLogParameter : This parameter is to define the administrator audit logging with parameters passed with the cmdlets. By Default, this is set to log all the parameter and it is set by the value “*”.
AdminAuditLogAgeLimit: This parameter is to define the age of the audit logs to be stored. By default, it has been set to 90 days, after which the log entries get deleted. Based on the requirement and size of your organization, you can modify the Age limits. You can specify the number of days, hours, minutes and seconds in the format dd.hh:mm:ss (E.g. 180.00:00:00)
Auditing Admin Logs:
Audit logs are stored in the hidden arbitration system mailboxes and can be accessed only via Exchange Admin Central (EAC) or Search-AdminAuditlog or New-AdminAuditLogSearch cmdlet. It cannot be accessed by any other mode.
Auditing Admin logs via EAC
EAC allows audit logs with multiple options.
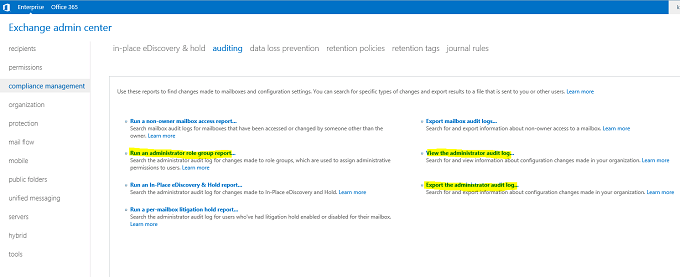
Shown below are the details of the same which can be found at EAC -> Compliance Management -> Auditing:
- Run as Administrator Role Group Report
- View the Administrator audit log
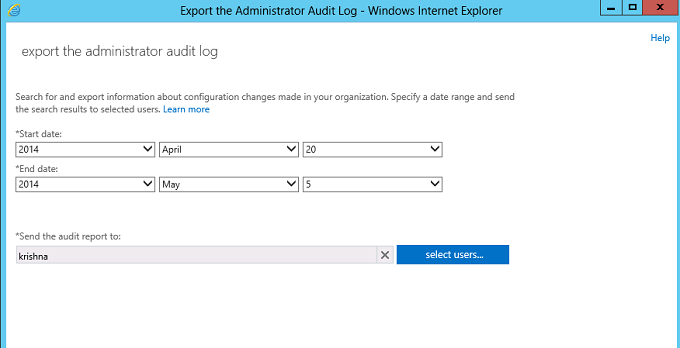
- Export the Administrator audit log
Shown below is the search on the Administrator role groups with the result for adding member “Krishna” into the Role group “Discovery Management”.
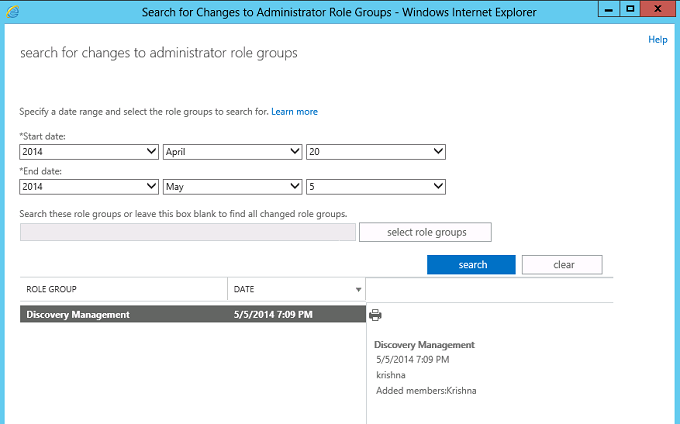
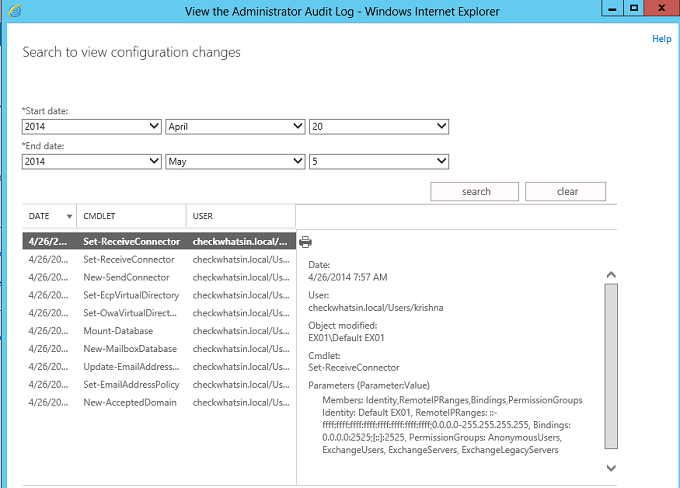
Shown below is the details of the same:
Auditing Admin logs using Search-AdminAuditlog cmdlet
Search-Adminauditlog cmdlet searches the logs based on the parameter specified and displays on the screen.
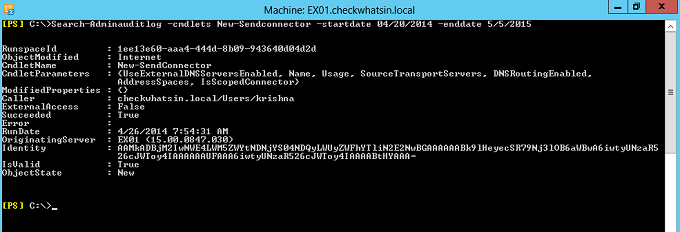
Shown below is a sample cmdlet which can be used to search the logs for their execution details of the cmdlet new-Sendconnector on a particular day.
Search-Adminauditlog –cmdlets New-Sendconnector -startdate 04/20/2014 -enddate 5/5/2015
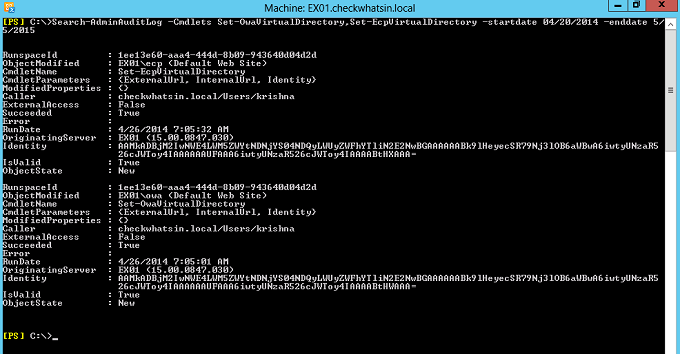
Shown below is the cmdlet to search the logs with the details of Set-OWAVirtualDirectory and Set-ECPVirtualDirectory cmdlet execution with the specified time line
Auditing Admin logs using New-AdminAuditlogsearch
The New-AdminAuditLogsearch is similar to the Search-AdminAuditlog cmdlet; however, instead of displaying the results on the screen, it performs the search and then sends the result in XML format to the recipient specified as the parameter.
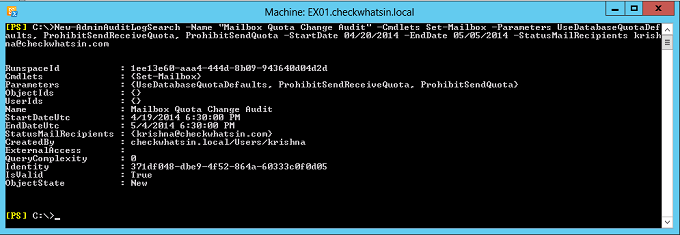
New-AdminAuditLogsearch cmdlet search for all the logs matching the below conditions and send the mail to krishna@checkwhatsin.com:
- Cmdlets : Set-Mailbox
- Parameters: UseDatabaseQuotaDefaults, ProhibitSendReceiveQuota, ProhibitSendQuota
- StartDate: 04/20/2014
- EndDate : 05/05/2015
New-AdminAuditLogSearch -Name “Mailbox Quota Change Audit” -Cmdlets Set-Mailbox -Parameters UseDatabaseQuotaDefaults, ProhibitSendReceiveQuota, ProhibitSendQuota -StartDate 04/20/2014 -EndDate 05/05/2014 -StatusMailRecipients krishna@checkwhatsin.com
Admin audit logging totally relies on AD replication. Depending on the replication settings, the changes may not be logged immediately and available for the search. Logs should be available for the search once the replication is completed. In addition to the logging of Exchange cmdlets, you can also add the manual log entry. It could be used to add manual log using the cmdlet Write-AdminAuditLog with theCommentparameter. It could be used, when custom script is started and ended, during change activities, during start and end of any maintenance activity. These logs can be searched via EAC auditing page or using the Search-AdminAuditLog or New-AdminAuditLogSearch cmdlets. It is recommended to keep the Admin audit settings default, which logs all the commands except test-, get- and search- cmdlets.
I hope you find this article useful in the production environment.