A routine sysadmin task that PowerShell lends itself to is parsing data and text files, and the Windows event logs use XML formatted information that can be easily parsed using the Get-EventLog and Get-WinEvent PowerShell cmdlets. In this article I’m going to show you how to get started using PowerShell to parse the event logs, and explain the differences between the two cmdlets to make the event log monitoring easier for you.
Get-EventLog vs. Get-WinEvent
Get-EventLog was the first PowerShell cmdlet that Microsoft included in Windows to facilitate working with the event logs. As of PowerShell v2.0, the –ComputerName parameter was added so that it could also be used to query the logs on remote computers. But Get-EventLog has some limitations that led to the introduction of Get-WinEvent in PowerShell version 2. Get-EventLog only works against the System, Application, and Security logs, and not the new ETL logs (Event Trace Logs) that were introduced with Event Tracing for Windows (ETW) in Windows 7, which contain information from a much wider variety of sources than the traditional logs that have been present since the days of Windows NT.
The Get-EventLog cmdlet doesn’t allow the returned results to be filtered directly, which means that the dataset must be parsed by piping the results to the Where-Object cmdlet for further processing. This might not be too much of a problem if you only want to work with the logs on the local machine, but can become a problem when querying remote computers, as the logs need to be transferred across the network before they can be parsed, which takes extra time and generates unnecessary network traffic if the logs are quite large.
Therefore, if you really want to return the entire contents of a log, and don’t need to work with it further, using Get-EventLog is an option, but Get-WinEvent was developed to address the shortcomings of Get-EventLog, is equally capable of returning entire logs, and going forwards is likely the cmdlet that Microsoft will support for working with the event logs.
PowerShell Event Log Basics
Let’s start by returning the entire contents of an event log using Get-WinEvent. Open a PowerShell prompt, type the command line below and press ENTER.
Get-WinEvent –LogName application
This will output the entire contents of the Application log to the CLI. In practice, it’s likely that you’ll only want to see the most recent events, and the easiest way to do that is by adding the –MaxEvents parameter:
Get-WinEvent –LogName application –MaxEvents 10
The above command line displays the last ten events recorded in the Application log. Get-WinEvent can be used to parse the ETL logs, but you need to find the log name first. To list all the available logs, use:
Get-WinEvent –ListLog *
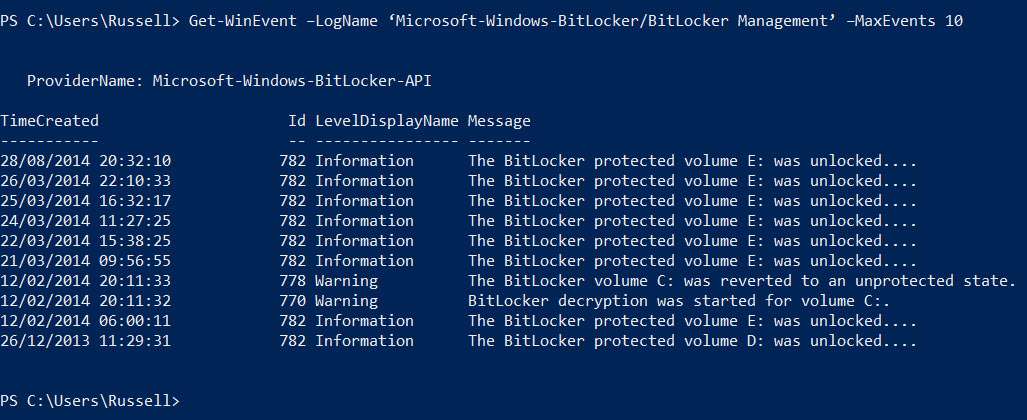
And then look for the desired log name, for example, the BitLocker Management log can be returned using the command below. Note that apostrophes are required at the top and tail of the log name because it includes a space:
Get-WinEvent –LogName ‘Microsoft-Windows-BitLocker/BitLocker Management’ –MaxEvents 10
You can also get detailed information about a specific log as shown here by adding the Format-List cmdlet:
Get-WinEvent –ListLog ‘Microsoft-Windows-BitLocker/BitLocker Management’ | Format-List -Property *
If you want to perform any of the above tasks on a remote computer, just add the –ComputerName parameter, followed by the computer name:
Get-WinEvent –ListLog ‘Microsoft-Windows-BitLocker/BitLocker Management’ –ComputerName contososrv1 | Format-List -Property *
Don’t forget that you must hold the necessary permissions to read the desired log, whether it’s on the local computer, or a remote device.
And this is where you can test your memory: make sure to pick the correct answer!



