As an Active Directory administrator you’re probably familiar with important groups like Domain Admins, Schema Admins and Enterprise Admins. When an account is a member of one or more of these groups that account has some major power in your AD environment. Just like the old saying goes, “With great power comes great responsibility”, members of these groups must be trusted. You’re in for a bad day whenever an intruder or disgruntled employee becomes a member of an important group like these. It behooves you to monitor important groups like a hawk. But how? I’m glad you asked.
One way to monitor important Active Directory groups is through a scheduled task and a Windows PowerShell script. Using the Active Directory module in the Remote Server Administration Tools (RSAT) package you can remotely query members of any AD group. Combine that capability with running on a recurring schedule through a scheduled task you’ve got yourself a nice, homebrew auditing solution.
To do this will require the script to run the group membership queries as well as creation of the scheduled task itself which I will also create via a script. Let’s get started.
Before we can be notified of changes we first need to just query group membership to begin with. This is very easy with the Get-AdGroupMember PowerShell cmdlet. Using this cmdlet you can simply use the Identity parameter and specify a group name and it will immediately return all of the members inside of that group.
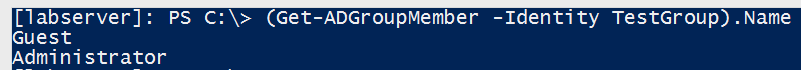
You can see in my example I have a group called TestGroup and two members inside; Guest and Administrator. Now I’ll remove the Guest account as a test and run it again.
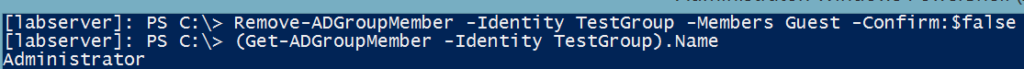
The only member in that group now is Adminstrator. Great! We’ve now tested the scenario of removing a member. Now, let’s test to see if I can get the change in membership if I add a member.
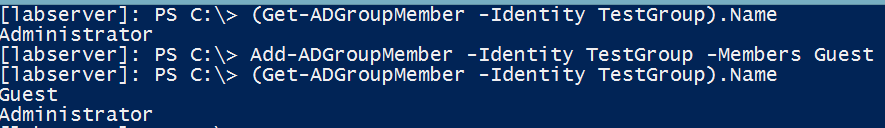
Success! I’ve now confirmed I can detect if an account has either been added or removed from an AD group. This is all well and good but I’m not about to run this on my own over and over throughout the day just to see if something has changed. Automation saves the day!
Now, let’s add a group member again and this time, instead of simply eyeballing the differences let’s add some code in there for PowerShell to detect the difference. In this example, I’ve added the Guest account to the TestGroup again but this time captured the state of the group before and after the change in variables. By doing so, I now have the ability to do a simple comparison and can easily see that the Guest account was added.
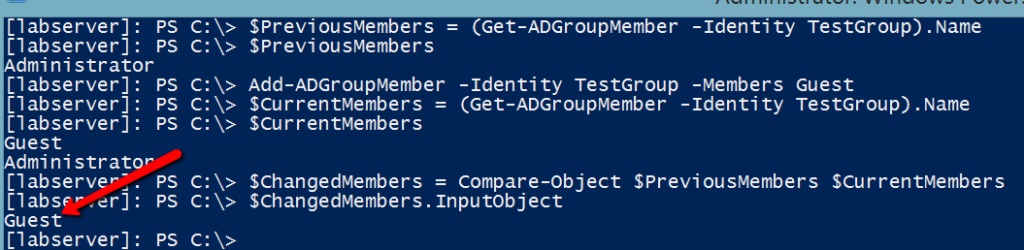
The exact same tactic can be used for any member removed as well.
We’ve created the code to gather group membership in two different states and can now also compare the two for group membership changes. What next?
The next step is to roll this code into a script where this can be taken to the next level. I’ve created an example script to demonstrate this concept. The script takes this concept and runs with it. The script is just an example of what can be done with this code. It not only detects the change but can do so for multiple groups, writes a log file with status information and also keeps a CSV file with group membership to be saved to disk to be saved across reboots.
Finally, there is a short page on detecting on who added a user to a domain admins group. This takes the concept yet again to an entirely different level since the script I’ve provided here just detects the change not who actually did it. Netwrix Auditor has all this capability what we discussed today builtin already. There’s no need to fiddle with scripts unless you really want to. With their Netwrix Auditor software product auditing when a user is added or removed from an AD group is trivial. I suggest you check it out if you’d like this and much more advanced auditing capabilities.



