Since Windows Server 2008, Microsoft has enabled administrators to create multiple password policies for domains in Active Directory. In a modern cloud-enabled environment, it is important that higher privileged accounts are locked down using policies and audited regularly.
Here’s a step by step guide as to how to enable Multiple Password and Account Lockout Policies in your environment. This is also known as a fine-grained password policy.
Don’t forget that you always can use free AD account tool from Netwrix to investigate
user account lockouts faster.
Before attempting this, please make sure that your domain and forest functional level is at least 2008 or higher and that you are logged in as a Domain Administrator (or higher).
Active Directory stores these new password policies in a Password Settings Container (PSC) – this is where we will start:
- Open adsiedit.msc from the Start Menu
- Right click ‘ADSI Edit’ in the left pane and select ‘Connect To’
- In the ‘name’ box, enter the domain name that you wish to implement this on and click OK
- Expand out the left-hand tree: DC=Your Domain -> CN=System -> CN= Password Settings Container
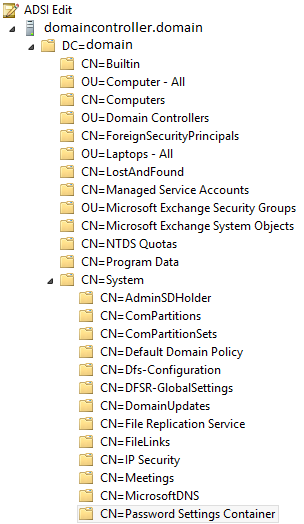
- Right click the empty space on the right and select ‘New’ -> ‘Object’ -> msDS-PasswordSettings -> Next
- Give this policy a name, here I’m calling it ‘Chief Executives’ -> Next
- For each of the attributes that the wizard prompts you with, fill in an appropriate value:
- Password Setting Precedence – 0 upwards
- This is the order in which Password Policy applies to a user: a LOWER
number indicates a HIGHER priority (will override others).
- This is the order in which Password Policy applies to a user: a LOWER
- Reversible Encryption Enables – true or false
- Store the password using reversible encryption – not recommended!
- Password History Length – 0 to 1024
- How many passwords are remembered after users have changed them.
- Password Complexity Enabled – true or false
- The password must meet complexity requirements (ie must have numbers, symbols, upper and lowercase)
- Minimum Password Length – 0 to 255
- Minimum Password Age – a timespan written in dd:hh:mm:ss or (none)
- How long the user must keep a password before being allowed to change it (stops changing, then changing back again)
- Maximum Password Age – a timespan written in dd:hh:mm:ss or (never)
- Lockout Threshold – 0 to 65535
- How many passwords can be entered incorrectly before the account is locked
- Lockout Oberservation Window – a timespan written in dd:hh:mm:ss or (none)
- The time in which to look at previous incorrect passwords and lockout if required.
- Lockout Duration – a timespan writeen in dd:hh:mm:ss or (never)
- How long to lockout an account for once the bad password count has been reached
- Click ‘Finish’, then right click the new password policy and click ‘Properties’
- Find the attribute ‘msDS-PSOAppliesTo’ and double click, then ‘Add Windows Account’
- Password Setting Precedence – 0 upwards
Specify the groups or users that this password policy should apply to:
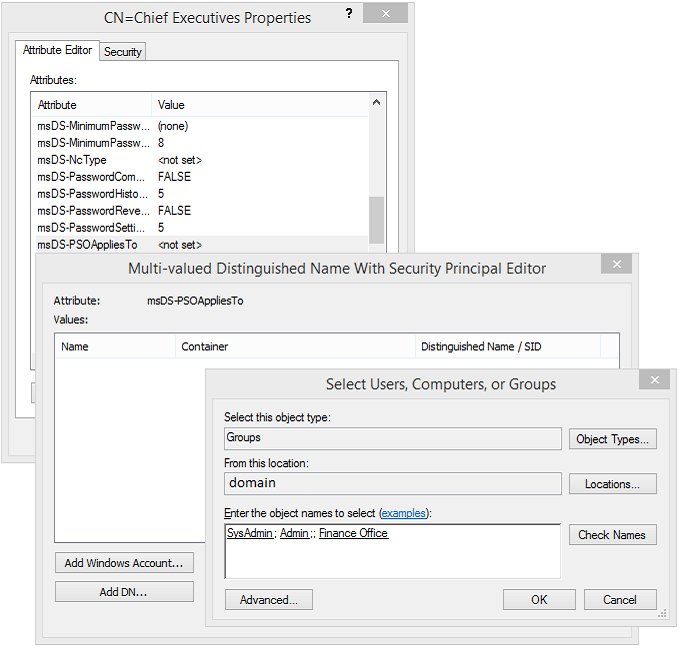
- Press OK all the way out when you’re done!
Once your new password policy is replicated to other domain controllers, it should be enforced almost instantly.
If you are lucky enough to have a Windows Server 2012 domain, or a Windows 8 or higher computer with Remote Server Administration tools installed, this process is somewhat easier:
- Open Active Directory Administrative Centre and connect to your domain
- Navigate to the same location as within ADSI: Domain -> System -> Password Settings Container
- Right Click and Choose ‘New’ -> ‘Password Settings’
A dialog will appear with mostly the same options as described above, but with less control over some of the durations (for example, you can’t set a duration in hours or minutes for minimum/maximum password age.
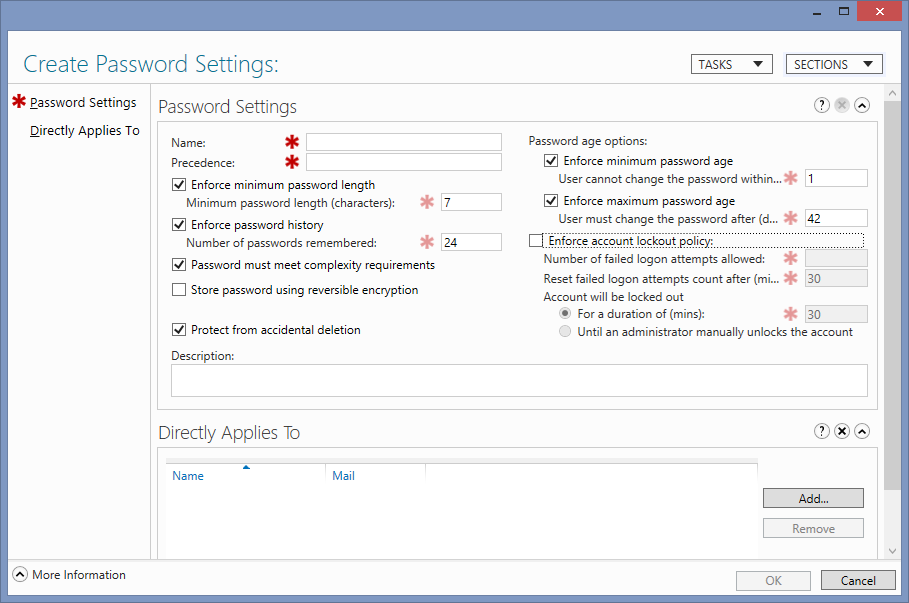
- Set your options and then add the users / groups that this password policy should apply to, then press OK.
Alternatively, you can do the whole lot in two PowerShell command as follows…
Create the Password Policy:
New – ADFineGrainedPasswordPolicy – ComplexityEnabled: $true -LockoutDuration: “00:30:00” – LockoutObservationWindow: “00:30:00” – LockoutThreshold: “5” – MaxPasswordAge: “42.00:00:00” -MinPasswordAge: “1.00:00:00” – MinPasswordLength: “7” -Name: “FriendlyNameHere” – PasswordHistoryCount: “24” – Precedence: “5” -ReversibleEncryptionEnabled: $false – Server: “domaincontroller.domain.local”
And apply it to a group or user:
Add – ADFineGrainedPasswordPolicySubject – Identity: “CN=FriendlyNameHere, CN=Password Settings Container, CN=System, DC=domain, DC=local” – Server: “domaincontroller.domain.local” – Subjects: “DNPathToUserOrGroup”
Again, descriptions of the attributes are above.
I would highly recommend setting up Fine-Grained Password Policies – here are the 4 tiers we have setup:
- Guest and ‘Throwaway’ Accounts
– Simple passwords allowed, more than 5 characters, no expiry - Regular Staff
– Simple passwords allowed, more than 12 characters, 30 day expiry - Finance and Confidential Material Staff
– Complex passwords, more than 12 characters, 30 day expiry, 12 passwords remembered - ICT Staff and Administrators
– Complex passwords, more than 12 characters, 14 day expiry, 12 passwords remembered