Security permissions in Active Directory can be a tricky topic. Not only does Microsoft hide them from you by default in Users and Computers, there is also no built-in tool to get an overall picture of how permissions have been applied to AD.
In this article, I’ll take you through the basics of delegating, removing permissions, using built–in tools to find permissions that have been delegated, and finally a custom PowerShell script that scans AD.
Why Delegate?
Imagine you’re the head of a large company with several departments: finance, HR, sales, upper management. If every user who forgot their password had to call the IT helpdesk, you would be swamped with calls.
Instead, you could delegate permissions to the head of each department so that he or she can reset his or her own team’s passwords.
Another classic use case for delegation is the ability for staff to send emails as each other—either a shared mailbox, or a PA sending email on behalf of his or her boss.
Give everyone Domain Admin?
You might’ve thought—okay, let’s give each department head Domain Admin permissions, then they can reset the passwords when required.
Whilst this is technically true, they would then be able to do anything you can do—including accessing user data. Data breach in the making!
How to delegate permissions in AD
The correct way of achieving this of course is by using Delegation. This will allow you to individually select permissions that you want to give away.
1. Open up Active Directory Users and Computers and connect to your favourite test domain.
2. Right click on the department Organisational Unit that you wish to give permission to reset passwords.
3. Find the ‘Delegate Control’ option (this should be the first option in the list). Click this and press Next.
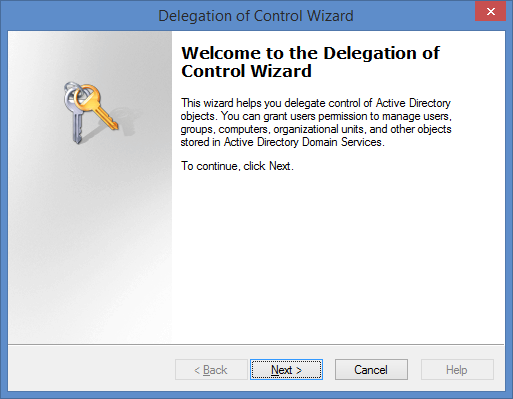
4. You are now prompted to choose users or groups to whom you wish to delegate control—these are the people who you want to be able to perform a task.
It is HIGHLY recommended that you create a security group for each set of permissions that you are delegating (i.e., one for ‘Sales – Password Reset Ability’, ‘HR – Password Reset Ability’). This allows you to very easily add/remove users from these groups in the future, rather than messing around with permissions directly.
5. Go ahead and add in a group. (In the figure below I’ve added in our senior management team.)
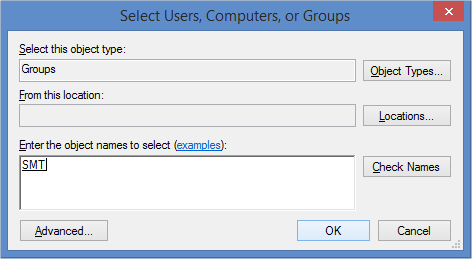
6. Press next and then pick the option ‘Reset user passwords and force password change at next logon’.
7. Press next and then finish—you’re done!
Removing Delegated Permissions in AD
Now that you’ve completed the wizard, you might be wondering how you check that you did actually delegate permissions and how to remove them again.
1. From Users and Computers, press the View menu and make sure ‘Advanced Features’ is ticked.
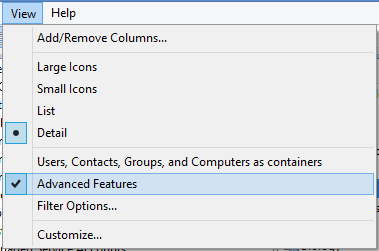
2. By ticking this box, you can see the security tab when you choose Properties on objects in Active Directory.
Right click on the same OU that you just delegated permissions and choose Properties, then the Security Tab.
3. Choose ‘Advanced’ and then scroll up and down until you find the group to whom you just gave permissions. You should see the ‘Reset Password’ permission listed under ‘Access’.
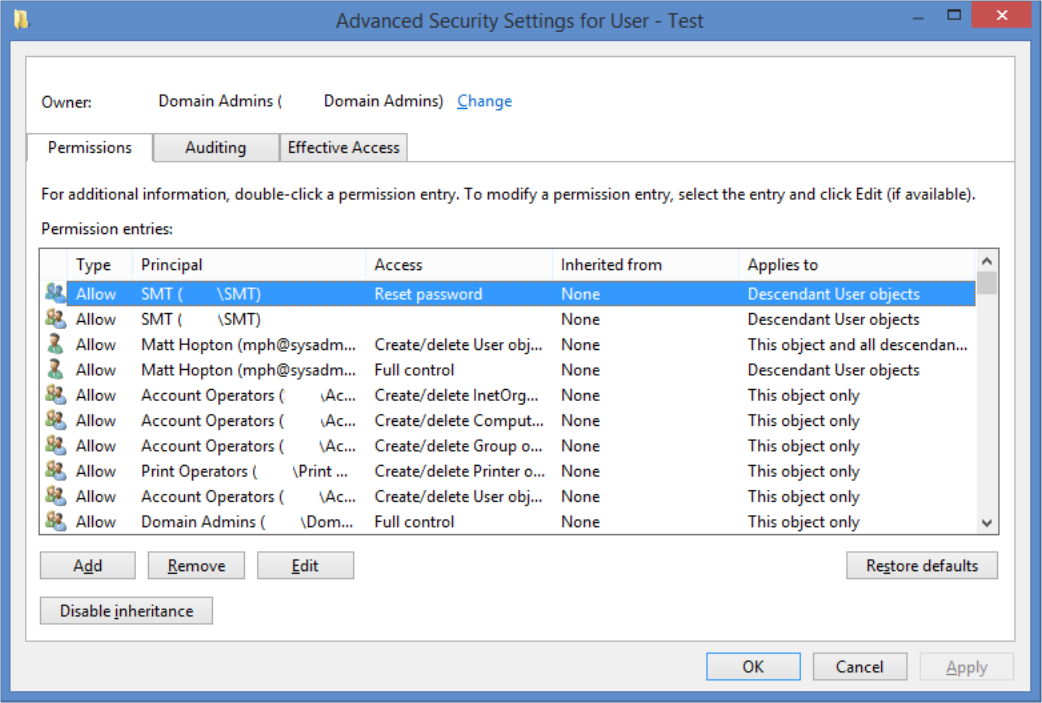
4. If you wanted to remove this permission, you could select it and press Remove, but leave it in place for now and press Cancel.
As you can see, finding delegated permissions is quite hard—especially when you consider that you can delegate not only to OUs, but also to security groups, and even to user objects themselves.
Permission Hunting (Using DSACLS)
So, a nightmare scenario for you to consider is someone has reset the boss’ password and you need to find out who had permission to do it. (If you had Netwrix Auditor installed, you could have a look in there, but for now we’ll assume you don’t.)
1. In Users and Computers, navigate to the user object that you want to check permissions for.
2. Right click and select Choose Properties, then ‘Attribute Editor’
3. Scroll and double click on ‘distinguishedName’. Copy this string for later.
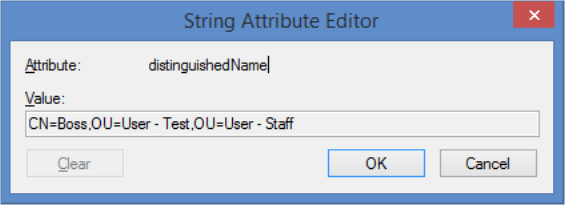
4. Open up a command prompt and type ‘dsacls’, followed by pasting the string you just copied, enclosed in speech marks:
5.Hit enter.
6. At this point you’ll probably realise there’s too many permissions on screen—you have two options:
a. Use |more on the end of the command to display one screen fully at a time.
b. Pipe the output into a text file and read that instead by using > filename.txt.
7. I went for the 2nd option, opened the file in notepad and eventually found that the senior management group has permissions to reset the boss’ password!
Permission Hunting (Using PowerShell)
Now that you’ve discovered delegation, you might be wondering if there are any delegations that you don’t know about—either from past employees, or malicious administrators.
I’ve put together a short PowerShell script which will search each delegable object type and list the two common permission delegations—reset password and ‘send-as’ (from Exchange).
Here’s a sample run from a domain:
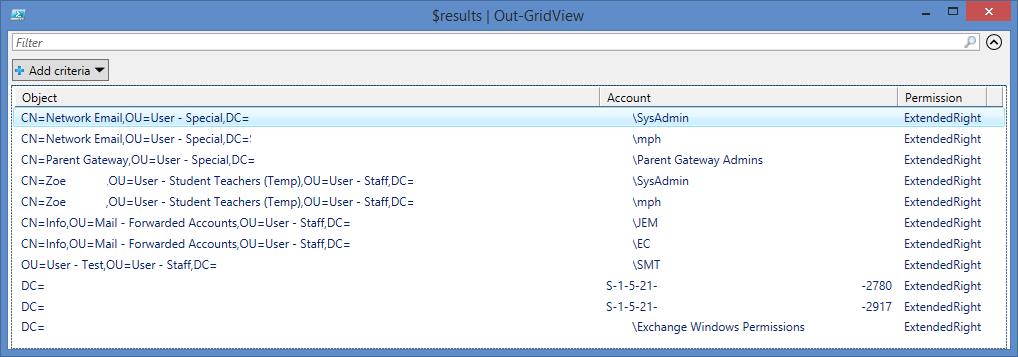
To use this script on your own domain:
1. Open Active Directory Users and Computers and navigate to the domain (or Organisational Unit) you’re investigating.
2. Right click it and choose Properties.
3. In the ‘Attribute Editor’ tab, look for the ‘distinguishedName’ property.
4. Select it and press View, then copy the LDAP Path. You will need this later.
5. Download a copy of the script from GitHub:
6. Right click and edit the script using PowerShell ISE.
7. Edit line 6 ($bSearch = …), replacing DOMAINCONTROLLER with the name of one of your domain’s DCs.
8. Edit line 6, replacing LDAP with the path you copied in step 4.
9. Save the script and press run.
10. Let the script search through your Active Directory; progress is reported in the console and when it is completed you will receive a popup detailing objects that have permissions delegated to them—you might be surprised!
If you need more information about how to detect who modified permissions in Active Directory check our how-to. There’s also a free tool from Netwrix that delivers actionable insight into who has permissions to what in Active Directory and file shares.



