With last year out of the way, analysts have combed over Microsoft’s list of vulnerabilities. What should come as no surprise to anyone is that 94% of the security bulletins with a critical rating could have been mitigated by removing administrative privileges. 100% of the Internet Explorer/Microsoft Edge critical bulletins were mitigated by removing administrative privileges. There are few legitimate cases for privilege credentials being interactively used in any Microsoft environment. This is especially true considering the many improvements made since Windows Server 2012.
Ask yourself this question – do any users (including IT or administrative staff) use administrative accounts for routine tasks? If you answered yes (or are not 100% sure), you are at risk. Like many environments, you have probably secured standard users but have elevated important personnel accounts. IT accounts in your environment probably use elevated credentials regularly. This can include logging in to their daily use computer and using critical applications and trivial programs (such as a web browser or email). Other risks can include shared accounts and common passwords across accounts.
In this article, we provide you with a 3-step guide to preventing privilege account escalation.
Step #1: Admit That IT Can Be a Liability
If your employees already use standard accounts, your administrative accounts are potentially the largest vulnerability in your domain. It does not matter how diligent, intelligent, or aware you are. A single mistake, such as using domain admin credentials on an infected workstation, can be your undoing. Accounts used by IT are the keys to the kingdom; they are prime targets for attackers.
Mitigating this risk is easy if you follow three rules:
- Assume your environment is already compromised. Solutions that you deploy should be hardened to prevent further compromise
- Domain administrator (or users with extensive delegated permissions) should be rarely used interactively
- Beware the hidden administrators. These include:
- The local administrator account on workstations and servers
- Service accounts with weak or unchanging passwords
- Shared elevated accounts (pay attention to what your department uses)
Knowing these rules will help. You must have actual solutions that strengthen your position and close privileged escalation gateways.
Step #2: Preventing Privilege Account Escalations
Microsoft has a tool for each of the rules listed above. The first tool, which includes accompanying concepts, is known as Privileged Access Management (PAM). PAM provides a way to securely delegate and manage Directory Services. The underlying technology for PAM consists of improvements in AD and Microsoft Identity Manager (MIM). When configuring PAM, you will create a trusted forest. Due to the way MIM implements this forest, it is hardened and known to be uncompromised.
Common account/group SID allows you to securely escalate permissions and interact with objects. The concept is similar to the MDOP tool, Advanced Group Policy Management. MIM handles the underlying workflow that includes time-sensitive security group memberships. Although this method may sound extreme, it is very easy to maintain. It is also the only 100% proven solution to prevent a previous compromise from bypassing any new security layers. PAM addresses the first rule listed in the previous section.
The second tool available is the Privileged Access Workstation (PAW) model. PAW provides a clean channel for administration. This is accomplished by using a highly secure and dedicated administrative machine. In the illustration below, a single administrator has two channels for his or her job duties. The top channel is through a PAW and only allows access to directory services through a dedicated user credential. That credential access should be managed through PAM. The second channel is used for other daily tasks, such as those involving Office applications.
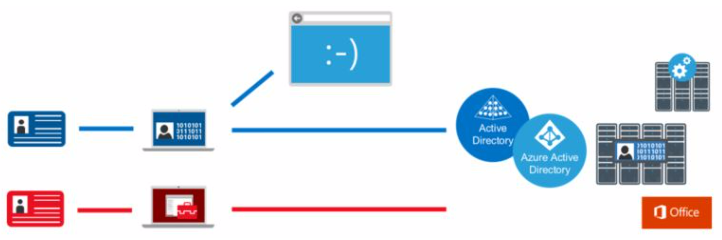
Resources can be saved by designating the administrator’s physical machine as the PAW channel and running a VM on top of it for other daily tasks. Microsoft specifies that exact order if you choose to incorporate VMs in the PAW infrastructure.
The single biggest benefit to PAW is realized for AD (including Azure AD) administrators. When implementing PAW, target these accounts first, as they are the ultimate prize for attackers. After the accounts are on the PAW model, other global service admins should be migrated. Be on the lookout for non-IT staff that should be on a PAW. Microsoft lists the following employees as potential targets:
- Classified or preannounced data
- Staff managing high visible services (such as a company’s social media accounts)
- Worker with access to trade secrets or soon-to-be protected data
If you think an account might benefit from the PAW model, it is a safe bet that they should be migrated onto it.
The final tool for preventing account escalations also addresses our third rule – the hidden administrator. The most obvious example is the default local administrator. In accordance with privileged account management best practices, that account should be disabled. Many organizations follow that guidance but set the local administrator password to the same value across the entire domain. In terms of workstation access, this is the equivalent of a domain administrator account. One compromised machine compromises every machine.
Local Administrator Password Solution (LAPS) is Microsoft’s free password management tool for local user accounts. It is a replacement (and enhancement) of the unsecure local users Group Policy Preference extension.
LAPS works through a new Group Policy Client Side Extension (CSE). This CSE should be installed on every workstation and server. The Active Directory or Group Policy administrator configures the minimum password security settings through the LAPS administrative template. When group policy is processed on a client, the LAPS extension does the following:
- Checks for password expiration on the managed local account by consulting an AD machine account attribute
- Generates and validates an account password (if the password has expired)
- Stores that password in a confidential attribute in the Active Directory computer account. The new password expiration date is written to a separate attribute.
- Changes the local user password to the generated value
In accordance with PAM, permission to read the local user password can be securely delegated. A UI tool is even provided for password lookup.
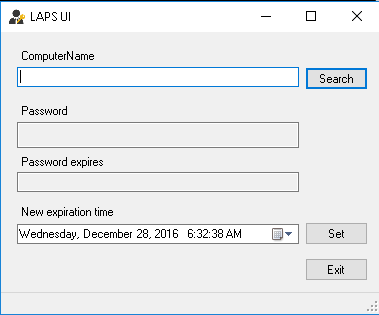
While LAPS provides an elegant solution for a local user, you should still be on the lookout for other hidden administrators. Not to sound paranoid, but always assume a compromised environment. This should be of more concern if the environment was not managed properly in the past.
Step #3: Monitor for Creeps and Exploits
There are many ways for compromised accounts to be used. By their nature, privileged accounts will always be a target for use and escalation. The three solutions above block many attack vectors, but a malicious actor only needs to be successful once.
Data collection and analysis is both your first and final line of defense. Services, such as the security and compliance tools in Azure or Office 365, provide event aggregation and alerting. These same techniques should be applied to other critical services. Any account action or logon attempt by a privileged account should be audited and reviewed for anomalies. Protected groups should be monitored for group membership changes. Finally, changes for convenience should be vetted against the potential for compromise. This is especially true if non-IT staff are enrolled in additional security services like the PAW model. Group Policy and Desired State Configuration make configuring and enforcing security policies easier.
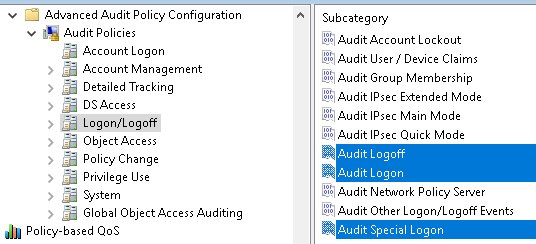
By following the guidance in this article, your environment can be made immune against the threat of privilege escalation. If you have integrated these security measures for all accounts (including IT), followed the three rules above, and continued to monitor, you can be assured that any attack gateway is considerably smaller.
Try our free tool to stay on top of who has permissions to what in Active Directory & file shares.



