Information security risk is the potential for threats to exploit vulnerabilities and cause financial loss. Organizations must evaluate risks by both likelihood and impact, then prioritize them using qualitative methods for simplicity or quantitative approaches for precision. This prioritization enables informed investment in controls that mitigate system downtime, data theft, fraud, and compliance failures.
Information security risk is the possibility that a given threat will exploit the vulnerabilities of one or more assets and thereby cause financial loss for the organization. For example, if your systems go down, how much money will your company lose because of downtime? The seriousness of a given risk depends on the specifics of your organization. For a more thorough introduction to risk assessment, please refer to these risk assessment best practices. In this post, we’ll explore two approaches to prioritizing risks: one qualitative and one quantitative.
Because information security risk is the likelihood of financial loss, no matter which approach you choose, the first step is to think about how your organization makes money, how employees and assets affect the profitability of the business, and what risks could result in large monetary losses for the company. After that, you should think about how you could enhance your IT infrastructure to reduce the risks that could lead to the largest financial losses.
Here are some of the top risks in information security you should consider:
- Attackers can alter electronic data or steal and misuse it, or gain unlawful use of a computer or system. For example, if someone successfully uses fraudulent data to purchase a product from your online store, your company will lose money. Therefore, you need to implement a process or solution that will prevent fraud, or at least mitigate the risk of fraud.
- Legal issues. Many types of incidents can result in expensive legal issues. For instance, if somebody hacks into your system and steals data from your database, even if the information they steal costs nothing, your organization might face legal repercussions for failing to provide adequate database security. This is especially true if you are subject to HIPAA, PCI-DSS or other compliance regulations.
- Data theft or damage. If your trade secrets are stolen, you could lose business to your competitors.
- When systems fail to perform their primary functions, your employees might not be able to work and customers might not be able to purchase goods from your website.
You need to identify and then prioritize information security risks so you can wisely allocate resources to improve IT security. You can choose either a qualitative or quantitative approach:
- Qualitative methods assess risk based on non-numeric categories or levels (e.g., low, moderate and high). Qualitative approaches are generally simpler and easier than quantitative techniques, especially if this is your first IT risk assessment. This is often the best approach for small and medium businesses.
- Quantitative techniques involve assigning numeric values to risk likelihood and monetary loss based on a matrix. Quantitative approaches generally require more time and money to implement than qualitative methods, but the results are more useful for detailed cost-benefit analyses. Therefore, this approach is often more appropriate for larger organizations.
Qualitative Risk Prioritization
A qualitative prioritization of risk starts by determining two things for each risk:
- How much money your company will lose if the risk event occurs
- The chance that this risk event will happen
Use a table like the one below to assign seriousness value to each of these factors.
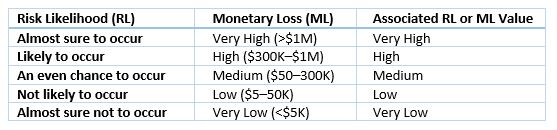
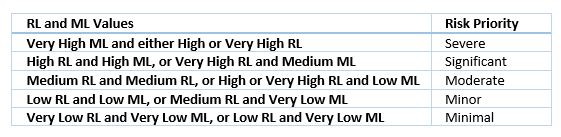
Then use the values for those two factors to prioritize the risks. For example if system downtime would result in Very High financial losses and the chance of downtime is High, then that risk has a Severe priority. However, if downtime would result loss of a Low amount money and the chance of downtime is High, then this risk has a Moderate priority. Here is an example of a very simple risk prioritization table:
Quantitative Risk Prioritization
Quantitative assessments assess risk based on numbers, where the meanings and proportionality of values are maintained by the organization. This type of assessment most effectively supports cost-benefit analyses. The benefits of quantitative assessments can, in some cases, be outweighed by the costs of the time and effort of experts, and the possible deployment and use of tools required to make such assessments.
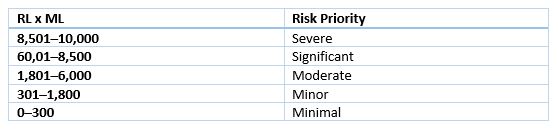
Again, you start by assessing the likelihood that the risk event will occur and how much money your company will lose if it does. Then you assign a numerical value to each of these factors using a table like this:
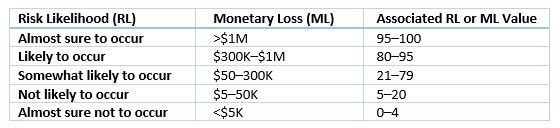
Multiply the RL and ML values together and use a table like the following to calculate the priority for each risk:
Using Your Risk Prioritization Results
Once you have identified and prioritized your risks, you need to establish a risk management plan — and get it approved by your company’s top management so you can get a budget for implementing it. The detailed risk management plan provides a business case for funding. It’s not enough to say “our systems might get hacked”; you need to show the impact this risk would have to the business — what is the business problem when somebody can hack into your systems and steal trade secrets or client data? You are demonstrating the return on investment for risk mitigation measures such as ensuring systems are up to date with proper antivirus software installed, or implementing an intrusion defense system (IDS) or intrusion prevention system (IPS).
Whether you choose a qualitative or quantitative approach to IT security risk assessment and prioritization, you are building the foundation for IT security at your organization.
Watch this recorded IT risk assessment webinar to learn best practices in establishing a continuous risk assessment and mitigation process.