IT risk assessments are vital for cybersecurity and information security risk management in every organization today. By identifying threats to your IT systems, data and other resources and understanding their potential business impacts, you can prioritize your mitigation efforts to avoid costly business disruptions, data breaches, compliance penalties and other damage.
This article explains what a security risk assessment is, the benefits of conducting regular security risk assessments, and the steps involved in the risk assessment process.
What Are IT Risk Assessments and Security Risk Assessments?
Security risk assessment is the process of identifying vulnerabilities in the IT ecosystem and understanding the financial threat they pose to the organization, from downtime and related profit loss to legal fees and compliance penalties to customer churn and lost business. A careful and thorough risk assessment will help you accurately prioritize your security efforts as part of your broader cybersecurity program.
Security risk assessments are a subset of a broader process — IT risk assessment. IT risk assessments consider not just threats to cybersecurity but a host of cyber risks. The Institute of Risk Management defines cyber risk as “Any risk of financial loss, disruption or damage to the reputation of an organization from some sort of failure of its information technology systems.” Similarly, Gartner defines cyber risk as follows: “The potential for an unplanned, negative business outcome involving the failure or misuse of IT.”
Examples of cyber risks include:
- Exfiltration of sensitive or important data
- Compromised credentials
- Phishing attacks
- Denial of service (DoS) attacks
- Supply chain attacks
- Misconfigured settings
- Hardware failures
- Natural disasters
- Human errors
It is important to note that both types of risk assessments are not one-time events. They should be performed on a regular schedule due to the dynamic nature of both IT environments and attack methodologies. The benefits and procedures explained below apply to both IT risk assessments and security risk assessments.
Benefits of Security Risk Assessments
IT risk assessments and cybersecurity risk assessments provide significant value to the organization. Key benefits include:
- Insight into where your most valuable IT assets resides — Some data stores, machines and other IT assets are more important than others. Since what IT assets you have and their value can change over time, it’s important to repeat the risk assessment process regularly.
- Understanding of risk — By identifying and analyzing the potential threats to your business, you can focus first on the risks that have the highest potential impact and the highest probability.
- Vulnerability identification and remediation — A gap-focused IT risk assessment methodology can help you identify and close vulnerabilities that threat actors can take advantage of. Examples include unpatched software, overly permissive access policies and unencrypted data.
- Cost mitigation — Undertaking a security risk assessment not only safeguards your business from the high cost of a data breach, but it also enables prudent use of budget for security initiatives that deliver the most value.
- Regulatory compliance — Regular security risk assessments can help organizations comply with the data security requirements of mandates such as HIPAA, PCI DSS, SOX and GDPR, and thereby avoid costly fines and other penalties.
- Improved customer trust — Demonstrating a commitment to security can increase customer trust, which can lead to improved client retention.
- Informed decision making — The detailed insight provided by a cybersecurity risk assessment will facilitate better decision-making regarding security, infrastructure and personnel investments.
Steps in a Security Risk Assessment
Now let’s run through the steps in a proper security risk assessment:
- Identify and prioritize assets.
- Identify threats.
- Identify vulnerabilities.
- Analyze existing controls.
- Determine the likelihood of an incident.
- Assess the impact a threat could have.
- Prioritize the risks.
- Recommend controls.
- Document the assessment results.
Note that while larger entities may task their internal IT teams with this process, organizations without a dedicated IT department could benefit from delegating it to an external specialist.
Step 1. Identify and Prioritize IT Assets
IT assets include servers, printers, laptops and other devices, as well as data like client contact information, email messages and intellectual property. During this step, be sure to solicit input from all departments and business units; that approach helps ensure you get a complete understanding of the systems the organization uses and the data that it creates and collects.
You also need to determine the importance of each cyber asset. Criteria that are commonly used include the asset’s monetary value, role in critical processes, and legal and compliance status standing. You can then classify your assets into categories, such as critical, major or minor.
Step 2. Identify Threats
A threat is anything that could cause harm to your organization. Examples include outside threat actors, malware, malicious acts by business users and mistakes by insufficiently trained administrators.
Step 3. Identify Vulnerabilities
A vulnerability is a weakness that could enable a threat to harm your organization. Vulnerabilities can be identified using analysis, audit reports, the NIST vulnerability database, vendor data, information security test and evaluation (ST&E) procedures, penetration testing, and automated vulnerability scanning tools.
Step 4. Analyze Existing Controls
Analyze the controls that are in place to reduce the probability that a threat will exploit a vulnerability. Examples of technical controls include encryption, intrusion detection systems, and multifactor authentication (MFA). Non-technical controls include security policies, administrative procedures, and physical or environmental protections.
Both technical and non-technical controls can be subdivided into preventive or detective categories. Preventive controls, such as encryption and MFA, are designed to thwart attacks. Detective controls, like audit trails and intrusion detection systems, are utilized to identify threats that have either transpired or are currently unfolding.
Step 5. Determine the Likelihood of an Incident
Assess the probability that each vulnerability might be exploited using factors such as the nature of the vulnerability, the capacity and intent of the threat source, and the presence and efficacy of your controls. Instead of a numeric score, many organizations use labels such as high, medium and low to denote the probability of a threat.
Step 6. Assess the Impact a Threat Could Have
Assess the potential consequences of an incident in which an asset is lost or compromised. Key factors to consider include:
- The role of the asset and any dependent processes
- The asset’s value to the organization
- The asset’s sensitivity
For this step, start with a business impact analysis (BIA) or a mission impact analysis report. These documents use quantitative or qualitative measures to assess the repercussions of damage to the organization’s information assets, including impacts on their confidentiality, integrity and availability. The impact can be categorized qualitatively as high, medium or low.
Step 7. Prioritize the Risks
For each threat/vulnerability pair, determine the level of risk to the IT system, based on the following:
- The likelihood that the threat will exploit the vulnerability
- The approximate cost of each of these occurrences
- The adequacy of the existing or planned information system security controls for eliminating or reducing the risk
A useful tool for estimating risk in this manner is a risk-level matrix. A high likelihood that the threat will occur is given a value of 1.0; a medium likelihood is assigned a value of 0.5; and a low likelihood of occurrence is given a rating of 0.1. Similarly, a high impact level is assigned a value of 100, a medium impact level 50 and a low impact level 10. Risk is calculated by multiplying the threat likelihood value by the impact value, and the risks are categorized as high, medium or low based on the result.
Step 8. Recommend Controls
Using the risk level as a basis, determine the actions needed to mitigate the risk. Here are some general guidelines for each level of risk:
- High — A plan for corrective measures should be developed as soon as possible.
- Medium — A plan for corrective measures should be developed within a reasonable time window.
- Low — The team must decide whether to accept the risk or implement corrective actions.
Step 9. Document the Results
The final step of the risk assessment process is to create a comprehensive report that aids management in making informed decisions on budget, policies, procedures and more. The report should delineate each threat, associated vulnerabilities, at-risk assets, potential impact on your IT infrastructure, probability of occurrence, and recommended control measures and cost. Often, a risk assessment report will identify key remediation steps that can mitigate multiple risks.
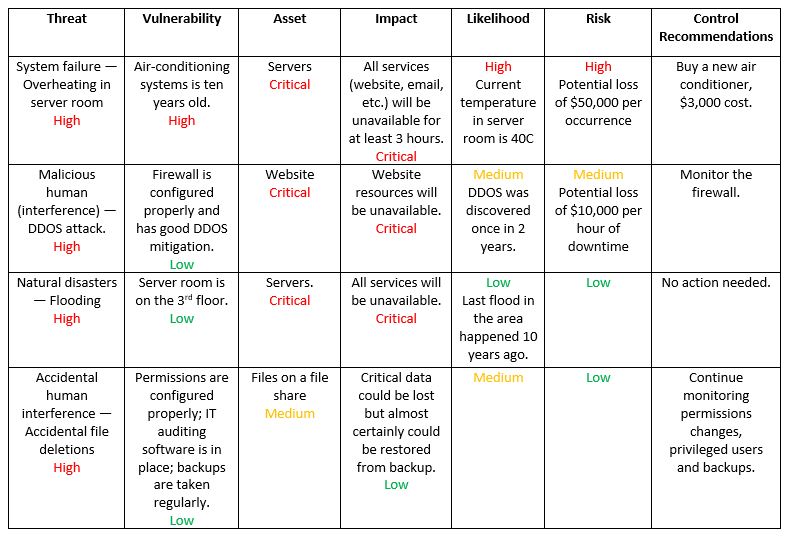
Summary
Security risk assessments and risk management processes are the foundation of any security management strategy because they provide detailed insight into the threats and vulnerabilities that could lead to financial harm to the business and how they should be mitigated. With a clear assessment of your IT security vulnerabilities and insight into the value of your data assets, you can refine your security policy and practices to better defend against cyberattacks and safeguard your critical assets.
FAQ
What is IT risk assessment?
IT risk assessment is the process of identifying an organization’s critical IT assets, potential threats that could damage or compromise those assets, and vulnerabilities in the IT infrastructure, and analyzing that information in order to improve security controls to prevent data breaches and disruption of essential business operations.
How do you conduct an IT risk assessment?
The steps in an IT risk assessment include the following: Identify IT assets and their value; uncover potential threats to each asset; discover vulnerabilities that can be exploited by those threats; and estimate the likelihood of the potential threat events. In addition, it’s important to create an IT risk analysis report that includes a plan to address the risks according to their priority.
What are the components of security risk assessment?
The key components of a risk assessment include the following:
- A catalog of IT assets and the business processes and operations that rely on them
- A detailed list of the potential threats to each of those assets and the likelihood of their occurrence
- An analysis of vulnerabilities that could lead to the loss or compromise of IT assets
- A list of the security controls currently in place to mitigate risk
- An assessment of the financial impact that the organization would suffer if the threat event occurred



