If you are responsible for corporate information security risk management, we both know your job is tough. Businesses keep generating large volumes of data, IT systems are increasingly complex, and cyber threats continue to evolve. What you have to deal with may sometimes look like an endless number of challenges, and your budget and resources might seem too limited to tackle all of them. Among other things, as an information security leader, you are expected to:
- Take a systematic approach to IT security.
- Determine which risks have most impact on your organization and protect the assets that matter most.
- Proactively mitigate risks and minimize damage from cyberattacks and data breaches.
- Ensure your organization can recover from security incidents faster and more easily.
- Justify investments in IT security to the board of directors.
Having a comprehensive information security risk management (ISRM) strategy will help you overcome these challenges. In this post, I will share some tips about how to create an effective ISRM strategy and what a good program looks like. For your convenience, I also provide a FAQ at the end.
What is information security risk management?
Information security risk management is the process of managing the risks associated with the use of information technology. In other words, organizations identify and evaluate risks to the confidentiality, integrity and availability of their information assets. This process can be broadly divided into two components:
- Risk assessment— The process of gathering and analyzing information about your assets and controls, and combining that data with an evaluation of the likelihood of events that could pose a threat to the IT environment and their potential impact, in order to define and prioritize your risks
- Risk treatment— The actions (if any) taken to remediate, mitigate, avoid, accept, transfer or otherwise manage the risks
What makes a good information security risk management approach?
Here are three criteria for determining whether your organization’s ISRM strategy is effective at improving your security posture:
- It ensures that unacceptable risks are being identified and addressed properly.
- It ensures that money and effort isn’t being wasted on risks that are not significant.
- It provides senior management with visibility into the organizational risk profile and risk treatment priorities to support their ability to make strategic decisions.
What are the steps for creating an effective information security risk management program?
Practice shows that a multi-phased approach to creating an ISRM program is the most effective, as it will result in a more comprehensive program and simplify the entire information security risk management process by breaking it into several stages. It will make the ISRM process more manageable and enable you to fix issues more easily. Here are five steps for building an effective information security risk management program:
Step #1. Business alignment
First, you need to understand your organization’s business conditions, such as budget considerations, staff and complexity of business processes. I cannot stress the importance of this step enough. Even if you have the best team, tools and controls, you may still fail if you’re not focusing your efforts on what is most important for the business.
During this stage, you have to connect with the organization’s leadership team to understand the business processes and their dependencies on technical assets and data flows. You also need to document the organization’s risk profile, including a detailed description of each risk that it faces as well as its risk appetite — the level of risk it is prepared to accept to achieve its objectives.
This will give you the foundation upon which you can build the ISRM program — and the support of the executives you need to implement it successfully.
Step #2. Program definition
Next, your organization needs to define the ISRM program. Be sure to:
- Define a prescriptive annual plan followed by a high-level three-year plan. Determine the specific goals and objectives that must be met on an annual basis. This plan should be adjusted annually to accommodate changes in business conditions and activities. When all capabilities are in place and business conditions stay the same, the typical timeframe for implementing an ISRM program is 30–36 months.
- Clearly define the point of arrival for capabilities based on management input. The point of arrival is basically a definition of the capabilities the organization would like to have in place once the program has been executed. You can identify the point of arrival by working closely with the leadership team to understand their goals regarding ISRM.
- Ensure the availability and capability of necessary staff for execution of the program. A key element of any ISRM program is proper staffing. All too often, organizations do not have enough qualified staff members to achieve the objectives of their ISRM programs. Therefore, it is essential to evaluate staff availability and qualifications to ensure you can meet all the objectives.
- Gain an understanding of the organization’s culture. Implementing an ISRM program is much more difficult if the people in the organization do not support its implementation. Depending on the organization’s culture, you will need to openly discuss the ISRM program with all the interested parties or seek guidance from senior management to drive adoption of the program.
Step #3. Program development
In this stage, you need to define the functional capabilities and controls related to IT security and risk management (e.g., vulnerability assessment, incident response, training and communication), along with the governance model that will determine who will be responsible for each area of the ISRM strategy. If you choose to outsource implementation of ISRM capabilities to third parties, be sure consider the risks and ensure appropriate oversight by internal staff.
Step #4. Metrics and benchmarking
Next, your organization needs to define the metrics to be used to evaluate the effectiveness of the ISRM strategy. Here are two best practices for this step:
- Ensure alignment with industry standards and guidelines.There are multiple standards to help you make sure your ISRM program complies with industry regulations, including COBIT, International Organization for Standardization (ISO) 27000 series and the U.S. National Institute of Standards and Technology (NIST) 800 series. I recommend considering ISO/IEC 27005:2018, NIST Special Publication 800-37 (Revision 2) and also NIST Special Publication 800-53A (Revision 5), which provide detailed guidelines on how to build a risk management program. It is important to consult multiple compliance standards and frameworks to determine whether your ISRM program has all necessary functions and capabilities.
- Use KPIs to measure the effectiveness of the functions and capabilities developed through the ISRM program.When developing KPIs, you need to identify the business value that you would like to gain with ISRM capabilities and then define objective criteria that can be used to assess that value. Try to base KPIs on the potential business impact and point-of-arrival guidelines, and assign dollar values where possible. This will help you connect your security posture with the business context for the organization’s leadership. Also, it is essential to identify the thresholds of what is acceptable and what is unacceptable for each KPI.
Step #5. Implementation and operation
Finally, you should implement your ISRM strategy — and monitor its operation to identify issues or areas for improvement. Define a schedule or conditions for reviewing the program; major changes in your IT environment, data breaches in your industry and new cyberattack techniques are all valid reasons for you to look at your ISRM program with a critical eye and revise it as necessary.
Which framework is best for building an effective ISRM?
The NIST frameworks are a great resource. Any organization can turn to NIST guidelines to model their own risk management strategy and security baselines. If your organization is looking for a thorough examination of how best practices can be applied through structured regulatory frameworks that also correspond to compliances, you would be well served by studying the NIST Risk Management Framework and the NIST Cybersecurity Framework:
NIST Risk Management Framework (RMF)
The NIST Risk Management Framework (RMF), as described in NIST Special Publication 800-37 (Revision 2), provides a comprehensive, flexible, repeatable and measurable process for improving how IT systems are designed, secured and monitored. Although the NIST RMF was created by the US Department of Defense (DoD), it serves as a good basis for a data security and privacy plan for any organization.
The NIST RMF involves the following 7 steps (note that last two differ for federal agencies and organizations):

Figure 1. NIST Risk Management Framework (RMF). (from nist.gov/rmf)
Step #1. Prepare
Preparation includes identifying key risk management roles; determining the organization’s risk tolerance; and performing an organization-wide risk assessment of security and privacy risks to the organization from the operation and use of IT systems.
Step #2. Categorize
Next, you need to categorize IT systems by risk level. Estimate the adverse impact of a loss of confidentiality, integrity or availability of systems and the information they process, store or transmit.
Step #3. Select
Based on the results of the previous step, you need to select and implement appropriate controls for each system. During this step, you will make decisions about what baseline security controls you want to implement based on what category the security risks fall into.
Step #4. Implement
The next step is to implement the controls to reduce system security and privacy risks.
Step #5. Assess
Next, it is important that the controls are implemented correctly and operate as expected to protect the systems.
Step #6. Authorize
- For federal agencies. Once your security controls have been put into action, a system can be granted (or denied) Authority to Operate (ATO) by the government.
- For other organizations. Internal or external stakeholders might require the opportunity to review an authorization package that includes your security and privacy plans, milestones, assessment reports and supporting evidence, or other documentation).
Step #7. Monitor
- For federal agencies. System controls must be checked on a regular basis. An ATO is valid for only three years, after which the entire process must be redone.
- For other organizations. The organization should continuously monitor their controls to ensure they remain effective, and make updates as needed based on changes to the IT environment or threat landscape.
NIST Cybersecurity Framework
The NIST Cybersecurity Framework is another framework that can help companies better manage and mitigate cybersecurity risk. The steps of this framework include the following:
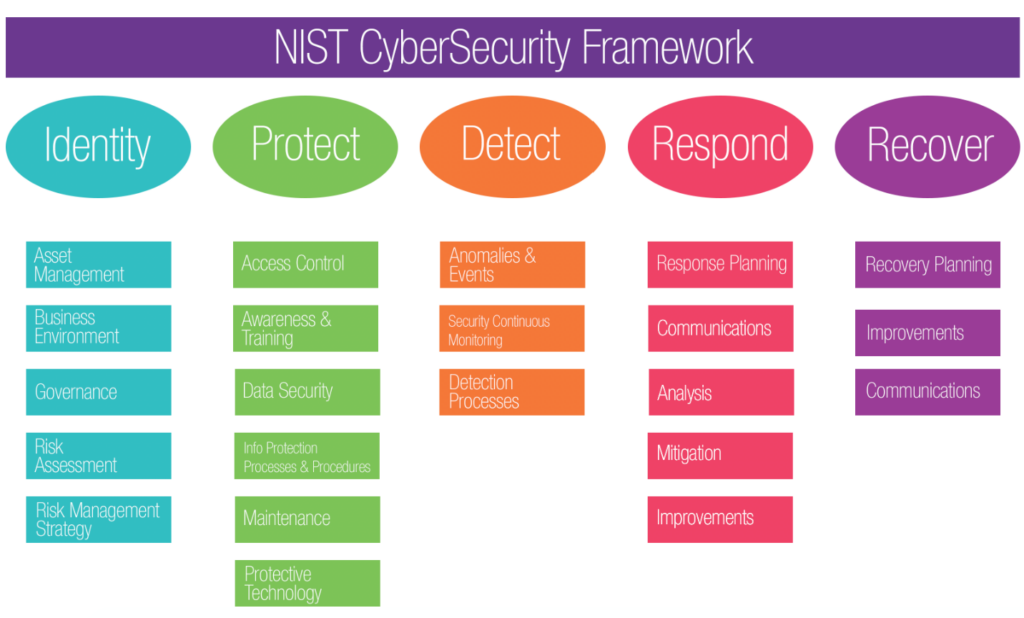
Figure 2. Framework Core Structure image (from the NIST Framework for Improving Critical Infrastructure Cybersecurity, version 1.1).
- Identify — Understand and prioritize the cybersecurity risks to systems, people, assets, sensitive data and capabilities. Activities include asset management, governance and risk assessment.
- Protect— Implement appropriate security controls and other safeguards to protect critical assets against cyber threats. Examples of activities here are identity management and access control, promoting awareness, and training staff.
- Detect— Ensure your organization can quickly spot events that could pose risks to data security. Techniques include continuous security monitoring and user behavior analysis (UBA).
- Respond — Develop a plan for responding to a cybersecurity incident to contain its impact, including analysis, communications and mitigation.
- Recover — Having a strategy for restoring capabilities or services that were impacted by a security incident helps ensure a faster return to normal operations. Be sure to review the recovery plan and make improvements, such as updating or replacing policies.
Summary
Understanding and managing risks to systems and sensitive data is essential for an organization’s success. Developing an ISRM program makes the risk management process more manageable and helps you protect your most critical assets against emerging cyberthreats.
FAQ
What is risk management in cybersecurity?
Risk management in cybersecurity is managing the security and privacy risks related to information systems. It is a holistic activity that affects every aspect of the organization, including mission planning, enterprise architecture, software development and systems engineering.
What are information security risks?
Information security risks are threats that could can cause damage or disruption to IT systems or data. Common IT security risks are disclosure of passwords, malware and spyware, unauthorized access to the network, and social engineering attacks.
What is the purpose of the NIST Risk Management Framework?
The Risk Management Framework developed by National Institute of Standards and Technology (NIST) helps organizations build a secure and sustainable ISRM program. It helps them identify and assess the risks to their systems and data, so they can make more informed, risk-based IT security decisions.
Are there any certification programs for the NIST Risk Management Framework?
RMF certification is required only for federal and state agencies, but it can be valuable even if you aren’t employed by the government. Here are a few of the programs can help you learn how to apply the Risk Management Framework in your risk management strategy and get certified if you choose:
- Introductory course from NIST (free)
- Introductory course from the CDSE (free)
- Training class for DoD IT pros from BAI (paid)
- Four-day boot camp from Infosec (paid)
- Two-day training from Tonex (paid)
How does risk management improve IT security?
A thorough risk management process can strengthen IT security significantly by identifying the risks to an organization’s IT systems and data, and making informed decisions about how to mitigate and eliminate vulnerabilities.