Modern IT infrastructure is comprised of various interconnected network components that make communication and resource sharing possible throughout your organization. Whether securing sensitive data, facilitating collaboration, or simply ensuring uninterrupted access, a network of devices is at play—and the elements of these devices are critical to a business’s successful operation.
Below, we explore network devices’ definition, types, functions and importance in maintaining business efficiency, security, and reliability.
Network Device Definition
A network device is a piece of hardware or software integral to communication between a computer and an internet network. Common network devices are:
- Routers
- Switches
- Hubs
- Modems
- Firewalls
- Access points
Network devices manage traffic flow and direct data packets, provide security, and enable connectivity between network segments or the Internet. Each device serves a specific purpose that allows for a seamless flow of information and connectivity across an organization’s IT ecosystem.
Significance of Network Devices
Network devices play two key roles:
- The first is establishing a network connection, as a router or a modem does.
- The second one is maintaining, protecting and enhancing that connection, as with a hub, repeater, switch or gateway
Network devices are critical for establishing and managing networks. The purpose of a computer network is to share resources like files, printers, and internet connections among an organization’s users and devices. They ensure data is accurately routed and secured, supporting network services and applications’ effective and reliable operation. Without network devices, your IT infrastructure would lack the ability to manage data traffic, leading to inefficiencies, data loss, and security vulnerabilities. Network devices also enable scalability for businesses, allowing networks to adapt to changing business needs, which is essential for maintaining optimal performance and protecting against cyber threats.
Functions of Network Devices
Networking devices serve the following general purposes:
- Facilitate data transmission and communication between devices
- Enable efficient and secure network connectivity
- Enhance network performance and optimize traffic flow
- Provide network security by enforcing access control and threat prevention
- Simplify network management and configuration
- Extend network coverage and overcome signal limitations
Types of Network Devices
Understanding the different types of network devices is important for optimizing and securing your organization’s network infrastructure. Below, we provide a list of network device examples that form the foundation of effective network management and communication:
- Repeater
- Hub
- Bridge
- Switch
- Routers
- Gateway
- Brouter
- Network Interface Card
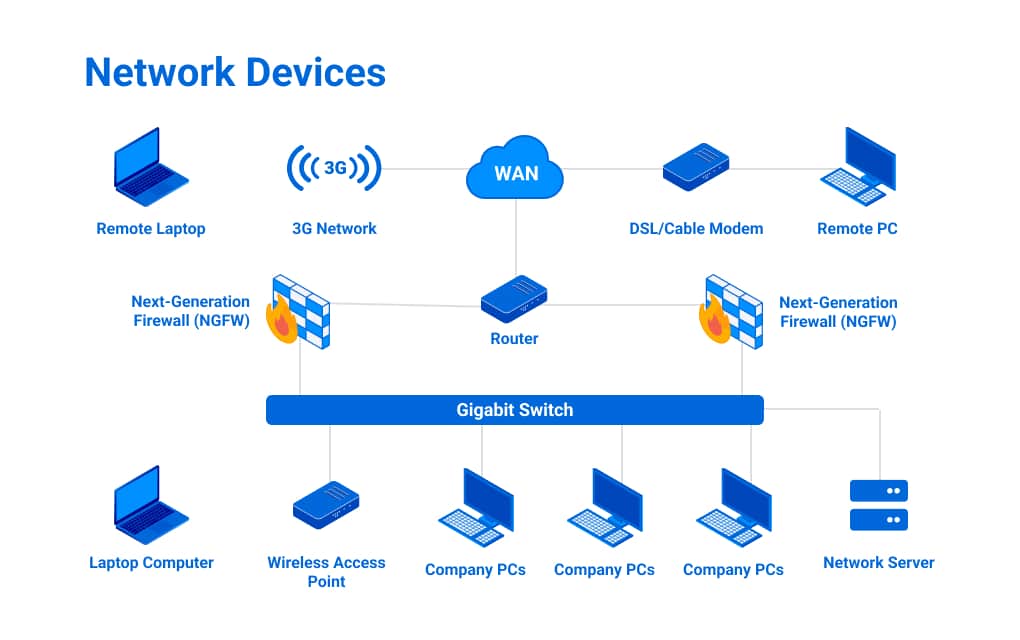
Let’s analyze each of these types and sub-types of network devices.
Repeater
A digital signal can only travel so far down a cable until it degrades. This gradual weakening is referred to as attenuation rate. A repeater operating at the OSI model’s physical layer (Layer 1) is a powered device that reenergizes the signal to keep traveling further. Dedicated repeaters are rarely used today, as powered hubs, switches, and routers do the job of a repeater. However, repeaters are occasionally employed to extend the range of remote wireless access points.
Hub
A network hub is an essential multiport device that connects multiple Ethernet devices into a single broadcast network segment, which makes them prone to traffic congestion. There are three types of Hub:
- Passive hub
- Active hub
- Intelligent hub
Let’s look at each of these:
- Passive hub: No power source is needed to connect devices without amplification.
- Active hub: This hub amplifies incoming signals before broadcasting and requires external power. Thus, it acts as a repeater.
- Intelligent hub: Includes network management, monitoring, and diagnostic features.
Once widespread, hubs are now rarely used as switches have replaced them. Like repeaters, hubs operate at the OSI model’s physical layer (Layer 1).
Bridge
While a hub connects multiple devices, a network bridge connects two or more network segments and filters the traffic between them. Their role is to isolate local segment traffic and reduce traffic congestion for better network performance. A local bridge connects two or more network segments within the exact physical location or LAN. In contrast, a remote bridge connects network segments that are geographically separated, often over a WAN link.
Types of Bridges
There are two types of bridges:
- Transparent bridges
- Source bridges
Let’s look at each of these:
- Transparent bridges build and maintain a MAC address table by examining incoming frames’ source addresses and making forwarding decisions by checking the destination MAC address against this table.
- Source bridges used a different approach and were commonly used with token ring networks, which are virtually obsolete. Bridges operate at the OSI model’s data link layer (Layer 2). You will most likely never work with either type of bridge today.
Switch
There are many different types of switches available today, such as:
- Unmanaged switches
- Managed switches
- Smart switch
- Layer 2 switch
- Layer 3 switch
- PoE switch
- Gigabit switch
- Rack-mounted switch
- Desktop switch
- Modular switch
Types of Switches | Functions of Switches |
|---|---|
| Unmanaged Switches | Unmanaged switches are plug-and-play devices with a fixed configuration that cannot be modified or optimized. They have limited functionality and provide no means of remote access or monitoring. These switches are designed for small networks or home use. |
| Managed switches | Managed switches are entirely configurable and can be managed or monitored through a web interface, command-line interface, or SNMP session. |
| Smart switches | Smart switches balances unmanaged and fully managed switches. It essentially provides the basics, with a web interface accessing management features. |
| Layer 2 switch | Layer 2 switch operates at the OSI model’s data link layer (Layer 2) and uses MAC addresses to forward data within a LAN. It connects local devices within the same network segment and uses MAC addresses to manage their traffic. These switches improve network efficiency by reducing collisions and segmenting traffic into separate collision domains. |
| Layer 3 switch | Combines the functionality of a Layer 2 switch and a router. They are often used at multiple virtual LANs (VLANs) sites. Packet switching is based on MAC addresses like a traditional switch, but this device also incorporates routing capabilities using IP addresses, allowing them to route traffic between different VLANs and subnets. |
| PoE switch | This delivers data and electrical power to network devices via a single Ethernet cable, eliminating the need for separate power supplies. Because the connected PoE devices have no power cords, it simplifies installation and reduces cabling. Examples of PoE devices include cameras, VoIP phones, and wireless access points. |
| Gigabit switch | This high-speed switch supports data transfer rates of 1 gigabit per second (Gbps) or more. |
| Rack-mounted switch | A rack-mounted switch is a network switch designed to fit a standard 19-inch server rack. |
| Desktop switch | This type of switch is commonly used for a small or home office environment and is typically stored on a desk or tabletop. |
| Modular switch | A flexible network switch that allows the addition of various modules or expansion cards for future customization and scalability |
Routers
The main job of a router is to direct traffic. Routers transfer packets to their destinations by charting a path through interconnected networking devices using different network topologies. They are intelligent devices that store information about their connected networks. Routers commonly use access control lists (ACLs) to filter traffic; some can even serve as packet-filtering firewalls.
Routers also divide internal networks into two or more subnetworks and can be connected internally to other routers, creating zones that operate independently. Routers establish communication by maintaining tables about destinations and local connections. A router also contains information about the routers they are connected to and uses this information to forward packets to any destination it doesn’t know about. Routers operate at the OSI model’s network layer (Layer 3). There are two types of router:
- Static Router
- Dynamic Router
Let’s take a look at each of them.
Static Router
A static router uses manually configured routes to direct network traffic to ensure consistent, predefined data-pack paths without automatically adjusting to network changes. They are ideal for smaller networks.
Dynamic Router
A dynamic router automatically communicates with other dynamic routers to modify its routing table based on real-time network conditions. It uses dynamic routing protocols like OSPF, RIP, or BGP to exchange information about network topology and link states with other routers. These protocols enable routers to discover optimal paths, adapt to network changes, and reroute traffic efficiently. Dynamic routers continuously update their routing tables, allowing automatic failover and load balancing. They can quickly respond to network failures or congestion by finding alternative routes. This flexibility makes them ideal for large, complex networks where manual configuration would be impractical.
Gateway
A common network device used to connect networks is a gateway. A gateway connects different networks and enables communication between them. Think of it as a translator that converts data from one protocol or format to another. This helps ensure compatibility between diverse network environments. A gateway is essential for communication that must traverse different network architectures.
Example of Gateway
A typical example of Gateway network device is a LAN that connects to a vast area network (WAN) or the internet. These devices usually work at the OSI model’s Transport and Session layers (Layer 5 and 6). Gateways may also provide security features, such as firewalls, and offer network performance optimization features.
Brouter
A brouter is an abbreviated term for “bridge router” and combines the functions of both a bridge and a router. Because of this, it operates in the data link layer (Layer 2) and the network layer (Layer 3) of the OSI model. A brouter forwards data packets based on MAC addresses (like a bridge) and IP addresses (like a router). Brouters are no longer used today, as most networks use specialized routers and switches.
Network Interface Card
Any network-connected device includes a Network Interface Card (NIC). This card provides a dedicated connection between a computer and a network and manages the data transmission and reception. It is referred to as a card, originally designed as an expansion card inserted into a slot in the motherboard. Most NICs today are integrated directly into the motherboard. They come in various types, including:
- Wired (e.g., Ethernet)
- Wireless (e.g., Wi-Fi)
- Fiber optic
NICs typically consist of several key components:
- A controller for processing data
- A port for cable or transceiver connection
- A bus interface for connecting to the computer
- A unique MAC address for identification on the network
Virtual Network Devices
Cloud computing has given rise to a variation of all kinds of network devices. Operating a virtualized infrastructure (IaaS) includes the types of network devices discussed, such as routers, switches, firewalls and interface cards. They can exist as an own virtual machine operated by the organization or be part of the environment provided by the cloud service in use.
Additional Network Components
The following are additional network components:
- Modems
- Network Cables
- Firewall
- Wireless Access Points (WAPs)
- Intrusion Detection & Preventing Systems (IDPS)
- Virtual Private Network (VPN) Appliances
Modems
A modem (short for modulator-demodulator) is a device that converts digital signals into analog signals of different frequencies and transmits them to a modem at the receiving location. These signals From the modem can be transmitted over telephone lines, cable systems, or other communication mediums. A modem also works to convert incoming analog signals back into digital data. They are commonly used to facilitate internet access by customers of an Internet Service Provider (ISP).
Types of Modems
There are four main types of modems:
- DSL modem: Uses telephone cables and is considered the slowest connection.
- Cable modem: Transmits information over TV lines faster than DSL.
- Wireless modem: Connects devices using Wi-Fi networks and relies on nearby Wi-Fi signals.
- Cellular modem: Allows a device to connect to the internet using a cellular network instead of Wi-Fi or fixed-line connections.
Network Cables
A network cable is a physical medium to connect devices in a computer network. Common types include:
- Ethernet cables (e.g., Cat5e, Cat6)
- Coaxial cables
- Fiber optic cables.
These cables differ in speed, bandwidth, and transmission distance capabilities. An Ethernet cable is commonly used to connect devices such as a computer or camera to a network switch. In contrast, a fiber optic cable connects routers to a pipeline to carry high traffic loads. Regardless of the type, cables typically consist of insulated conductors, shielding, and connectors at each end to facilitate device connections. All network cables have an attenuation length, which means they can only carry digital signals for so long before a power source must energize them. This length varies depending on the cable type, quality, and transmitted signal frequency.
Firewall
A firewall is a network security device that establishes a barrier between trusted internal networks and untrusted external networks. A firewall connects multiple areas called zones, such as:
- LAN
- WAN
- DMZ
Using assigned security policies, they filter traffic by examining data packets that flow between the different zones. The internet is, of course, the most untrusted network of all. Firewalls can also be placed within the internal network to isolate internal departments that host sensitive data, such as HR or Finance. Firewalls can be hardware-based, software-based, or a combination of both.
Firewalls may enforce blocklists (also known as deny lists) that allow all traffic but certain types. For more restrictive security, you can implement an allowlist (also called an allow list) that blocks all traffic except what is specified. Several types of firewalls exist, and which one is right for you depends on your operation. Some of the most common firewall types include:
- Packet Filtering
- Stateful Inspection
- Next-Generation Firewall (NGFW)
Let’ elaborate on each of the three types for firewalls.
Packet filtering
Acts as a network layer checkpoint, analyzing data packets by IP address, packet type, port number, or network protocols
Stateful inspection
Analyzes data at network and transport layers, inspecting source IP, destination IP, source port, and destination port.
Next-Generation Firewall (NGFW)
This advanced network security device goes beyond traditional firewall capabilities and boasts multiple security features integrated into the product. Some examples include deep packet inspection, intrusion prevention systems (IPS), application awareness and control, and advanced threat detection. NGFWs may also use AI to combat sophisticated threats by examining the contents of packets and identifying applications and potential threats within the traffic.
Wireless Access Points (WAPs)
A wireless access point (WAP) is a networking device with a built-in antenna, transmitter, and adapter. WAPs use the wireless infrastructure network mode to provide a connection point between WLANs and a wired Ethernet LAN. A WLAN essentially serves as an interconnection point between the WLAN and a fixed wire network.
A service set identifier (SSID) name is necessary to connect to a wireless network. The SID is used to identify all systems belonging to the same network, and client stations must be configured with the SSID to be authenticated to the WAP. The WAP might broadcast the SSID, allowing all wireless clients in the area to see the WAP’s SSID. However, for security reasons, APs can be configured not to broadcast the SSID, meaning an administrator needs to give client systems the SSID instead of allowing it to be discovered automatically. Wireless devices ship with default SSIDs, security settings, channels, passwords, and usernames. For security reasons, changing these default settings as soon as possible is strongly recommended because many internet sites list the default settings used by manufacturers.
Depending on the size of the network, one or more WAPs might be required to provide full coverage. Additional WAPs allow access to more wireless clients and expand the wireless network range. Each WAP is limited by its transmission range — the distance a client can be from a WAP while still obtaining a reasonable signal and data process speed. The distance depends on the wireless standard, the obstructions, and the environmental conditions between the client and the WAP. Higher-end WAPs have high-powered antennas, enabling them to extend how far the wireless signal can travel.
There are many types of WAPs, such as:
- Standalone Access Points:
- Controller-Based Access Points
- Cloud-Managed Access Points:
- USB Access Points
Standalone Access Points
These independent devices provide wireless connectivity to clients. These units are suitable for small businesses or home networks needing a limited number of access points.
Controller-Based Access Points
These WAPs are managed by a central wireless LAN controller to simplify the administration of multiple access points. They are ideal for more extensive networks, where centralized management is crucial for efficient operation and scalability.
Cloud-Managed Access Points
These are managed through a cloud-based platform and offer remote management and monitoring capabilities. These are highly suitable for distributed networks and multi-site businesses, where centralized cloud management provides efficient oversight and control across multiple locations.
USB Access Points
USB Access Points are small, portable devices that connect to a USB port to create a wireless hotspot. They are helpful for temporary setups, travel, or extending a small home network.
Intrusion Detection & Preventing Systems (IDPS)
An Intrusion Detection and Prevention System (IDPS) is a network security tool that monitors, detects, and prevents malicious activities and security threats in computer networks.
Its core functions are to monitor network traffic for suspicious activity, detect potential threats, and take action to prevent or mitigate possible attacks. The critical components of an IDPS include the Intrusion Detection System (IDS), which monitors and creates alerts on suspicious activities, and the Intrusion Prevention System (IPS), which actively blocks or prevents identified threats.
Unified Threat Management (UTM)
A UTM device is a security appliance that combines multiple security functions into a single hardware or software solution. An IDPS is commonly included in a Unified Threat Management (UTM) device such as an NGFW.
Virtual Private Network (VPN) Appliances
A traditional virtual private network (VPN) is a secure connection method that remote users use to connect to a corporate network. A VPN connection comprises two main components:
- VPN server (a firewall or a dedicated VPN appliance)
- VPN client application installed on the connecting device
The connection creates an encrypted tunnel through the internet that encrypts all data flowing between the VPN client device and the corporate network. There are also third-party VPN service subscriptions that can help users protect sensitive information, bypass geo-restrictions, and protect their identity.
Components of Network Architecture
The following are the additional components of network architecture:
- Transmission media
- Protocols
- Topology
Transmission media
Transmission media refers to the physical pathways that serve as the road system of your network that data traverses. Examples include Ethernet cables, fiber optics, and wireless signals. The choice of transmission media will impact the speed, distance, and reliability of data transmission.
Protocols
Protocols are rule sets and conventions that govern data exchange between network devices. Establishing a set standard ensures interoperability between different products of multiple vendors. Common within the family of IP-based protocols for network devices and their management are:
- TCP
- UDP
- (S)HTTP
- SSL/TLS
- DHCP (Dynamic Host Resolution Protocol)
Routing protocols for wide-area networking are BGP, Network Address Translation (NAT), Port Address Translation (PAT) and their combined use as well as switching routines like fast forward or store and forward.
Topology
Topology describes the layout and structure of the network, outlining how different nodes and devices are interconnected. Common topologies include star, bus, ring, and mesh. All network components are connected to a central node in a star topology. The classic example is a group of desktop computers connected to a centralized switch. This is by far the most popular topology choice today. Each topology has advantages and disadvantages that may affect the network’s performance, scalability, and fault tolerance.
Common Challenges in Network Device Management
There are so many moving parts within a modern network today, and many things can go wrong. With the complexity of interconnected devices and diverse protocols, network management becomes a multifaceted challenge. IT professionals must navigate a landscape where hardware failures, software glitches, bandwidth issues, and user-related problems can arise at any moment. Let’s look at some common challenges that network support teams face in managing network devices:
- Physical Connectivity Issues
- Malfunctioning Hardware Devices
- DNS Issues
- Temperature and Ventilation Problems
- Overutilization of Capacity
- Power Supply Fluctuations
- Battery Overuse
Let’s look at each of the challenge for managing network devices in computer networks

Physical Connectivity Issues
A connectivity issue arises when traffic cannot flow between two points. This issue can arise from damaged cables, faulty connectors, or malfunctioning hardware, leading to network outages, intermittent connectivity, slow data transfer, and increased downtime. While connectivity problems can significantly disrupt operations, they are often among the easiest to troubleshoot.
Malfunctioning Hardware Devices
When your network devices fail or operate sub-optimally, it can lead to slow data transfer rates, increased latency, packet loss, and even complete network downtime. Losing a single centralized network component can significantly disrupt business operations and reduce productivity, which is why built-in resiliency is critical today.
DNS Issues
DNS stands for Domain Name System. It is a hierarchical and distributed naming system for computers, services, and other resources connected to the Internet or a private network. DNS issues can significantly impact network functionality by disrupting name resolution processes. Without an available DNS server, you cannot traverse the internet, check your email, or even log onto a Windows domain.
Temperature and Ventilation Problems
Servers and network appliances contain processors that create a great deal of heat. Overheating can damage a network device, reduce its product lifespan, or initiate an unexpected shutdown. Because of this, the rooms that house your network equipment must have proper cooling and ventilation. The temperature of the data center or closet containing your equipment must be monitored to counter any temperature rise.
Overutilization of Capacity
Network overutilization is analogous to a congested highway during rush hour. When network traffic exceeds its designed capacity, it leads to digital gridlock. This congestion manifests as slower response times, increased latency, and packet loss. Users may experience frustrating symptoms such as buffering during video streaming, dropped VoIP calls, and sluggish web application performance.
Power Supply Fluctuations
Your company’s network is driven by power. Power supply fluctuations can lead to intermittent connectivity issues, packet loss, and increased latency. Consistent power variations can also reduce the lifespan of network equipment, resulting in higher operational costs due to more frequent replacements. Using uninterruptible power supplies (UPS), surge protectors, and proper electrical system maintenance is essential to minimize these risks.
Battery Overuse
Rapidly draining batteries cause devices to throttle performance and, over time, can reduce network interaction responsiveness and connection times. This frequent disconnect and reconnect cycle increases signaling load and data usage, potentially contributing to network congestion.
Best Practices for Network Device Security
Understanding the different types of network devices available today is the first step in building a reliable network. However, ensuring your network is safe, runs efficiently, and doesn’t become vulnerable over time is also essential. Below are some best practices that will help you avoid connection and security issues:
- Opt for multi-vendor support
- Prioritize critical alerts
- Proactively monitor and troubleshoot
- Gain deeper visibility
- Automate basic tasks
- Clarify hardware dependencies and processes
- Troubleshoot cable connectivity issues
- Handle faulty ports
- Verify traffic overload
- Perform regular firmware and software updates
- Harden all network devices
- Implement strong user management and access control
- Use network segmentation and VLANs
- Monitor for anomalous activity
- Perform periodic security assessments
Opt for multi-vendor support
Diversifying vendor relationships is a strategic approach for organizations seeking optimal IT solutions. By avoiding vendor lock-in, companies can select best-in-class products and services tailored to their needs and changes. This strategy gives organizations greater leverage to negotiate competitive pricing and more favorable support agreements and adapt to changing technological landscapes. It also allows businesses to capitalize on innovations from various vendors, ensuring they remain agile and efficient in their IT operations.
Prioritize critical alerts
Network devices generate numerous alerts, notifications, and log files. IT support teams need a method to filter through this noise and identify relevant events. Prioritizing critical alerts is essential to ensure that the most significant issues are addressed promptly and efficiently, reducing discovery and remediation times.
Proactively monitor and troubleshoot
A proactive approach means avoiding potential network issues rather than reacting to them as they occur. By anticipating potential issues in advance, you can better avoid disruptive downtime, performance bottlenecks, and security incidents. This approach helps optimize network resources, improve user experience, maintain compliance, and increase the resiliency of your network.
Gain deeper visibility
A lot is happening beneath the hood of a modern IT network, and you need visible access to all of it to manage it effectively. The more visibility you have, the better you can identify and remediate issues. You also can’t secure what you can’t see. Visibility into all network areas allows for the early detection of suspicious activities and potential threats, reducing the mean time to respond to potential threats, also known as MTTR. Visibility helps you plan capacity and allocate network resources to support current and future demands.
Automate basic tasks
Automation ensures that standard procedures and repeatable processes are conducted in an established, consistent manner every time. Automating manual routine tasks reduces human error and frees up the valuable time of your IT staff, who have far more critical things to do. Automation can also garner significant cost savings over the long term.
Clarify hardware dependencies and processes
Because a network depends on many different components, it can act like a row of dominos; if one device fails, others can quickly fall. The result can be cascading performance issues and failures throughout the network. Understanding the dependencies of your network applications and workloads allows support teams to proactively identify and resolve minor issues before they escalate into more significant problems.
Troubleshoot cable connectivity issues
Faulty cables can cause intermittent connections, slow data transfer, and complete network outages. Identifying and resolving these issues promptly reduces any potential disruption to the network. In most cases, replacing cables is an easy fix.
Handle faulty ports
It is easy to rule out faulty port behavior by simply plugging a cable into a different port.This quick action can immediately rule out or confirm a port-specific issue. If the port is the issue, the next step is to verify the port configurations using the switch management interface. An incorrect VLAN assignment is a typical example of port misconfiguration. Sometimes, the issue may be hardware-related, which can mean replacement.
Verify traffic overload
When areas of your network become overutilized, the phones start ringing, with users reporting slow performance issues. Network admins need to identify potential bottlenecks where traffic converges and exceeds capacity. Using network monitoring tools will allow them to detect unusual spikes or sustained increases in network traffic. Consistently high utilization of network connections often indicates a need for increased bandwidth.
Perform regular firmware and software updates.
All devices require regular updates to purge bugs and continue operating correctly. Network devices require frequent updates because hackers constantly devise new ways to infiltrate networks and steal information. Checking for firmware and software updates is essential to maintaining a working infrastructure at total capacity.
Harden all network devices
Often, network devices’ default configurations are overly permissive, increasing the risk of malicious actors breaking into the network. Always ensure that each device’s settings are hardened according to your protocols and industry standards. Disable all unnecessary features, services, and ports and require strong passwords for authentication.
Implement strong user management and access control
Implement the principle of least privilege to restrict user access rights to the minimum necessary for their job functions. This approach limits authorized users’ access to sensitive data and networks, reducing the risk of unauthorized actions or data breaches. Keep access lists and implement controls to ensure no one is entering places they aren’t supposed to be. Ideally, standing privileged accounts should be replaced with just-in-time access to heighten security.
User network segmentation and VLANs
Network segmentation creates subnetworks within a more extensive network to help keep unwanted visitors out of sensitive files. This helps reduce the blast zone of a cyber-attack and gives security personnel more time to respond and mitigate it. Implement a VLAN to ensure that only specific devices can access segmented networks for further protection.
Monitor for anomalous activity
While anomalous or suspicious activity may signal malicious activity, it is often a critical signal that something sinister may occur. This is where constant network activity monitoring comes into play. Determining what constitutes “normal” behavior within your network is key. This is done by maintaining comprehensive logs of all users and devices over time. Once a behavior baseline is established, you can more effectively spot and address suspicious activities that deviate from established patterns.
Perform periodic security assessments
Never assume your bases are covered simply because you have security network devices. It would be best if you always had a means of verification. Regular audits of your network infrastructure can help provide this means of verification. These audits can be conducted internally or by an outside party specializing in these functions. Regular security assessments are not only best practices but are often mandated by various regulatory or industry frameworks such as HIPAA or GDPR.
How Netwrix Can Help
Netwrix Auditor for Network Devices provides comprehensive visibility into your network devices. It automates the auditing of configuration changes, tracks device logins from remote access and suspicious IP addresses, and scans for security threats and device malfunctions from a unified platform. With Netwrix Auditor, you’ll be able to improve business continuity and stay on top of network security threats with ease.
Conclusion
From routers and switches to firewalls and access points, each device in your network plays an important role. Properly managing these devices allows you to optimize network performance and quickly troubleshoot issues. A comprehensive understanding of the makeup of your network will make it easier for you to evolve as your organization’s business and technology needs change. IT teams must also commit to best practices when managing and securing your network. By prioritizing knowledge and skills in this area, IT professionals can ensure their networks remain resilient, responsive, and ready to meet the challenges of the interconnected world that your business serves.
FAQ
What are the types of network devices?
The most common network devices include repeater, hub, bridge, switch, routers, gateway, brouter and network interface card.
What is a network device?
A network device is hardware or software that establishes and maintains a secure and effective internet connection. These devices link computers, phones, printers and other internet-compatible devices with various networks. They also block potentially dangerous data or users from entering secure networks.
Where can I find network devices?
You can find network devices in several places: online retailers, electronics stores, office supply stores, IT suppliers, manufacturers websites, local IT service providers.
What are the 7 pieces of network hardware?
The seven pieces of network hardware are routers, switches, modems, access points, firewalls, network interface cards, and hubs.



