Attackers use a variety of trajectories to infiltrate organizations with viruses and malware these days. There is a premium service from Microsoft Exchange called Exchange Online Advanced Threat Protection (ATP) that offers five distinct features that add additional layers of security to your email and documents:
- Safe Links
- Safe Attachments
- Spoof intelligence
- Quarantine
- Advanced anti-phishing capabilities
This blog post describes the first three of these features.
Availability
ATP is included only for users who are licensed for Office 365 Enterprise E5, Office 365 Education A5 and Microsoft 365 Business plans. If you don’t want to upgrade everyone to one of these plans, you can purchase ATP as an add-on license for US$2 per user per month. You can add ATP to the following Exchange and Office 365 subscription plans:
- Exchange Online Plan 1
- Exchange Online Plan 2
- Exchange Online Kiosk
- Exchange Online Protection
- Office 365 Business Essentials
- Office 365 Business Premium
- Office 365 Enterprise E1
- Office 365 Enterprise E3
- Office 365 Enterprise F1
- Office 365 A1
- Office 365 A3
Requirements
ATP can be used with any SMTP mail transfer agent, such as Microsoft Exchange Server 2013. For more information, check the “Supported browsers” and “Supported languages” sections in the Exchange Admin Center in Exchange Online Protection.
Safe Links
The Safe Links feature of ATP guards against malicious links in both emails and Office documents in real time. It is similar to the unified threat management of older edge-protection and web-protection firewalls, in which the URLs users clicked on were intercepted by the firewall and run through a scanning and hygiene process before the content was allowed to come into the network. With Safe Links, email entering or leaving the organization goes through Exchange Online Protection (EOP), which filters out spam and phishing messages it knows about and scans each message through a variety of antimalware detection engines.
When users click on links in messages that land in their inboxes, the ATP service checks the link and does one of the following:
- If the URL has been deemed by the ATP service to be safe, it is allowed to be opened.
- If the URL is on your organization’s “do not rewrite” list, the website simply opens when the user clicks the link. A “do not rewrite” list is good for internal systems and line-of-business applications that take certain actions based on URLs, like one-click expense report approvals.
- If the URL is on a custom block list that your organization configured, a warning page is displayed to the user.
- If the URL has been deemed by the ATP service to be malicious in nature, a warning page is displayed to the user.
- If the URL goes to a downloadable file and your organization’s ATP Safe Links policies are configured to scan such content, the ATP service will scan the file before downloading it.
To modify your Safe Links policy, take the following steps:
- Navigate to https://protection.office.com. Under Threat management, choose Policy and then click Safe Links.
- In the “Policies that apply to the entire organization” section, select Default and then click the pencil button to edit the policy configuration.
- In the “Block the following URLs” section, you can add sites that no one in your organization ought to be able to visit. (This won’t stop them from going to the site by directly entering its address into the address bar in their web browser, but it will prevent them from clicking a link in an email or document to visit it.)
- In the “Settings that apply to content except email” section, leave everything checked.
- Click Save.
When a user clicks a link in an email or Office document, they will see a message like this:
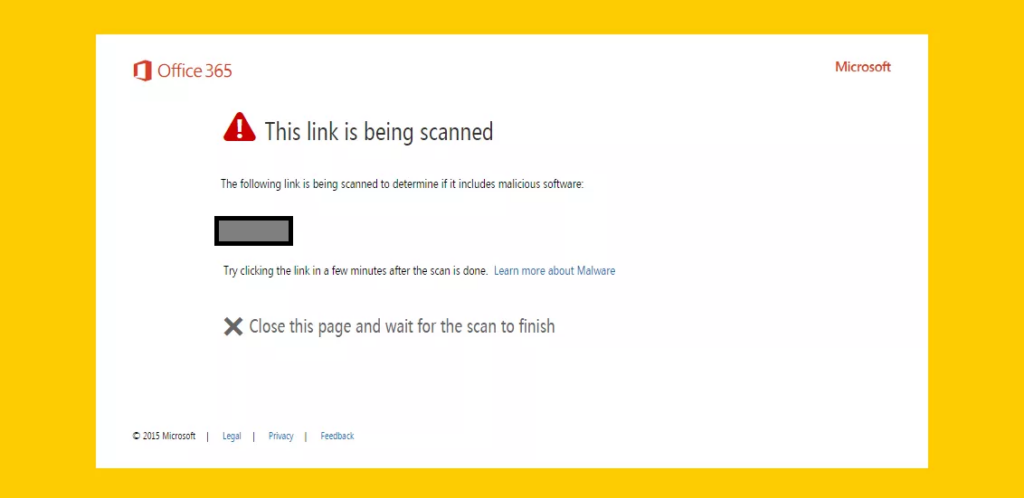
Figure 1. How Safe Links notifies a user that it is scanning a link
Safe Attachments
Scanning engines can miss unknown malware and viruses when they first break out, before they have been classified and the signatures have been updated. With Safe Attachments, messages with unsafe attachments — those that don’t match known signatures — are sent to a sandboxed virtual environment where they are securely opened. If the service detects suspicious activity like a virus or malware trying to execute, the message is rejected or quarantined. If no suspicious activity is detected, the message is released to the user.
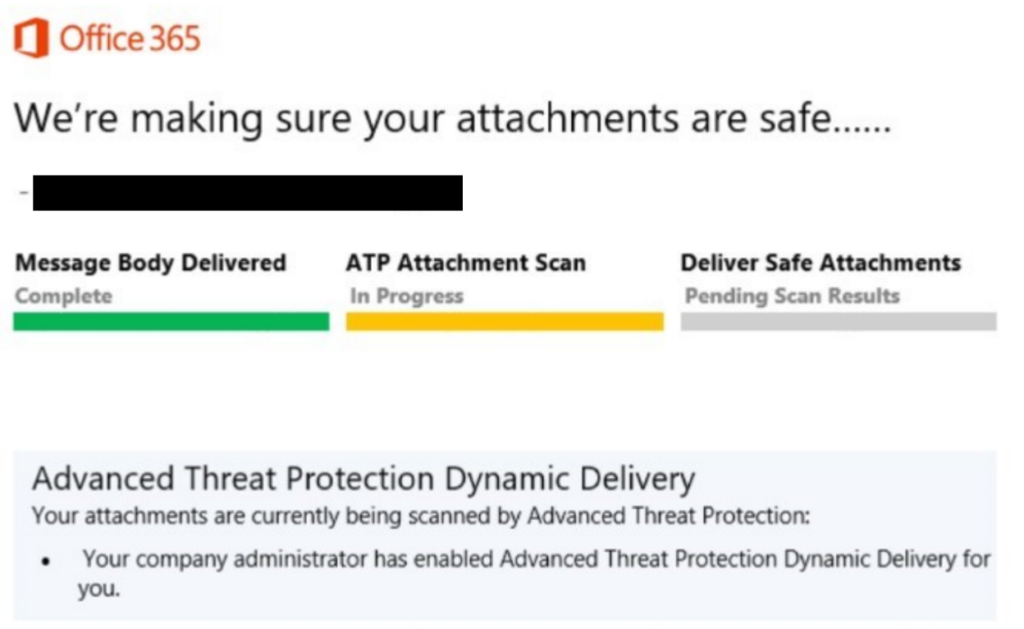
Figure 2. Scanning attachments with the ATP safe attachments service
To configure Safe Attachments policies, take these steps:
- Go to https://protection.office.com. In the left pane, under Threat management, choose Policy and then click Safe Attachments. Make sure that if you’re presented with the option to “Turn on ATP for SharePoint, OneDrive, and Microsoft Teams,” you do so. (You’ll want to allow at least 30 minutes for this to take effect across all of Microsoft’s global Office 365 datacenters.)
- Click the + sign to create a new Safe Attachment Policy, and then enter a name and description for the policy. The table below explains the available settings. I recommend dynamic delivery for most recipients. It’s the safest, it won’t delay the body of an email, and it is virtually transparent to users who are not in front of their computer all the time.
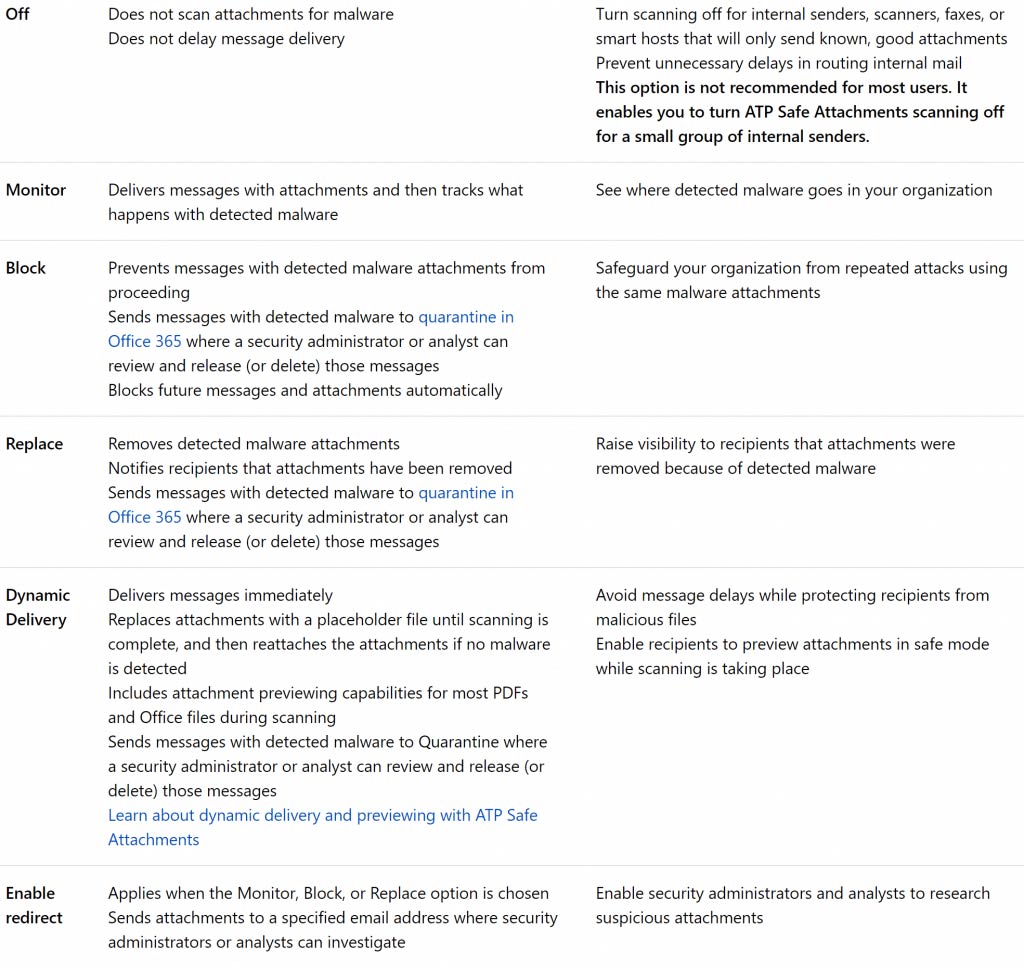
Figure 3. Safe Attachments policy options (image courtesy Microsoft Corporation)
Spoof Intelligence
Spoof intelligence spots mail that appears to be from a user account within one of your organization’s domains. Specifically, it detects mail with a From address (or with a sender field in the headers of a message) that matches one of the domains configured on your Office 365 tenant. Sometimes these messages can be legitimate — for example, you might send a marketing newsletter from a separate service like Aweber or Mailchimp, or your copier and scanner might send emails to your tenant and have a “From” address in your tenant. But other times it is someone impersonating an internal user in order to trick people into sending a check to pay a fake invoice, initiate a foreign wire transfer and so on.
Spoof intelligence collects all the suspicious senders it detects in your mail flow and presents them in one convenient location, where you can decide which senders you’ll allow to send mail into your tenant and which ones should be blocked. To review this list, go to the Security and Compliance page and click Anti-spam settings.
Conclusion
The ATP can’t thwart all malicious attacks but it’s a good tool that provides a robust zero-day protection against unknown malware and viruses. If you’re ready to learn about other Office 365 services that help protect sensitive data, check out this Managing Office 365 Data Loss Prevention blog post.
FAQ
What is Microsoft Defender for Office 365?
Microsoft Defender for Office 365 (formerly Advanced Threat Protection) is a cloud-based email security service that protects against sophisticated threats such as zero-day malware, phishing, and business email compromise. It extends Exchange Online Protection with advanced features including Safe Attachments, Safe Links, and threat investigation capabilities. Safe Attachments opens email attachments in a virtual environment to detect malicious behavior before delivery. Safe Links rewrites URLs to check them against Microsoft’s threat intelligence database when users click them. The service also provides spoof intelligence, impersonation protection, and detailed threat analytics. Plan 1 covers email protection while Plan 2 adds threat hunting, automated investigation, and response capabilities. This comprehensive approach addresses the reality that attackers are logging in, not breaking in, making email security crucial for protecting organizational data and identities.
How to configure Exchange Online Protection?
Configuring Exchange Online Protection requires administrative access to the Microsoft 365 security center and proper licensing. Start by accessing the Security & Compliance Center at protection.office.com and navigate to Threat Management policies. Configure anti-spam policies to set spam confidence levels, quarantine actions, and allowed/blocked senders lists. Set up anti-malware policies to define attachment filtering, malware detection responses, and administrative notifications. Create mail flow rules to handle specific scenarios such as external email warnings or attachment blocking. Configure connection filtering to allow or block specific IP addresses and enable directory-based edge blocking. Test your configuration using Microsoft’s built-in policy tester and monitor the threat protection status dashboard. Remember to configure user notifications for quarantined messages and train users on reviewing quarantine contents. Regular policy reviews ensure protection keeps pace with evolving threats.
How to enable Microsoft Defender for Office 365?
Enabling Microsoft Defender for Office 365 requires proper licensing and configuration through the Microsoft 365 security center. First, ensure users have Defender for Office 365 licenses assigned through the Microsoft 365 admin center. Access the security center at security.microsoft.com and navigate to Email & Collaboration policies. Create Safe Attachments policies by defining protected users, attachment scanning action (block, replace, or dynamic delivery), and timeout settings. Configure Safe Links policies to protect against malicious URLs in email and Office documents, enabling real-time URL scanning and user click protection. Set up impersonation protection policies to detect domain and user impersonation attempts. Enable spoof intelligence to protect against spoofed senders. Test policies using the configuration analyzer and simulate attacks using Microsoft’s attack simulation training. Monitor protection effectiveness through the threat protection status reports and adjust policies based on organizational needs and threat landscape changes.
Is Exchange Online Protection included in Office 365?
Exchange Online Protection (EOP) is automatically included with all Exchange Online subscriptions and most Microsoft 365 plans at no additional cost. This baseline protection provides anti-spam and anti-malware filtering for all email traffic. However, EOP offers basic protection compared to Microsoft Defender for Office 365, which requires separate licensing for advanced features. EOP includes connection filtering, recipient filtering, sender policy framework validation, and basic anti-phishing protection. It does not include Safe Attachments, Safe Links, or advanced threat hunting capabilities found in Defender for Office 365. Organizations with standard security requirements often find EOP sufficient, while those facing sophisticated threats or requiring compliance capabilities need the advanced features of Defender for Office 365. Understanding this distinction helps organizations choose appropriate protection levels without over-purchasing licenses they don’t need.
How to troubleshoot Safe Attachments not working?
Troubleshooting Safe Attachments requires systematic verification of policy configuration, user licensing, and mail flow. First, confirm affected users have Defender for Office 365 licenses assigned and policies applied correctly. Check the Safe Attachments policy settings in the security center to ensure the correct action is configured (block, replace, or dynamic delivery). Verify that attachment types aren’t excluded from scanning and that file size limits haven’t been exceeded. Review message headers for X-MS-Exchange-Organization-SkipSafeAttachmentProcessing to identify bypassed messages. Check if transport rules or other mail flow rules are interfering with Safe Attachments processing. Monitor the threat protection status report to confirm attachments are being processed. For persistent issues, use message trace to track specific emails through the protection pipeline. Remember that Safe Attachments adds processing time, so dynamic delivery helps balance security with user experience. Test with known-bad files to verify protection is functioning correctly.



