Group Policy is a feature in Windows that allows administrators to manage and configure operating system components, application settings, and user environments across Active Directory (AD) environments. This article examines both Microsoft’s native Group Policy tools and leading third-party Group Policy management solutions. It aims to enhance Group Policy’s effectiveness and simplify its application, offering a comprehensive look at how to leverage Group Policy for better control and management within Windows environments.
Group Policy Management Console
The Group Policy Management Console (GPMC) is a powerful Microsoft Management Console snap-in designed for Active Directory administrators. It allows for the centralized management of Group Policy Objects (GPOs) across an Active Directory environment. With its graphical user interface, administrators can manage GPOs without needing direct access to domain controllers. The GPMC is included in Windows client operating systems and was previously part of the Remote Server Administration Tools (RSAT). GPMC also offers a PowerShell module for automating Group Policy tasks, enhancing administrative efficiency and flexibility in policy management across your domain or forest.
GPMC and Group Policy Management Editor
GPMC lets you create, edit, delete, and link Group Policy objects (GPOs) and link them to AD domains, sites, and organizational units (OUs). The console allows for the assignment of GPOs to specific users or groups and the delegation of permissions to manage these policies effectively. Within the GPMC you can explore every setting specified in a Group Policy Object (GPO). The example below shows the settings within the Default Domain Policy for the Fabrikam domain. Note that there are configured settings for both the computer and user side.
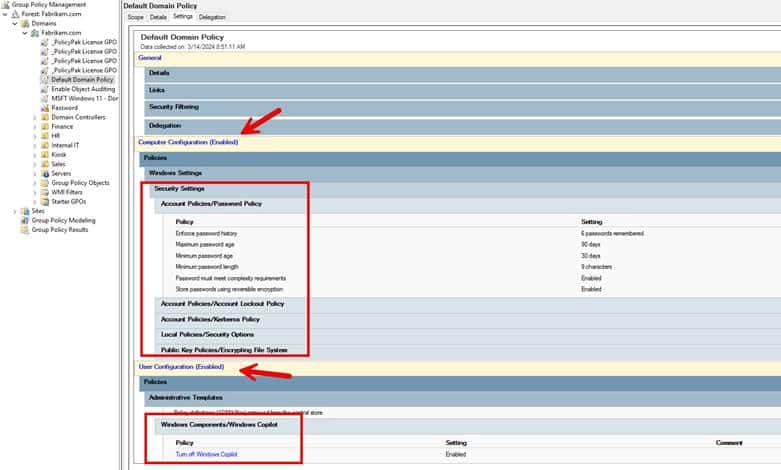
Other GPMC features include Windows Management Instrumentation (WMI) filters for added assignment granularity and the ability to enforce GPO links to bypass inheritance restrictions.
To configure settings within a GPO for the first time or modify them you will need the Group Policy Management Editor which works in conjunction with GPMC. It is used to edit the policy settings of an individual GPO. Here you can configure things such as password policies, user access permissions, software installations, desktop environments, network configurations, and security settings. The screenshot below shows the Editor used to specify two policy settings: one called “Blocks external extensions from being installed” and the other called “Control which extensions cannot be installed.” When Enabled they are activated to perform their function.
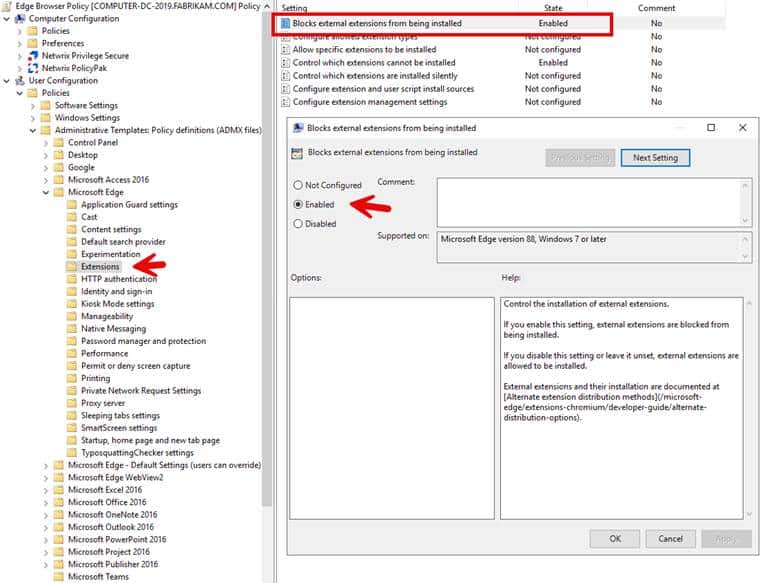
Together, the GPMC and Group Policy Management Editor work together to empower administrators to effectively manage their Active Directory computers and users, enhancing both security and productivity within their organizations.
Resultant Set of Policy (RSoP)
It doesn’t take long for group policy to get complicated when you start creating group policy objects for a large domain with multiple levels of organizational units. The GPMC’s “Group Policy Results” reporting is a built in “Resultant Set of Policy (RSoP)” tool that helps administrators understand which policies are applied as well as their source.
The GPMC’s “Group Policy Results” tab gives you the effective RSoP, which can help diagnose policy-related issues by reporting the combined effect of all Group Policies active for a specific environment, making it easier to troubleshoot and ensure the correct policies are applied to the right users and computers.
Note this is different than the GPMC’s “Group Policy Modeling” tab which can simulate results of users or computers moving around Active Directory.
The screenshot shows the result of RSoP for what policies would affect the user account, Administrator, when logged on to Computer-DC-2019.
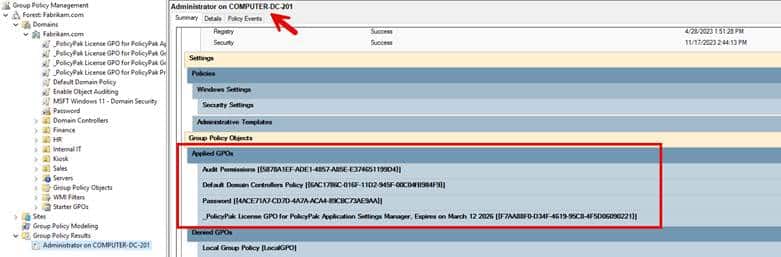
Another way to generate RSoP details would be by using the command line tool ‘gpresult /R’ using a command prompt or PowerShell.
Tools from SDM Software
SDM Software makes an assortment of tools and utilities for Group Policy management, many of which you can download on a trial basis. These Group Policy and GPO tools are designed to enhance and simplify the management of Group Policies across your Windows environments.
GPO Migrator tool is designed to help administrators manage and migrate GPOs more efficiently. This GPO tool simplifies the process of moving GPOs from one environment to another, such as from a test to a production environment, or between domains in different forests. This tool is especially useful for organizations undergoing restructuring, mergers, or upgrades, where GPOs need to be consolidated or reorganized without losing their settings or integrity.
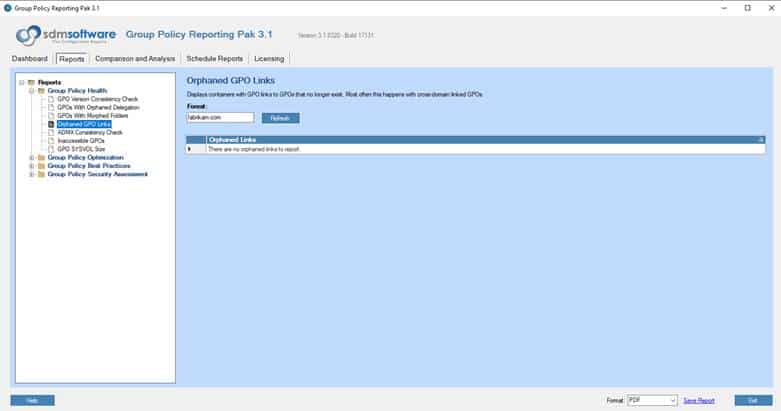
SDM GPO Policy Reporting Pak offers comprehensive reporting and analysis capabilities for GPOs. It enables administrators to generate detailed reports on GPO settings, configurations, and compliance status, facilitating better management, auditing, and compliance with organizational policies and standards. In the screenshot below we have run a report to find any GPOs that have orphaned links.
Group Policy Auditing and Attestation (GPAA) is a tool designed for comprehensive monitoring and control over Group Policy changes. It provides real-time alerts and audits for all Group Policy modifications, including detailed comparisons of settings before and after changes. GPAA addresses the critical questions of “Who, What, When, and Where” in Group Policy auditing. Additionally, it features capabilities for GPO rollback and attestation, ensuring clear ownership and history of GPOs, enhancing security and compliance management within your IT environment.
Group Policy Compliance Manager (GPCM) offers a comprehensive tool for managing and reporting on Group Policy deployment statuses across your network. It ensures your Windows systems are configured as intended for desktop security and other critical settings. GPCM helps identify discrepancies, providing insights into configurations that don’t meet expected standards and the reasons behind them, enhancing your network’s security and compliance posture.
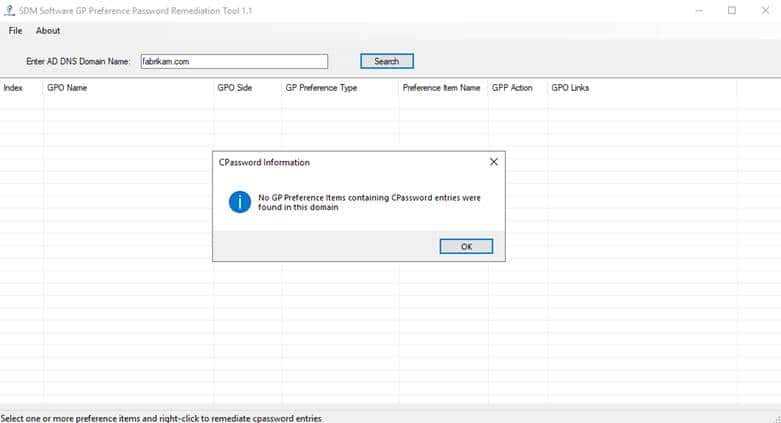
Group Policy Preference Password Remediation Utility is a GPO management tool that helps you find and fix vulnerable “cPassword” entries in Group Policy Preferences across your Active Directory domain. It not only identifies these entries but also offers an option to remediate them by removing the cPassword entries from the Group Policy Object (GPO). Before making any changes, the utility backs up the GPOs you’re about to fix, ensuring you have a recovery point if needed. A screenshot of the utility is shown below.
Netwrix Endpoint Policy Manager
Netwrix Endpoint Policy Manager significantly enhances Group Policy management by offering a comprehensive solution for configuring and securing applications, operating systems, and user settings beyond the capabilities of native Group Policy. It facilitates granular control over application settings, ensures the enforcement of security policies across an organization’s IT environment, and maintains compliance with corporate standards, even for remote or mobile devices. PolicyPak can enforce settings on computers whether they are on the network or not, providing administrators with a powerful tool for ensuring system security and compliance.
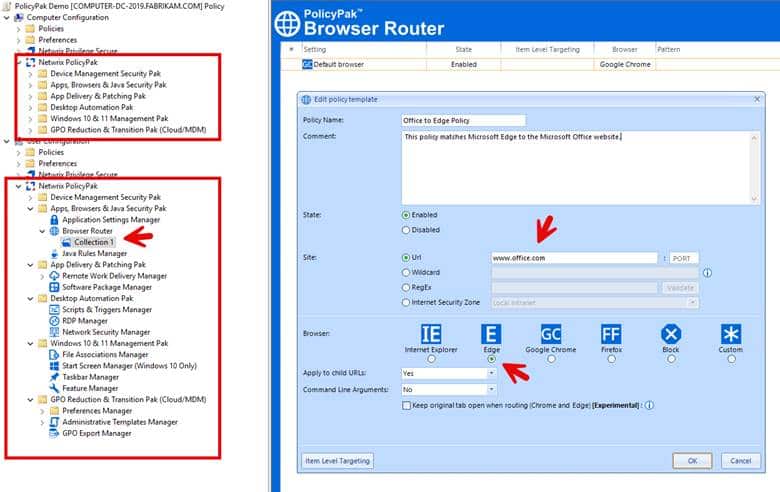
Netwrix Endpoint Policy Manager integrates with the existing Group Policy Management Console (GPMC) to extend its capabilities. PolicyPak leverages Group Policy to distribute its custom Paks, which contain specific settings for applications and Windows configurations, ensuring they are applied consistently across all targeted devices. This integration makes it easier for administrators to manage their environments by using a familiar tool while benefiting from the enhanced functionality that PolicyPak provides. The screenshot below shows the various Paks and components available on both the computer and user side of Group Policy. The Browser Router feature is set up assign Google Chrome as the default internet browser, while specifically directing users to use Microsoft Edge when accessing www.office.com.
Netwrix Endpoint Policy Manager allows administrators to extend group policy coverage to more than just domain-joined machines. For instance, you can export any or all of your Group Policy settings and import them into your preferred MDM service, like Intune to give those machines the settings granular coverage of Group Policy that your MDM service doesn’t have.
With PolicyPak, you can even apply group policy settings to standalone non-domain joined and non-MDM enrolled Windows desktops as well. PolicyPak also provides full Group Policy settings coverage. Beyond that, PolicyPak can manage more than 300 third party applications such as Java and Adobe products to ensure that applications are optimized and secure for your user experiences.
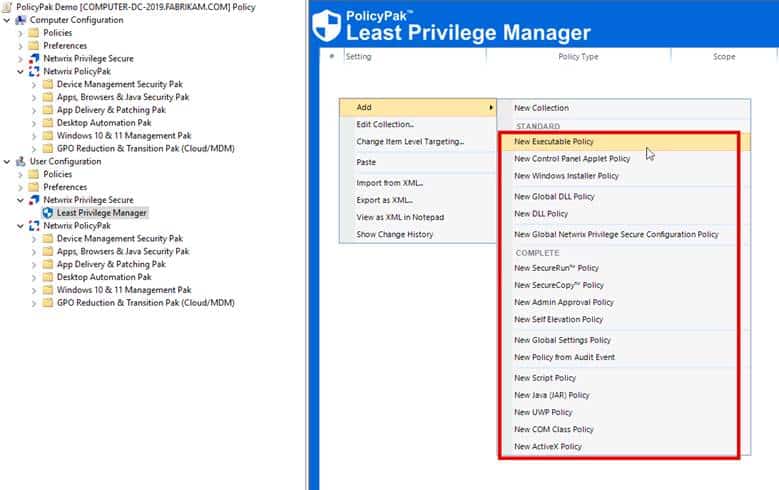
PolicyPak also includes the Least Privilege Security Pak that empowers administrators to enforce least privilege security without hampering user productivity. It enables the elevation of application privileges, when necessary, and allows specific tasks to run with elevated rights, mitigating the risks associated with excessive user privileges. With PolicyPak, you can dissolve blanket local admin rights for standard users while allotting granular admin rights to designated applications and Windows features. You can also enforce Allow List like coverage of applications and executables with a few clicks of the mouse. The screenshot below shows the many types of PolicyPak Least Privilege Manager security policies you can create.
Netwrix Endpoint Policy Manager can work alongside your on-prem Active Directory and Group Policy, alongside your MDM service like Microsoft Intune, and also comes in a SaaS edition that allows you to centrally manage everything from the cloud. Whether you need to manage traditional desktops, virtual desktops, thin clients, domain joined devices or non-domain joined machines, Netwrix Endpoint Policy Manager can give you the Group Policy management tools you need to manage your hybrid environment.
Netwrix Auditor for Active Directory
Netwrix Auditor for Active Directory delivers detailed auditing capabilities for Active Directory and Group Policy. It offers in-depth security insights, tracking all AD and Group Policy changes, including comprehensive who, what, when, and where details, plus before-and-after values. Its Enterprise Overview dashboard visually represents events over time, allowing for deep dives into specifics and report generation. The platform also generates GPO state-in-time reports, facilitates comparison of GPO settings across different times, identifies redundant settings to optimize logon processes, and provides customizable report filters for targeted information retrieval.
Using a series of built-in reports, you can drill down to get detailed information about GPOs. For example, you could run a report to find all current GPO settings that affect password policy in the domain and compare the results with a past point in time to see if any changes were made. Another report shows whether there are duplicate settings in GPOs. Tracking down redundant settings can help improve logon efficiency and simplify operations. All reports offer filters that let you narrow down the results so you can find exactly the information you need.
Netwrix Auditor also offers compliance assurance for standards like GDPR, PCI DSS, and HIPAA by integrating with security systems and alerting on AD and GPO changes. Its main benefit over similar tools lies in comprehensive auditing for Active Directory, crucial for Group Policy security. Ensuring AD’s security and compliance is essential, as Group Policy’s effectiveness can be undermined if AD is compromised. Netwrix Auditor provides not just policy management but complete visibility and control over your Active Directory’s security posture.
Netwrix Auditor can also be integrated with Netwrix Endpoint Policy Manager. This integration enables users to view PolicyPak-related GPO changes in Netwrix Auditor directly from the Group Policy Object you’re editing when the PolicyPak MMC snap-in is installed. The integration streamlines GPO change validation, auditing, and review, eliminating the need to manually access a separate reporting platform.
Microsoft Security Compliance Toolkit
Microsoft’s free Security Compliance Toolkit (SCT) contains baseline security templates for all supported versions of Windows and Windows Server that can be used to create Group Policy objects or configure local policy. These baselines provide recommended security settings that align with industry best practices and standards, aiming to minimize vulnerabilities. In the context of Group Policy, the SCT’s baselines can be imported into Group Policy Objects (GPOs) to efficiently apply these settings across networked computers, ensuring that the organization’s systems are configured for optimal security and compliance.
SCT is updated regularly and includes comprehensive documentation of recommended Group Policy settings, along with spreadsheets that show you the differences between settings in the current and previous releases so that you can quickly understand what has changed. You can download the latest baseline security templates here. Policy Analyzer and Local Group Policy Object (LGPO) tools. Policy Analyzer helps compare different GPO sets or versions, enabling checks against local policies and registry settings. You can then export the results into a spreadsheet. Local Group Policy Object (LGPO) is a command-line tool for automating the management of local policy on systems that aren’t joined to an Active Directory domain.
Advanced Group Policy Management
Advanced Group Policy Management (AGPM) is part of the Microsoft Desktop Optimization Pack (MDOP), which is available to Software Assurance customers only. It extends the features of the Group Policy Management Console by providing version control, role-based administration, change approval workflows, and detailed change tracking for GPOs. This can significantly improve the ability to manage, edit, and deploy GPOs while ensuring compliance and minimizing the risk of errors. AGPM facilitates a more structured, secure, and auditable approach to Group Policy management, making it easier to manage changes and roll back unwanted or problematic GPO changes. AGPM is mainly designed for large domain environments that have multiple teams of Group Policy admins.
Microsoft’s native tools for group policy management might be enough for SMBs, but larger organizations might need additional features and capabilities. The tools discussed here each bring unique functions, offering administrators the ability to customize their Group Policy management approach to fit their organization’s needs. While some tools are available for free, others may require a licensing fee. Trying out some of these tools could help you determine which one best meets your requirements.



