Network administrators often need to adjust the configuration settings of their Cisco switches and routers. However, because the running configuration file is stored in volatile memory, any changes made will be lost if the device is powered off or restarted. In this article, we’ll show you how to copy the running configuration to the startup configuration to ensure these modifications are retained. We’ll also demonstrate how to copy the running configuration file to the startup configuration to preserve these changes.
The Cisco IOS
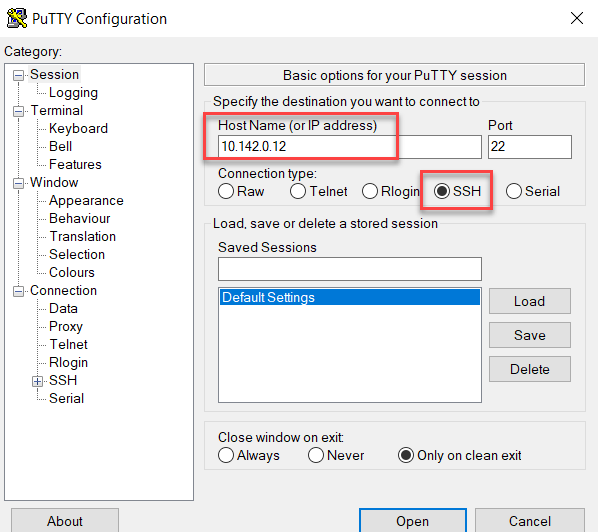
Cisco IOS, or Internetwork Operating System, is the core software powering Cisco routers and switches, enabling network connectivity, security, and advanced features. It also provides a Command Line Interface (CLI) that allows network admins to enter commands into a terminal emulation program. The CLI can be accessed via three methods: the console, Telnet, and Secure Shell (SSH). The commands available depend on the Cisco mode that the user is currently running. In this instance, we will use Putty to remotely connect to a Cisco switch on a local network using SSH. The use of Telnet to configure a device is insecure and should not be used for regular deployments. Initial setup might require the us of a console or telnet connection.
Cisco Modes
The various modes on Cisco devices provide structured, hierarchical access levels to ensure that users can only execute commands within their permissions. Restricting access is critical to your network’s health because any misconfigurations made to your devices can degrade performance or even disrupt connections. Users can confirm what mode they are in by using the CLI prompt.
Here’s a concise overview of the various Cisco modes, their corresponding prompts, and the actions permissible within each.
EXEC mode (user mode)
- Prompt: Router>
- This is the initial mode when a user logs into a Cisco device. It gives the user limited access to the system, allowing them only to view configuration settings and perform basic troubleshooting commands such as ping and traceroute.
Privileged EXEC mode (enable mode)
- Prompt: Router#
- This mode provides higher-level access to view configurations and statistics. It is accessed by entering the “enable” command from the User EXEC Mode. It allows a user to view all settings and execute privileged commands such as “reload,” which tells the switch to reboot the Cisco IOS.
- Privileged access should be password-protected to prevent unauthorized access.
Global Configuration mode
- Router(config)#
- Commands made in Global Configuration mode affect the entire device. While EXEC and Privileged EXEC are read-only modes, Global Configuration mode gives the user writable access to modify the active configuration file. To use Global Configuration mode, enter Privileged EXEC Mode and then execute the “configure terminal” command. Numerous shortcuts are also accepted, such as config t.
Interface Configuration mode
- Router(config-if)#
- Users can access this mode from the Global Configuration mode to configure specific interfaces by entering commands like “interface FastEthernet 0/0.”
These are the modes that Cisco support users will most commonly use. Other modes include Line Configuration mode, Router Configuration mode, VLAN Configuration mode, and Subinterface Configuration mode. Below is a screenshot of our SSH session to a switch called Cisco Switch 101. Here, the user transitioned from Privileged EXEC mode to Global Configuration mode.

The “Show” Command
To change any of the device’s configuration settings, you must first know what the settings are. This makes the “show” command especially helpful, as it is used to display the current configuration and status of any Cisco device. It can be executed from the User EXEC mode and the Privileged EXEC mode. Some of the most common examples of this command include the following:
show running-config — Displays the current active configuration of the device.
show startup-config — Shows the configuration that will be loaded the next time the device restarts.
show version — Shows detailed information about the Cisco device’s software version, uptime, and hardware details.
Where Configuration Files are Stored
Cisco routers and switches utilize various types of memory to handle designated functions, and they store different kinds of information. The running configuration and startup configuration are stored in separate types of memory. Here’s a summary of the primary memory types and how each one is used.
- RAM (Random Access Memory) — This is volatile memory where the device stores its running configuration, routing tables, and operational data, all of which is lost upon a reboot.
- ROM (Read-Only Memory) — ROM stores a bootstrap program that is loaded when the switch first powers on. This program locates the full Cisco IOS image and loads it into RAM.
- Flash memory — This memory can be either inside the device or on a removable memory card. Flash memory stores fully functional Cisco IOS images and is the default location where the switch searches for its Cisco IOS at boot time. Flash memory also can be used to store other files, including backup copies of configuration files.
- NVRAM (Nonvolatile RAM) — NVRAM stores the initial or startup configuration file that is used when the Cisco device is powered on or reloaded.
Understanding the Two Configurations
First, let’s explain the purpose of each configuration.
- Running Configuration — This is the active configuration stored in the device’s RAM. Any changes made to the device are immediately reflected here. Since RAM is dynamic, a reboot or loss of power will cause the device to revert to its last saved configuration.
- Startup Configuration — This is the configuration that the device loads upon startup and is stored in the device’s NVRAM. Any changes made here are persistent through reboots.
Both configurations feature identical in settings. Below is an example of the running-config of our test switch.
Cisco Switch 101# show running-config Building configuration... Current configuration: 1067 bytes ! ! Last configuration change at 11:23:54 UTC Tue Feb 17 2023 by admin ! version 15.1 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname Cisco Switch 101 ! boot-start-marker boot-end-marker ! ! enable secret 5 $1$mERr$2T3mEi2Kt7PF9Fv9A4A2.. ! no aaa new-model ! ! ip cef no ip domain lookup ! ! interface FastEthernet0/0 ip address 10.142.0.12 255.255.255.0 duplex auto speed auto ! interface FastEthernet0/1 no ip address shutdown duplex auto speed auto ! ! ip default-gateway 10.142.0.1 ip classless ! line con 0 exec-timeout 0 0 privilege level 15 logging synchronous line aux 0 line vty 0 4 login ! end
Copy running-config startup-config
In this example, we will first rename our switch to “cisco” using the “hostname” command. Now we want to save the running configuration to the startup configuration by using the “copy” command as shown below.
copy running-config startup-config
You can also use the abbreviated command:
Copy run start
This will overwrite the current startup config file.
You can also copy the running config to an external source such as a TFTP server, as shown in the example below for our newly renamed switch.
cisco# copy running-config tftp: Address or name of remote host []? 10.137.14.55 Destination filename [running-config]? !! cisco#
A breakdown of this command sequence is as follows:
1. The command “copy running-config tftp:” initiates the process.
2. When prompted for the TFTP server’s address, “10.137.14.55” is provided.
3. The switch then asks for the destination filename. Pressing “Enter” here will create the default name “running-config.”
4. The “!!” indicates that the transfer was successful.
You can also copy the startup config to a TFTP server. Security best practices recommend that you maintain external backups of configurations for all your Cisco devices to prepare for potential device failures and other disasters.
Erase the contents of NVRAM
Rebooting or powering down a Cisco device will erase its running config settings. If you want to erase the startup config file contained within the NVRAM, you can use the command:
cisco# erase startup-config
The device will then prompt you to confirm that you want to perform the action.
Once the process is completed, the startup configuration stored in NVRAM will be deleted. If you reload the device without first saving another configuration to the startup configuration, the device will boot with its default settings. The default settings for a Cisco switch or router are as follows:
- All interfaces are enabled.
- Auto-negotiation is enabled for ports that can use it (duplex auto and speed auto).
- All interfaces are part of VLAN 1.
You can then add configuration settings such as the device’s hostname and IP address, subnet mask, and default gateway.
Why You Need to Monitor Cisco Configuration Changes
Improper modifications or unauthorized access to your Cisco network devices can result in reduced network efficiency and business disruptions. Therefore, it is crucial to implement consistent audit processes and vigilantly monitor activity within your network infrastructure.
Netwrix Auditor for Network Devices provides complete visibility into your network infrastructure and alerts you about events you consider most dangerous. This clear, actionable information enables you to significantly simplify your investigations into security incidents. Here are just some of the steps you can take toward greater network security with a Cisco auditing tool from Netwrix:
- Audit attempts to log on to network devices and verify that each successful logon is fully authorized.
- Monitor password resets and configuration changes.
- Stay aware of hardware malfunctions with automatic alerts.
- Track individual network scans to quickly determine whether each instance was a planned network health check an attacker conducting reconnaissance before attempting a data breach.
It isn’t enough to save your running configuration settings. You need to monitor them and other aspects of your network infrastructure to ensure normal, secure operations for your business.



