With cyber threats rapidly evolving and data volumes expanding exponentially, many organizations are struggling to ensure proper security. Implementing a solid cybersecurity framework (CSF) can help you protect your business.
One of the best frameworks comes from the National Institute of Standards and Technology. This guide provides an overview of the NIST CSF, including its principles, benefits and key components.
NIST Cybersecurity Framework Purpose and Benefits
The NIST Framework offers guidance for organizations looking to better manage and reduce their cybersecurity risk. It is important to understand that it is not a set of rules, controls or tools. Rather, it offers a set of processes that can help organizations measure the maturity of their current cybersecurity and risk management systems and identify steps to strengthen them.
Implementing the NIST cybersecurity framework is voluntary, but it can be immensely valuable to organizations of all sizes, in both the private and public sectors, for several reasons:
- It is easy to understand and use.
- It’s meant to be customized — organizations can prioritize the activities that will help them improve their security systems.
- It is risk-based — it helps organizations determine which assets are most at risk and take steps to protect them first.
Benefits of NIST CSF
Use of the NIST CSF offers multiple benefits. In particular, it can help you:
- Gain a better understanding of current security risks
- Prioritize the activities that are the most critical
- Identify mitigation strategies
- Evaluate potential tools and processes
- Measure the ROI of cybersecurity investments
- Communicate effectively with all stakeholders, including IT, business and executive teams
Components of the NIST Cybersecurity Framework
The NIST CSF includes three components:
- Core
- Implementation Tiers
- Profiles
Core
The core lays out high-level cybersecurity objectives in an organized way, using non-technical language to facilitate communication between different teams. At the highest level, there are five functions:
- Identify — Determining the cybersecurity risks to all company assets, including personnel, systems and information
- Protect — Implementing systems to safeguard the most vital assets
- Detect — Spotting active cybersecurity events that could pose a threat to your environment
- Respond — Taking action against threats to prevent or mitigate damage
- Recover — Restoring capabilities or services damaged by a threat
Each function is divided into categories, as shown below. There 23 NIST CSF categories in all.
Each category has subcategories — outcome-driven statements for creating or improving a cybersecurity program, such as “External information systems are catalogued” or “Notifications from detection systems are investigated.” Note that the means of achieving each outcome is not specified; it’s up to your organization to identify or develop appropriate measures.
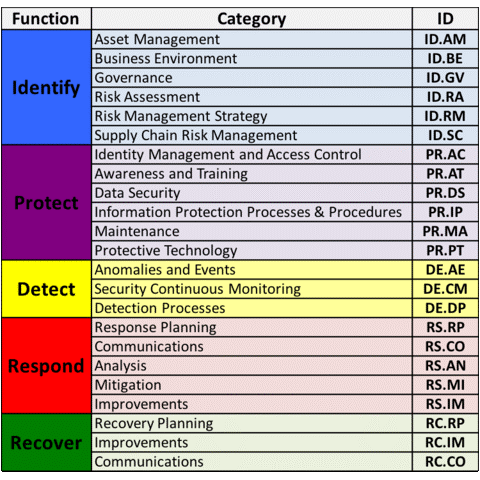
NIST CSF Core Functions and Categories
Implementation Tiers
The NIST CSF has four implementation tiers, which describe the maturity level of an organization’s risk management practices. In other words, they help you measure your progress in reducing cybersecurity risks and assess whether your current activities are appropriate for your budget, regulatory requirements and desired risk level. The tiers are:
- Tier 1: Partial — Informal, nonexistent or unsystematic risk management methods
- Tier 2: Risk Informed — Partial, isolated implementation or unfinished risk management processes
- Tier 3: Repeatable — Formal and structured policies and procedures and robust risk management programs
- Tier 4: Adaptive — Responsive risk management programs that are continuously adapted and improved
Remember that it’s not necessary — or even advisable — to try to bring every area to Tier 4. Instead, determine which areas are most critical for your business and work to improve those. NIST CSF suggests that you progress to a higher tier only when doing so would reduce cybersecurity risk and be cost effective.
Profiles
Profiles are essentially depictions of your organization’s cybersecurity status at a moment in time. Organizations often have multiple profiles, such as a profile of its initial state before implementing any security measures as part of its use of the NIST CSF, and a profile of its desired target state. These profiles help you build a roadmap for reducing cybersecurity risk and measure your progress.
Each profile takes into account both the core elements you deem important (functions, categories and subcategories) and your organization’s business requirements, risk tolerance and resources. But profiles are not meant to be rigid; you may find that you need to add or remove categories and subcategories, or revise your risk tolerance or resources in a new version of a profile.
Getting Started with NIST CSF
NIST offers an Excel spreadsheet that will help you get started using the NIST CFS. The spreadsheet can seem daunting at first. One way to work through it is to add two columns: Tier and Priority. In the Tier column, assess your organization’s current maturity level for each subcategory on the 1–4 scale explained earlier. Use the Priority column to identify your most important cybersecurity goals; for instance, you might rate each subcategory as Low, Medium or High. This webinar can guide you through the process.
As you move forward, resist the urge to overcomplicate things. Trying to do everything at once often leads to accomplishing very little. Remember that the framework is merely guidance to help you focus your efforts, so don’t be afraid to make the CSF your own.
Also remember that cybersecurity is a journey, not a destination, so your work will be ongoing. With these lessons learned, your organization should be well equipped to move toward a more robust cybersecurity posture.
FAQ
- What is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework (CSF) is a set of voluntary guidelines that help companies assess and improve their cybersecurity posture.
- What is the NIST framework used for?
The framework helps organizations implement processes for identifying and mitigating risks, and detecting, responding to and recovering from cyberattacks.
- Who should use the NIST Cybersecurity Framework?
Organizations of any industry, size and maturity can use the framework to improve their cybersecurity programs.
- Should our organization implement the NIST Cybersecurity Framework?
You should consider implementing NIST CSF if you need to strengthen your cybersecurity program and improve your risk management and compliance processes.
- What are the five elements of the NIST cybersecurity framework?
The NIST CSF has five core functions: Identify, Protect, Detect, Respond and Recover.
- What are the three parts of the NIST cybersecurity framework?
The NIST CSF consists of three main components: core, implementation tiers and profiles.



