Weak or stolen passwords remain a leading entry point for attackers targeting Active Directory. Strong password policies — covering length, complexity, reuse, lockout, and auditing — are essential to reduce account takeover risks and ensure compliance. Modern best practices favor long, complex passwords, supported by tools like self-service resets and policy enforcement, to balance security with usability.
One of the most common ways for attackers to slip into a corporate network is by compromising the username and password of a legitimate user account. Usernames are typically trivial to guess because they follow an established standard in a given organization, such as FirstnameLastname@domain.com.
Unfortunately, compromising basic passwords is also surprisingly easy for threat actors today. For example, they can run a program that tries out various potential passwords for a particular user account. When they hit the right one, they can slip into the network and begin moving laterally to steal sensitive data, unleash ransomware, or cause other damage.
Accordingly, it’s essential to establish a strong password policy that makes passwords difficult to guess. If your organization uses Active Directory (AD) as its primary identity store, this article can help. It explains the available domain password policy settings in AD, shows how to check your current policy, and details the modern password policy best practices to follow. Then it explores how third-party solutions can help you reap the benefits of strong password policies without frustrating users or increasing helpdesk call volume.
Benefits of Strong Password Policies
Password policies set standards for password composition, such as minimum password length and complexity requirements. They can also prevent the reuse of previous passwords, control how often passwords must be changed, and even ensure that an excessive number of failed login attempts will result in account lockout.
Having strong and consistent password requirements for all user accounts policy can significantly reduce the risk of account compromise by thwarting password spraying, brute force, and credential-stuffing attacks. Moreover, having strong password policies is necessary for compliance with a wide range of regulations and industry standards, such as HIPAA and GDPR.
How to Configure Active Directory Password Policies
How to Configure Your Password Policy
To configure the Password Policy, open the Group Policy Management Console (GPMC) on a Windows server and navigate to Computer Configuration > Windows Settings > Security Settings > Account Policies. Select Password Policy and configure each of the policy settings on the right.
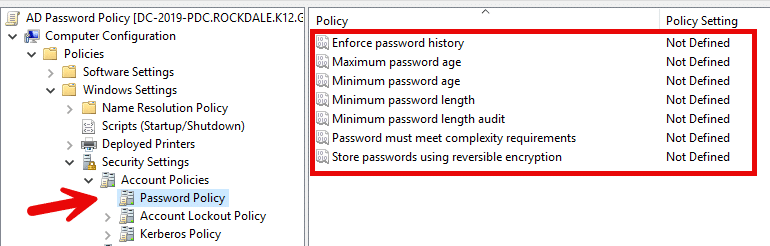
What settings should you choose? Approaches to password management have evolved significantly in recent years, with current best practices placing less emphasis on frequent password changes and more on password strength. The default settings from Microsoft should be regarded as a starting point; for strong security and compliance, consider the following guidance:
| Setting | Description | Default | Best Practices |
| Enforce password history | The number of unique passwords a user must create before reusing an old password | 24 | Enforce password history to prevent users from reusing old passwords repeatedly. |
| Maximum password age | How long a password can exist before it expires and the user must choose a different one | 42 days | Consider setting a high maximum password age and forcing users to change their passwords only when an event like a breach makes it prudent. |
| Minimum password age | How long a password must exist before the user is permitted to change it | 1 day | Keep the default setting to prevent users from circumventing the “enforce password history” setting by performing multiple password resets in a row in order to reuse a preferred password. |
| Minimum password length | The fewest number of characters a password can have | 7 | Microsoft recommends a setting of at least 12 characters because modern password cracking tools can crack 8-character strings in seconds. |
| Minimum password length audit | Allows administrators to audit password changes that would violate a potential new minimum password length policy before actually enforcing it. | 1 | Microsoft recommends leaving the auditing policy enabled for three to six months to detect all software that does not support the proposed minimum password length. |
| Password must meet complexity requirements | Controls whether passwords must meet the following two requirements: A password may not contain the user’s account name value or display name.A password must include characters from 3 of the following categories:Uppercase letters Lowercase letters Base 10 digits Special characters, such as $ or % | Enabled | Keep the password complexity setting enabled. Requiring passwords to meet complexity requirements can slow down automated attacks and reduce the likelihood of users reusing passwords across multiple accounts. |
| Store passwords using reversible encryption | Supports apps that require users to enter a password for authentication | Disabled | Keep this setting disabled to prevent attackers from decrypting passwords that they manage to steal. |
How to Configure Your Account Lockout Policy
You should supplement your Password Policy with an Account Lockout Policy to ensure that adversaries do not get unlimited attempts to guess an account password.
In GPMC, under Account Policies, select Account Lockout Policies. The available settings will appear on the right. In particular, you can specify how many failed logon attempts will trigger a lockout and how long the lockout will last.
Account lockout duration: The number of minutes that an account will be locked once the maximum number of failed login attempts has been reached.
Account lockout threshold: The number of failed login attempts that will trigger a lockout of the account
Allow Administrator account lockout: Determines whether the built-in Administrator account will be subject to the account lockout policy.
Reset account lockout counter after: Determines the number of minutes that must elapse after a failed login attempt before the failed login attempt counter is set back to zero.
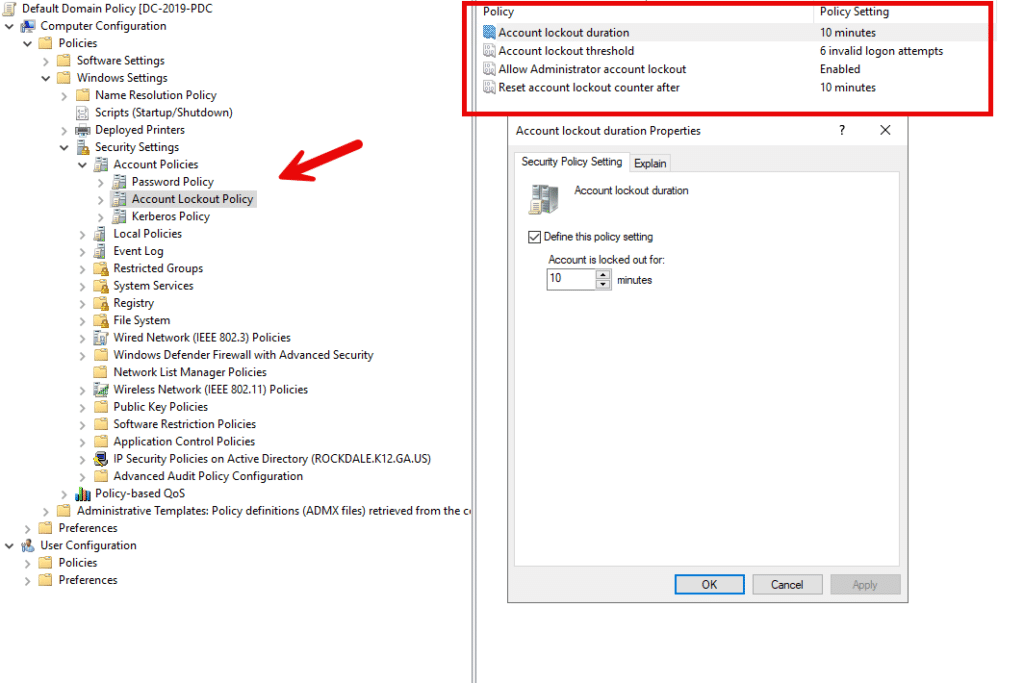
How to Modify Your Password Policies
At some point, you may need to update your Password Policy or Account Lockout Policy. For instance, you might want a different setting after a security incident or need to comply with new regulatory requirements. Modifying your existing password policy GPO is as easy as returning to GPMC and altering the settings. The process takes mere minutes to complete.
How to Create Different Password Policies for Different Groups
Active Directory supports fine-grained password policies, which enable you to apply different policies to different groups and users. (Note that your forest functional level must be at least Windows Server 2008.) For example, you can require high-risk groups like admins to have longer passwords and change them more frequently than other users.
You can create and manage fine-grained password policies in two ways:
- In Active Directory Management Center (ADAC), click on your domain, navigate to the System folder, click on the Password Settings container, and configure a Password Settings object (PSO). Then apply the PSO to the desired groups.
- Alternatively, you can use the PowerShell command New-ADFineGrainedPasswordPolicy.
How to Monitor and Troubleshoot Password Policy
How to Check Password Policy in Active Directory
You should keep a close eye on your Active Directory password policy settings. Methods for doing this include the following:
- Group Policy Management Console — One option is to use GPMC, as shown earlier.
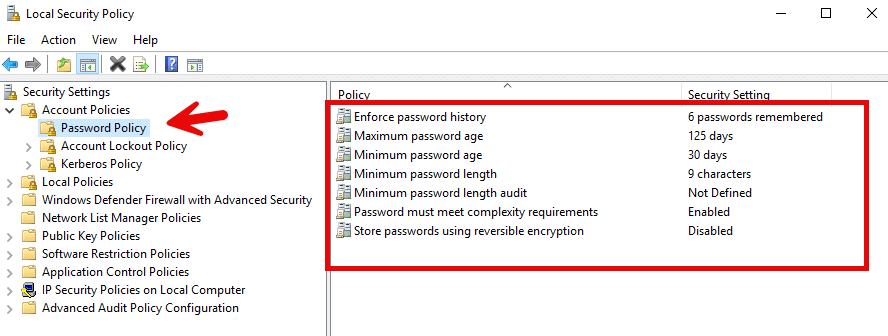
- Local Security Policy — To open this tool on a domain-joined computer, type secpol.msc in the Run dialog or search bar. Then navigate to the Password Policy settings.
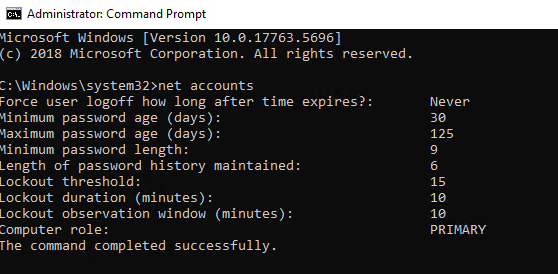
- Command prompt — You can open a command prompt with administrative privileges and use the command net accounts to display the current password policy settings.
- PowerShell — Another way to display the domain’s password policy settings is to use the Get-ADDefaultDomainPasswordPolicy command.
How to Troubleshoot Password Policy Issues
If a user is not receiving the most up-to-date password policy, you can run the following commands on their machine to investigate and attempt to resolve the problem:
- gpresult /r — Shows the GPOs applied to the user and computer
- gpupdate /force — Applies the current GPO settings
Password policy issues can also be related to problems with domain controller (DC) replication — if not all DCs have the same password policy settings, users might experience inconsistent results depending on which DC they authenticate to. To view any replication failures or delays between domain controllers, use the repadmin /replsummary command.
Overcoming Common Password Policy Challenges
The most fundamental challenge in implementing password policies is balancing the desire for strong security with the reality that users often respond to overly strict rules in ways that undermine security. For example, requiring frequent password changes mitigates the risk from stolen password databases — but it can lead users to engage in workarounds that undermine security, such as choosing weaker passwords or simply incrementing a number at the end their password each time. Similarly, requiring users to create long and complex passwords reduces the risk that hackers will be able to guess or crack those passwords to gain access to the corporate network. However, users might resort to writing down their passwords to avoid frustrating lockouts.
Proper communication can help mitigate this problem. Security teams should not only tell users what the password requirements are but explain why they are necessary and how trying to circumvent them can lead to breaches and other security incidents. Whenever the password policy is changed, be sure to have your help desk team ready to provide extra support for users.
There are also third-party tools that can help. In particular, consider the following types of solutions:
- Password policy enforcement software enables you to implement changes to password policy gradually, providing a grace period during which users are encouraged but not forced to comply with the new requirements.
- Password manager tools make it easy for users to comply with strict policies. The software will generate and store a strong and unique password for each of their accounts and enter it for them whenever it is needed. That way, a user needs to create and remember only one password — the one for the password manager application.
- Self-service password reset software enables users to securely reset or change their own passwords and unlock their accounts without calling the help desk. Since lockouts are less painful, users are less likely to try to avoid them with insecure workarounds.
Conclusion
Strong password policies are a key element in a robust cybersecurity strategy. By following the best practices detailed here, you can reduce the risk of account takeover by adversaries, thereby enhancing security and compliance.
To add an extra layer of security, require multifactor authentication (MFA) instead of just a user ID and password, especially for risky use cases such as administrative logons and requests to access sensitive or regulated data.
For more information, read our password policy best practices for strong security in AD.
FAQ
What are password policies in Active Directory?
AD Group Policy offers a Password Policy that enables administrators to establish standards for user passwords. For example, they can establish a minimum password length, prevent the reuse of previous passwords, and control how often passwords must be changed.
Where can I see password requirements in Active Directory?
You can view the Group Policy password policy settings using any of the following methods:
- Group Policy Management Console — Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policy.
- PowerShell — Use the Get-ADDefaultDomainPasswordPolicy cmdlet.
- Local Security Policy tool — On a domain-joined computer, run secpol.msc.
- Active Directory Administrative Center — Check the Password Settings container.
How do I edit the password policy in Active Directory?
You can easily edit the AD password policy using the Group Policy Management Console. In most cases, the password settings will be a part of the Default Domain policy.
How can I check password expiry in Active Directory?
There are multiple ways to do this. Here are two options:
- In Group Policy Management Console, navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policy.
- Run the following PowerShell command: Get-ADDefaultDomainPasswordPolicy | Select MaxPasswordAge.
How long can an AD password be?
The maximum length for an AD user account password is 256 characters. However, for standard users, 12–14 characters will suffice.
What is password complexity?
Password complexity refers to rules that control the composition of passwords themselves. The goal is to prevent users from selecting weak passwords, such as a simple dictionary word or name, which are easier for hackers to guess or crack. When enabled, the AD password complexity policy forces users to choose passwords that:
- Do not contain the user’s account name value or display name
- Do include characters from three of the following categories: Uppercase letters, lowercase letters, base 10 digits, and special characters such as $ or %
How should I assign a Group Policy for passwords?
In Active Directory, password policies are configured and applied using Group Policy. While Microsoft recommends that group policies, in general, be assigned to at the organizational unit (OU) level, it is a best practice to control GPO password policy settings using the Default Domain Policy, which applies to all users and computers in the Active Directory domain. This is to ensure that the password policy is applied to all domain user accounts.


 of ENG [Free Guide] short-384x406.jpg)
