The local Windows administrator account is a coveted target for hackers and malware. There are potentially a lot of bad things that can happen if a hacker can crack the local admin account of one of your servers.
Dreadful things usually occur when someone downloads a malicious malware strain using the administrator account as well. The magnitude of these problems is amplified even more if you use the default administrator account for every similar machine uses the same password.
You can have the most complex password in the world, but once it is compromised on one machine, it is open season for all other devices using the same local admin credentials.
Of course, you could customize the local admin credentials for every Windows device, but that can prove highly time-consuming not to mention the task of inventorying the many credential sets. The process becomes virtually unworkable when you enable password refreshes (which you should of course). This is why many admins often just disable it.
But it’s understandable to have some type of local admin account to “walk up and fix the machine” like resetting it’s domain trust relationship or hardcoding an IP address, and so on.
If having the same local admin password on each machine is a terrible idea, what can be done about it?
Tip 1: Use Microsoft Local Administrator Password Solution (LAPS)
Microsoft Local Administrator Password Solution (LAPS) is a Microsoft tool that gives AD administrators the ability to manage the local account password of domain-joined computers and store them in AD.
When implemented via Group Policy, LAPS creates a random password of a defined length and complexity that is cryptographically secure and different every time, on every machine. It then applies the newly created password to the Local Administrator account and records the password in a secure field in your Active Directory schema. They can then be retrieved when access is needed to the account. The process is done automatically whenever a Group Policy defined password refresh is due.
LAPS does have a few requirements to implement it:
- It only applies to Windows devices
- Devices must be domain joined
- It requires a free Group Policy client-side extension
- It requires a schema extension (don’t freak out.)
- It only works for the local admin account
- It only works for ONE local admin account (in case you have more than one.)
Tip 2: LAPS and Group Policy
As mentioned, LAPS is deployed using Group Policy, which means it requires the creation of a GPO. You first need to download LAPS which you can do here.
Then use the wizard to install it on your Group Policy Management machine. You’ll want to do this by hand, and typically NOT in some automated way.
Make sure you at least select the GPO Editor Templates in order to access the necessary ADMX files. The fat client is a graphical user interface that gives a user with applicable rights the ability to query the password for a designated device. You only need to install the Management Tools, and not the “AdmPwd GPO Extension” on your machine (the one with the GPMC.)
You must then go into your local PolicyDefinitions folder and copy the AdmPwd.admx and AdmPwd.adml files and paste them into your AD central store. (Check this video on this process).
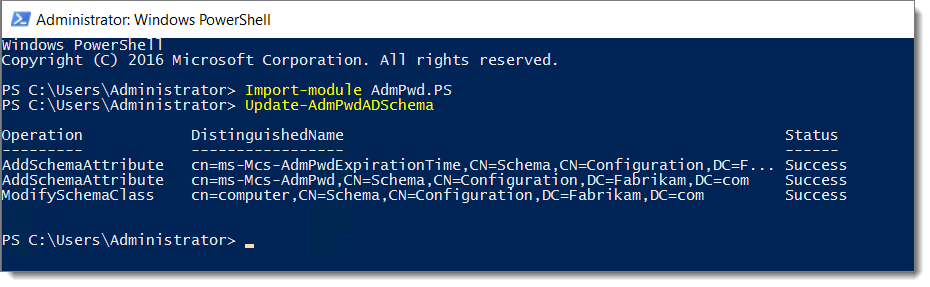
Next, we need to extend the AD Schema in order to accommodate the local passwords.
The two required attributes are:
- ms-Mcs-AdmPwd – Stores the password in clear text
- ms-Mcs-AdmPwdExpirationTime – Stores the time to reset the password
To update the schema, simply import the AdmPwd PowerShell module and use the update-AdmPwdADSchema command as shown below.
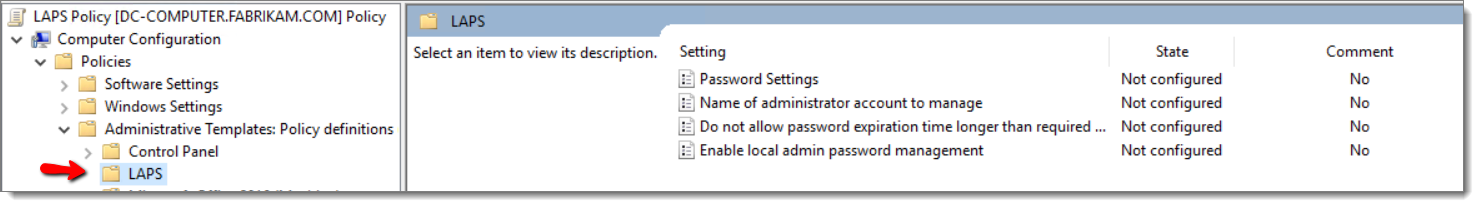
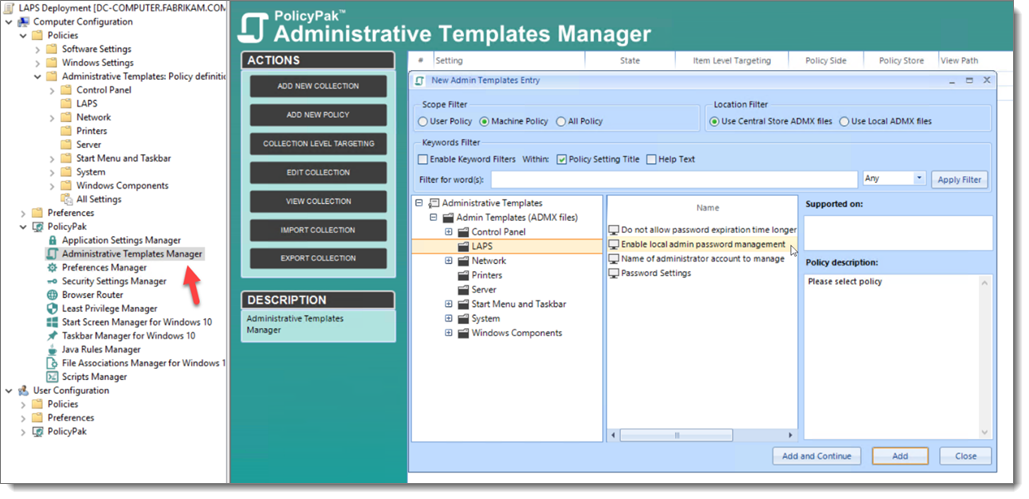
The next step is to create a computer side GPO. For this example, I will call it LAPS Policy. The LAPS settings will now appear under Computer Configuration > Administrative Templates > LAPS where 4 settings are available as is shown below.
You can use your LAPS GPO to manage the password for either the default local admin or a custom local admin account. Below I have enabled the “Enable local admin password management ”setting.”
If you have renamed the local admin account, (which you should) you can then specify the updated name. Once the admin account is selected, the final step is to enable the Group Policy setting which configures the password settings (that include password length and age.)
Once configured, simply deploy the LAPS client-side-extension software via your desired software deployment method, like PDQ Deploy. You only need the “GPO Extension” part if you’re going to do an initial test by hand. You can see this here.
You can also use PolicyPak to gain more control over the deployment process. More on that in just a minute.
Tip #3: Getting Passwords when needed via LAPS
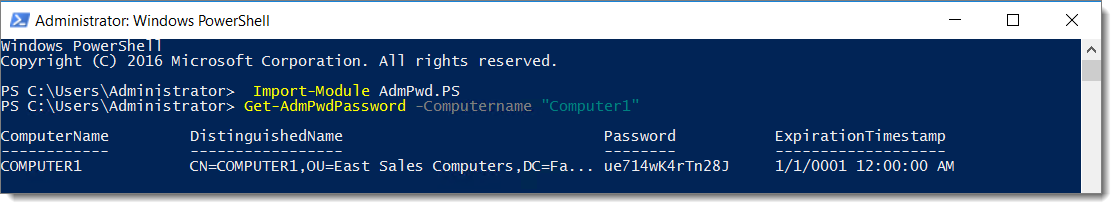
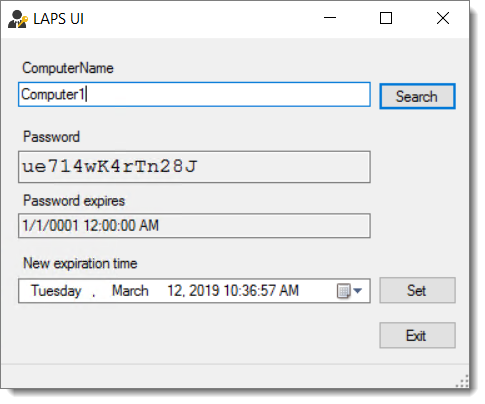
So, the day comes that you need to know what the current generated password is for one of your Windows machines. How do you do it? There are several ways. On is to use the following PowerShell command.
Get-AdmPwdPassword -Computername “name of computer”
If you installed the LAPS Fat Client, you can access the LAPS UI application in your start menu.
Tip #4: Assign Granular LAPS Policies to Users via Item-Level Targeting
PolicyPak offers all of the ADMX template settings in its PolicyPak Admin Templates Manager and we update them at the time of every new ADMX release. There’s a lot of advantages to using Admin Templates Manager versus standard Group Policy.
PolicyPak uses Group Policy Editor as is shown below but adds a secret superpower.
The key benefit is that PolicyPak can utilize Item-level Targeting for any Group Policy setting, including LAPS.
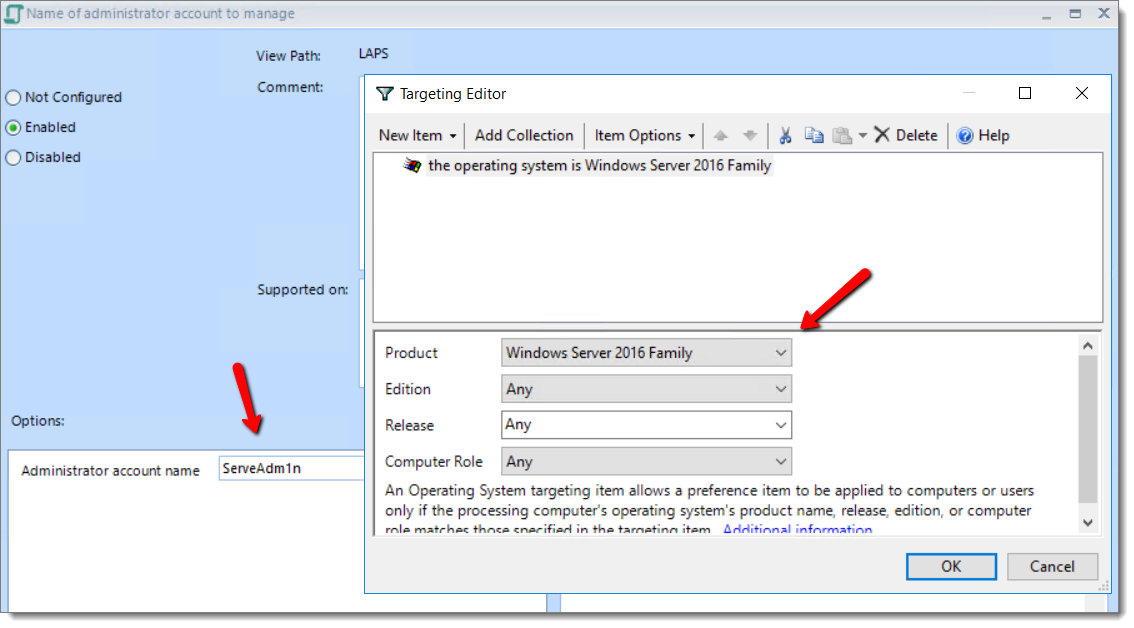
If you are familiar with Group Policy Preferences, then you already know how ILT provides a lot more granularity concerning policy assignment. For instance, let’s say that all of the local admin accounts residing on your servers are named ServAdm1n and you want to create a separate LAPS policy for those admins. Since those aren’t admin domain accounts, you can’t target them using group policy but you can use ILT to target those machines running Windows Server 2016.
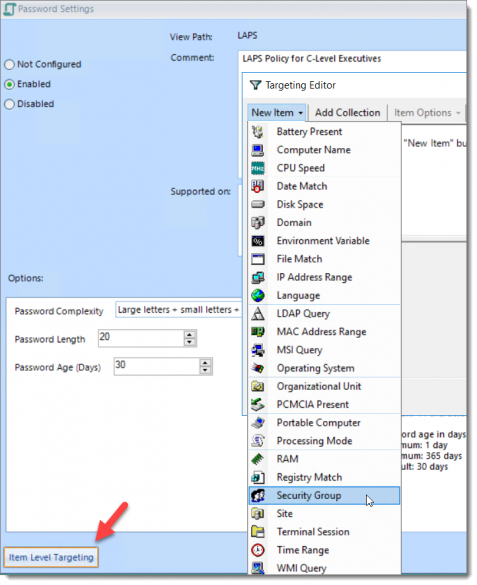
Now let’s make a LAPS policy for C-Level executive laptops. Naturally, we would want to have a strong password for those local admin accounts. In this case, I want to enforce 20-character passwords using the strongest complexity. Then I will use ILT to target the C-Level security group. As you can see in the screenshot below, there are many targetable options including computer name, OU Match, Site Match, computer form factor (Laptop vs. Desktop) and more!
As a bonus, while traditional GPOs created within the Group Policy Editor can normally only be deployed using Group Policy, PolicyPak settings can be deployed using a number of ways such as SCCM, KACE or your preferred MDM service.
You can learn more about that process by watching this video that demonstrates the process of delivering Group Policy settings, without the Group Policy engine itself.
Tip 5: Pair LAPS with PolicyPak Least Privilege Manager
Local Administrator Password Solution is a great tool to tighten administrative access to your most important machines. In fact, it also makes a great pairing with PolicyPak Least Privilege Manager. PolicyPak Least Privilege Manager completely removes the need to have local admin rights, enabling Standard Users to do special functions like an admin… but without actual admin rights.
Together, you could enforce LAPS on all of your enterprise machines … since you won’t be needing local admin access any longer.
In the end, whatever you can do with Group Policy, you can do it better with PolicyPak. Implement LAPS and add PolicyPak and get more security, power, and agility.