Modern organizations typically use a mixture of operating systems, including Unix, Linux, Windows and macOS. Network File System (NFS) is an open client/server protocol that allows organizations to centralize their data storage on one or more servers and enable seamless file sharing between their various operating systems.
This blog explains how to mount NFS Windows clients so users can access shared files over the network as if they were stored locally. It also provides best practices to optimize both security and performance.
Configuring NFS on Windows: Step-by-Step Guide
To allow a user to access remote NFS files, follow these steps to configure Windows mount NFS.
Step 1: Install the ‘Client for NFS’ feature on your Windows machine to set up the NFS client for Windows.
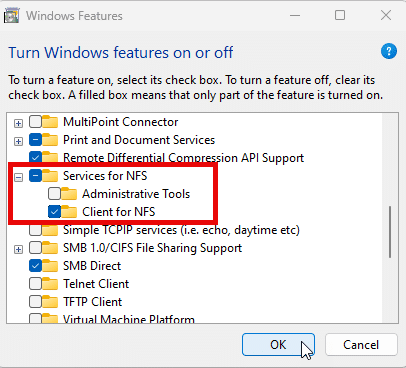
In Windows 10 or Windows 11, open Control Panel and go Windows Features. Expand Services for NFS and check the box next to Client for NFS, as shown below.
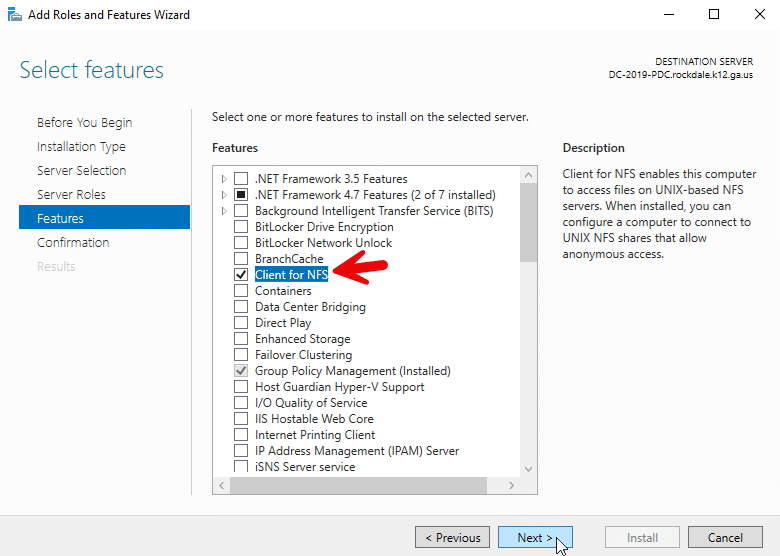
For Windows Server 2012 and above, run the Roles and Features Wizard and select Client for NFS, as shown below.
Alternatively, you can use an elevated Windows PowerShell session to install the NFS client Windows:
- For Windows 10 or Window 11, the command is:
Enable-WindowsOptionalFeature -Online -FeatureName ServicesForNFS-ClientOnly
- For Windows Server, the command is:
Install-WindowsFeature -Name NFS-Client
Step 2: Verify the client and connectivity.
Verify that the NFS Client service is running on your machine, as shown below.
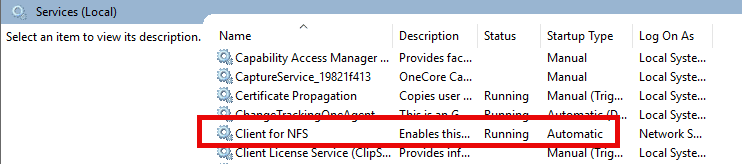
Of course, you must have connectivity to the designated NFS server. For a successful Windows NFS mount, ensure that the NFS Client service is running and the firewall allows NFS traffic. The default port is 2049.
Step 3: Perform identity mapping.
To enable Windows users to authenticate to a Unix server providing NFS exports, we need to map Windows users to the Unix user identifiers (UIDs) and group identifiers (GIDs) used by Unix-like operating systems. This mapping allows the Unix server to determine which user made the request for the NFS export.
Identity mapping can be done using any of the following methods:
- Active Directory (if integrated with the NFS environment)
- Local user mapping files
- Windows Registry settings
The first option is preferred for security and scalability reasons.
Method A (Preferred): Perform Identity Mapping in Active Directory (AD)
If both the Unix NFS server and Windows NFS client are joined to the same Active Directory domain, then we can use identity mapping in Active Directory. This is the preferred method whenever possible.
By default, a NFS client won’t look up identity mapping in Active Directory. However, we can change that by running the following command in an elevated PowerShell session on the NFS client:
Set-NfsMappingStore -EnableADLookup $True -ADDomainName “yourdomain.com”
You can add these LDAP options to specify your domain controllers:
Set-NfsMappingStore -LdapServers “dc1.yourdomain.com”,”dc2.yourdomain.com”
Restart the NFS client service.
Next, we need to configure our identity mapping. We can do that in Active Directory Users and Computers as follows:
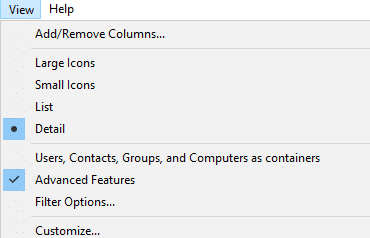
- Enable Advanced Features enabled under the View dropdown, as shown below.
- Right-click on the object you want to view and select Properties.
- In the Attribute Editor tab, select the uidNumber or gidNumber attribute and click Edit.
- Enter a value, and click OK to save your changes.
Alternatively, you can use the following PowerShell command:
Set-ADUser -Identity <UserPrincipalName> -Add @{uidNumber=”<user_unix_uid>”;gidNumber=”<user_unix_gid>”}
Replace the following:
- UserPrincipalName — The user to modify (e.g., user@domain.com)
- @{ … } — A hashtable containing the new attributes to add
- uidNumber — The Unix user ID (UID) for the user
- gidNumber — The Unix group ID (GID) for the user’s primary group
To perform this task automatically, create a CSV file containing user data and loop through it.
Method B: Perform Identity Mapping using Local Configuration Files
Using local user mapping files is a straightforward approach to establish correspondence between Windows users and Unix UIDs/GIDs without relying on Active Directory. This method uses two main configuration files:
- passwd — Maps Windows users to Unix UIDs
- group — Maps Windows groups to Unix GIDs
Both files are typically located in the C:\Windows\system32\drivers\etc\ directory. They follow a specific format, with each line representing a user or group mapping. When a Windows user attempts to access an NFS resource, the NFS service consults these files to look up the user’s Windows account name and retrieve the corresponding UID and GID, which are then used for NFS operations.
This method is simple to set up and manage in small environments and is particularly useful for standalone servers or workgroups. However, because it requires manual maintenance of mapping files, it doesn’t scale well for large environments. In addition, while it offers a solution for environments where Active Directory integration is not feasible, it’s important to consider security implications and regularly audit the mappings to ensure they remain accurate and secure.
Method C: Perform Identity Mapping using Windows Registry Settings
This method involves setting registry values to specify a default UID and GID that the Windows NFS client will use when accessing NFS shares. It’s particularly useful when you want all NFS access from the Windows client to appear as a specific Unix user, regardless of the Windows user account.
To implement this mapping, use the following PowerShell commands:
New-ItemProperty “HKLM:\SOFTWARE\Microsoft\ClientForNFS\CurrentVersion\Default” -Name AnonymousUID -Value <unix_export_owner_uid> -PropertyType “DWord”
New-ItemProperty “HKLM:\SOFTWARE\Microsoft\ClientForNFS\CurrentVersion\Default” -Name AnonymousGID -Value <unix_export_owner_gid> -PropertyType “DWord”
You need to reboot to have the new settings take effect. This mapping will apply to all NFS mounts made by the Windows client. After performing identity mapping, you can mount NFS in Windows using the command prompt.
Note that this method applies the same UID/GID to all NFS access from the Windows client, which may not provide sufficient access control in multi-user environments. In addition, modifying the registry requires administrative privileges, which could be a security concern. For these and other reasons, this method is considered an insecure approach and is not recommended.
Mounting in NFS means attaching a remote file system (exported by an NFS server) to a directory on the local file system of a client machine. When a client mounts an NFS share, it connects to the remote file system and makes it appear as if the NFS share is part of the local directory structure.
To mount NFS on Windows, map it to an available drive letter using the command prompt, as follows:
mount \\<nfs_server_ip_address>\<pathtonfsexport> Z:
Replace the following:
- <nfs_server_ip_address> — The IP address of your NFS server
- <pathtonfsexport> — The export path on the server
- Z — The drive letter to which the NFS share will be mounted on your Windows computer.
You can add additional options; for instance, mount -o anon specifies that the connection should be made anonymously, and mount -o nolock overrides the default file locking used by NFS.
After running the mount or mount o command,check whether the NFS share was successfully mounted by running the net use command to display all mapped network drives.
Troubleshooting Tips
Here are some errors that can arise during the mounting process and their typical underlying causes:
- Permission denied — Incorrect export settings on the NFS server or NFS rule blocking
- Access denied by server — Mismatched UID/GID between client and server
- Version mismatch — Client and server using incompatible NFS versions
- Mount point already in use — Attempting to mounting to a directory that’s already being used as a mount point
- No such file or directory — The export path on the server doesn’t exist
Best Practices for NFS Mounting on Windows
The following best practices can help you optimize security and performance when using NFS mounting on Windows.
Security
- Use strong authentication protocols such as Kerberos.
- Configure firewalls to segment the network and restrict NFS access from untrusted networks, allowing only necessary ports (TCP and UDP port 2049).
- Encrypt data in transit using secure protocols to safeguard data against eavesdropping and tampering.
- Limit NFS export permissions by granting the minimum required access and restricting client connections to specific IP addresses or hostnames.
- Regularly update and patch both the Windows client and NFS server to protect against known vulnerabilities.
- Enable detailed logging on the NFS server and monitor for suspicious activity.
- Use additional network security measures like VPNs for remote access.
Performance
- If possible, use NFSv4 or NFSv4.1 rather than NFSv3.
- Enable read and write caching on the client side to improve performance for frequently accessed data. You can do this using the following command: mount –o readcache,writecache.
- If security is not a concern in your environment, consider using the nolock option to disable file locking.
- Keep the Windows NFS client software up to date to benefit from the latest performance improvements and bug fixes.
FAQ
Does Windows 11 support NFS clients?
Yes, Windows 11 supports NFS clients.
How can I use NFS in Windows?
Here are some ways you can use NFS in Windows:
- You can provide access to the same file share using both the SMB and NFS protocols by using a Windows NFS file server.
- You can deploy a non-Windows operating system to provide NFS file shares accessible to non-Windows clients using the NFS protocol.
- To enable applications to be migrated from one operating system to another, you can store data on file shares accessible using both the SMB and NFS protocols.
What improvements are included in NFS version 4.1?
For complete details, visit the Microsoft NFS page. Key improvements in version 4.1 include:
- Remote Procedure Call (RPC)/External Data Representation (XDR) transport infrastructure, which offers better support and provides better scalability
- RPC port multiplexer
- Auto-tuned caches and thread pools
- New Kerberos privacy implementation and authentication options
How do I add the server for NFS role service?
In Server Manager or Windows Admin Center, use the Add Roles and Features Wizard.
What Windows command-line administration tools does Server for NFS contain?
- Mount provides an NFS mount on Windows clients that maps to a local drive.
- Nfsadmin manages configuration settings of the Server for NFS and Client for NFS components.
- Nfsshare sets up NFS share settings for folders that are shared via Server for NFS.
- Nfsstat displays or resets statistics on calls received by Server for NFS.
- Showmount lists the file systems that have been exported by Server for NFS.



