Active Directory nested groups allow one group to be a member of another, simplifying permissions but increasing complexity and risk. Global, domain local, and universal groups each have specific nesting rules that govern how access can be granted across domains. Best practices include following the AGDLP model, avoiding circular nesting, and regularly reviewing group structures to maintain security and prevent excessive access.
Active Directory (AD) security groups enable administrators to grant access to IT resources, both within a domain and across domains. However, groups can be members of other groups. This group nesting has profound implications for security, so it’s vital to understand nesting and how to nest groups correctly. This article explains how group nesting works and the best practices to follow.
What is Group Nesting?
Group nesting is the process of making one Active Directory group a member of another group. A nested group inherits all the permissions and privileges of each group it is a member of. The primary reason is to simplify the process of giving access to resources. It allows an administrator to make permissions more granular and assign groups where appropriate.
This diagram illustrates a simple series of nested groups: Group4 nested into Group3. Group3 nested into Group2. Group2 nested into Group1.
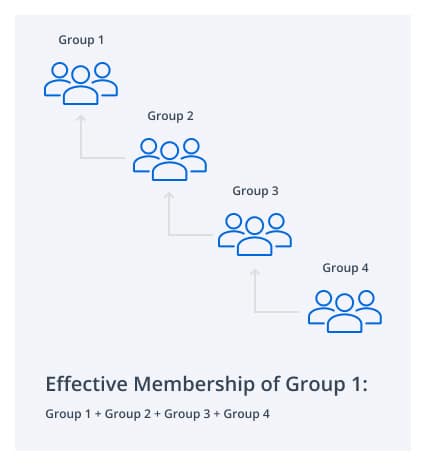
The deeper the nesting, the harder it is to track changes to effective membership and the larger the risk of ‘Circular Nesting’, when a group inadvertently becomes a member of itself. Effective membership is the sum of all users in all groups within the nesting hierarchy.
Nesting AD Groups based on Group Scope
Whether a group can be nested into another group depends on the scope of each of those groups.
Nesting of Domain Local Groups
Domain Local groups are generally used to manage permissions to domain-specific resources, such as a specific printer.
- A domain local group can contain users, computers, global groups and universal groups from the same domain or any trusted domain inside or outside the forest.
- A domain local group can be a member of another domain local group in the same domain.
Nesting of Global Groups
Global groups are generally used to grant rights to a set of AD users who have similar job responsibilities (such as all accountants or all members of the Marketing department).
- A global group can contain users, computers and global groups from the same domain.
- A global group can be a member of domain local groups or other global groups in the same domain.
Nesting of Universal Groups
Universal groups generally have other groups, rather than individual users or computers, as members.
- A universal group can contain users, global groups, and other universal groups from any domain in the forest.
- A universal group can be a member of domain local groups or other universal groups.
- A universal group cannot be a member of a global group.
Example
For example, you might create the following groups:
- A domain local group called US-MarketingPrinter, which has permission to access the printer in the Marketing team’s area
- Two global groups, US-Marketing and Asia-Marketing, that contain the user accounts for your two marketing teams
- A universal group called UMarketing,which is granted access to marketing data and applications
You then nest both global groups in the universal group, thereby granting all your marketing pros access to marketing IT resources. And you nest the US-Marketing global group in the domain local group to give those users access to the printer in their office.
How to Nest Groups in Active Directory
Here is how you can nest a group into another group in Active Directory.
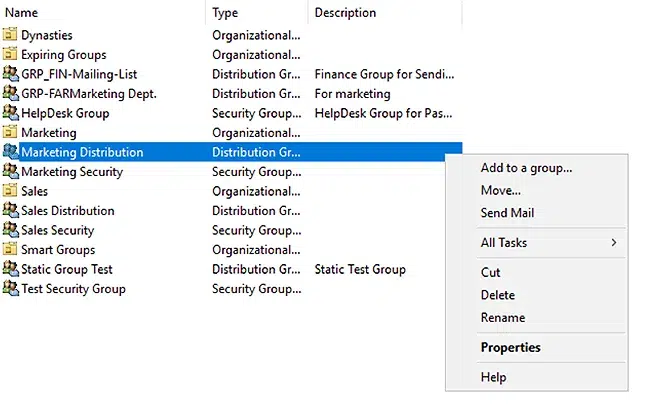
- Open the Active Directory Users and Computers (ADUC) console.
- Right-click the group that you want to nest inside another group, and click Properties.
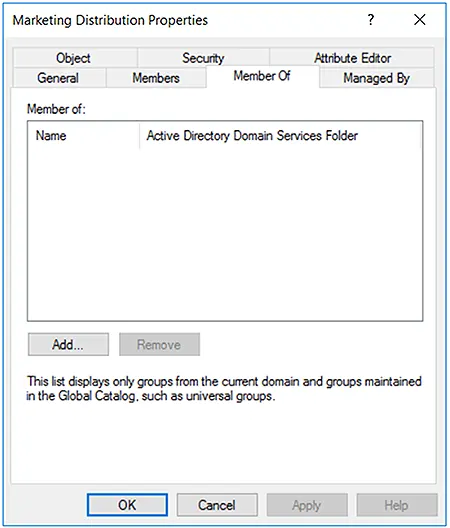
- Go to the Member Of tab and click Add.
- Locate the group you want your group to be a member of. You can search for the group by typing a name and then clicking the Check Names button.
- Select the group from the list and click OK.
- The Member Of tab will now show the nesting you specified. Click OK to save your change.
Best Practices for Nesting AD Groups
The following best practices will help you use group nesting effectively.
When Users Are in the Same Domain
If users are part of the same domain, you should nest groups as follows:
- Add user and computer accounts to global groups
- Add global groups to domain local groups
- Grant the domain local groups access to resources
- Assign permissions to domain local groups for appropriate access
When Users Are in Different Domains
If users are in different trusted domains, nest groups as follows:
- Add user and computer accounts to global groups
- Add global groups to universal groups
- Add universal groups to domain local groups
- Assign permissions to domain local groups for appropriate access
Risks of Group Nesting
If group nesting is not closely managed, it can quickly swirl out of control, resulting in a loss of clarity and control over who has access to what — which, ironically, is exactly the opposite of what group nesting is intended to do.
This illustration demonstrates a simple use of nested groups. ‘Admin Group’ has been applied to the ACL on three sensitive Data folders.
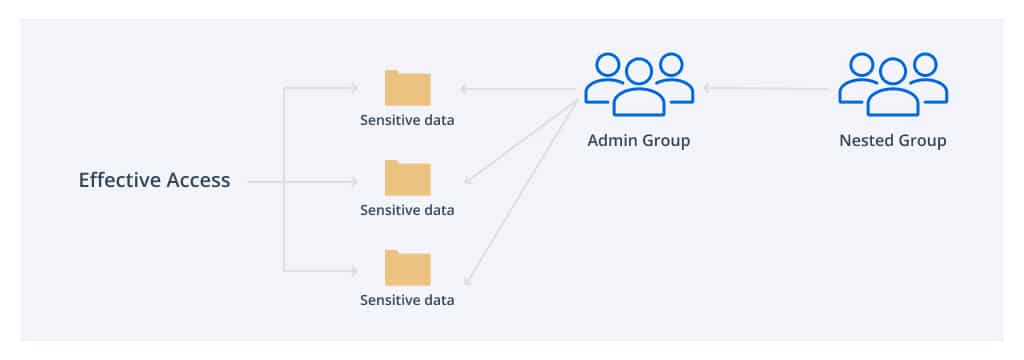
In particular, users often need access to resources on a temporary basis, such as for a particular project. A corresponding security group is created and nesting relationships are established. When the task is complete, access should be revoked immediately for security reasons. However, the IT team is usually reluctant to make changes to security groups because the complexity of nesting can make it difficult to predict the impact of those changes. As a result, user accounts can end up with far more access than they need, opening the door to insider abuse and giving extra rights to any adversary who compromises the user account.
Active Directory Group Nesting with GroupID
The dynasty feature of Netwrix Directory Manager helps you nest groups automatically in keeping with the structure of your organization. GroupID offers three types of built-in dynasties:
- Organizational dynasty — Creates AD groups based on business companies, departments groups nested within a company, and job titles groups nested within each department.
- Geographical dynasty — Creates AD groups based on country, each state group nested within a country, and each city group nested within a state.
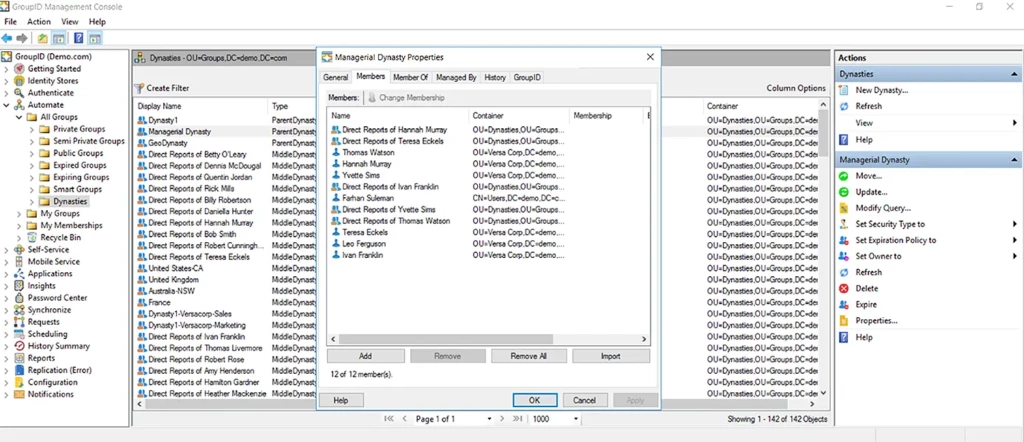
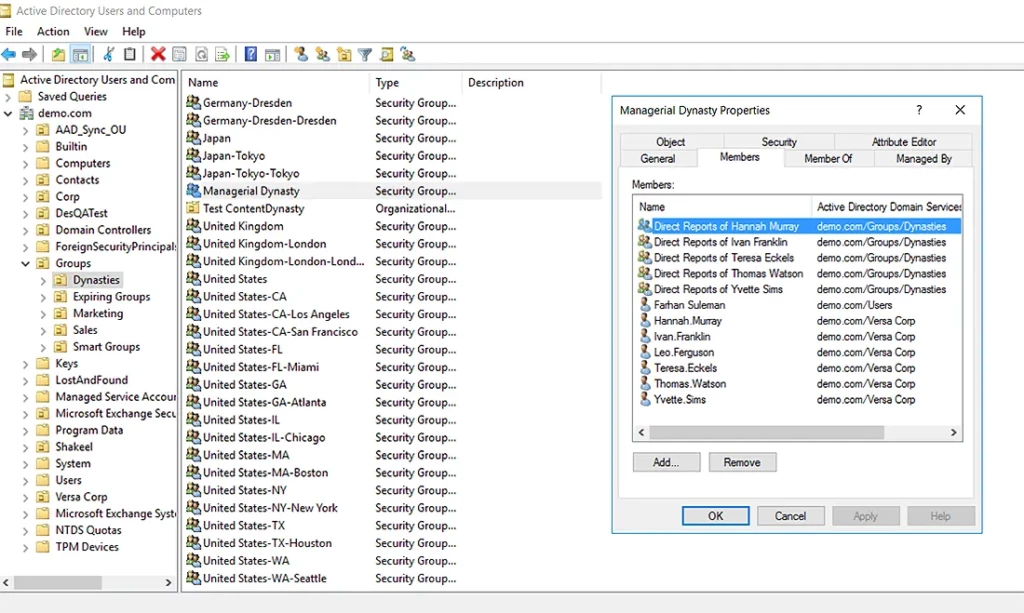
- Managerial dynasty — Creates AD groups based on the direct reports of each manager and sub-level manager in an organization, nested respectively.
You can also easily create your own custom dynasties, where you can set your desired attributes to auto create nested groups.
The following screenshots show how these dynasties are displayed in Netwrix Directory Manager and in ADUC:
Using Dynamic Groups
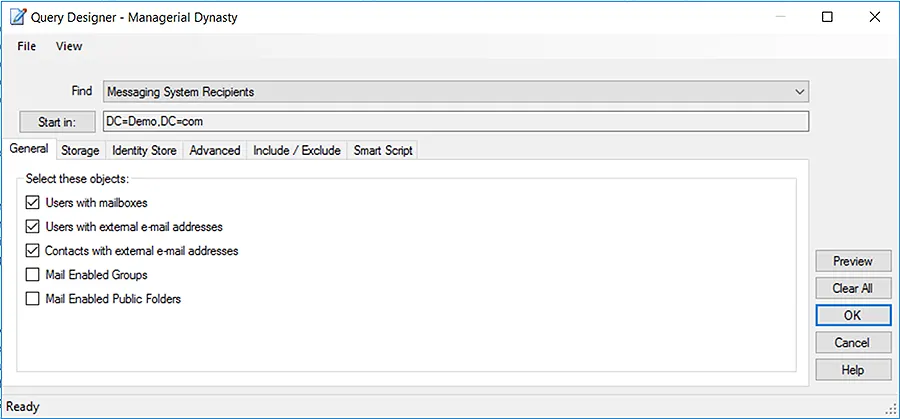
Netwrix Directory Manager enables you to create AD groups whose membership is dynamically determined by an LDAP query that you set up. This query is defined once and scheduled to run automatically. Hence, whenever the directory information changes, the groups’ membership is auto updated accordingly. Administrators no longer have to add or remove members manually, which saves them a great deal of time while avoiding human errors.
You do not have to write code to define the LDAP queries; you simply use the intuitive Query Designer:
Conclusion
Using Active Directory groups is an established best practice for managing access to data, applications, and other IT resources. But to maintain security and business productivity, those groups have to be set up properly and nested accurately. With manual methods, that work can be a real challenge. A solution like Netwrix Directory Manager can dramatically simplify the work of managing your Active Directory groups, including the complexities of group nesting.