Introduction
Imagine being named XYZ in a crowd of other XYZs – a purposeless name that creates confusion and does not communicate a purpose, adding to the cognitive pile of everyone’s day-to-day tasks. Similarly, Active Directory groups created by users need to have logical names so that current and future users do not find themselves stuck in a pickle.
Active Directory (AD) groups play a vital role in controlling access to IT resources and routing messages. If the names of your security and distribution groups do not clearly communicate their purpose, your business is at increased risk of both security and productivity issues: IT teams will find it difficult to ensure that users are provisioned in accordance with the least privilege principle, and business users can struggle to communicate effectively.
This article provides key best practices for group naming and explores an effective way to implement those best practices.
Group Naming Best Practices
Here are four best practices for groups that can help keep your Active Directory tidy.
- Be consistent.
- Establish standard prefixes
- Provide a description for each group.
- Establish an approval-based workflow for group creation.
Be consistent
It is essential to have a set of rules for naming AD groups. As you build your rules, work with a variety of stakeholders to ensure that the system you create is useful and the resulting group names will make sense to all users. In addition, think ahead to possible changes in your directory and work to make your rules flexible so they can continue to serve your needs.
Establish standard prefixes
One common way to build consistency in group naming is to establish standard prefixes for group names that indicate the group’s purpose. For example, you might require a prefix that reveals the department or team the group is created for, followed by the level of permissions assigned to it, as illustrated here:
- HR_Payroll — A group for Human Resources employees who need to process payroll.
- ENG_Backend_FullControl — A group for Engineering team members who need full control of backend servers.
- FIN_Audit_ReadOnly — A group for people who need read-only access to Finance resources in order to perform audits.
Provide a description for each group
Even if you have a system in place to ensure that group names are descriptive, they are somewhat abbreviated. Accordingly, it’s smart to provide a meaningful description for a group while creating it, so that you have a clear record of the group’s purpose. This saves users time and effort when scrolling through the group list and guessing a group’s purpose. For example, you might have the distribution list GRP_FIN_MailingList, which is a fairly clear name, but you can make the group’s purpose even clearer by providing the description, “Distribution list for sending out weekly updates to the Finance team.”
Establish an approval-based workflow for group creation
To minimize the risk of unnecessary groups being created and ensure that your naming conventions are followed, create a workflow that requires any group creation request to be approved by an authorized person. In addition, ensure that all requests to change a group are also routed through an approval workflow.
Enforcing Group Naming Best Practices with Netwrix Directory Manager
Enforcing your group naming policies can be a challenge. Active Directory does not provide any check on group names except for uniqueness.
Netwrix Directory Manager enables you to define group naming policies that work across both Active Directory and Azure AD. In particular, you can easily:
- Define standard group name prefixes.
- Standardize group names using regular expressions.
- Auto-name child groups using a naming template.
- Prevent users from using certain words in group names.
Define standard group name prefixes
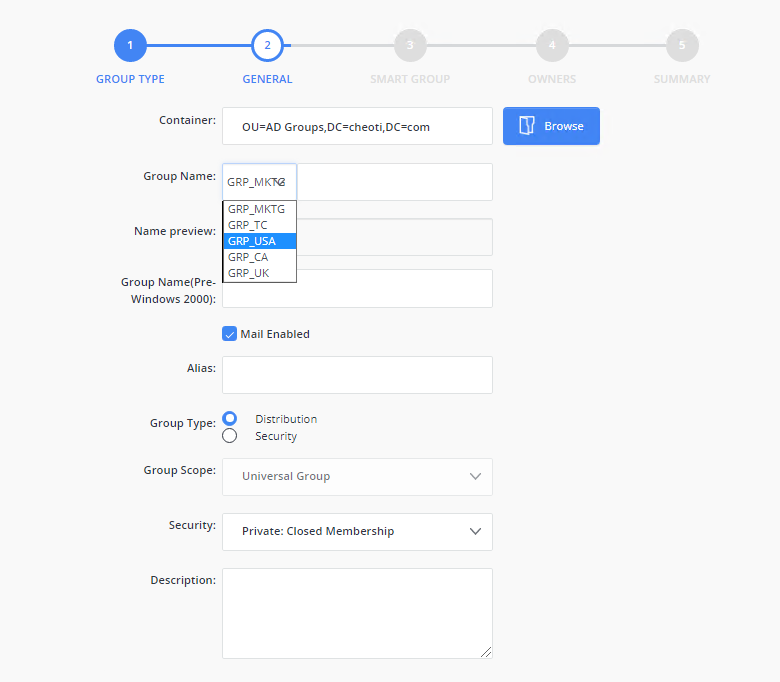
Administrators can use the Group Name Prefixes policy in Netwrix Directory Manager to define a set of prefixes to be used for group names. For example, you might define a set of prefixes for your department, your geographic locations, and the roles in your organization.
When a user creates a group, they can simply choose the appropriate prefixes from a drop-down list to append to a group’s name.
For example, the compound prefix US_Sales indicates a group created for the US Sales team. The following figure shows how group name prefixes are displayed to a user who is creating a group through Netwrix Directory Manager:
Standardize group names using regular expressions
With Netwrix Directory Manager, you can use regular expressions to ensure that group names follow a standard pattern. For example, you can define a regular expression that will require the first character of each group name to be a capital letter.
Auto-name child groups using a naming template
Netwrix Directory Manager can create groups in a hierarchy based on attributes such as geographical location (country, state, city), organizational structure (company, department, title), or managerial relationships (managers and their direct reports). It creates a parent group with nested child groups, with the child groups named automatically according to a naming template. This helps ensure groups are assigned logical names and makes it easier to identify all groups that are nested within a parent group.
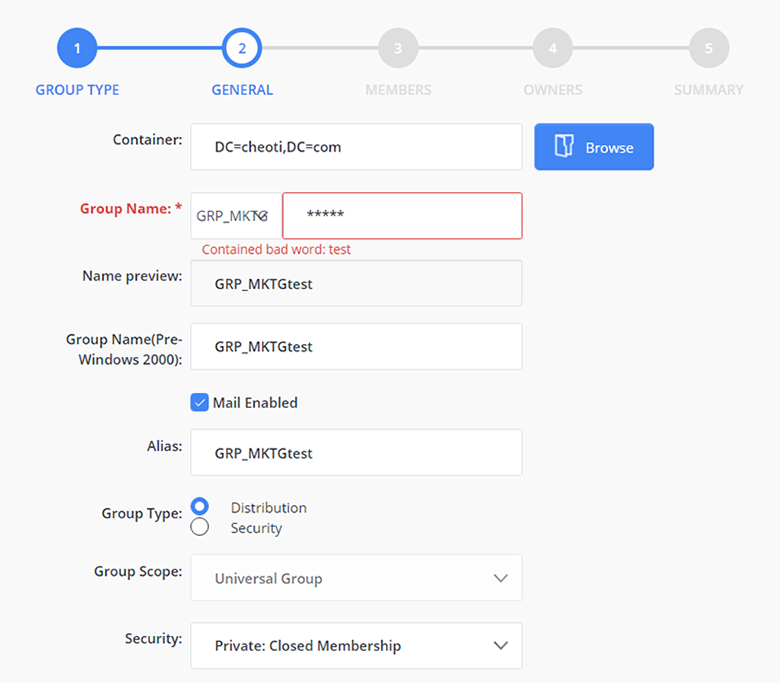
Prevent users from using certain words in group names
Netwrix Directory Manager enables you to specify words that users should be blocked from using in group names (as well as in aliases or values for other attributes). If a user enters a blocked word, an error is displayed that clearly indicates how the group name needs to be changed in order to be accepted: