Every time you deploy a new Cisco device, whether to handle network growth or as part of a product refresh cycle, someone needs to configure it to meet your unique needs. But configuring switches or routers is not a one-time event — support teams often need to add a new VLAN, change an access port to a trunk or add a new route to the routing table.
This article explains why these types of changes are temporary and details the commands you need to use to have them remain in effect after the device reboots.
How Changes to a Cisco Device Are Stored
On a Cisco device, the running configuration is the set of configuration settings that the device is actively using. The running config is stored in the device’s random access memory (RAM) and dictates how the device behaves in terms of routing, switching, interface settings and other network functions. The running configuration is dynamic, which means it can be modified by privileged techs during operation.
Any setting modifications remain intact as long as the device remains powered on. However, the running configuration is not automatically saved in a more permanent storage. If you make changes to it and the device is somehow rebooted or loses power, all those changes will be lost unless you have taken additional steps to save your changes. This is because, upon restart, the device loads its configuration from the startup configuration, which is stored in the device’s non-volatile random access memory (NVRAM). In other words, the startup config is what the device reverts to upon a reboot.
Why You Should Always Save Your Changes
Consider a worst-case scenario: Changes have been made to Cisco devices over the course of a year but none of them has been saved to the startup config. Then there is a power failure and all the devices reboot.
Now what do you do? Does your organization even have all those changes documented? It would be like the horror stories from before Office applications saved documents automatically, where writers lost entire manuscripts. In short, it is imperative that you save changes made to the running configuration.
Test before saving! Remember that making any change to the configuration of a Cisco device can significantly impact network performance and security. Therefore, it’s vital to thoroughly test any new settings before saving them to the startup config file.
How to Save Your Changes
Here is the good news: You can save your config changes using a simple two-word command:
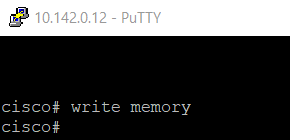
write memory
Below is an illustration of the command in a Putty session:
How to View the Running Config and Copy It into the Startup Config File
Another strategy you can use is to overwrite the entire startup config file with the running config settings.
You can view the startup configuration by using the command:
show startup-config
To overwrite the current startup config file with the running configuration settings, use the following command:
copy running-config startup-config
Alternatively, you can use this abbreviated version of the command:
copy run start
Be Sure You’re in the Correct Cisco Mode
Cisco devices use a hierarchical set of modes to ensure that when a user connects to a device, they can execute only the commands that align with their permission levels. A user’s current mode is indicated by the type of prompt displayed after the name of the Cisco device, as shown in the table below.
To modify the active configuration file, you need to be in Global Configuration mode.
| Mode | Description | Prompt | How to Access |
| Exec mode | Allows limited access to view configuration settings and performs basic troubleshooting commands, such as ping and traceroute to test for connectivity. | Router> | This is the initial or default mode when a user logs into a Cisco device. |
| Privileged Exec mode | Enables the user to view all settings and execute commands, such as reload, which tells the switch to reboot the Cisco IOS. Privileged access should be password-protected to prevent unauthorized access. | Router# | While in Exec mode, issue the enable command. |
| Global Configuration mode | Provides writable access to modify the active configuration file. | Router(config)# | From Privileged Exec mode, enter the command configure terminal. |
How Netwrix Can Help
To ensure normal, secure operations for your business, it isn’t enough to save changes to your running configuration settings — you also need to monitor activity on your Cisco devices and broader network infrastructure.
Netwrix Auditor for Network Devices provides complete visibility into what is happening in your network infrastructure and alerts you about the events you consider the riskiest. It provides clear, actionable information that dramatically simplifies investigation and enables prompt and effective response.
Here are just some of the things you can do with this Netwrix solution:
- Audit attempts to log on to network devices to promptly spot suspicious events.
- Monitor password resets and configuration changes to catch threats in their early stages.
- Get alerts about hardware malfunctions so you can respond promptly and minimize business impact.
- Track scanning activity to detect attackers conducting reconnaissance to help them breach your network and steal sensitive data.



