Open Access or unrestricted file share access is an inevitable condition that exists in most if not all, enterprise environments. Many organizations create ‘Open Shares’ to allow end-users an easy way to access resources.
These shares are open because access to them is unrestricted at both the Share and NTFS levels, meaning most end users can access them. This is achieved by the use of ‘Open Access Groups’ such as the built-in groups listed below:
- Everyone—This group encompasses all users who have authenticated to the system using a valid set of credentials, as well as built-in accounts, including GUEST and LOCAL_SERVICE.
- Authenticated Users – This group is a subset of the Everyone group, excluding non-password-protected built-in accounts such as GUEST.
- Anonymous Logon – This built-in security group includes users or services that access resources over a network connection by using a null user account name, domain, and password.
- Domain Users – The domain users group is a default group within Active Directory to which all user accounts are added by default.
By default, when you create a CIFS share in Windows and many other operating systems, the Everyone group is granted read access at the share level, leaving administrators to lock down access through the NTFS permissions. This is a best practice from Microsoft and is completely fine as long as admins take the appropriate steps to lock down access.
While some shares are intentionally left open, the number of open shares inevitably grows beyond expectations due to sloppy access provisioning within Active Directory, complex group nesting structures, or even lazy administrators.
This quickly becomes problematic when sensitive data such as PII or PCI is contained within these open repositories. A Ponemon Institute study showed that 71% of employees say they have access to data they shouldn’t have and that this access is “frequent” or “very frequent”.
Now, in the event of a data breach, the attacker has essentially been given an open door to potentially valuable data, even when using the lowest-level credentials. In this case, the attacker doesn’t need to go through the additional credential theft exercises that would typically raise the red flags that organizations are prepared to detect.
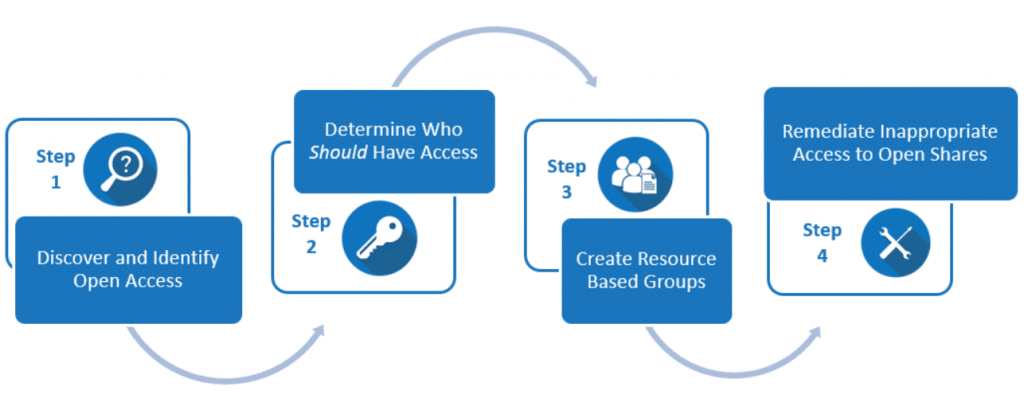
Here at Netwrix, we work with clients daily to help remediate this open share epidemic and have developed a proven approach to do so. It comes down to four basic steps:
- Discover and Identify Open Shares
- Determine Who Should Have Access
- Create Resource-Based Groups
- Remediate Inappropriate Access to Open Shares
The first step in remediating open shares is knowing where they exist. With a solution such as Netwrix Access Analyzer, you have the ability to scan your entire environment to search, discover and identify open file shares.
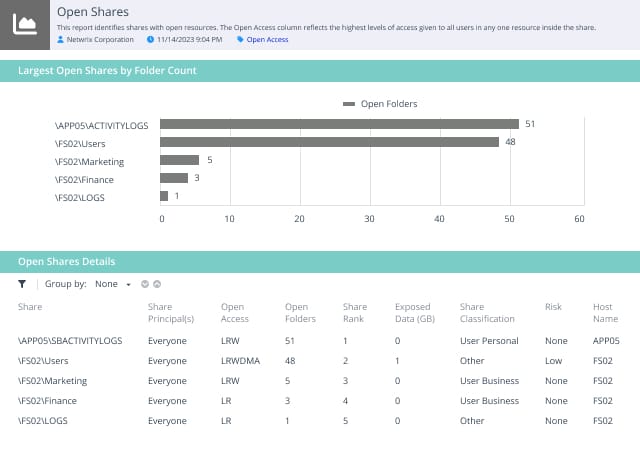
The approach here is flexible. It has the built-in capability of identifying areas where the combination of share and NTFS permissions exposes data through the open-access groups mentioned earlier in this post. Administrators can also specify additional Active Directory or local groups that provide a similar level of access.
Determine Who Should Have Access
Much of the reason that Open Shares are created in the first place is since it can sometimes be difficult to determine who should actually have access to a given set of resources. For example, it may be easy to assume that the Marketing department members are the only folks who would ever need access to the Marketing Share, but what about when the Product Management team is collaborating with Marketing on a new campaign or new collateral? Then, in this case, it may be appropriate to grant some level of access to the Product Management team.
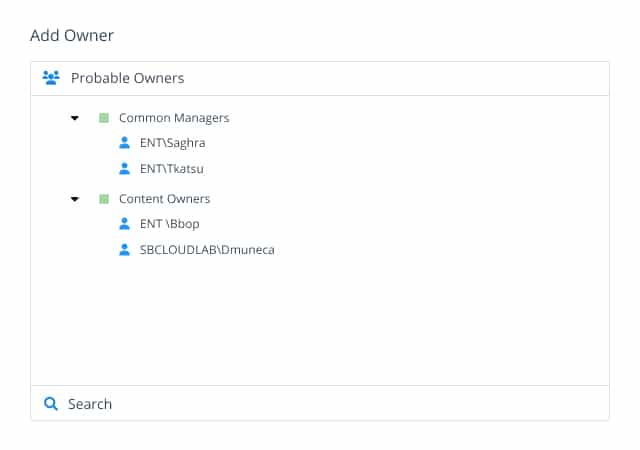
Netwrix Access Analyzer leverages historical knowledge of who actively accesses the data where and to what capacity to decide who should have access to a given resource. And these decisions aren’t made in a black box. With the proven ability to determine data owners and visibility into Active Directory to understand organizational hierarchy, the right audience can approve any level of access that will be granted.
Create Resource-Based Groups
A resource-based groups access model makes it easy to manage access on a resource by resource basis. The Netwrix Access Analyzer approach leverages our knowledge of who actively access this information and to what capacity to automatically create and populate Active Directory groups for each level of access required on a per-share basis, and goes a step further to actually assign the appropriate access. This step is important because it not only ensures that the folks who need access are getting it but also removes folks who have access but are not using it.
This approach also helps to streamline the self-service process, making it easy for end-users to request and be granted access through these new resource-based groups, while also making the entitlement review process easier.
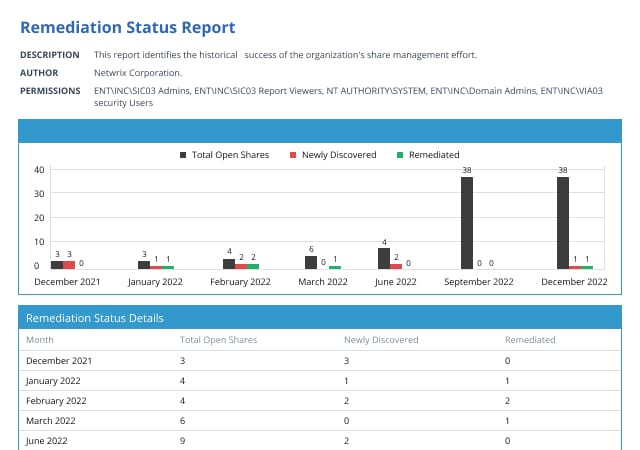
Once these resource-based groups have been assigned, you can safely remove the access for the open-access groups that were previously provisioned, without fear of locking users out of shares they need to which they need access. Netwrix Access Analyzer provides state in time reports to easily display an organizations progress through this open share remediation process.
Maintain a Least Privilege Model Going Forward
Now with this approach, you’ve been able to remediate the open shares that you know about today, but what about tomorrow? Open shares pop up day after day, month after month, year after year, so it’s important to automate and maintain this process for open share discovery and remediation.
Using software such as Netwrix Access Analyzer lets you automate this process with ease, providing regular discovery of open shares, easy determination of data owners, and a proven process to remediate this condition without disrupting day to day work.



