BadUSB, Rubber Ducky, and Flipper Zero devices bypass traditional USB blocking by impersonating keyboards and executing commands at machine speed. Netwrix Endpoint Management combines Endpoint Protector’s device control with Policy Manager’s privilege enforcement to block rogue devices, remove unnecessary admin rights, and contain lateral movement before it escalates.
A $50 gadget can undermine your defenses in seconds. BadUSB, Rubber Ducky, and Flipper Zero devices impersonate keyboards, firing off commands at machine speed to disable protections and create backdoors. These aren’t sci-fi scenarios; they’re real attacks that many USB defenses miss.
Here’s how they work, why traditional controls fail, and how to prevent them effectively.
A $50 USB Stick Can Wreck Your Network
Imagine this: A USB drive is left in your parking lot. An employee plugs it in, just curious.
Within seconds, the device pretends to be a keyboard and types hundreds of commands at machine speed. It disables protections, installs malware, and opens backdoors.
All it takes is one plug-in. One careless moment. One $50 device.
This isn’t sci-fi. It’s real. These attacks are known as BadUSB, Rubber Ducky, or Flipper Zero exploits, and they’re one of the most overlooked endpoint threats today.
What Are BadUSB, Rubber Ducky, and Flipper Zero Attacks?
These attacks are classified as HID (Human Interface Device) exploits. The trick is simple but devastating:
- They don’t act like storage. Instead of showing up as a USB drive, they impersonate a keyboard.
- They move faster than any human. Commands are typed at lightning speed before anyone can react.
- They exploit trust. Operating systems treat them as legitimate keyboards, giving them a free pass.
Anatomy of an Attack
USB HID attacks are the cybersecurity equivalent of sleight of hand—deceptively simple but highly effective:
- Delivery: The attacker plants the device in a place your employees might find or mails it directly.
- Execution: The device is plugged in, and keystrokes begin instantly.
- Privilege escalation: If the user has local admin rights, the fake keyboard can effectively disable antivirus software, launch malware, or create new accounts.
- Lateral movement: If admin credentials are reused across machines, attackers spread rapidly through your network.
The result? A small device triggers a potentially catastrophic breach.
Why Old Defenses Fail
Most organizations block USB storage. But USB blocking does not equal HID blocking. A BadUSB doesn’t appear as storage; it presents itself as a new keyboard. That’s why traditional defenses miss the threat, creating a blind spot for many security teams.
To see these blind spots in action and learn how to close them, watch our webinar: Modern Device Control & USB Security: Beyond Blocking.
How Netwrix Stops the Attack
Netwrix Endpoint Protector: Device Control for HID Attacks
With Endpoint Protector’s Device Control module, you can prevent rogue HID attacks in real time:
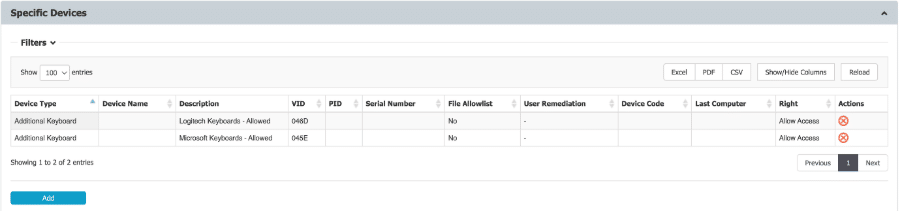
- Block additional keyboards: A one-click policy blocks all “extra keyboards” from functioning.
- Vendor ID whitelisting: Only trusted, recognized keyboards work. Anything masquerading as a keyboard but lacking an approved Vendor ID (like Rubber Ducky or Flipper Zero) is denied.
- Cross-platform enforcement: Alerts and blocks on Windows, macOS, and Linux.
Result: Low-maintenance, high-impact protection that neutralizes HID attacks.
Here’s the two-step process using Endpoint Protector.
Step 1: Deny Access for Additional Keyboards.

Step 2: Use Vendor ID whitelisting to ensure that only trusted, recognized keyboards in your environment will function. Any device attempting to masquerade as a keyboard but failing the Vendor ID check (e.g., a Rubber Ducky) is blocked instantly.
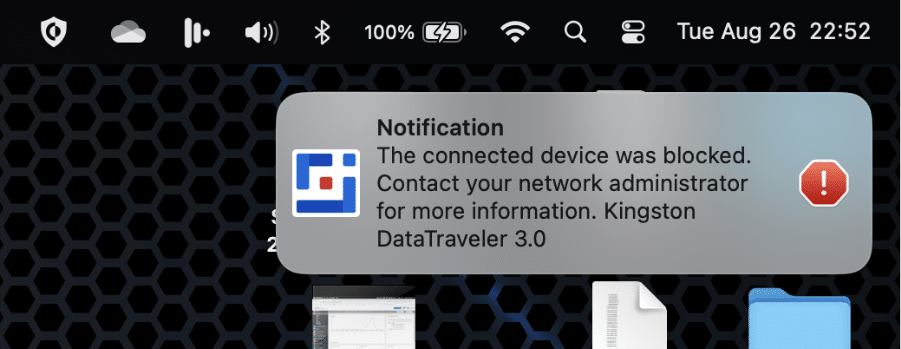
The results are obvious to end users. Here’s an example of blocking an unintended device (similar pop-ups for Windows, Mac, and Linux machines).
Netwrix Policy Manager: Defense in Depth
If attackers gain physical or remote access, device control alone isn’t enough. That’s where Netwrix Policy Manager (formerly PolicyPak) comes in:
- Remove local admin rights by default, reducing the risk of privilege escalation.
- Enable just-in-time access by integrating with ServiceNow or your helpdesk to approve legitimate admin requests as needed.
- Restrict the use of high-risk tools such as PowerShell, CMD, and Run, while allowing exceptions for approved applications and scripts.
- SecureRun™ – Automatic blocking of untrusted self-download applications.
Together, these controls ensure attackers can’t use rogue devices or stolen privileges to take over your systems. Creating EPM rules to overcome UAC prompts is easy.
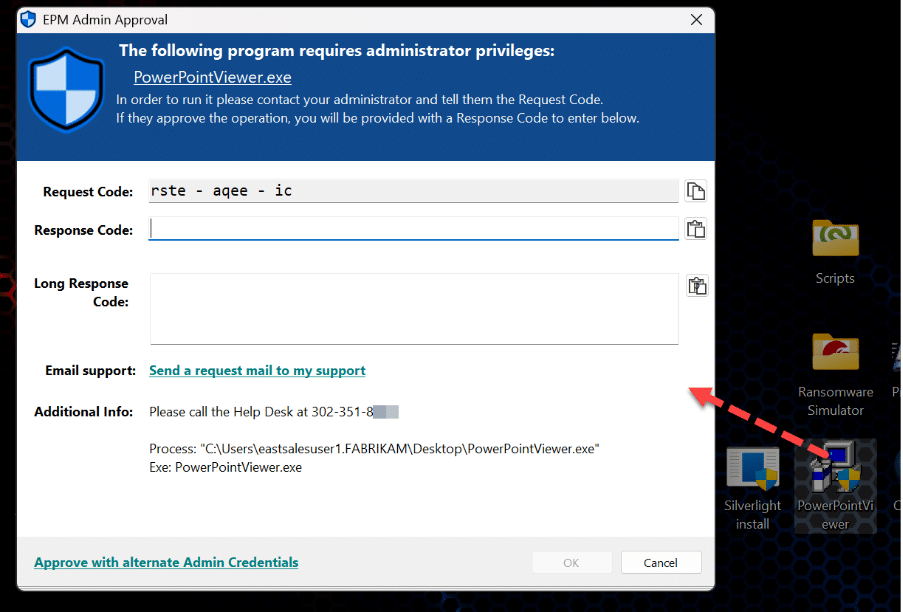
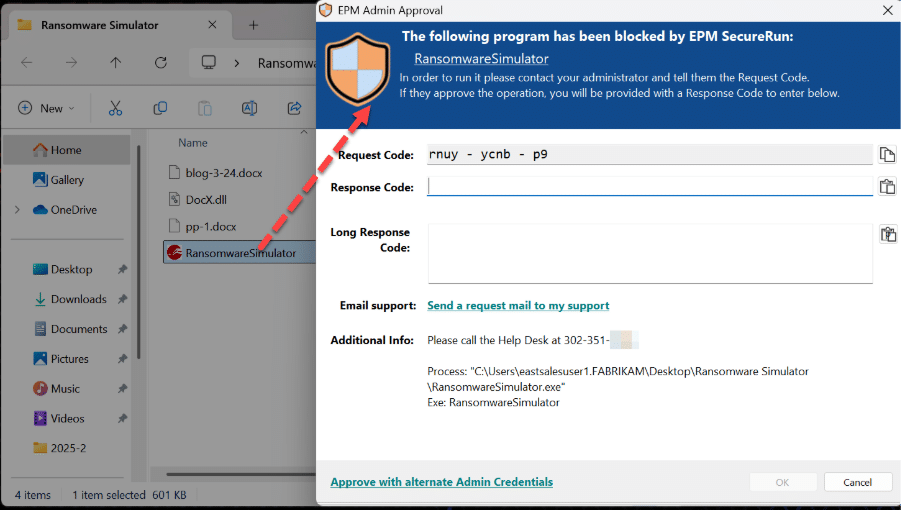
And for those items which don’t yet have rules, users may the Just-in-time Admin Approval access like what is seen here.
Items which are automatically blocked by SecureRun can be also be fielded by your Servicenow / HelpDesk.
Business Value for Security Leaders
Netwrix Endpoint Management (Endpoint Protector + Policy Manager) isn’t just about stopping gadgets; it’s about reducing organizational risk while keeping IT efficient:
- Compliance-ready: Satisfies NIST, CIS, and ISO guidelines for removable media and privilege management.
- Operational simplicity: No productivity loss, users keep their trusted devices while attackers don’t.
- Risk reduction: Detects and blocks lateral movement attempts before ransomware can spread.
- Cost avoidance: Prevents high-dollar incident response and downtime from a single careless action.
Key Takeaway
BadUSB, Rubber Ducky, and Flipper Zero attacks target the most trusted device in your environment: the keyboard.
With Netwrix Endpoint Management, powered by Endpoint Protector and Policy Manager, you:
- Block rogue USB HID devices before they execute.
- Remove unnecessary local admin rights and enforce least privilege.
- Contain lateral movement with just-in-time access and privileged session controls.
A high-risk attack vector becomes a non-issue, and now a $50 gadget no longer poses a million-dollar risk.



