Managing change for in-house applications and platforms is crucial for maintaining stability, security, and accountability. Unlike managing changes at the device level, working with applications requires a more comprehensive strategy. Let’s break it down.
Why Change Control Matters
Imagine trying to manage an application that spans multiple environments, each with its unique configurations. Things can get messy fast. Here’s why change control is a must:
- Deployment Complexity: Most applications aren’t just one piece of software. They’re a collection of binaries that need constant monitoring—sometimes across multiple regions.
- Configuration Complexity: Think about the critical settings for your application—authentication, authorization, encryption, and external integrations. Now imagine what happens if unauthorized changes occur. Beyond the security risk, it’s often hard to even find where all these settings are, especially in distributed applications.
- Stability and Reliability: A single unplanned change can bring your application to its knees, causing downtime or degraded performance. With a robust change control process, you can trace issues, troubleshoot effectively, manage accountability, and avoid chaos.
Unauthorized changes like these could be an indication of a security breach in action.
What Changes Should You Focus On?
When it comes to managing change, not all changes are created equal. Here are the big ones you’ll want to keep an eye on:
- Critical Configurations: These include settings for authentication, privileges, authorization, encryption, and integrations with external systems. They’re the foundation of your app’s security.
- System and Application Changes: Things like config files, OS settings, database configurations, network settings, and registry values all fall here. These tweaks might seem small but can have huge impacts.
- Code and Binary Modifications: Ensure that any changes to your application’s code or binaries are tracked and secure.
- Database Schema Updates: These require special attention to ensure they don’t disrupt your application’s functionality or performance.
Monitoring critical files and configurations such as these is known as File Integrity Monitoring (FIM) and it’s what Netwrix Change Tracker excels at.
FIM for your Applications and Platforms with Netwrix Change Tracker and Splunk
New to Netwrix Change Tracker in version 8 is an integration with Splunk that makes it possible to collect change events from anything that can log changes in its configuration to Splunk:
- Logging Change: Configure Splunk to collect and index changes to your application’s configuration.
- Query the data: Build a query in Splunk that returns changes to your application’s configuration.
- Configure the Splunk integration in Change Tracker:
- Enter credentials to authenticate Change Tracker for API access to Splunk.
- Create a device in Change Tracker for your application. The change events will be linked to this.
- Configure a tracking policy with your Splunk query so Change Tracker knows which events to pull.
- Filter Authorized Changes Connect Change Tracker to your ITSM system to pull in data on planned changes or create planned changes in the UI.
- Auditing, Alerting, and Reporting: Any unplanned change with no authorized planned change will be audited as such and trigger an alert. Reporting can be scheduled to obtain an overview of unplanned change.
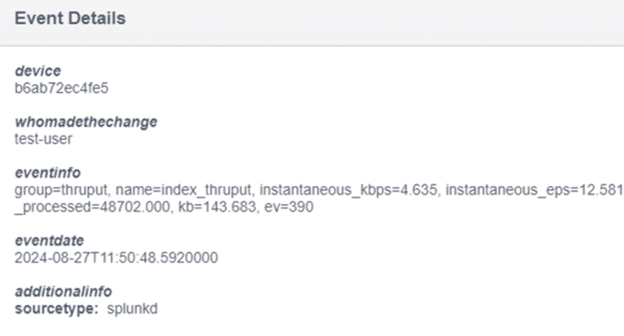
A change event from Splunk in Change Tracker with details on what was changed, who changed it, and when.
For details on configuring this integration please check our documentation.
Conclusion
The paring of Change Tracker and Splunk provides a scalable and easy way to perform File Integrity Monitoring on your inhouse applications and platforms despite the complexity in their architecture or deployment.


