The foundation of Windows security is simple — if you want access to a network resource such as a file or folder, you need the appropriate permissions. But implementation is more complex because the Windows operating system has two types of permissions: NTFS permissions, which operate at the file system level, and share permissions, which govern network access to shared resources.
In this article, we’ll explore NTFS permissions vs share permissions, including what each of these permission types can do, how they are different, and how you can use NTFS and share permissions together to enforce the principle of least privilege across all your Windows machines.
What Is NTFS?
NTFS (New Technology File System) is the standard file system for Microsoft Windows NT and later operating systems, replacing an older file system called File Allocation Table (FAT). However, FAT (especially FAT32) is still used, especially on removable storage devices.
NTFS supports efficient storage and retrieval through its Master File Table (MFT), which tracks all files and directories on the disk. This structure allows NTFS to manage large amounts of data effectively while maintaining quick access times. Moreover, its file size support can handle the demands of today’s modern applications and media storage. In terms of security, it supports encryption at both the file and folder levels, and it allows administrators to set detailed permissions for files and folders as well.
What Are NTFS Permissions?
NTFS permissions are used to manage access to data stored in NTFS file systems. The main advantages of NTFS share permissions are that they affect both local users and network users and that they are based on the permissions granted to an individual user at Windows logon, regardless of where the user is connecting from.
There are both basic and advanced NTFS permissions. You can set each of the permissions to Allow or Deny to control access to NTFS objects. Here are the basic types of access permissions:
- Full Control — Users can add, modify, move and delete files and directories, as well as their associated properties. In addition, users can change permissions settings for all files and subdirectories.
- Modify — Users can view and modify files and file properties, including adding files to or deleting files from a directory, or file properties to or from a file.
- Read & Execute — Users can run executable files, including scripts.
- Read — Users can view files, file properties and directories.
- Write — Users can write to a file and add files to directories.
How to Set NTFS Permissions (Step-by-Step Guide)
- Right-click the shared folder.
- Open the Security tab and click Edit, as shown below:
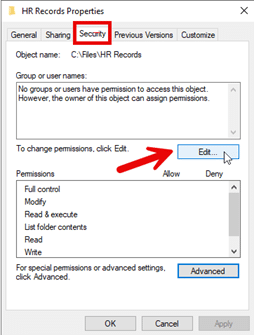
- Click Add. Then select the desired group (HR Personnel in the example below), and use the Allow and Deny checkboxes to assign the desired permissions, as shown below.
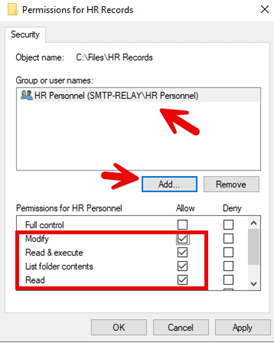
- Click Apply to apply the permissions.
Share permissions manage access to folders shared over a network, such as a shared folder located on a centrally hosted file server. Share permissions do not apply to users who log on locally. Share permissions apply to all files and folders in the share; you cannot granularly control access to subfolders or objects on a share. You can specify the number of users who are allowed to access the shared folder. Shared folder permissions can be used with NTFS, FAT and FAT32 file systems.
There are three types of share permissions:
- Read — Users can view file and subfolder names, read data in files and run programs. By default, the Everyone group is assigned Read permissions.
- Change — Users can do everything allowed by the Read permission, as well as add files and subfolders, change data in files, and delete subfolders and files. This permission is not assigned by default.
- Full Control — Users can do everything allowed by the Read and Change permissions, and they can also change permissions for NTFS files and folders only. By default, the Administrators group is granted Full Control permissions.
- Right-click the shared folder.
- Click Properties.
- Open the Sharing tab and click the Share button to share the folder:
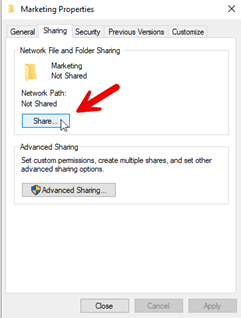
- Choose the group you want to share the folder with and assign share permissions as shown here:
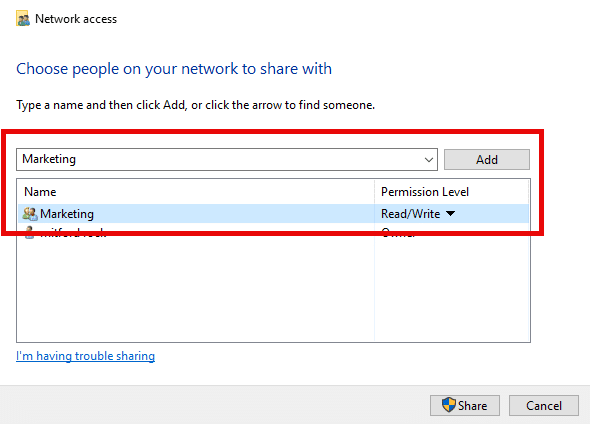
- Click the Share button at the bottom right.
- Once a folder is shared, you set advanced options. First, click Advanced Sharing:
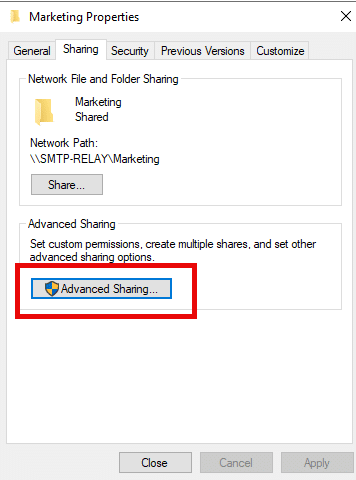
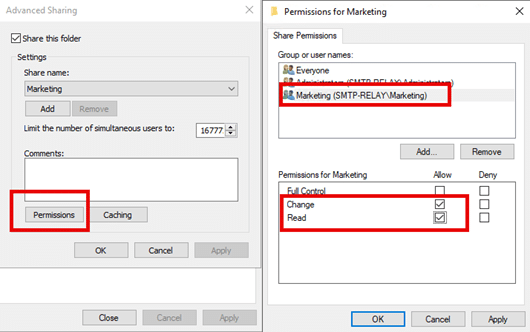
Then click the Permissions button. In the popup window, choose a user or group and assign the desired permissions, as shown below. Then click OK to complete the assignment.
Understanding the differences between share permissions and NTFS permissions is essential for properly managing access to files and folders in a Windows environment. Here are some key differences between the two:
| Feature | Share Permissions | NTFS Permissions |
| Ease of Management | Easy to apple and manage | More granular control of folder and contents |
| File System Compatibility | Works with both NTFS and FAT or FAT32 file systems | Available for NTFS file systems only |
| Connection Restrictions | Can limit concurrent connections | Cannot limit connections |
| Configuration Location | Advanced Sharing > Permissions | File/Folder Properties > Security tab |
| Scope of Access Control | Regulates remote network access only | Secures both local and remote access |
| Local Access Impact | Does not affect local access | Controls local and remote access |
| Security Coverage | Limited to networked environments | Secures both local and remote access |
| Complementary Use | Requires NTFS permissions for full protection | Functions independently but enhances overall security |
When both NTFS and share permission are in use, what happens when they overlap? For instance, if a folder has Full Control share permissions but only Read NTFS permissions, what is the final result?
When NTFS and share permissions are used simultaneously, the most restrictive permission always wins. For example, if the shared folder permission for the Everyone group is set to Read and the NTFS permission is set to Modify, the share permission applies because it more restrictive; the user is not allowed to change files on the shared drive.
It is generally recommended that you set share permissions at a higher level while using NTFS permissions to enforce specific access controls. For example, consider a shared folder in a collaborative environment where a team needs to access files frequently. Setting share permissions to Full Control for a group of users allows them to easily create, modify and delete files without encountering access issues when they connect to the shared folder over the network. However, to protect sensitive data within that shared folder, you can apply more restrictive NTFS permissions that limit access to specific files or subfolders. This approach ensures that while users can interact freely with most of the content in the shared folder, sensitive information is still protected by stricter NTFS controls.
Best Practices for Managing Permissions
Below are some best practices for managing permissions effectively and securely:
- Always assign permissions to groups rather than individual users unless you absolutely must. Assigning permissions to individual user accounts can lead to a complex and unmanageable permission structure. For instance, when a user gets deleted, any permission entries for that user will remain as orphaned SIDs in the Access Control List (ACL), cluttering the system and complicating permission management.
- Implement the principle of least privilege (PoLP): Grant users the permissions they need and nothing more. For example, if a user needs to read the information in a folder but never has a legitimate reason to delete, create or change files, make sure they have only the Read permission.
- Assign permissions to groups, not user accounts: Assigning permissions to groups simplifies management of shared resources. If a user’s role changes, you simply add them to the appropriate new groups and remove them from any groups that are no longer relevant.
- Use only NTFS permissions for local users: Share permissions apply only to users who access shared resources over the network; they do not apply to users who log on locally.
- Put objects with the same security requirements in the same folder: For example, if users in one department require Read permission for several folders, store those folders in the same parent folder and share that parent folder, rather than sharing each folder individually.
- Manage the Everyone and Administrators groups wisely: Limit the Everyone group to public or non-sensitive resources and avoid granting it access to critical systems or data. Keep the membership of the Administrators group minimal, and use separate accounts for administrative tasks rather than giving admin rights to day-to-day accounts.
- Avoid nested permission conflicts: Set permissions at the highest level possible in the folder structure and limit the use of deeply nested groups or folder structure to prevent unintended inheritance. Avoid breaking permission inheritance by using explicit denials sparingly.
- Use tools for permission management and audits: Employ audit tools to generate reports on who has access to what and when permissions were changed, and configure alerts for unexpected permission changes and access attempts.
- Document and describe your permission strategy and processes: Handling NTFS and shares permission in an ad-hoc manner can create unnecessary complexity and security gaps. Best is to define your permission philosophy and strategy upfront and combine them with tested process of granting, monitoring and removing permissions on a frequent, regular basis.
Troubleshooting Permission Issues
Diagnosing and Fixing Broken Permissions
Broken permissions occur when users cannot access resources they are authorized to use or gain access to unintended areas due to misconfigurations. To identify and address these issues:
- Use tools or operating system features to check the effective permissions of a user or group on a specific resource.
- Check for and remove any unknown or unresolved SIDs (security identifiers) in permission entries, which may indicate orphaned accounts.
- Ensure the correct user or group owns the resource, as ownership can override other permissions. As an administrator, you may have to take ownership of the file or folder and reset permissions.
- For critical groups, consider explicitly assigning the required permissions instead of relying solely on inheritance.
Overlapping or inherited permissions from nesting cause unexpected access issues or conflicts. To address these issues:
- Review the effective permissions by combining share and NTFS permissions, remembering that the most restrictive permission takes precedence.
- If possible, avoid using nested shares when possible, as they can create confusing permission scenarios.
- Trace permission hierarchies by mapping out inherited permissions between levels to understand the flow and identify conflicts.
- Check for Deny permissions at any level, as they can override Allow permissions higher in the hierarchy.
Using Permission Inheritance Effectively
You can streamline management by allowing resources to inherit permissions from parent objects. However, make sure you understand how inheritance works, since permission inherited from parent folders can override explicit permissions assigned to child folders, potentially granting broader access than intended. These best practices can help:
- Periodically review inherited settings to ensure they align with organizational policies.
- To update all subfolders and files when modifying folder permissions, use the Replace all child object permissions entries with inheritable permission entries from this object option.
- Be cautious when breaking inheritance, as it can lead to unexpected access issues. Disable inheritance only when absolutely necessary, and be sure you understand the implications.
In most situations, NTFS permissions are going to be your best choice as they are tied to the file system itself. In cases where users will be accessing resources directly on a Windows machine they are logged onto, NTFS is the only option, since file share permissions don’t limit local access. NTFS permissions also offer more fine-grained control over files and subfolders within a shared folder, and they can accommodate more complex permission structures when you need to set different permissions for various users or groups on specific files or subfolders.
There are cases when Windows share permissions may be better suited. In particular, for any drive partitioned with FAT32, NTFS permissions are not an option. In addition, share permissions enable you to restrict the number of remote users that can simultaneously access a shared folder. Sharing permissions may also be suitable in a small office where resources are accessed only over the network and there isn’t a dedicated admin to manage the environment.
You will get the best results, however, when you combine NTFS and share permissions, remembering that the most restrictive permission will always take precedence. Keep share permission broad and use NTFS permissions for detailed access control. A good rule of thumb is to set share permissions to Full Control for admins and Change for domain users, and use NTFS permissions for more granular control.
Automating Permissions Management
Manually managing permissions can be a tedious and time-consuming task, and it is susceptible to human errors that can compromise security. Automation can enhance security and reduce administrative workload.
Role-Based Access Control (RBAC) and Automation Tools
With RBAC, access rights are granted to roles rather than to individual users, and then each user is assigned the appropriate role or roles based on their job functions. When the needs of a role changes, such as when a new application or database is adopted, the role is granted the appropriate new permissions and all the users with that role automatically inherit those permissions. When a particular user’s duties change, their permissions can be updated simply by changing their role assignments.
One native tool for managing user access and permissions is Active Directory (AD). AD provides user templates that simplify account creation, enable group-based permission assignment, and integrate seamlessly with numerous third-party applications. There are also some excellent third-party tools on the market. For instance, SolarWinds Access Rights Manager (ARM) and Lepide can help automate user provisioning, while Netwrix Identity Manager offers identity lifecycle management, access certification and audit reporting to ensure that users have appropriate access to resources based on their roles
Conclusion
Mastering the nuances of share permissions vs NTFS permissions is essential for enforcing the principle of least privilege in a Windows environment. Taking advantage of permission inheritance, leveraging role-based access control and utilizing advanced automation tools can make access management a lot simpler for you as an administrator. By adopting the best practices outlined in this guide and investing in the right tools, you can ensure effective permissions management and stronger cybersecurity.
FAQ
What is the difference between share and NTFS permissions?
Share and NTFS permissions serve different but complementary roles in Windows security:
- Share permissions control network access to shared resources only. These permissions don’t affect local access to files and folders. There are three basic levels: Read, Change and Full Control.
- NTFS permissions provide comprehensive protection for both local and network access, with six granular permission levels: Read, Write, List Folder Contents, Read & Execute, Modify, and Full Control. NTFS permissions apply to all files and folders on NTFS volumes, support inheritance and special permissions, and enable file encryption.
Which takes precedence, NTFS or share permissions?
When both NTFS and share permissions are present, Windows enforces the most restrictive permission. For instance, if share permissions allow Full Control but NTFS restricts to Read, the user will have only Read access.
What happens when share permissions and NTFS permissions combine?
When share and NTFS permissions are combined, the most restrictive permission always applies. This provides an additional layer of security by ensuring users can’t exceed their most restricted permission level, regardless of whether it comes from share or NTFS permissions.
What is the purpose of NTFS permissions?
The core purpose of NTFS permissions is to enable consistent least-privilege access control, whether the resource is accessed locally or over the network. They also:
- Support inheritance through folder hierarchies
- Provide granular control over shared folders and their contents
- Allow file and folder encryption
- Enable auditing of access attempts
Do NTFS permissions override share permissions?
NTFS permissions do not override share permissions by default. However, if accessing a resource over the network, share permissions cannot grant a higher level of access than the active NTFS permission. When both permission types are enabled, the most restrictive permission wins.
What happens when you combine both share and NTFS permissions on a share?
When combining share and NTFS permissions on a shared resource, the most restrictive permission takes precedence. While share permissions do not apply for local access, both share and NTFS permissions can be applied for network access. For instance, if share permissions are Full Control and NTFS permissions are Read, the user will have only Read access
What are the best practices for share and NTFS permissions?
- Use share permissions for broad access control, and rely on NTFS for detailed permission management.
- Keep permissions simple and organized
- Except for files residing on a non-NTFS partition, never rely solely on share permissions.
- Remove any unnecessary admin rights.
- Use explicit Deny permissions only for special circumstances.
- Monitor access patterns to identify suspicious attempts to access sensitive data.
- Conduct periodic reviews of your permission settings to ensure they align with current business practices and security requirements.


