Let’s face it. Managing and securing IT networks is far more complex today. Beyond securing endpoints, sensitive data, and the network perimeter, security teams must also focus on identity security, access management, and regulatory compliance. They not only have to create password policies but protect those passwords and access privileges. Twenty years ago, no one had to worry about things such as cloud identity. Today, a different world demands a different set of tools.
Identity Governance and Administration (IGA) tools play a vital role today in securing the identities that comprise your network. IGA is about more than just secure authentication. They automate identity management processes, reduce administrative burdens, and ensure appropriate access controls. IGA tools ensure that essential identity lifecycle management tasks, such as onboarding and provisioning, are handled quickly and consistently. This not only enhances security but improves the operational efficiency of IT and supports scalable organizational growth. For this and other reason, IGA tools are becoming a mainstay for the modern enterprise.
Reasons for Needing an IGA Solution
Before investing time in exploring various IGA solutions, you might question whether your organization even needs one. If you are a digital organization, you need some way to manage and secure the many digital identities that need to connect and interact with your digital environment. Implementing an IGA solution provides enhanced visibility into identity administration and access entitlements across your IT infrastructure. It offers a practical approach to implementing Zero Trust and Least Privilege access models, which are essential in today’s cybersecurity landscape. Beyond these fundamental benefits, there are several other compelling reasons to consider an IGA solution:
- An IGA solution will help your organization prove compliance with your encompassing data regulations worldwide.
- IGA reduces the administrative burden on IT staff and streamlines workflows by automating identity and access management processes.
- IGA can lower your operational support costs by automating repetitive tasks like provisioning saves time and money, a savings that only compounds as the business scales.
- IGA can scale along with your growing hybrid architecture as you incorporate more cloud resources and services that expand your attack surface.
IGA vs. IAM: What’s the Difference
Sometimes people get confused between Identity Governance and Administration and Identity Access Management (IAM) as both deal with the management of identities and access within an organization. The differences between the two begin with their scope and focus.
- IAM is primarily concerned with the technical aspects of identity management, such as authentication (verifying that someone is who they claim to be), authorization (determining what resources they can access), and ensuring secure access to systems and data.
- IGA includes these IAM functionalities but extends beyond them to incorporate governance. This means IGA is concerned with ensuring that access rights are not only implemented but also monitored, reviewed, and audited regularly to comply with policies, regulations, and business requirements.
In summary, while IAM provides the tools and processes to control access, IGA ensures that these controls are compliant, auditable, and aligned with organizational governance and regulatory requirements. IAM handles the “how” of access, while IGA handles the “why” and “whether it should continue”.
Key Features of IGA Tools
Now that we have established the necessity of identity governance and administration tools and the available options today, let’s examine the features that a robust IGA tool solution needs to have.
- Identity Lifecycle Management capabilities that include things such as user onboarding and provisioning, credential management, access request reviews and deactivation processes.
- Automated access request management that streamlines the process of requesting, approving, and granting access to systems, applications, and data.
- Provisioning and de-provisioning of user accounts quickly enough to keep pace with dynamic personnel changes
- Entitlement management that oversees granting, issuing, and revoking user access to digital resources
- Role-Based Access Control (RBAC) that manages user access based on predefined roles so that permissions are restricted to the least privileged access of job roles.
- Segregation of Duties (SoD) in which IGA tools define SoD policies and analyze access rights across multiple applications and systems to identity potential violations.
- Access certification and Review means that IGA tools automate the process of regularly reviewing user access rights to ensure compliance with regulations.
- Policy enforcement that is automated and consistent
- Audit and compliance reporting that simplifies the process of meeting routine or on-demand audit requirements, reducing the reporting burden on cybersecurity personnel.
- Analytics and reporting capabilities that provide customizable dashboards, visualizations, and detailed reports on user access, risk levels, and compliance status.
Benefits of Implementing IGA Tools
While robust security is of the essence, businesses cannot allocate unlimited funds to cybersecurity. Companies today are striving to automate as many of their business processes as possible, including cybersecurity. Modern IGA tools include automated features that simplify identity management and access control. This reduces the burden on security teams and enhances efficiency. By automating the provisioning and deprovisioning of user accounts, manual intervention and human error are eliminated. This also frees up security teams to focus on tasks of a greater value. Other benefits of IGA tools include the following:
- Enhanced security: IGA tools enhance security and reduce risks by providing greater visibility across IT environments. Comprehensive audit trails and anomaly detection are two examples of how this increased visibility can help your organization identify potential threats and improve their overall security posture.
- Efficient access management: Greater efficiencies are achieved through automation by accelerating access management tasks, leading to significant time which again reduces costs.
- Improved Compliance and Audit Performance: IGA tools make it easier to demonstrate compliance with extensive auditing trails by facilitating access reviews, either periodically or on demand.
- Support for Enterprise Security: Only automation can quickly adapt to the scale of your business quickly and reliably to ensure consistent security practices at scale.
- Flexible Access for Improved Productivity: Streamlining the management of user accounts means that employees can quickly obtain the necessary permissions without overcompensating privilege.
Specific Business Problems Addressed by IGA Tools
Cyberattacks can inflict costly disruptions to your business. In addition, the cost of remediation, forensic analysis and damage to your brand’s reputation can significantly impact the bottom line as well. When you reduce risk to your business through strengthened security, you save money in the long run. Some of the ways that IGA tools reduce risk include the identification and remediation of inappropriate access to key resources as well as automated policy enforcement.
By automating many of the labor intensive processes of Identity Governance and Administration you not only enforce consistent security enforcement, but you also reduce the operational costs of these tasks. By delivering faster and more efficient access, employees can be productive right out of the gate and adapt quickly to new responsibilities roles. In some cases, IGA tools may provide self-service access management that allows users to streamline the onboarding process at the best time for them.
For those organizations that are bound by regulatory or industry compliance, the centralized visibility of access rights improves compliance and audit performance. IGA tools provide detailed audit trails and reports, enabling organizations to track who has access to what resources and how those accesses were granted. This makes it easier for security teams to verify controls for regulations such as HIPAA, GDPR, and SOX.
Types of IGA Solutions
In terms of architecture, there are three primary IGA tool solution types. The first is an on-prem solution that requires software to be installed and operated withing an organization’s own IT infrastructure.
Cloud based IGA tool solutions reduce the need for extensive infrastructure as they reside on some type of cloud. This simplifies deployment and negates support and maintenance costs. They provide greater scalability and flexibility compared to traditional on-prem solutions and provide more seamless integration with other IT systems.
Hybrid IGA tool solutions combine the benefits of both on-prem and cloud based in one package. This allows organizations to manage identities and access rights across both on-premises and cloud environments. They support dynamic business needs while allowing for gradual migration to the cloud while maintaining critical on-premises infrastructure.
Key Considerations in Implementing IGA Tools
It would be nice if you could just base a purchase decision on the feature set of a product, however, as IT decision makers know, there are other factors to consider. Unless you are a new business startup, you have an existing network to consider that probably includes legacy applications and systems. Comprehensive security of your enterprise means that any proposed IGA tool solution must integrate seamlessly with your current systems and infrastructure.
Depending on the industry that your organization serves, your organization must grapple with compliance requirements, which means that your proposed solution must support adherence to them. You also must include users in the equation as their experiences will have a large bearing on the long-term success of your IGA tool implementation. Training will have to be provided that educates them on how it will affect their job roles and why it is so important.
Because businesses are so dynamic today, you must choose a solution that will accommodate future growth as well as the evolving needs of your organization without the threat of significant disruption. Like any IT product, vendor support and reputation must be heavily considered. Considering all these factors will help organizations implement IGA tools effectively, enhancing security, compliance, and operational efficiency.
Use Cases of IGA Tools
Enterprises are migrating more services and applications to the cloud every day. This makes cloud identity governance has become increasingly important as administrators need the ability to manage identity and access rights across multiple cloud environments. Visibility is a real challenge in cloud environments and IGA tools provide the insights you need to understand what is going on throughout all the underlying layers of the cloud so that you can maintain control. Of course, very few enterprises are cloud only today, which means your IGA tools must be able to manage hybrid environments. These tools unify identity governance across on-premises and cloud infrastructures, centralizing access control for diverse IT ecosystems
The number of regulatory compliances continue to grow as governmental bodies expand requirements for organizations that host personal identifiable information. IGA tools that are specifically designed for your specific compliance requirements can save you a lot of extra work and worry when audits take place. IGA solutions enforce access policies aligned with these regulations so that your business can always maintain a compliant posture.
No discussion on IGA use cases would be complete about recognizing the dramatic shift to remote work. Dispersed workforces present unique challenges so your IGA tools must provide adaptive authentication for various remote access scenarios and ensure compliance and security for remote work environments.
Finally, let’s talk about the movement towards zero trust environments. Zero trust means that you can no longer rely on one-time authentication. IGA tools enable the ongoing verification of user identities and access rights so that identity is never assumed at any point. Because privileged access is the objective for any threat actor, access rights are continuously evaluated and adjusted based on changes in user roles, behavior or risk levels
Choosing the Right IGA Solution
If you’ve determined that your organization needs an IGA solution, the next step is to choose the right one that meets your needs. Start by assessing the risk levels associated with different identities, as not all identities and access requests pose the same risk. An effective IGA solution should use a risk-based approach, prioritizing critical and sensitive access points, enabling the organization to implement stricter controls and monitoring in high-risk areas, thus enhancing overall security. Other considerations should include:
- Ensure the solution can grow with your organization, accommodating increased users, devices, and data as needed.
- The solution must offer robust compliance reporting and audit capabilities to help meet industry-specific regulations.
- How many manual routine processes does your organization conduct that can be automated to simplify and reduce the reduce the administrative burden on IT teams and minimize the risk of human error.
- Look for features that empower users to handle tasks like password resets and access requests independently, improving efficiency and user experience.
- Consider the existing systems that an IGA solution must integrate with to ensure smooth interoperability.
By carefully evaluating these factors, you can choose an IGA solution that not only meets your current identity management needs but also positions your organization to adapt to future challenges and opportunities.
Some Top IGA Tools
Given the growing need to secure user identities, achieve better password management, and protect critical system platforms, there are multiple IGA solution products of choice today. Here is a brief list of some of the prominent identity and governance administration solutions available.
- IBM Security Verify Governance
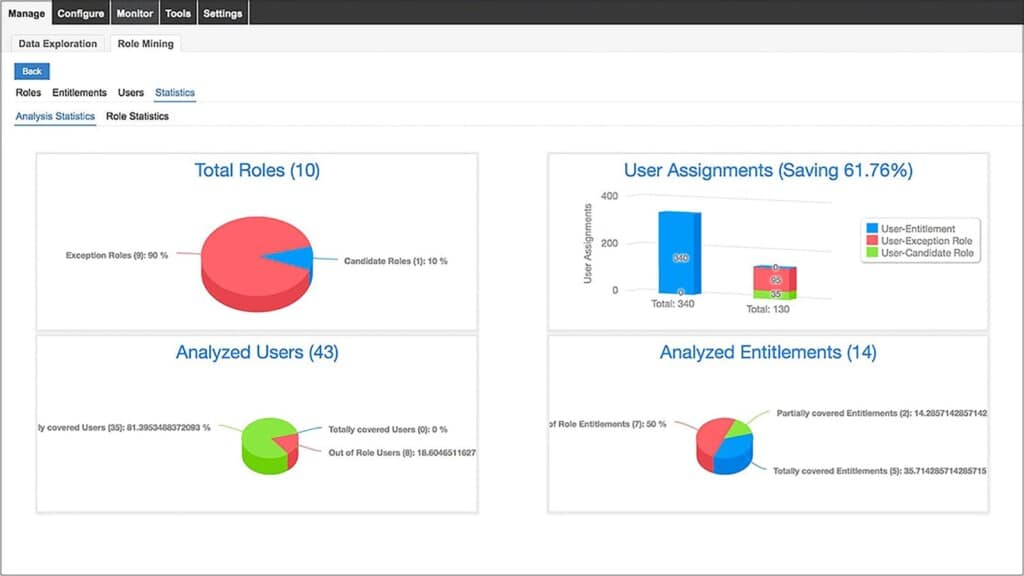
IBM Security Verify Governance is an integrated identity governance solution designed to help IT teams effectively manage identities, access, and compliance. This IBM toolset provides capabilities for provisioning, auditing, and reporting on user access and activity throughout the identity lifecycle. Admins can create business-centric rules for managing the separation of duties while streamlining the onboarding and offboarding of employees. It also includes intelligent advanced features, including identity analytics, that provide insights into risky users, insider threats, and behavior anomalies that may be indicative of an attack. By automating the labor-intensive processes that make up the typical identity lifecycle process, operational costs are significantly lowered. The screenshot below shows how admins can conduct role analysis of user roles and assignments.
- One Identity Manager
One Identity Manager is a comprehensive IGA solution that helps reduce risk and satisfies compliance by giving users the exact amount of access to data and applications required for their job roles. Their solution supports on-prem, cloud and hybrid architectures so it can integrate with a variety of IT systems, including cloud services, on-premises applications, and directory services. It supports the implementation of roles that align with business processes and offers detailed logging and reporting capabilities to support compliance efforts and audits. Like other modern solutions, it delivers insights into identity-related risks and compliance status through advanced analytics and customizable reports.
- SailPoint
If you are looking for a solution to provide identity governance into your SAP systems, then SailPoint may be a viable solution for you. SailPoint helps organizations manage digital identities, access rights and compliance across their IT environments, including SAP systems. SailPoint’s capability to integrate with SAP ERP and other SAP applications enables organizations to consolidate all resources, including SAP, into a single unified governance platform. This integration allows for comprehensive identity management and access governance across the entire SAP ecosystem streamlined fashion.
- Omada Identity
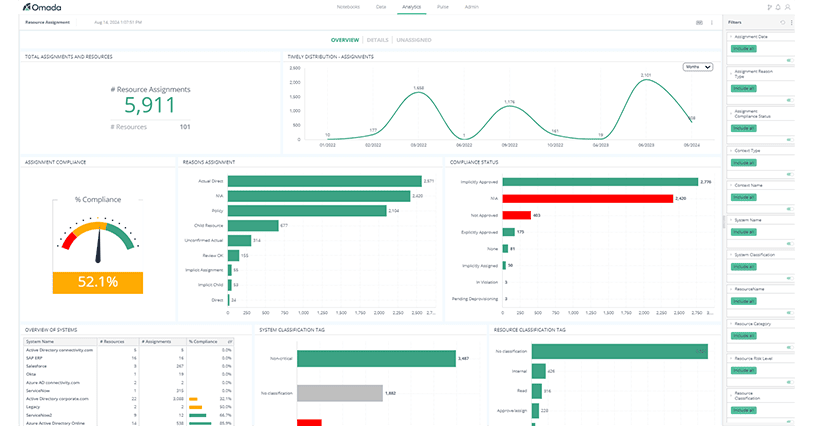
Omada Identity helps enterprises obtain a 360-degree overview of all identities and access rights across hybrid systems and applications to ensure compliance with policies and regulations. Their IGA tool solution minimizes risk by automatically identifying and deprovisioning orphan or inactive accounts, and centralizing management of all identities. As a result, the number of easy targets for threat actors to exploit is diminished. The solution also gives security teams the ability to classify systems and assets based on risk, reconcile accounts and uncover risks that used to go unnoticed. Below is a copy of the Omada admin console.
Implementation of IGA
Implementing an IGA solution is no different than other major implementations. It starts with ample assessment and planning. This includes a comprehensive assessment of your organization’s current identity management processes, policies, and infrastructure. identify gaps, risks, and compliance requirements. Include enough detail to outline the goals, timeline, and resources needed. Once the groundwork is laid, you can move forward with the next steps:
- Define roles and responsibilities for users within the organization, applying the principle of least privilege to ensure that users have access only to the data and applications necessary for their job functions.
- Research and carefully evaluate IGA vendor options to find the solution that best aligns with your organization’s needs.
- After installation, integrate the new IGA solution with your existing IT infrastructure to ensure that user data remains consistent and up-to-date across all platforms.
- Develop and implement policies for identity governance, including account creation, password management, access requests, and user activity monitoring, and use the IGA solution to enforce these policies effectively.
- Provide training for employees and IT staff on the use of the IGA solution and the importance of compliance.
- Implement continuous monitoring of user activities and access patterns to detect and respond to anomalies or potential security threats.
- Regularly review and update policies and access controls to adapt to changes in the organization and evolving security threats.
Netwrix and Identity Governance
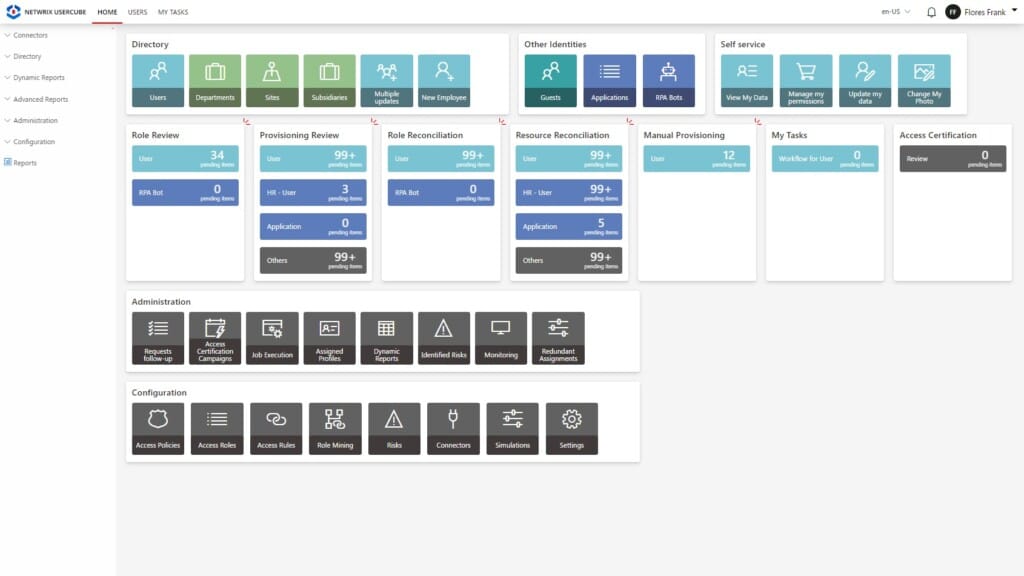
Netwrix has been recognized as a leader in the IGA space by numerous analyst firms, including Gartner. The Netwrix IGA solution is designed around a simple premise; to secure your data, you need to secure your identities. After all, it is your identities that have access to that data. That is why the primary mission of our SaaS solution is to ensure that users have the right access to the right things at the right time. Any additional access beyond that opens you up to security vulnerabilities. The Netwrix solution centralizes the management of all identities and access rights to ensure that users have the correct access in compliance with policies and regulations. It does this by building a repository of human and non-human identities from different sources to become a single source of truth for reliable information about your identity environment.
Netwrix is also heavy on automation. The Netwrix IGA solution automatically deprovisions access when it is no longer needed, thus minimizing the risk of orphan accounts that can be exploited by attackers. Users and managers alike can request access using a self-service interface that routes requests to relevant owners for approval.
This solution also provides automated attestation and easy-to-create compliance reports that can quickly be presented to auditors to prove compliance. For other reporting needs, Netwrix IGA offers an extensive set of customizable reports for transparency and auditability.
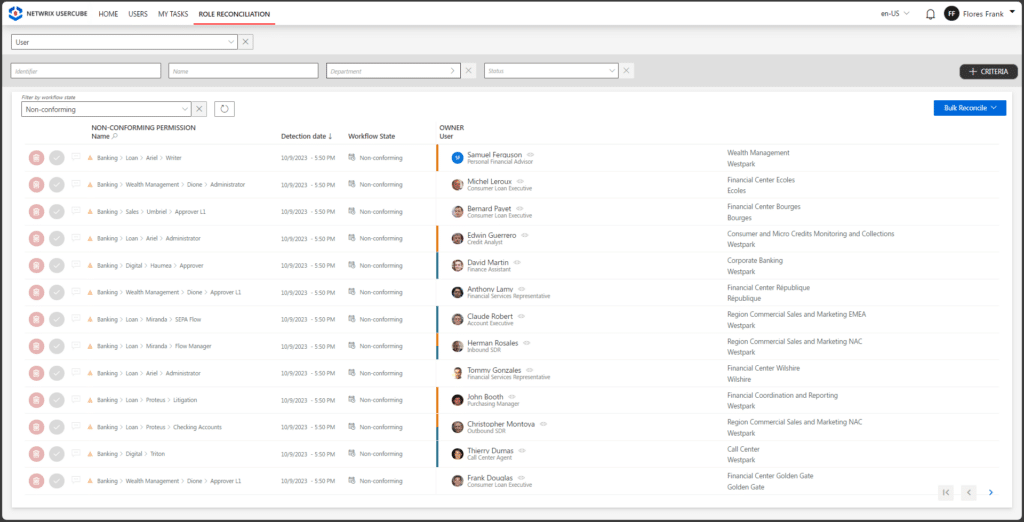
The integrated intelligence of Netrix IGA allows you to analyze existing access rights to quickly identify gaps between your expectations and reality. This capability enhances your organization’s ability to maintain compliance and security. Built-in intelligence is one of the reasons why Netwrix is considered one of the premier modern IGA solutions available today.
Future Trends in IGA Tools
Cybersecurity is a moving target, which means that IGA tools must adapt to address emerging challenges and leverage new technologies. Looking ahead, several key trends are shaping the future of IGA solutions:
- AI and Machine Learning Integration: IGA tools are increasingly incorporating advanced AI and ML capabilities to enhance their effectiveness. Predictive analytics allows for more sophisticated risk analysis and anomaly detection that was never possible in the past. This results in a more proactive and intelligent approach to identity governance.
- Enhanced Automation and Self-Service Capabilities: Self service portals are becoming more intuitive so that users can manage their own access requests, password resets and profile updates with minimal IT intervention.
- Evolution of Cloud-Based IGA Solutions: While cloud-based IGA solutions have come a long way already, advancements will continue that allow them to integrate with multi-cloud and hybrid environments.
- Increased Focus on Zero Trust Security Models: The continued shift towards zero trust security will enable organizations to enforce the principle of least privilege more effectively and adapt access rights dynamically based on changing user contexts and risk levels.
Conclusion
While it is hard to predict the future, we can say one thing for sure. Networks are going to grow more complex thanks to hybrid architectures and integrated supply chains. As organizations increasingly adopt cloud services and interconnected systems, the need for advanced IGA tool solutions is going to increase.
The threats that your business must protect against are many. There are also many reasons why you need an identity governance and administration solution as well.
- Enhanced security and trust
- Ensured compliance with government regulations
- Cost savings and operational efficiencies
- Reduced risk of data breaches and ransomware
Protecting the complex networks of today requires modern IT security, and that includes strategies around lifecycle management and identity governance. The right IGA solution improves visibility, reduces risk exposure, and scales in lock step with your organization to ensure protection and compliance. Learn more about how an effective IGA strategy can foster trust and confidence across your digital landscape.
FAQ
What is identity governance and administration?
Identity governance and administration (IGA) is a security framework that manages who has access to what data and systems across your organization. IGA tools automate user provisioning, enforce access policies, and continuously monitor permissions to ensure people have the minimum access they need to do their jobs effectively. It’s your digital security control system, constantly verifying that the right people have the right access at the right time.
Unlike traditional identity and access management, IGA goes beyond just authentication. It actively governs the entire lifecycle of user identities and their entitlements, from onboarding to role changes to departure. This proactive approach prevents insider threats and stops attackers who’ve compromised legitimate credentials from moving laterally through your systems. Data security that starts with identity – that’s the foundation of modern cybersecurity.
How does IGA differ from IAM?
IGA and IAM work together but serve different purposes in your security architecture. IAM (Identity and Access Management) handles the basics: authentication, single sign-on, and basic access controls. IGA takes it further by continuously governing those identities throughout their entire lifecycle and ensuring access remains appropriate over time.
The key difference lies in governance and oversight. While IAM asks “Can this person log in?” IGA asks “Should this person still have access to this sensitive data after their role changed six months ago?” IGA tools provide the visibility and control needed to implement least privilege at scale, automatically detecting excessive permissions and streamlining access certification processes. IAM handles the login process while IGA ensures that login leads to appropriate, well-governed access.
What does an IGA tool do?
IGA tools automate the process of managing user identities and their access rights across your entire IT environment. These tools continuously discover and catalog user accounts, analyze their permissions, and identify risky access patterns that could indicate insider threats or compromised credentials. They streamline user provisioning and deprovisioning, ensuring new employees get the right access quickly while departed employees lose access immediately.
Modern IGA solutions like those from Netwrix connect identity security to data protection by mapping user access to sensitive information. They automate access reviews, enforce segregation of duties policies, and provide detailed audit trails for compliance reporting. Instead of relying on manual spreadsheets and quarterly access reviews, IGA tools give you real-time visibility into who can access your critical data and alert you when something looks suspicious. Practical identity security that reduces both risk and administrative overhead.
What are the main challenges in IGA implementation?
The biggest challenge in IGA implementation is often organizational, not technical. Many organizations struggle with getting buy-in from business units who see access governance as an obstacle rather than an enabler. People worry about losing access they think they need, while IT teams face pressure to balance security with productivity. The key is demonstrating early wins by focusing on the most obvious excessive permissions first and showing how proper governance actually improves efficiency.
Technical integration challenges typically center around legacy systems and hybrid environments. Organizations often have identity data scattered across multiple systems – Active Directory, cloud platforms like Entra ID, and various business applications. A pragmatic approach starts with your highest-risk systems and most critical data, then expands coverage gradually. Don’t try to boil the ocean on day one. Deploy in phases, measure success, and build momentum with each milestone.
How can identity governance tools integrate with Entra ID?
Modern IGA tools integrate with Microsoft Entra ID through native APIs and connectors, extending Azure’s built-in identity capabilities with advanced governance features. While Entra ID handles authentication and basic access management, IGA tools provide the deeper visibility and automated governance needed for enterprise security. They pull user data, group memberships, and role assignments from Entra ID while adding policy enforcement and risk analysis capabilities.
The integration works by synchronizing identity data between your IGA platform and Entra ID, enabling centralized visibility across both cloud and on-premises environments. Advanced IGA solutions can trigger automated responses in Entra ID based on policy violations or risk indicators detected elsewhere in your environment. This creates a unified identity security posture where Entra ID serves as your identity provider while your IGA tool ensures those identities remain properly governed throughout their lifecycle. Connecting the dots between authentication and authorization in a way that scales with your business needs.



