In a recent download poll performed by Netwrix, an encouraging 54.3% of administrators expressed their need to reset passwords in-bulk reflecting the growing need to clear old passwords that for some may have not changed in years. This type of action indicates that password security is a concern and there is no better way to secure user accounts than to forcibly require them to be reset. This action has the potential to thwart any person having gained unauthorized access to a network and it’s systems.
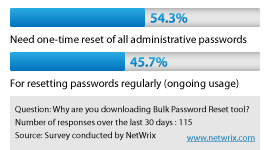
While this action may seem very dramatic, the truth is only a sweeping change like this has the potential to greatly improve security for organizations that previously had little to no password management policies. It is also used in environments that may have some policies in place however management requires a one-time or periodic bulk-reset to ensure security as a preventive measure or as part of a combined response to a security-related incident. Once completed, IT then has the ability to implement appropriate policies moving forward for password lengths, durations, and history reusability and has the confidence knowing that all systems and accounts have received a recent reset. While this is a great measure to take, what’s more important is extended password management capabilities that extend beyond the scope of local administrator accounts, but to all privileged accounts throughout the organization. Incorporation of ongoing administrative password management into an overall security plan for an organization is the best long-term approach.
Windows natively does not easily offer these kinds of features and Netwrix has the answer in the Privileged Account Manager tool. In order to address an ongoing administrator password management strategy, a tool such as the Netwrix Privileged Account Manager is the best fit. Like many of our products, it too is available in a feature-rich freeware version. The standard version of this tool delivers a number of great features to further improve security and administrative account control such as secure role-based access to all privileged accounts, fully audited check-in and check-out actions (revealing real-user names instead of “root” or “Admin”), automatic password resets at customizable intervals (such as every 90-days) with propagation to corresponding systems including updated service and scheduled task accounts.
What changes have you seen over the past 12-24 months regarding basic security improvements such as password policies and mandatory password resets? How is IT and management responding to security risks with rogue admin accounts? Have these actions created additional problems for the help desk and are they worth the trouble? Please provide your comments and feedback below:


