We continue the “Deep Dive” series. In it you might find the answers to some of your technical questions. The industry experts will provide their insights on several topics and research some new features of most popular applications. The first article of the series can be found here. Also, read more about Exchange 2013 CAS configuration (Part 1, Part 2)! You are welcome for comments and discussion!
RBAC is the new permission model in Exchange 2013. With RBAC, we don’t need to modify and manage access control lists (ACLs). It enables us to control at both broad and granular level, what administrator and end user can do. In Exchange 2013, RBAC now controls both the administrative tasks that can be performed and extent to which users can now administer their own mailbox and distribution groups.
Role group consists of the following components that define what administrators and specialist users can do:
- Management role group: The management role group is a special universal security group (USG) that contains mailboxes, users, USGs, and other role groups that are members of the role group. This is where you add and remove members, and it’s also what management roles are assigned to. The combination of all the roles on a role group defines everything that users added to a role group can manage in the Exchange organization.
- Management role: A management role is a container for a grouping of management role entries. Roles are used to define the specific tasks that can be performed by the members of a group assigned roles. A management role entry is a cmdlet, script, or special permission that enables each specified task in the role has to be performed.
- Management role assignment: A management role assignment links a role and a role group. Assigning a role to a role group grants members of the role group the ability to use the cmdlets and parameters defined in the role. Role assignments can use management scopes to control where the assignment can be used.
- Management role scope: A management role scope is the scope of influence or impact on a role assignment. When a role is assigned with a scope to a role group, the management scope targets specifically what objects that assignment is allowed to manage. The assignment, and its scope, are then given to the members of the role group, and restrict what those members can manage. A scope can consist of a list of servers or databases, organizational units (OUs), or filters on server, database or recipient objects. Let’s take a scenario, where the helpdesk team needs to provide the “Recipient Management” permission, which will be responsible to create and manage mailbox, create and manage distribution groups, move and migrate mailboxes and finally track the messages. But “Recipient Management” permission will also provide delete and disable access rights. This permission needs to be restricted for the helpdesk team. Let’s follow the below steps to customize the recipient management permission.
To start with, let’s understand the management roles under the “Recipient Management” role group using the below command
Get-Rolegroup “Recipient Management” | Select roles).roles | select name
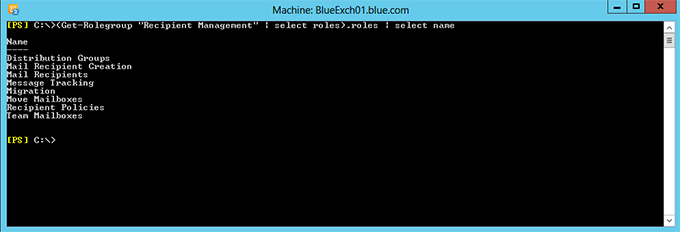
We need to pick only the required management role from the above command result and customize it to meet our requirement.
- Distribution Groups – Needs Customization.
- Mail Recipient Creation – Needs Customization.
- Mail Recipients – Needs Customization.
- Message Tracking – No Customization needed.
- Move Mailboxes – No Customization needed.
- Recipient Policies – Management role not required.
- Team mailboxes – Management role not required.
Let’s follow the below steps to create and customize the “Recipient Management” role group.
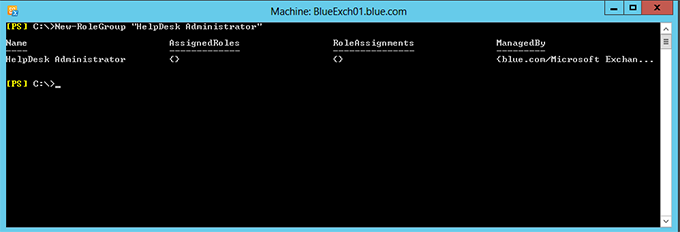
1. Create a new role group “Helpdesk Administrator” using the below PowerShell command
New-RoleGroup “HelpDesk Administrator”
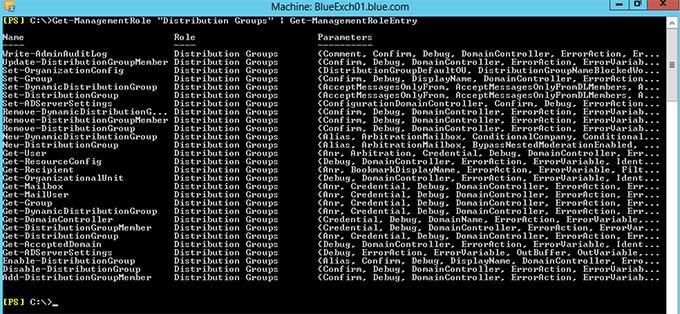
Get-ManagementRole “Distribution Groups” | Get-ManagementRoleEntry
Get-ManagementRole "Distribution Groups" | New-ManagementRole "Distribution Groups with no Remove"
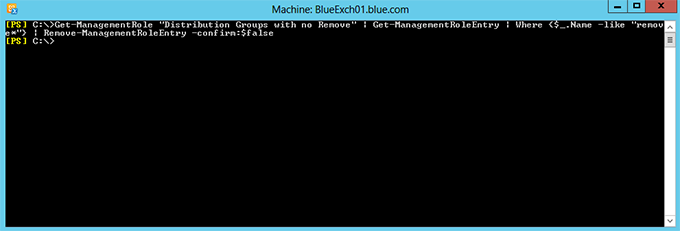
4. Then, remove all the “Remove-*” cmdlets from the management role “Distribution Groups with no Remove” using the below PowerShell command.
Get-ManagementRole "Distribution Groups with no Remove" | Get-ManagementRoleEntry | Where {$_.Name -like "remove*"} | Remove-ManagementRoleEntry -confirm:$false
New-ManagementRoleAssignment -SecurityGroup "HelpDesk Administrator" -Role "Distribution Groups with no Remove"
6. With this, we have customized the “Distribution Groups” management role. Now, we need to customize the “Mail Recipient Creation” and “Mail Recipients” management role.
7. Below are the set of PowerShell commands to customize the “Mail Recipient Creation” management role. It creates a new customized management role – “Mail Recipient Creation with no Remove” and assign it to the “HelpDesk Administrator”role group.
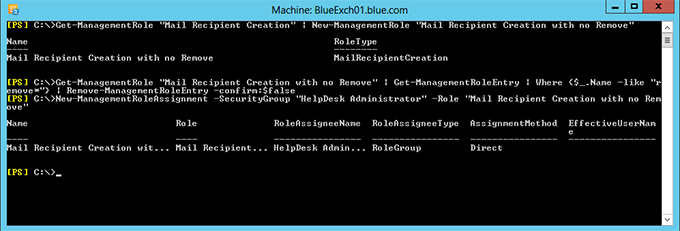
Get-ManagementRole "Mail Recipient Creation" | New-ManagementRole "Mail Recipient Creation with no Remove"
Get-ManagementRole "Mail Recipient Creation with no Remove" | Get-ManagementRoleEntry | Where {$_.Name -like "remove*"} | Remove-ManagementRoleEntry -confirm:$false
New-ManagementRoleAssignment -SecurityGroup "HelpDesk Administrator" -Role "Mail Recipient Creation with no Remove"
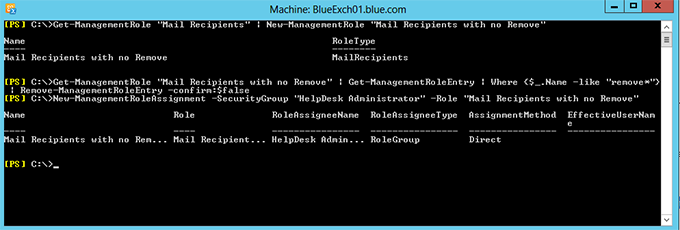
Get-ManagementRole "Mail Recipients" | New-ManagementRole "Mail Recipients with no Remove"
Get-ManagementRole "Mail Recipients with no Remove" | Get-ManagementRoleEntry | where {$_.Name -like "remove*"} | Remove-ManagementRoleEntry -confirm:$false
New-ManagementRoleAssignment -SecurityGroup "HelpDesk Administrator" -Role "Mail Recipients with no Remove"
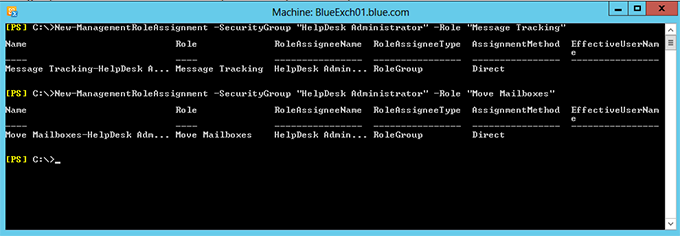
9. The “Message Tracking” and “Move Mailboxes” management role does not need any customization, as they have cmdlets which are necessary to perform the operations. The below commands assigned the default Roles “Message Tracking” and “Move Mailboxes” to the role group “HelpDesk Administrator”
New-ManagementRoleAssignment –SecurityGroup “HelpDesk Administrator” –Role “Message Tracking” New-ManagementRoleAssignment –SecurityGroup “HelpDesk Administrator” –Role “Move Mailboxes”
Get-RoleGroup “HelpDesk Administrator” | Add-RoleGroupMember –Member Krishna.kumar
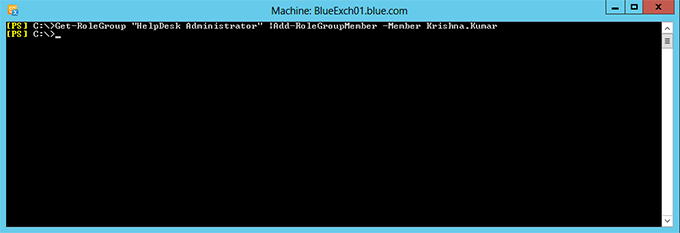
Finally, we have the fully customized role group “HelpDesk Administrator”. Members of the “HelpDesk Administrator” group member will have permission to create and modify mailbox, distribution group etc. but, not the remove permission. Hope you got some good understanding of customizing RBAC permission using PowerShell.


