Picture this. You work at a company that prides itself on it’s security practices. They’ve got firewalls, IDS/IPS systems, routinely perform security audits, keep patches up to date and have a really expensive SIEM product that generates alerts the moment something fishy goes on. A very important employee with highly sensitive data on his PC is going about his daily business. We’ll call him George. George decides to go out for lunch but forgets to lock his PC. This is bad practice all by itself but it’s even worse since George’s PC can be accessed by the public if no one is around. About 50 minutes into George’s lunch a nefarious individual (we’ll call him Pete) catches a glimpse of George’s PC just sitting at the desktop screen and decides to take a chance.
Knowing that George might come back at any time, Pete needs to get to George’s PC fast and leave as quick as he can. While on his PC, Pete does a quiet happy dance inside his head when he finds that George’s domain account is a local administrator. Pete now has full control over this computer. Since Pete doesn’t know George’s password, he decides to simply create another local user account and place it in the administrators group and grab the PC name. Pete quickly leaves and sees George coming back. Pete knows he owns that PC now.
Happy to poke around and see what he can do, Pete immediately heads out to his car, grabs his laptop and heads into the lobby. It just so happens there’s a free network drop right beside a chair. “This company is so inviting”, Pete thinks. He plugs in, tries to access George’s PC, gets prompted for credentials and he’s in.
Has a similar scenario happened in your company? Do you even know it has or will happen? There were a lot of security nonos that went on here but one was not monitoring the local administrators group. If this company was routinely monitoring that group, they could have known that an unknown account was added and now had full control, but they didn’t and George’s PC was compromised. How does this company prevent this in the future? One way is through a simple, free Windows PowerShell script.
Windows PowerShell is a very powerful scripting language and has many uses. One of those uses is enumerating local user accounts on local or remote computers as well as built-in email functionality. Using PowerShell, we can build a script that queries George’s (and other) computers on a routine basis for changes in the local administrators group and will receive automatic emails if a new member is added. Let’s see how to do this. But first, here’s a demonstration of what’s possible with this script.
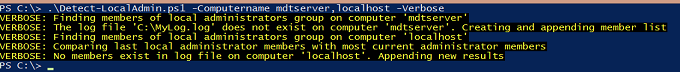
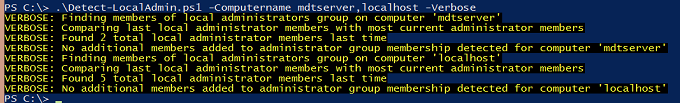
When this is ran for the first time against a few computers, it will create the log file which keeps track of the member lists. You can see in this example that this was the very first run, so no changes could be found.
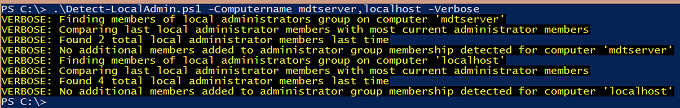
I run it the second time and, although the log file had been created, there was no change in group memberships for either computer.
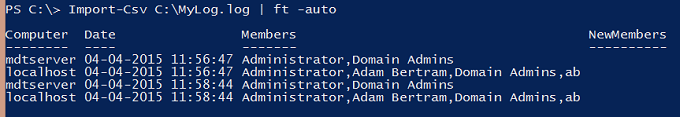
This script is generating a CSV file with the following contents. Notice the MDTSERVER computer has two members inside the local administrators group while the localhost has 4 different members.
Now, let’s add a member to the group on the localhost.
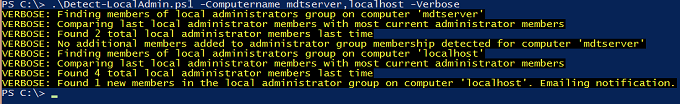
I can see on the last line that a new member was found on the localhost since the last time it ran and I have now received an email notifying of this. The CSV file also has recorded this activity.
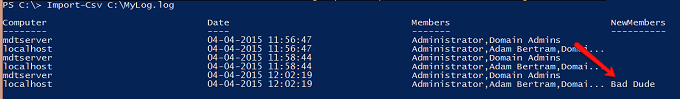
We now run the script again and it sees 5 total members but will not email notification. It only emails notifications on changes but could easily be changed to notify on any number of different criteria.
This script was just an example of what’s possible with PowerShell for auditing purposes. Use it as a template if it doesn’t fit your needs and customize it as you wish. PowerShell is a great tool to begin rudimentary or ad-hoc auditing services but I would not recommend it for building a large, enterprise-scale auditing solution. A comprehensive auditing solution should fit the bill there, and you can always use PowerShell as a complement.



