Windows servers can potentially generate thousands—or even hundreds of thousands—of events daily. Most are created from perfectly safe events that system administrators use to get a glimpse of what’s going on. An event might be generated to indicate a disk is running out of free space, an error occurred with Active Directory, or perhaps a piece of software was installed by a system administrator. There’s nothing to worry about here. However, hidden behind these thousands of normal events may lie an indicator that there could have been a hacker attack. How is an administrator supposed to find this needle in a haystack?
Define What to Look for
Before an admin can get started installing software or cracking open a script editor, he has to perform some background research. The first task is to define what to look for. Windows generates thousands of different events. The admin needs to figure out which of these events may potentially indicate a security threat.
To do that, he’ll first need to reference some popular indicators of security problems: security privileges being escalated, a user account being placed into an important group, or the security log being cleared are some popular nefarious activities of the bad guys. There are a lot of resources out there that give you this information.
Discover How the Data Is Represented
After the admin has decided what actions he’s looking for, his next step is to discover how these actions manifest themselves on a Windows server. There are many ways a security threat may show itself, but the method we’re talking about today is through Windows event logs. It becomes a priority to figure out which event IDs correlate to these potential security threats. A great one I’ve used is the Ultimate Windows Security guide. It contains most of the security-related events that are generated on a Windows server along with their event IDs.
Search for the Data
Now we’ve got something to work with. We’ve got the actions we need to look out for, how these actions are being manifested, and the event IDs that represent these actions. It’s time to perform queries on the server to search for these events. This is where the Windows PowerShell language comes in handy. PowerShell provides a few convenient, yet robust ways to query event logs on a Windows server. By using PowerShell to query event logs, it becomes a snap to spread your queries across multiple servers as well. Let’s look at an example of how to make this happen.
Windows has many different event logs to record many different types of activity. The one we’ll be focusing on here is the security log. The security log is the place where all the security events are recorded (believe it or not). But, the method we’re about to use will work equally well across other event logs as well.
Let’s say that an administrator has discovered three different activities:
- The security log is full – Event ID 1104
- The audit log was cleared – Event ID 1102
- A member was added to a security-enabled global group – Event ID 4728
Where to start? The first step is using a PowerShell cmdlet called Get-WinEvent. Get-WinEvent is the more advanced version of Get-EventLog, if you’ve heard of that one. Get-WinEvent, although more complicated to use, is more powerful and performs much faster than Get-EventLog. Let’s go over an example of using Get-WinEvent to find a single event ID on a single server.
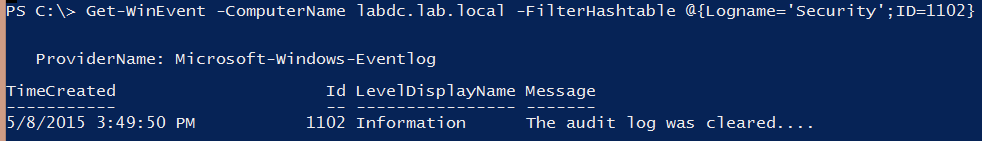
In this example, you can see I’m querying the server name labdc.lab.local. I’m using a FilterHashtable parameter to narrow down the events only to the security event log and to the specific ID I’m looking for, which is 1102 in this instance.
Pretty simple, right? What if I want to find multiple event IDs, like I referred to earlier? No problem!
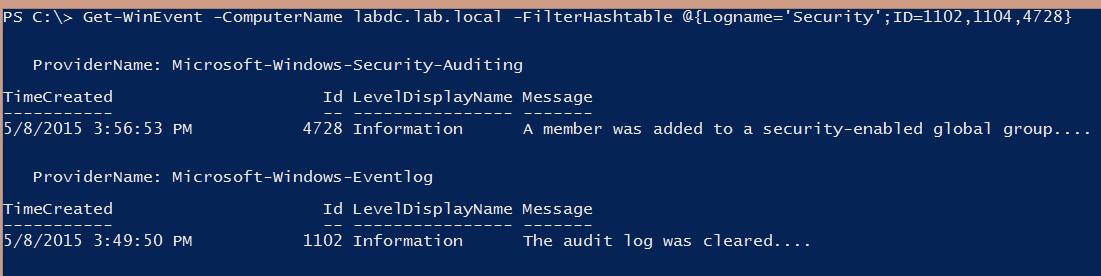
You can see in the example that I’m still querying the same server, but this time I’m looking for three different event IDs, and I was able to find an instance of event IDs 4728 and 1102.
This was just a single server. You probably have more than one server. So let’s expand its reach and query a list of servers.
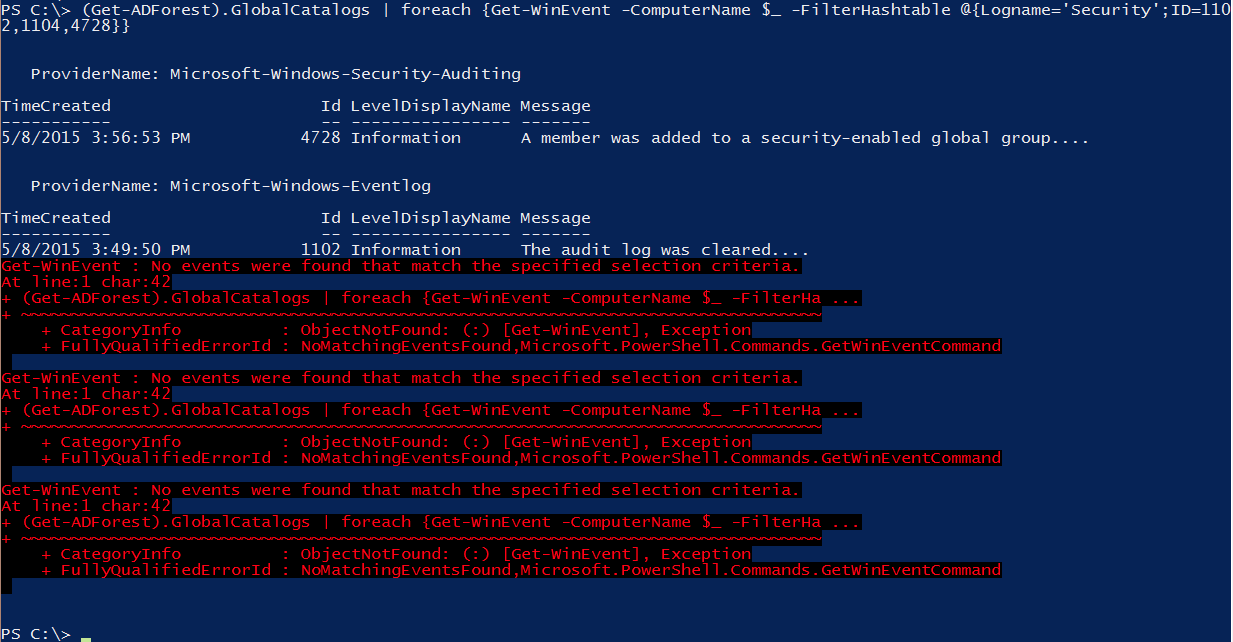
It was as simple as adding a foreach loop. As you can see from the example, I was able to find event IDs 4728 and 1102 on one of the Active Directory global catalog servers. No events were found on the other three servers.
This is just a sample of the kind of event log auditing you can perform with PowerShell. PowerShell is great for quick fixes and ad hoc auditing. If you need a more robust auditing solution, I’d recommend a tool like Netwrix Auditor. Netwrix Auditor was built from the ground up with auditing in mind, and it just works. If you’re not well-versed in PowerShell, don’t worry about it. Netwrix has already built the smarts into their Auditor product. No need to burden yourself with scripting.



