Most organizations with more than 10 or 20 people on staff that are running either Exchange Server on premises or Office 365 in the cloud have mailboxes that are shared on some level. These scenarios could include the following:
- An executive or manager that generally handles his own tasks but offers delegated access to his contacts, calendars, or emails to an administrative or executive assistant so that he or she can have access to the items in the manager’s inbox.
- A shared mailbox for a department such as “Customer Service” or “Accounting” for which all of the employees in that department share access to the mailbox to receive incoming mail, respond to it on behalf of the department (without using their own accounts), and manage its electronic affairs.
There could arise certain situations in which you would quickly need a list of mailboxes that allows people other than the mailbox’s owners to access the data within them. A best practice would be to audit this type of access on a consistent basis, whether that is quarterly, semi-annually or even monthly for very sensitive installation. A further best practice would be to log each time this type of permission is granted through your own security department; however, in the real world, this manual method of tracking before granting will not capture users who delegate access on their own through something as simple as right-clicking on their calendars in Outlook and electing to share the calendar with a fellow colleague. That is more difficult to capture in an automated way.
Using PowerShell script
Let’s tackle the simplest scenario first. To have a look at which mailboxes are shared with other users, you can use the power of PowerShell to capture these shared-out mailboxes so you know what you are working with.
Get-Mailbox –RecipientTypeDetails ‘SharedMailbox’ | Get-MailboxPermission | where {$_.user.tostring() -ne "NT AUTHORITYSELF" -and $_.IsInherited -eq $false} | Format-Table Identity, User –AutoSize
This command will provide a simple table showing the identity and users with access to shared mailboxes. This is a good place to start.
To look further into who has access to data in a mailbox, you will need to start interacting with Exchange Web Services, which has an API that can expose much more information than the PowerShell modules for Exchange currently do. Luckily, Microsoft Exchange Server MVP Glen Scales has posted a sample script on his blog that we can use to inquire about which users have access to specific folders within a user’s mailbox. Glen suggests on his blog that this report, which comes out as decent-looking HTML, can be emailed to users for a quick glancing over and verification, something along the lines of “Yes, I know these people and I know they have a valid reason for having access to my mailbox.”
$rptCollection = @()
$delegates = $service.getdelegates($MailboxName,$true)
foreach($Delegate in $delegates.DelegateUserResponses){
$rptObj = "" | select EmailAddress,Inbox,Calendar,Contacts,Tasks,Notes,Journal,MeetingMessages,ViewPrivateItems
$rptObj.EmailAddress = $Delegate.DelegateUser.UserId.PrimarySmtpAddress
$rptObj.Inbox = $Delegate.DelegateUser.Permissions.InboxFolderPermissionLevel
$rptObj.Calendar = $Delegate.DelegateUser.Permissions.CalendarFolderPermissionLevel
$rptObj.Contacts = $Delegate.DelegateUser.Permissions.ContactsFolderPermissionLevel
$rptObj.Tasks = $Delegate.DelegateUser.Permissions.TasksFolderPermissionLevel
$rptObj.Notes = $Delegate.DelegateUser.Permissions.NotesFolderPermissionLevel
$rptObj.Journal = $Delegate.DelegateUser.Permissions.JournalFolderPermissionLevel $rptObj.ViewPrivateItems = $Delegate.DelegateUser.ViewPrivateItems
$rptObj.MeetingMessages = $Delegate.DelegateUser.ReceiveCopiesOfMeetingMessages
$rptCollection += $rptObj
}
$tableStyle = @"
<style>
BODY{background-color:white;}
TABLE{border-width: 1px;
border-style: solid;
border-color: black;
border-collapse: collapse;
}
TH{border-width: 1px;
padding: 10px;
border-style: solid;
border-color: black;
background-color:#66CCCC
}
TD{border-width: 1px;
padding: 2px;
border-style: solid;
border-color: black;
background-color:white
}
</style>
"@
$body = @" <p style="font-size:25px;family:calibri;color:#ff9100"> $TableHeader </p> "@
$rptCollection | ConvertTo-HTML -head $tableStyle | Out-File c:delgateReport.html
Deploying a professional tool
Instead of using PowerShell scripts, you can deploy a professional tool. In the following screenshot (in this case, it’s Netwrix Auditor for Exchange), we see a change made to mailbox permissions and delegation:
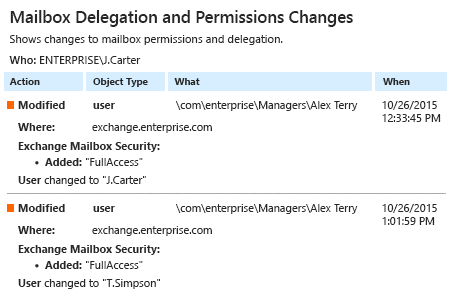
With this tool you can see who accessed what mailbox, when and from which workstation the access occurred, and what items the user viewed, edited or deleted.
This also helps demonstrate to auditors that you’re taking action to protect your network mailboxes against unauthorized access.



