As expected, the 27th RSA Conference in April 2018 was one of the major IT security events of the year. 650 exhibitors and 45,000 security professionals came together in San Francisco’s Moscone Center to elaborate on the state of the art and the future of cyber security. Over 500 sessions encompassed a variety of issues, from cryptomining and RaaS to hot topics in cyber law.
This year, RSA truly became a forum for CISOs, who are on the front line fighting against ever-increasing cyber threats. Panelists discussed the problems CISOs face in their daily jobs. The red thread of the sessions was recognition that the state of IT security is not all unicorns and rainbows. Attackers and threats have become more sophisticated, but there is still a lack of solutions to withstand them effectively, and the level of security awareness at the board level leaves much to be desired.
Here are five recommendations that CISOs can take advantage of to get maximum return on their cyber security efforts.
1: Know everything about your assets
You cannot secure and manage what you cannot see or do not know about. Therefore, visibility into all of your company’s IT assets and data is paramount for mitigating the risk of data breaches, speeding incident response and ensuring compliance with stringent regulations, such as the GDPR. However, there is no one-size-fits-all solution yet.
In a session titled “Recon for the defender: You know nothing (about your assets),” Ed Bellis and Jonathan Kran from Kenna Security highlighted lack of visibility as one of the reasons why companies still know too little about their assets. The company researched existing solutions for asset discovery and observed that they provide a quite fragmented level of visibility. Test subjects spent 15 hours a week or more with 15 different tools, but at best managed to discover only 60-70% of the assets in the test.
Therefore, Bellis and Kran advise CISOs to augment their current asset management tools with recon techniques typically used by hackers to discover subdomains, resources and properties a company is using.
However, the ultimate solution might be somewhere in between using automated tools and hiring a dedicated full-time person.
Related resources:
- How to collect server inventory
- How to find shared folders
- How to get a list of computer accounts
- Data classification explained
- Five reasons to ditch manual data classification
- How to identify, classify and secure sensitive content with Netwrix Auditor
2: Learn how to secure the cloud
As more organizations move to cloud and hybrid environments, cloud security is more pressing than ever. Infosecurity teams are particularly concerned that a shortage of best practices and efficient tools for cloud security coupled with a lack of visibility dramatically increases the risk of data breaches.
During the session, “Confessions of a cloud security convert,” Michael Farnum from Set Solutions talked about how to deploy an efficient cyber-security strategy for the cloud. He advised combining well-known security practices — network penetration testing, dynamic application security testing, automated patch management and vulnerability assessment — with relatively new ones, such UEBA and SIEM solutions for cloud services, and cloud access security brokers (CASB). A holistic approach is the key to success.
Rich Mogull from DisruptOPS and Bill Burns from Informatica, in their presentation on how to build and adopt a cloud-native security program, advised organizations not to ignore the security threat services already offered by cloud providers. For instance, their event-based alerts can see things their customers cannot, such as failed API calls.
Also, Janet Matsuda and Tim Prendergast from Palo Alto Networks hosted a session titled “Is cloud native security good enough?” in which they underlined that bringing key stakeholders — the CISO, infosec team, the application team — together into one agile team will greatly contribute to developing a sound cloud security strategy.
Related resources:
- [Free Download] Cloud Security Best Practices
- Recorded webcast: Tracking changes in Hybrid Identity environments
- How to gain visibility into what’s happening in AWS
- How to stay on top of user activity in Microsoft Office 365 with Netwrix Auditor
3: Accept identity as a new perimeter
The identity side of security was another hotly debated topic at RSA. In a cloud-enabled world, the concept of network perimeter fades away and the new “identity” perimeter rises to take its place.
As an example, during the CSA panel discussion “Surviving the Identity Apocalypse” moderated by Phil Dunkelberger from Nok Nok Labs, panelists discussed how compromised cloud credentials can cost companies a fortune, and how infosec teams can handle these risks effectively. Panelists highlighted that IAM solutions are problematic to work with on premises, so they are likely to fail in the cloud too. Therefore, Bill Mann from Centrify encouraged the audience to work on establishing coherent strategies and processes for IAM in the cloud before investing in a solution.
Related resources:
- How to monitor user logons in a domain
- How to view Azure AD sign in activity
- Free tool: Find and disable stale Active Directory accounts
- Injecting visibility into your IAM program for greater confidence
- SysAdmin Magazine: Keep a Close Eye on Permissions
4: Understand how to present to the board of directors
Discussions about the relationship between security teams and their boards of directors centered on money. Even though the number of breaches keeps growing, CISOs still struggle to get their security budgets increased. Scaremongering about the costs of data breaches does not really convince the C-suite. RSA panelists advise them to speak with business leaders in their language — the language of business benefits and financial risks.
Rick Howard from Palo Alto Networks, and Richard Seiersen from Lending Club, in their session “Superforecasting: even you can perform high-precision risk assessments,” suggested providing the board with graphics depicting three loss exceedance curves (see Figure 1):
- Inherent Risk Curve: How much money will the company lose in the event of a breach if it does not invest more money in security? (X) What is the likelihood of a breach if it does not invest more money in security? (Y)
- Risk Tolerance Curve: What risks are acceptable from the standpoints of money loss (X) and breach probability (Y)?
- Residual Risk Curve: How much money will the company lose in the event of a breach if it invests more money in security? (X) What is the likelihood of a breach if it invests more money in security? (Y)
Importantly, CISOs should calculate the cost of the risk reduction measures and be able to explain exactly how the security team will spend it. To articulate a clear plan, they need an accurate risk assessment solution, Howard and Seiersen said.
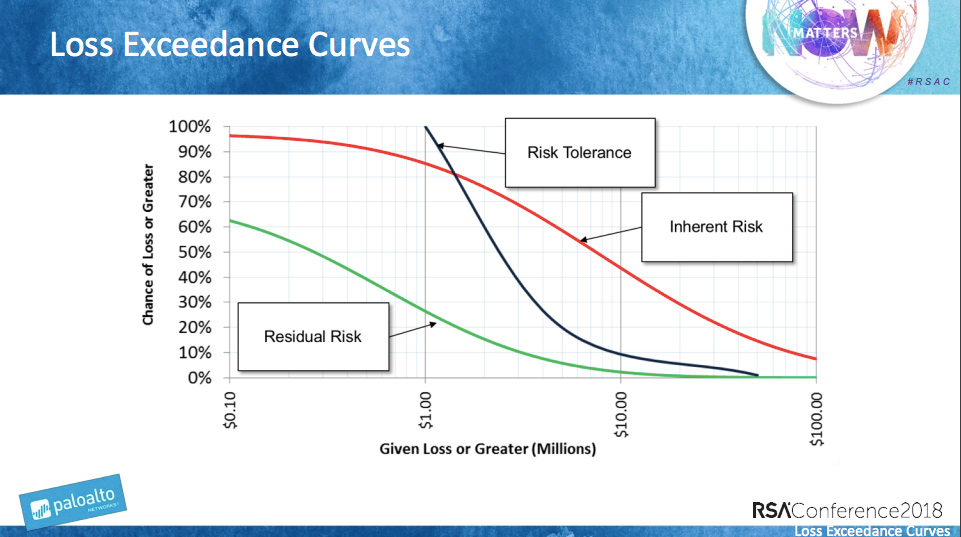
Figure 1. Rick Howard, Richard Seiersen. Loss Exceedance Curves. Superforecasting: even you can perform high-precision risk assessments.
Related resources:
- Five things to know about IT risk assessment
- Seven myths about IT risk assessment busted
- How to perform IT risk assessment
- How to identify, assess and reduce IT risks with Netwrix Auditor
But convincing the C-suite requires more than talking about breaches that might happen. It also requires discussing the business benefits that an improved security posture and refined IT processes can bring to the company. CISOs should think strategically and understand how business can leverage technology. Frank Kim from ThinkSec, in his session “10 tenets of CISO success,” provided a mapping with possible arguments for investing in cyber-security technology and training (see Figure 2).
Internal business processes will become more efficient, so cycle times will be lower and business will gain more space for innovation. In turn, customers and stakeholders will be more satisfied with the services, and the company will also improve its compliance. Finally, stewardship will reduce costs and increase revenue and profitability.
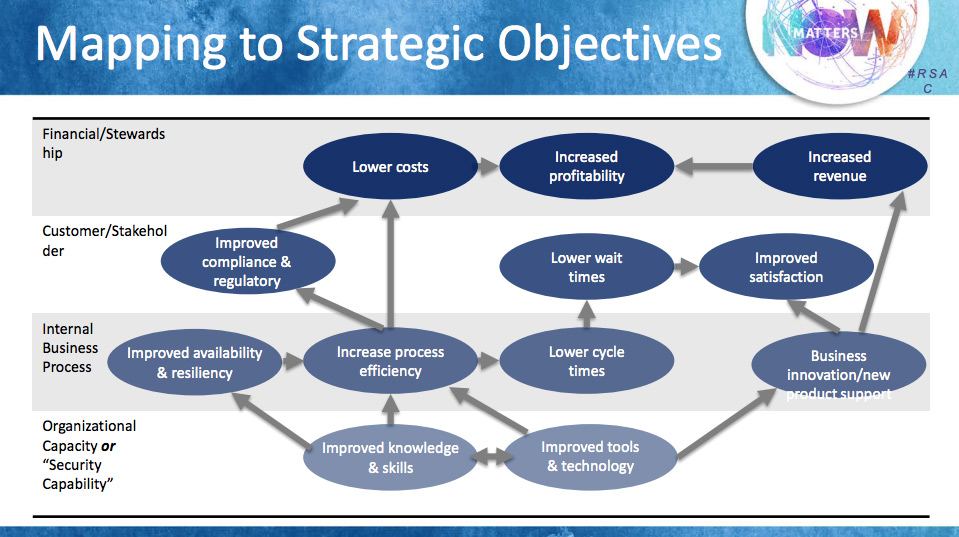
Figure 2. Frank Kim. Mapping to Strategic Objectives. 10 tenets of CISO success.
5: Use compliance as a lever
RSA was held just one month before the GDPR comes into force, so sessions dedicated to this standard were in abundance.
The true leitmotif of these sessions was the following: Make sure you understand all GDPR provisions, brush up your compliance processes to be ready before auditors take an interest and … enjoy! Exactly — panelists advised the audience to make friends with compliance standards, including the GDPR, because following their guidelines can dramatically improve security and operations. “Compliance is not your enemy — use it as a lever,” Monzy Merza from Splunk said during his session, “Going beyond defense: how security becomes a business enabler,” when he was advocating for not being so shortsighted that you treat compliance as no more than a checkbox.
Rashmi Knowles, Field CTO at EMEA RSA, during his presentation “Get up to speed on GDPR fast,” also highlighted the benefits the GDPR will bring to businesses, such as improved data strategies, better privacy policy management, and KPIs for data security and privacy.
To make friends with compliance, CISOs should also make friends with the compliance department, if there is one, and work side by side. Compliance requires teamwork, so IT security teams cannot afford to stay siloed anymore.
Related resources:
- Compliance demystified
- Recorded webcast: How to stop suffering and start benefiting
- SysAdmin Magazine: Why GDPR Won’t Kill You
- How to ensure compliance with regulatory standards using Netwrix Auditor
In conclusion
To survive in 2018, CISOs should know their business and assets, understand how to assess risks accurately, learn to think in dollars and business benefits, and accept that there is no single technology solution to address all threats.
They should also recognize that there is no 100% security. Hugh Thompson, Program Committee Chair of RSA, compared IT security to a car alarm — it does not guarantee that carjackers won’t steal your car, but it makes your neighbor’s alarmless car a more attractive target.
Let’s be the least attractive!