Group Policy is a configuration management technology that is part of Windows Server Active Directory. It can be used to configure settings in Windows client and server operating systems to make sure you have a consistent and secure setup across devices. There are literally hundreds of settings available to use as you configure your Group Policy objects (GPOs), but in this blog post, I’ll show you six critical Group Policy security settings that you need to get right to ensure basic security in your environment.
If you want to configure Group Policy to Microsoft’s recommended settings, download the Security Compliance Toolkit. It contains security baselines for all supported versions of Windows, which you can use as the basis for your own Group Policy objects, and spreadsheets that list and explain all the recommended settings. If you have devices that are not members of a domain, use local policy to configure settings. The toolkit contains a specific application that makes it easier to manage local policy settings on standalone devices.
Application Control (AppLocker)
Failure to keep unauthorized software off your machines is one of the key ways malware takes hold of systems. While it is important to remove local administrator privileges from end users to prevent system-wide changes, that restriction alone is not enough to prevent users (or processes running in the context of logged-in user accounts) from running code that could do serious damage.
To address this, Microsoft Windows 7 introduced AppLocker, which enables system administrators to quickly apply application control policies to systems. AppLocker works by establishing a whitelist of processes, scripts and installers that can run. You’ll find AppLocker settings in Group Policy under Computer Configuration > Windows Settings > Security Settings > Application Control Policies > AppLocker.
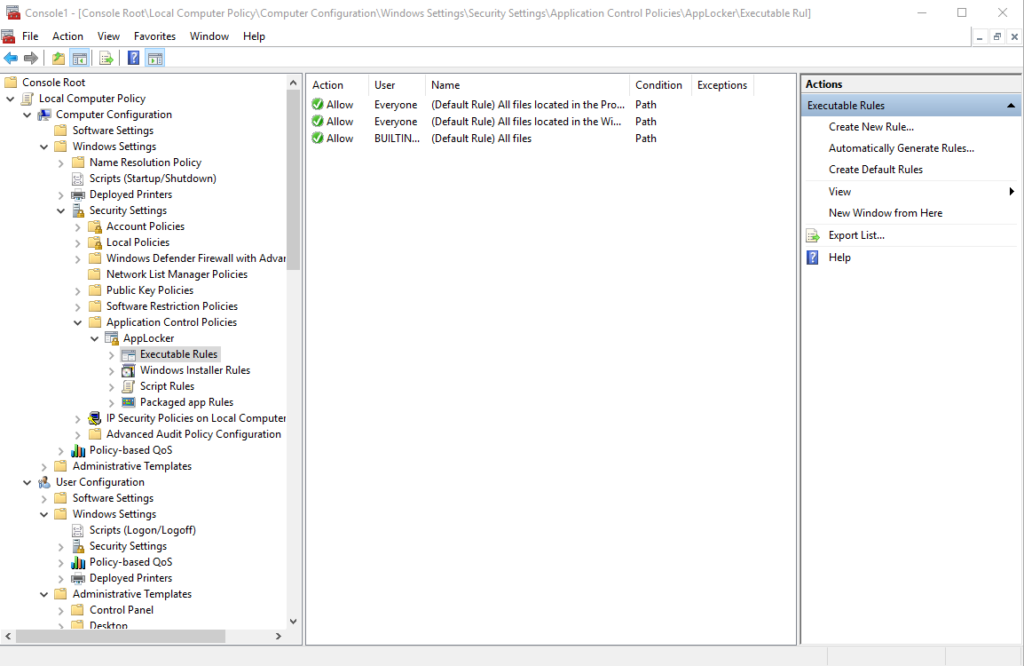
Figure 1. Where to find AppLocker settings in Group Policy
To create rules for each category listed under AppLocker, right-click the category (for example, Executable rules) and select one of the three options in the top half of the menu. Selecting Automatically Generate Rules… scans a reference system and creates rules based on the executables installed in trusted locations. If you decide to create rules manually, make sure that you Create Default Rules; otherwise you risk disabling critical functionality in Windows that could render systems unusable.
Once you’ve set up some rules, right-click AppLocker and select Properties from the menu. On the Enforcement tab, click the rule categories you want to enable and select Audit only from the menu. Let your rules run in audit mode for some time and check the Windows Event log for any issues. If you are sure the rules don’t block any important apps or Windows features, change the setting to Enforce rules.
The Application Identity service must be running on devices before AppLocker will enforce policies. In Windows 10, AppLocker can also be configured through the Local Group Policy editor. However, with Windows 10, Microsoft introduced Windows Defender Application Control (previously Device Guard), which is a more robust application control technology that is difficult for local administrators to circumvent.
Windows Update
Windows Update is a critical component of Windows that makes sure the operating system and other software stays up to date. If your organization is using Windows 10, think about using Windows Update for Business (WUfB) to keep devices patched. Unlike Windows Server Update Services (WSUS), WUfB doesn’t require any on-premise infrastructure but does give you some control over how Windows 10 feature and quality updates are applied. You can find Windows Update and Windows Update for
Business Group Policy settings under Computer Configuration > Administrative Templates > Windows Components > Windows Update.
If you are using an earlier version of Windows, use Group Policy to point devices at an internal WSUS or System Center Configuration Manager Software Update Point (SUP) using the Configure Automatic Updates and Specify intranet Microsoft update service location settings. There are lots of other settings too, like Do not include drivers with Windows Updates and Specify active hours range for auto-restarts, that might be useful.
Disable SMBv1 Client and Server
Some components of SMBv1 lack proper security. If you remember back to 2017, flaws in SMBv1 were one of the ways that the NotPetya virus was able to spread so quickly. Although Microsoft had already issued patches for SMBv1, many organizations had not applied them.
Later versions of Windows 10 already have the insecure SMBv1 components removed by default. But if you are using Windows 7, Windows 8 or an earlier version of Windows 10, you will need to make sure to either remove the SMBv1 component from your system or use Group Policy to disable it on all servers and clients that don’t need it.
To disable the SMBv1 server, create a REG_DWORD value called SMB1 under the following key path and set its value to 0:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters
To disable the SMBv1 client, create two registry values. The first is a REG_DWORD value called Start, which should be set to 4 under the following key path:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservicesmrxsmb10
The second is REG_MULTI_SZ value called DependOnService, which should be set to “Bowser”,”MRxSmb20?,”NSI” under the following path:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanWorkstation
To configure new registry items in Group Policy, go to Computer Configuration > Preferences > Windows Settings and right-click Registry. Select New > Registry Item from the menu and then add the required key path and value. Make sure that the Action field is set to Update.
Disable Guest Account and Local Administrator Accounts
The built-in guest and local administrator accounts are disabled by default in Windows 10. But if you want to make sure it stays that way, set the accounts in Group Policy to be always disabled. This is especially important to ensure strong access control on critical servers, such as domain controllers. You can find the settings under Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options. Set both Accounts: Guest account status and Accounts: Administrator account status to Disabled.
Deny Execute Access on Removable Disks
You can allow users to read and write to and from removable media but block them from running any executables. If you have AppLocker set up, this setting might be moot, but many organizations don’t use application control. In any case, blocking executables on removable media can help protect systems from malicious code.
You’ll find the Removable Disks: Deny execute access setting under Computer Configuration > Administrative Templates > System > Removable Storage Access.
Prevent Changes to Proxy Settings
Regardless of whether your organization uses a proxy server, it’s wise to prevent users from changing proxy settings. At worst, malicious proxy settings could divert all internet traffic in your network through an unauthorized middleman; at best, they could stop users from accessing internet resources. To stop users from changing proxy settings for Internet Explorer and Microsoft Edge, set Prevent changing proxy settings under User Configuration> Administrative Templates > Windows Components > Internet Explorer to Enabled.
Conclusion
Those are the six Group Policy settings you need to be certain to configure properly. Remember, before you apply Group Policy settings in your production environment, test them to be sure that they won’t have any adverse effects. For a full list of Microsoft’s recommended settings, download the baseline templates in the Security Compliance Toolkit.



