In today’s assume-breach era, constantly chasing the latest threat isn’t a viable strategy for data protection. Data threats will continue to grow in frequency and scale. Last year, 60% of companies experienced a ransomware attack, and analysts predict that this threat vector will continue grow because it is a quick path to monetization. Even the coronavirus pandemic is an additional avenue for hackers to attack your data; for example, a ransomware attack kept one health organization unable to inform the public about COVID-19. Clearly, data protection today is a business problem, not merely an IT problem.
To minimize security risks and satisfy compliance requirements, including breach notification rules, it is crucial to focus on data security rather than on perimeter security. In this article, we will explore the factors driving a shift to data-centric security.

Source: 2020 Netwrix IT Trends Report
The cloud erases the perimeter
The cloud has effectively killed traditional perimeter security. Experts predicted that by 2020, 83% of enterprise workloads will be in the cloud. At the same time, cloud adoption has caused data to continue to grow at unprecedented rates, spiraling out of the control of security teams.

Sources:
3. Cloud Computing Market Size, Growth Rate & Forecast (2019 – 2025), Research Cosmos
4. 2020 Technology Trends, ESG
5. Cloud Strategy Leaderhip, Gartner
6. 2019 Cloud Security Report, (ISC)2
7. Cloud Vision 2020: The Future of the Cloud Study, Logic Monitor
Although cloud providers offer advanced security measures, customers are ultimately responsible for securing their own data in the cloud. According to the 2019 Cloud Security Report (ISC)2, the majority of companies see data loss/leakage as their top security concern.
However, the Netwrix 2020 Data Risk and Security Report shows that companies are exposing themselves to two types of security risks. First are the risks coming from unauthorized data sharing: 54% of organizations are confident that their employees are not sharing data using any means of communication unknown to the IT team, but most of them can’t prove it, since 29% of them don’t track employee data sharing at all.
Second are the risks coming from remote workers. Although making data available for remote access is among the primary drivers for cloud migration, a study by OpenVPN reports that 90% of IT pros believe that remote workers are not secure. While over 70% think remote staff poses a greater risk than on-site employees, as shown in the Netwrix 2020 Data Risk and Security Report, 38% of organizations that employ remote workers have suffered cloud data security breaches.

Sources:
2. Netwrix 2020 Data Risk and Security Report
8. Remote Workforce Cybersecurity Survey, OpenVPN
Data is the target of security breaches
In 2020, we all know that every organization, regardless of market sector or business size, must secure its data to minimize data leakage and other security incidents. It was hard not to notice this necessity; the number of data breaches has increased by 67% over the last five years, as reported in a study by Accenture and the Ponemon Institute.
Even the increasing number of strict regulations that require organizations to manage and protect sensitive data, like HIPAA, CCPA and PCI DSS, won’t stop data breaches. Statistics show that, as of January 2020, at least 7.9 billion records, including credit card numbers, home addresses, phone numbers and other sensitive information, have been exposed through data breaches since 2019. The Netwrix 2020 Data Risk and Security Report finds that organizations still have numerous areas in which they can improve their data protection. For example, ensuring the secure storage of sensitive data was one of the most challenging tasks for regulated entities: Although 91% of organizations claim they store sensitive and regulated data only in secure locations, 24% of them admitted they had discovered such data outside of designated locations in the past year. Moreover, even though modern privacy regulations require companies to track the footprint of the personal data they collect, 33% of organizations subject to the GDPR and 25% of those subject to the CCPA do not track data sharing at all.
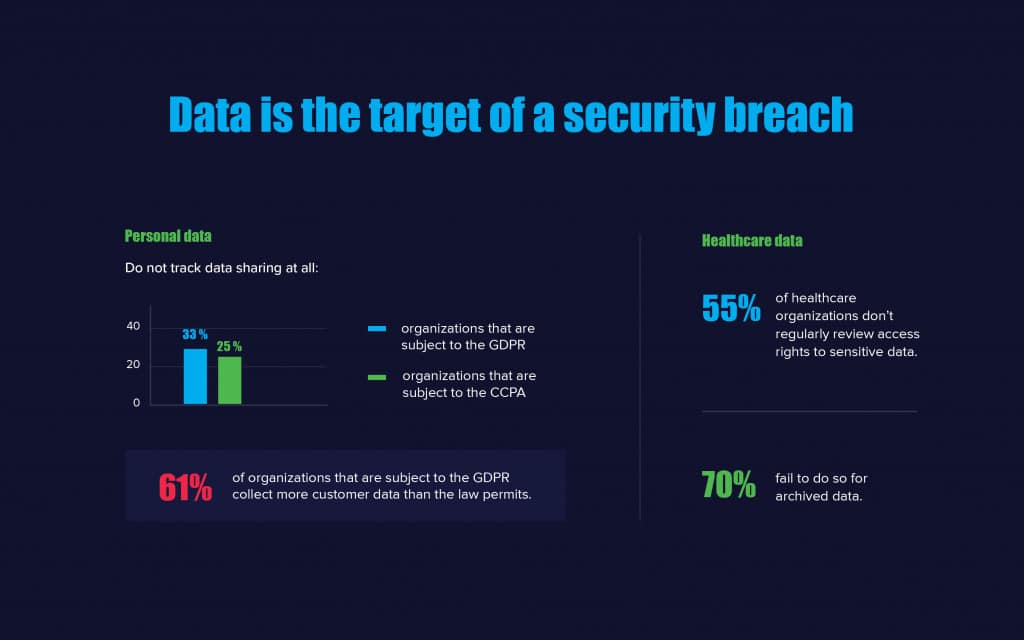
Source: Netwrix 2020 Data Risk and Security Report
Conclusion
In order to develop a successful data-centric security strategy, it’s essential to implement information security controls that are suitable for the value of the enterprise data being protected. As companies continue to allow more employees to work remotely and migrate workloads to the cloud, it’s more important than ever to make data-centric security a top priority. It’s also critical to understand how the data flows both inside and outside the perimeter, and to know where the company’s regulated and sensitive data resides.



