It’s easy to find resources for getting started with cybersecurity — but far harder to find ones designed for people who are already working as cybersecurity professionals. To help, we’ve collected some great options for advancing your skills.
Taking advanced training courses
All too often, cybersecurity pros assume that structured training courses are appropriate only for beginners. The truth is, there are free and paid cybersecurity courses on the market that will help you grow as a professional and avoid critical mistakes.
In addition, vendors often offer training when they release new software or product updates. Taking these classes can quickly bring you up to speed on the solution’s key functionality, saving you a lot of time later.
Earning official certifications
Almost all highly valued courses offer certification levels. Certifications are often costly, but they offer several benefits. First, certification means that you have proven your knowledge and ability in a certain area, which makes you a more desirable candidate for vacancies. For instance, acquiring a certificate from Cisco, a recognized vendor of various hardware, network and application solutions that are used almost in every company, will give you a definite competitive advantage.
Also, it’s a common practice for companies to conduct webinars for their certified specialists when they plan to roll out major improvements, which enables you to get acquainted with the updates before the official release.
Here are several of the most popular cybersecurity certifications:
Participating in hackathons
Another way to improve your cybersecurity skills and network with colleagues is to participate in hackathons, where professionals collaborate intensively to develop a unique project in a limited time. One of the most popular resources for finding these events is Hackathon.com. Enterprise giants such as Samsung also regularly organize hackathons.
Participating in penetration testing and bounty programs
Security specialists work with their IT environment closely every day. With new attack vectors and new vulnerabilities appearing almost every day, it’s wise for companies to periodically get an outside perspective on their cybersecurity posture. External penetration testers will try to breach their defenses using a variety of techniques, from scanning ports to looking for backdoors in publicly available services. Working as a pen tester can help you expand your knowledge of how to defend against cyber threats.
You can also participate in security bounty programs; many companies pay generously if you report a security bug or other vulnerability to them.
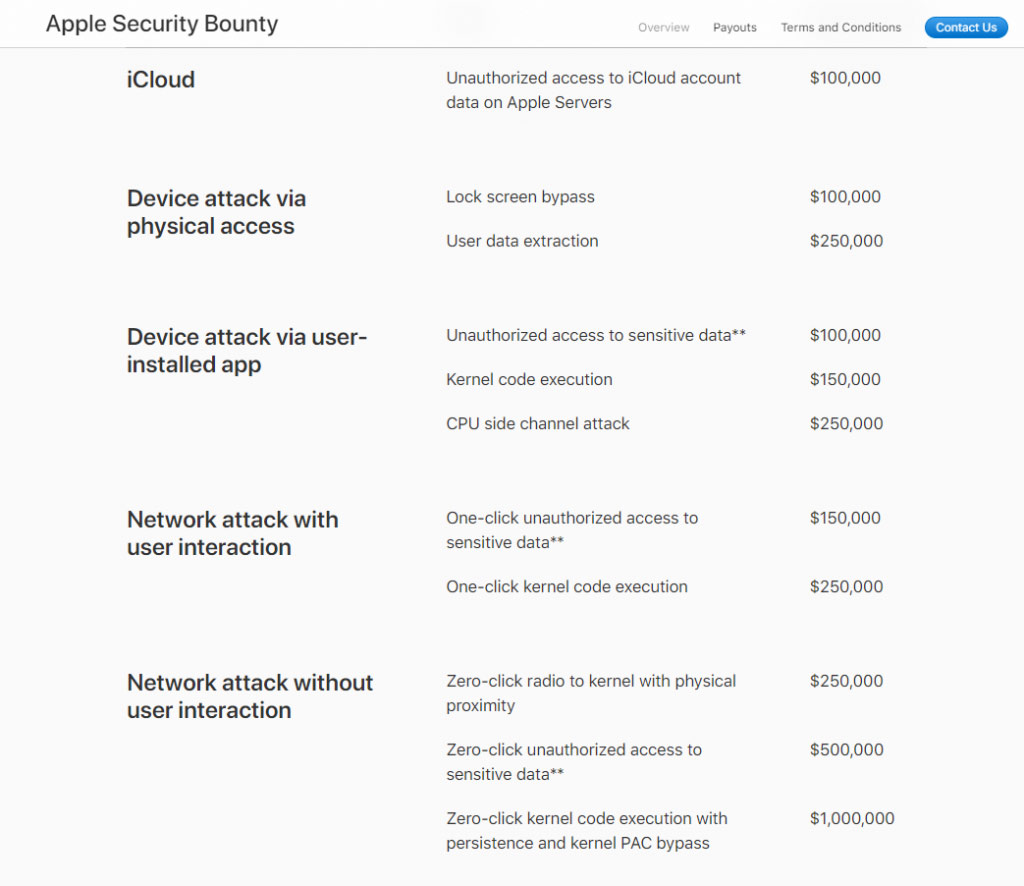
Vendors that offer security bounty programs include:
Any system operated by humans is remains vulnerable to social engineering attacks. Therefore, in addition to enhancing your technical knowledge in cybersecurity, it’s important to learn how to develop procedures to block social engineering attacks, such as requiring verification before providing information to third parties. Options for enhancing your knowledge in this area include taking a course or reading materials written by social engineers, such as this book.
Exploring adjacent fields
To become truly proficient in cybersecurity topics, it’s worth looking deeper into related fields. For instance, you can dive into a particular operating system or virtual environment, learning its file structure and permissions methodologies to understand its vulnerabilities. In addition, it’s worth dedicating some time to learn the OSI model, which divides network communication into seven layers, so you can ensure that security matters that lie above or below the level where you operate are covered.
Here are some additional resources that can help you deepen your knowledge:
- Cybersecurity Guide resource center
- Hackernoon community
- Reddit communities
- Online training: Cybersecurity Practices for Industrial Control Systems
- Linux Security community
- “The Art of Invisibility” by Kevin Mitnick
- “Hacking the Art of Exploitation” by Jon Erickson
- “Future Crimes: Inside The Digital Underground and the Battle For Our Connected World” by Marc Goodman.
Practice
The most effective method for honing your skills is to apply your knowledge. For example, you might start with something as simple as trying to protect your blog using a WordPress security checklist guide and then asking your peers to hack it.
Conferences
With conferences moving to online formats, cybersecurity pros have an unprecedented opportunity to learn from experts around the world. Here is list of virtual conferences and other events to consider attending.



