Managers and compliance auditors often ask IT admins to present a report listing file share permissions granted to a group or a particular user. Here are a few paid and free tools that will help you save time on generating these reports.
Free Tools for NTFS Reporting and Management
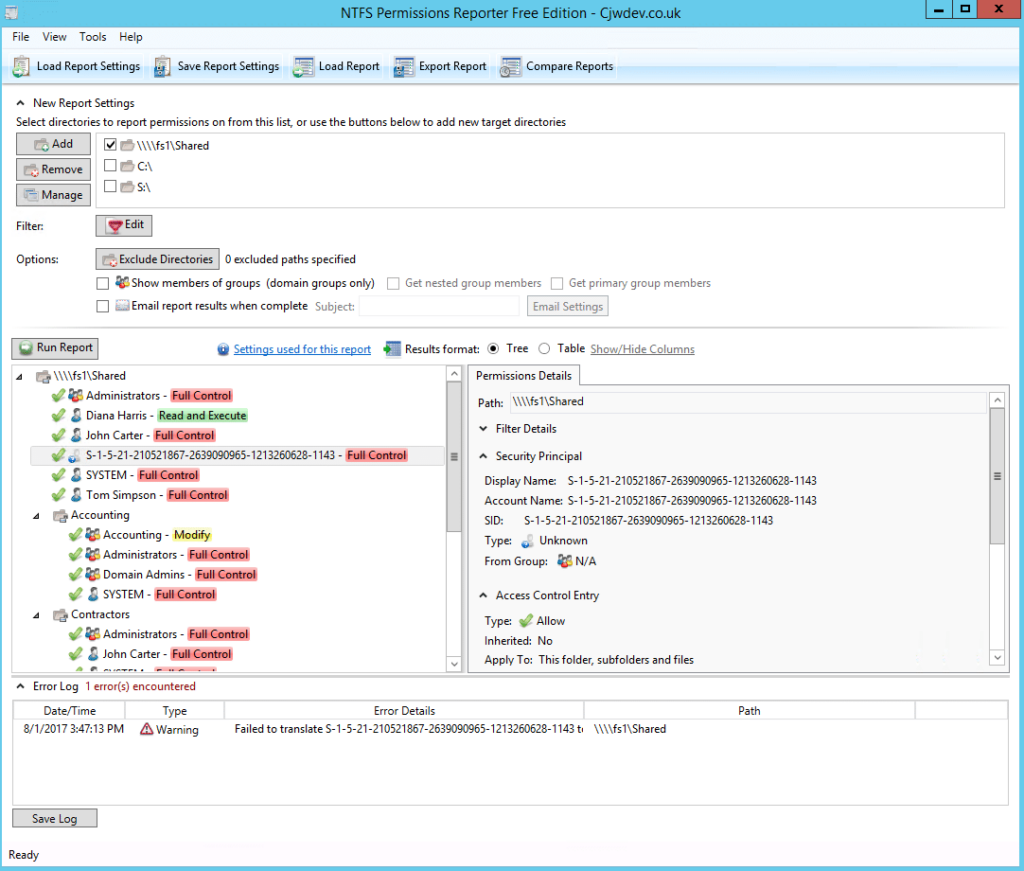
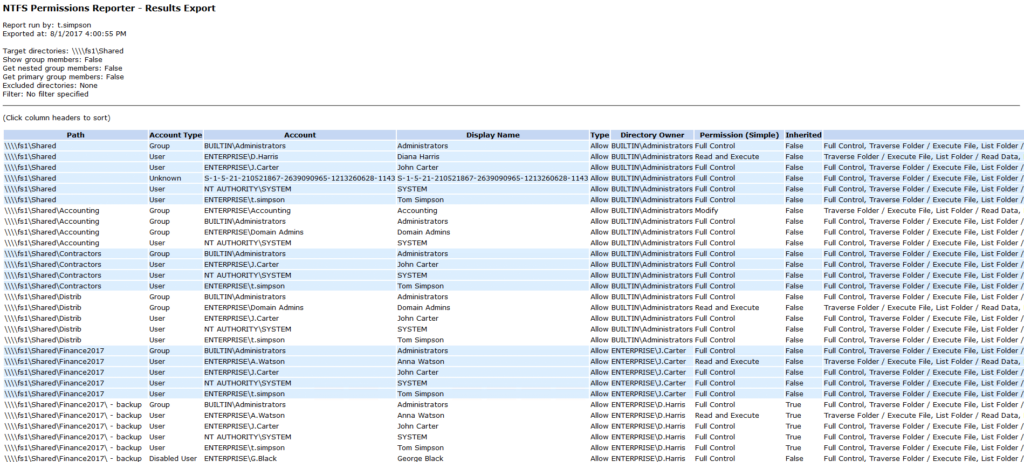
1. NTFS Permissions Reporter Free Edition from Cjwdev
NTFS Permissions Reporter generates reports on file and folder permissions and you can easily export the results to an HTML file. It displays group members (direct and nested) right in the report; plus, you can pick the report format (a tree or table), as well as highlight different permissions in different colors. However, it creates reports on NTFS permissions for a folder only; it cannot show the permissions of a user.
The tool is highly customizable, so at first the interface may look a little overloaded, but the tool is actually rather easy to use. Permission scanning may take additional time.
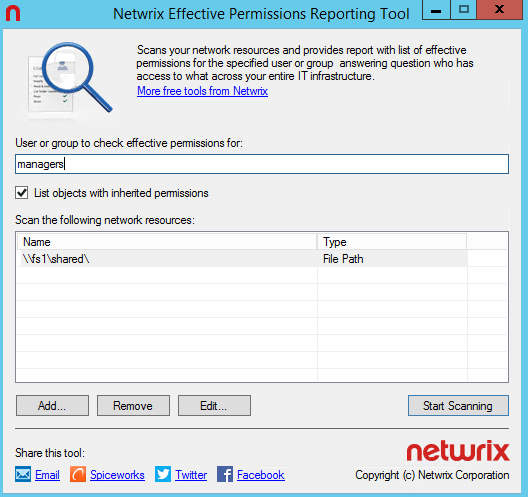
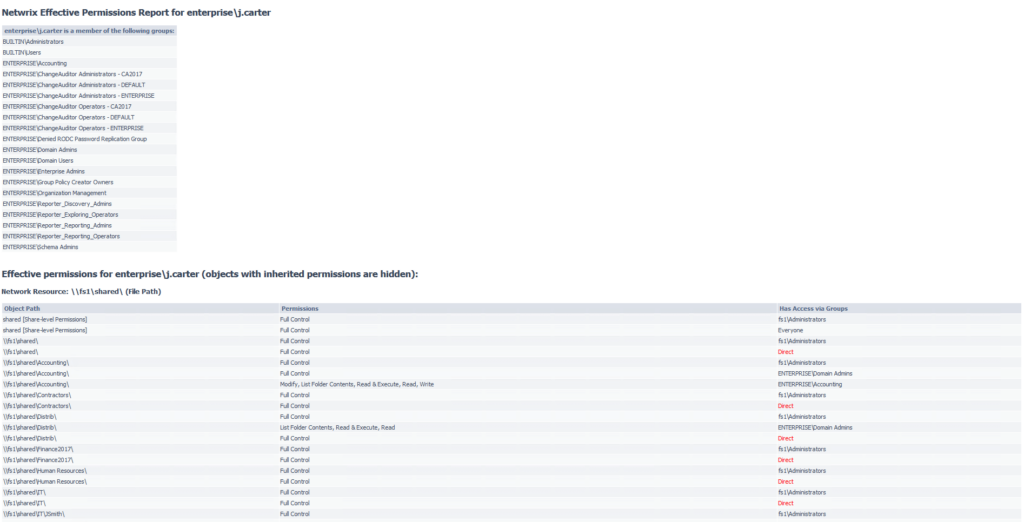
2. Netwrix Effective Permissions Reporting Tool
Netwrix Effective Permissions Reporting Tool provides users’ AD group memberships and file share permissions in a single report, along with whether the permissions were assigned explicitly or inherited. With this actionable information, you can rescind unneeded access rights to ensure that each user has only the permissions they need to do their job and prove compliance with requirements of data privacy mandates.
This freeware tool is very easy to use: Simply enter the name of a user or group to check its permissions. The scan is very fast and the HTML export functionality is straightforward. It doesn’t show folder permissions, however; that type of report is available in Netwrix Auditor for File Servers (20-day free trial).
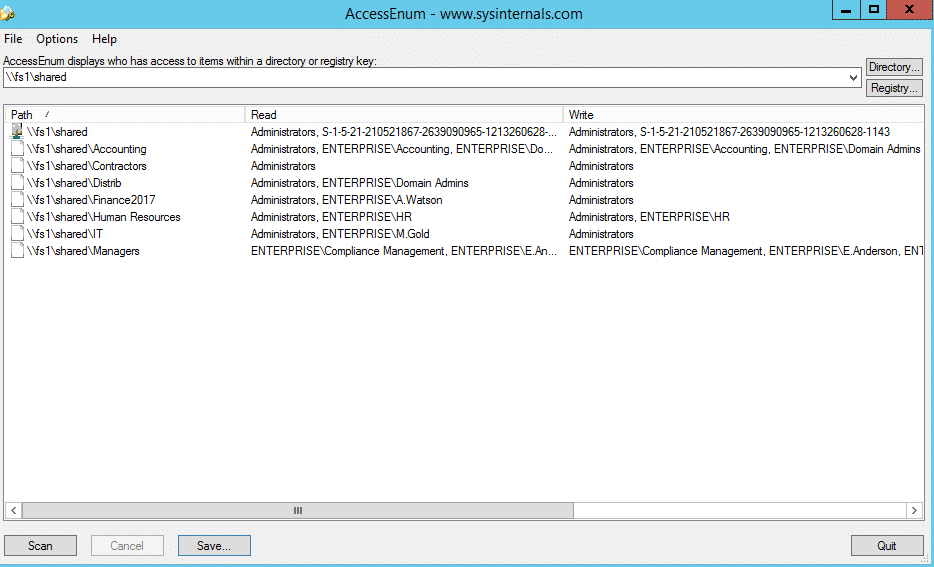
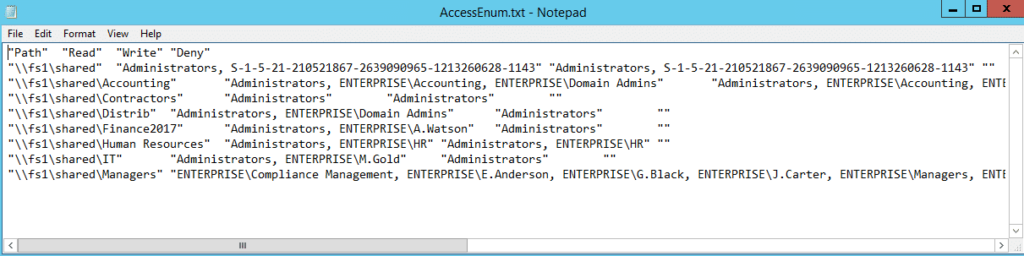
3. Microsoft’s Access Enum
AccessEnum is one of the Microsoft SysInternals tools. It gives you a full view of your file system and Registry security settings in seconds, and provides a table view of all permissions on your file share or registry. However, you can export only to .txt format, which is rather complicated to read. If you want the information in .xls format, you’ll need to copy it from the .txt file manually.
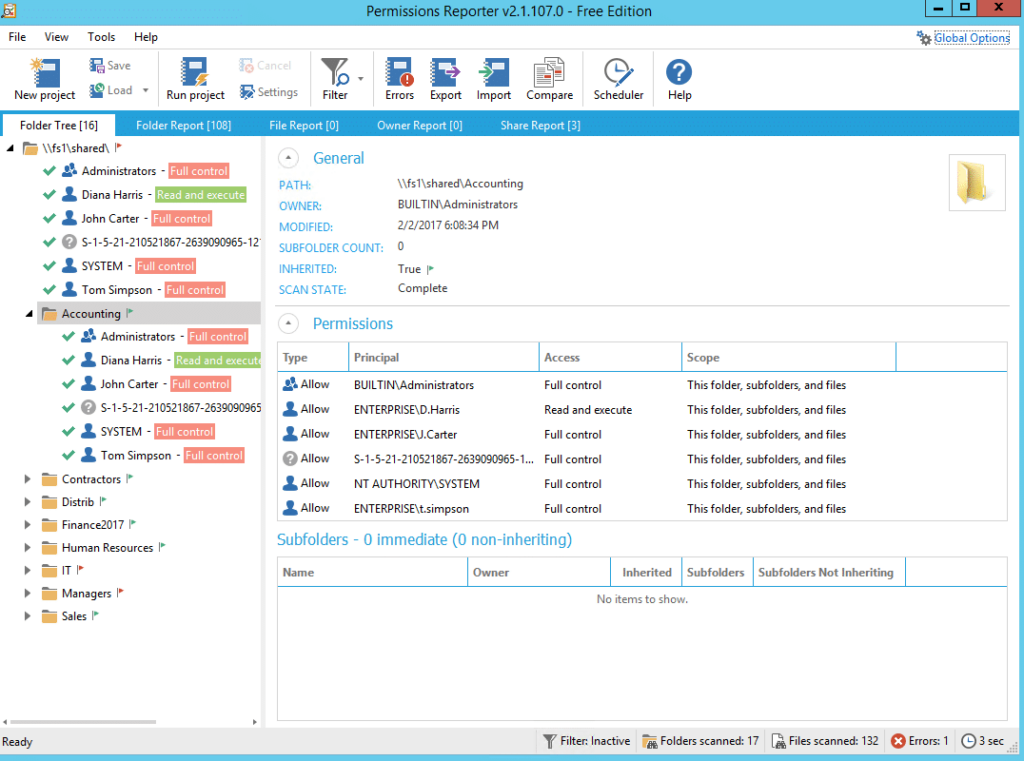
4. Permissions Reporter from Key Metric Software
Permissions Reporter has the same functionality as Cjwdev’s NTFS Permissions Reporter, but a prettier interface. It’s easy to create and download repots. However, permission scanning takes some time, and you can report on NTFS permissions to a folder or a HTML file only, not the permissions of a user.
5. Permissions Analyzer from SolarWinds
Some people might not be fond of Permissions Analyzer because you cannot export information from it, but for those who just need detailed information about user permissions, it can be rather handy. You can quickly see how users’ permissions were inherited, browse permissions by group or by individual user, and analyze user permissions based on group membership and permissions.
6. NTFS Permissions Tools from MajorGeeks.com
NTFS Permissions Tools offers file permissions management for NTFS file systems. This handy tool was made for admins who need a lightweight access rights manager — it enables you to make a lot of permissions and security changes at once. Its main advantage over Window’s built-in permission and security tool is that it takes less time to change permissions and security settings.
BONUS Free Tool: Microsoft PowerShell
If you prefer, you can always rely on your old friend PowerShell. Here are ready-to-use scripts for exporting folder permissions and user permissions into .csv format.
PowerShell code for exporting folder permissions
$OutFile = "C:Temppermissions.csv"
$Header = "Folder Path,IdentityReference,AccessControlType,IsInherited,InheritanceFlags,PropagationFlags"
Del $OutFile
Add-Content -Value $Header -Path $OutFile
$RootPath = "\fs1shared"
$Folders = dir $RootPath -recurse | where {$_.psiscontainer -eq $true}
foreach ($Folder in $Folders){
$ACLs = get-acl $Folder.fullname | ForEach-Object { $_.Access }
Foreach ($ACL in $ACLs){
$OutInfo = $Folder.Fullname + "," + $ACL.IdentityReference + "," + $ACL.AccessControlType + "," + $ACL.IsInherited + "," + $ACL.InheritanceFlags + "," + $ACL.PropagationFlags
Add-Content -Value $OutInfo -Path $OutFile
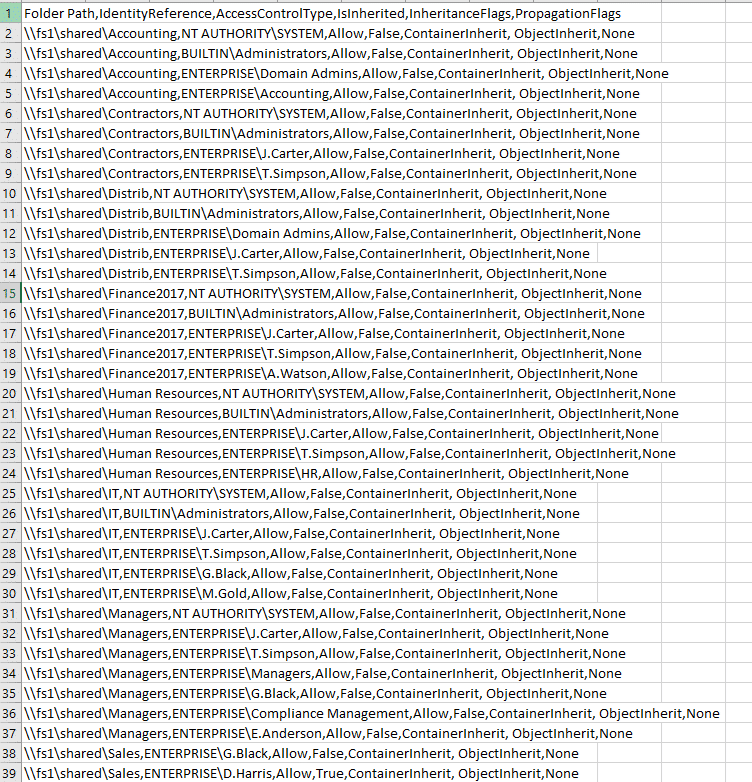
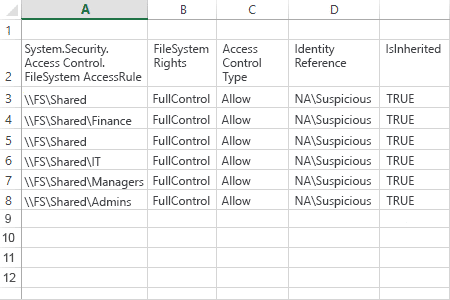
}}Sample report:
PowerShell code for exporting user permissions
"ENTERPRISEJ.Carter" } | Add-Member -MemberType NoteProperty -name "\fs1shared" -Value $path1 -passthru }} | export-csv "C:temppermissions.csv"Sample report:
Paid Tools for NTFS Reporting and Management
1. Netwrix Auditor for File Servers
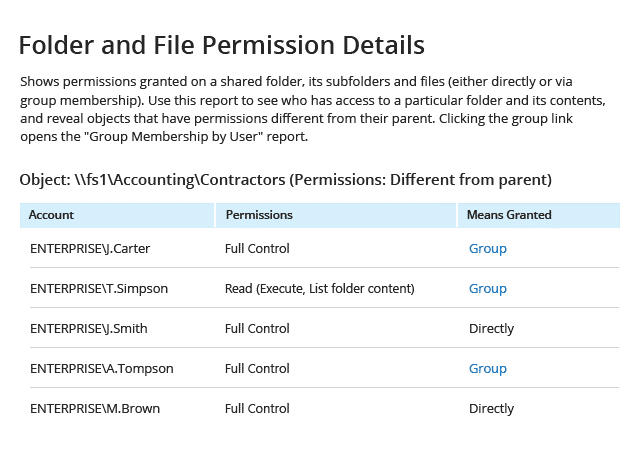
Netwrix Auditor for Windows File Servers delivers deep visibility into your Windows file servers, including permissions. It provides a complete picture of effective permissions by user and by object across multiple file servers and shares, and understand whether those file permissions were assigned directly or via group membership. Moreover, it makes it easy for data owners to perform regular user access reviews, limiting permissions sprawl.
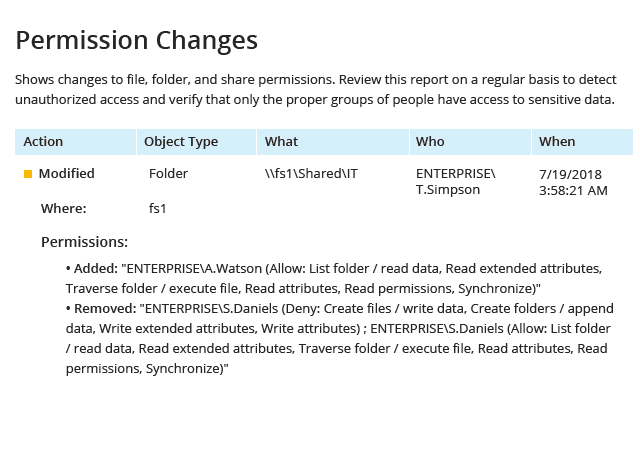
It also delivers visibility into all changes and all access events (both successful and failed) across your file storages, so you can promptly detect privilege escalation attempts and other suspicious activity. It can even identify duplicate files and stale data across your Windows file servers. Its ready-to-use reports streamline NTFS permissions audits and compliance reporting for PCI DSS, SOX, HIPAA and other regulations.
There is a 20-day free trial.
2. Jam Software’s TreeSize
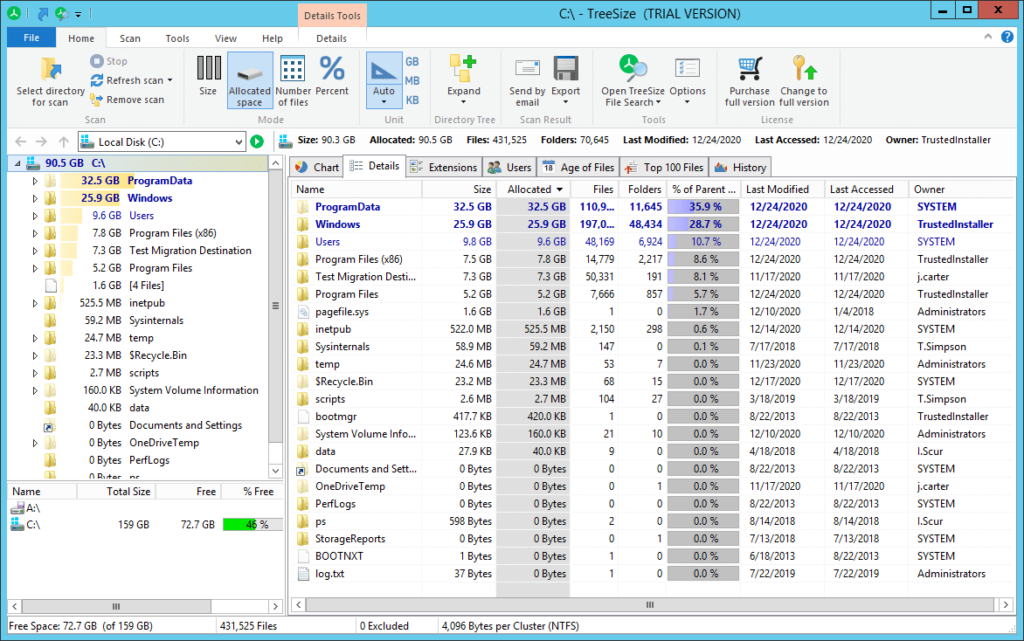
TreeSize is focused on storage analysis. There is a limited freemium licensing option and a 30-day free trial of the full version. The free edition is highly praised by IT admins for its high scan speeds, ability to process and analyze storage (including network drives and locally synchronized cloud drives), and option to break down scan results according to owner, file type, size, etc., throughout the entire file system. For instance, this tool can help admins find the largest files, the oldest files and the files with long paths.
The paid version also analyses file owners and permissions, NTFS compression rate, and much more. It can also process NTFS Alternate Data Streams and NTFS Hardlinks, will export scan results to various file formats, and provides command-line automation options.
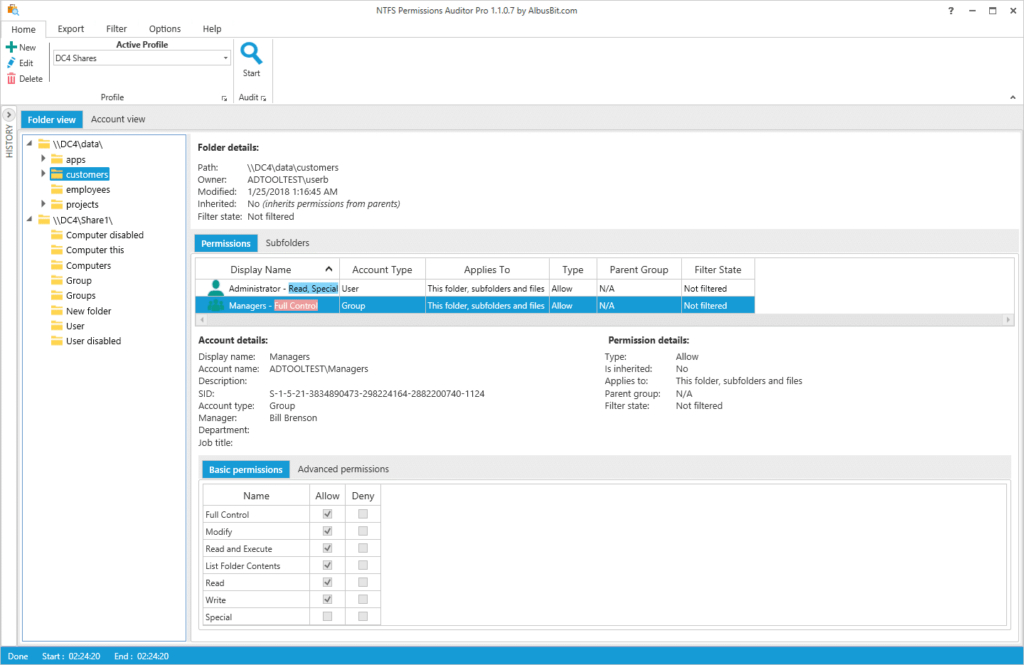
3. AlbusBit’s NTFS Permissions Auditor
NTFS Permissions Auditor allows you to review and analyze any NTFS folder permissions. The free version provides details like full path, owner, last modified date, inherited flag and a full list of permissions in hierarchical folder view or account view. The pro version offers additional features such as report filtering by criteria like account name, SID or department; permission change analysis; export to various formats; report customization; automation; and more.
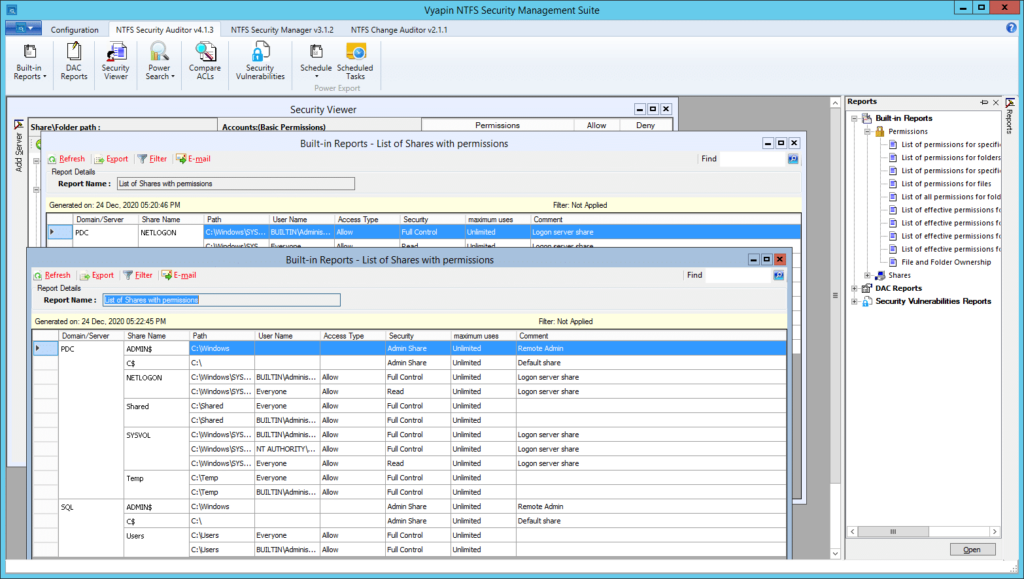
4. Vyapin’s NTFS Security Management Suite
NTFS Security Management Suite is more like a full-fledged NTFS management system than single-task NTFS permission tool. It consists of three modules:
- NTFS Security Auditor enables you to scan shares, folders and files in your network; perform an automated inventory of permissions at regular intervals; and compare ACLs. There are a variety of built-in reports for system administrators and compliance
- NTFS Change Auditor collects and analyses permission changes on specified locations.
- NTFS Security Manager is designed to simplify native permission management.
Vyapin provides a 15-day evaluation copy of NTFS Security Management Suite.
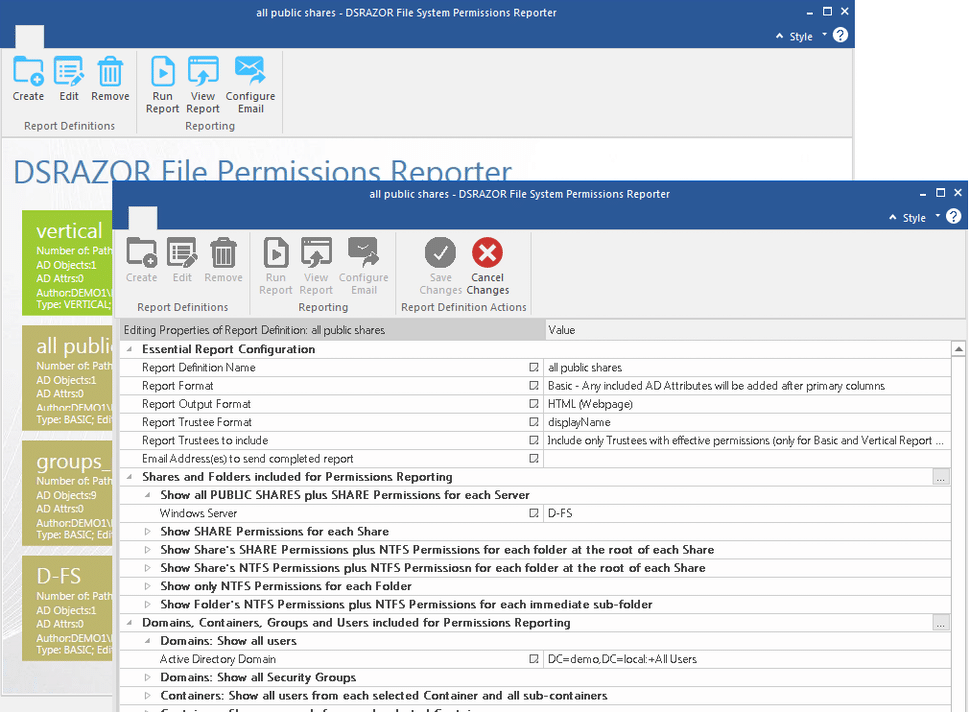
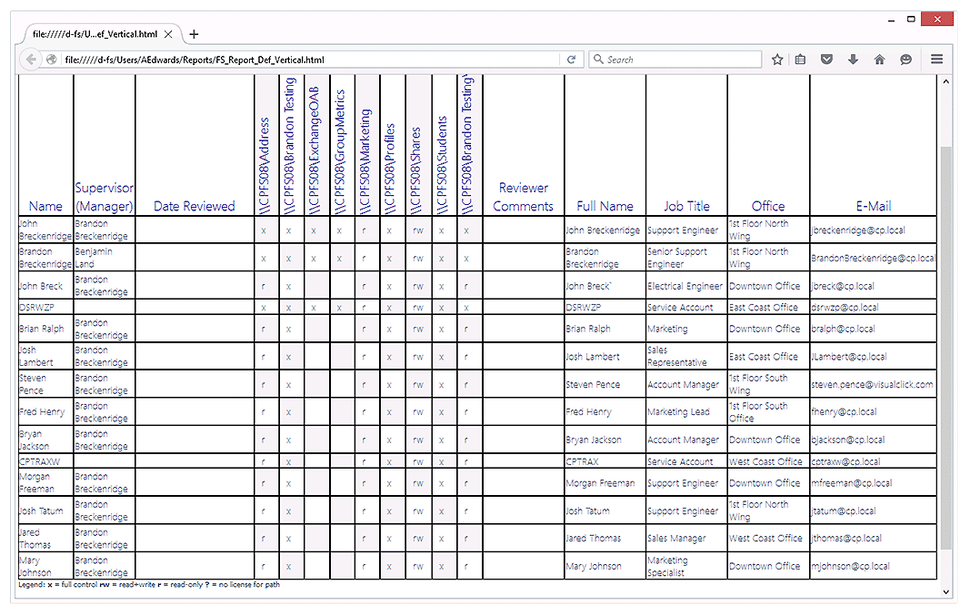
5. DSRAZOR from Visual Click Software
DSRAZOR is a versatile and customizable reporting tool for administrators and compliance auditors. You can analyze permissions for a particular file or folder. Reports are customizable and can include specific Active Directory attributes for each trustee, so auditors can tailor reports to their particular needs. There are comprehensive reports on past due, blocked or deactivated Active Directory accounts, and you can find out which accounts are not in use during a particular period, where the last login failed, and much more. However, while DSRASOR is praised by many for its versatility, there is a fairly steep learning curve — the report design tool is rather clunky, and setup process is not super user-friendly.
FAQ
Where are NTFS permissions stored?
NTFS (New Technology File System) permissions are stored in the Master File Table (MFT) of an NTFS file system. The MFT is a database-like structure that stores metadata for files and folders on an NTFS volume. It contains information about file attributes, file names, timestamps, and security descriptors, which include the NTFS permissions.
When you apply NTFS permissions to a file or folder, the permissions are stored as part of the file or folder’s security descriptor in the MFT. Each file or folder has its own security descriptor that holds the associated NTFS permissions. This information is used by the operating system to control access to the file or folder.
How do I manage NTFS permissions?
Managing NTFS permissions involves controlling access to files and folders on an NTFS volume. Here are the steps to manage NTFS permissions:
- Identify the file or folder for which you want to manage permissions.
- Right-click on the file or folder and select Properties from the context menu.
- In the Properties window, navigate to the Security tab to see the current NTFS permissions assigned to the file or folder.
- To manage NTFS permissions, click the Edit or Advanced button (depending on your Windows version).
- On the permission settings page, you can grant or deny various permissions, such as Full Control, Read, Write or Modify, to individual users or groups.
- After making the necessary changes, click Apply and then OK to save the modified NTFS permissions.
It’s important to exercise caution when modifying NTFS permissions, as improper changes can lead to access issues or compromise the security of your files and folders.
How do I audit NTFS permissions?
Auditing NTFS permissions allows you to monitor access to files and folders on an NTFS volume. To audit NTFS permissions, follow these steps:
- First, you need to enable auditing on the NTFS volume. Right-click on the file or folder, select Properties, and go to the Security tab. Click the Advanced button and navigate to the Auditing tab.
- Click the Add button and select the user or group for which you want to audit access. Choose the specific actions you want to audit, such as reading, writing, deleting or modifying permissions.
- Click OK to apply your changes and close the dialog boxes.
- To view the audit logs, you need to access the Event Viewer. Press Win + R to open the Run dialog, type eventvwr.msc and press Enter. In the Event Viewer, navigate to Windows Logs > Security. Look for events with Event ID 4663, which are file or folder access events.