Insider threats are a growing cybersecurity concern. A 2022 study by Ponemon found that the cost of insider threats leaped 44% in just two years, with the per-incident cost now $15.8 million. The report also shows that it takes companies an average of 85 days to contain an insider threat incident, up from 77 days in 2020.
While organizations are certainly aware of the issue, the resources required to address it often outpace their IT security budgets. A solid insider threat prevention strategy needs to consider many things: IT infrastructure, data storage technologies, data sensitivity, data protection measures, data security and privacy mandates, and industry norms and best practices.
Read this guide to learn more. We will start with an insider threat definition and then address questions like what is an insider attack and how do security threat actors operate. We will also provide insider threat examples and detail common indicators of insider threats, and explain how to identify and mitigate insider risks.
What Are Insider Threats?
What is an insider threat? Insider threats are security risks from any IT account with legitimate access to the organization’s information and assets. Anyone working for or connected to a company, such as current and former employees, contractors, business associates and vendors, is a potential insider threat — and so is an adversary who compromises the credentials of any of those users.
Types of Insider Threats
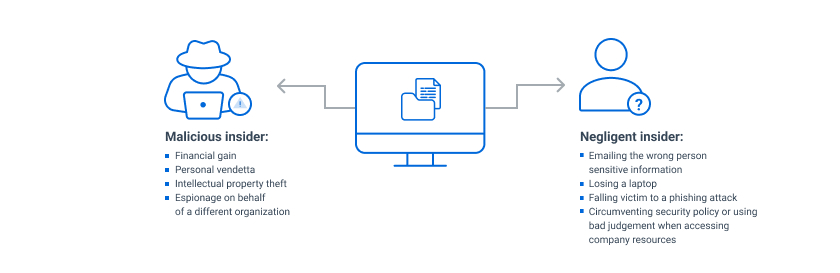
There are three types of insider threats: insiders who are negligent or careless, insiders with malicious intent, and hackers who become insiders by stealing legitimate system credentials.
Unintentional Insider Threats
Users can unintentionally or negligently compromise data or put the organization at increased risk due to insecure behavior. Unintentional insiders can be direct employees of an organization as well as contractors and third-party vendors.
Examples of unintentional or negligent behavior that can put an organization at risk include:
- Failing to protect credentials
- Falling victim to common attacks like phishing or social engineering
- Neglect to apply security patches and updates
- Sharing confidential information due to ignorance or disregard of data sensitivity levels
- Disregarding security policies that are inconvenient
- Emailing sensitive information to the wrong person
- Losing a laptop
Malicious Insider Threats
Malicious insiders are people with legitimate access to the network who deliberately take actions that benefit them but cause harm to the organization.
Motivations for intentional attacks include:
- Espionage — An employee might use their access to a company’s systems or data to gain information to achieve a competitive advantage. For example, an employee who is planning to quit might steal intellectual property or proprietary data to give to their new company.
- Revenge — A worker with a grudge against an organization could use their access rights to damage the company or its people. For example, they could attack important systems or steal and publish executives’ emails or other sensitive information.
- Profit — A malicious insider could use their access to make money. For instance, they could divert funds from a company account or sell sensitive data.
Adversary with Compromised Credentials
Another type of insider threat is a hacker who steals valid user or admin credentials to get into the corporate IT network. Credential theft costs companies $2.79 million per year, making it the most expensive form of insider threat.
Hackers use various methods to steal credentials, including:
- Phishing emails — Individuals inside an organization receive emails disguised as legitimate business requests, often asking for information like bank routing numbers or requesting that the recipient download an infected attachment or visit a malicious website.
- Pass the Hash — This hacking technique allows an attacker to authenticate using the stolen hash of a user’s password instead of the plaintext password.
- Password-guessing attacks — Hackers use a variety of approaches to guess a user’s password, including:
- Brute-force attacks: Hackers run a program that attempts to log on using common passwords and working through every possible character combination.
- Dictionary attacks: This tactic involves working through different phrases and word strings instead of individual characters.
- Spraying attacks: Hackers use a few common passwords to attack thousands of accounts at once.
- Reverse brute-force attacks: The attackers attempt to use one password to log into multiple user accounts.
Common Indicators of Insider Threats
What do you need to watch for to detect an insider threat? Here are some common indicators:
- Attempts, either failed or successful, to access systems or data outside of working hours or outside of normal job duties
- Unusual access patterns, such as attempts to download or copy large amounts of data
- Use of unauthorized systems, devices and software, such as public cloud storage
- Attempts to bypass security protocols or violate corporate policies
- Unusual behavior from employees, partners or contractors
- Corporate policy violations
Consequences of Insider Threat Incidents
Insider threats can cause severe and costly damage to an organization. Among the consequences are:
- Loss of critical data, such as intellectual property, trade secrets, personal data and customer data
- Other damage, such as taking down or compromising critical systems and spreading malware
- Productivity losses from delays in vital business functions like production, operations, customer service response and supply chain management
- Direct financial impact, including costs related to incident investigation and the remediation of systems and processes
- Legal and regulatory costs, including fines for compliance failures and costs of litigation from individuals affected by a data breach
- Loss of competitive edge resulting from data loss, such as a pharmaceutical company losing years of research into a promising drug, costing millions in potential revenue
- Damage to reputation that can make it difficult to regain the trust of customers and shareholders
Why Insiders Can Be More Dangerous than External Threats
Malicious or negligent insiders can be even more dangerous than external attackers for several reasons:
- Insiders have legitimate access to critical resources, so they do not necessarily need to identify and exploit security vulnerabilities.
- Insiders already know the lay of the land, so they do not need to go through the exercise of finding where sensitive data exists or learning which assets or resources are most valuable to the organization.
- Insiders may regularly handle critical systems or data, so they have a higher likelihood of errors or negligence that can cause lasting damage.
Each of these factors contributes to the underlying difficulty of detecting an insider threat. With legitimate access to resources, knowledge of where sensitive data exists, and the security controls in place, malicious insiders can cover their tracks much more easily than external attackers and thus can stay undetected for far longer.
Examples of Insider Threats that Led to Data Breaches
Here are some real-life cases in which an insider with legitimate access to a system was the root cause of a data breach.
- Anthem — One of Anthem’s consulting firms, LaunchPoint Ventures, revealed that one of its employee stole the personal health information of more than 18,000 Anthem Medicare members by emailing that data to their personal account.
- Rockwell and Boeing — Over the course of 25 years of employment at Rockwell and then Boeing, Greg Chung stole sensitive data to help the Chinese space program, not only damaging those companies but also national security.
- Capital One — A software engineer employed by AWS took advantage of a misconfigured web application in an AWS-hosted resource to steal over 100 million customer records from Capital One, including account and credit card application information.
Protecting Your Organization Against Insider Threats
No single technology can defend against insider threats. Instead, organizations need a multi-layered strategy that includes identity and access management (IAM), privileged access management (MFA), Active Directory (AD) security, and data access governance (DAG).
Here are the critical elements to build into your insider threat protection strategy:
Classify your data according to its value and sensitivity.
Understanding which information has the most value, where it’s stored, and how it’s accessed and used is essential for keeping it safe. Data discovery and classification solutions can help your company find sensitive and regulated information and classify it so you can apply appropriate security controls.
Monitor user activity across the entire network.
It’s vital to understand exactly who is accessing what data and what they are doing with it. Focus on monitoring critical systems and data first, and then expand the scope as necessary. Choose a monitoring tool that doesn’t just provide raw user activity events but also utilizes user behavior analytics to identify suspicious or risky actions.
Implement strong access controls.
Ensure that people have access to sensitive data only as necessary for their job function. In particular, have administrators use regular user accounts for routine business functions, and grant them temporary elevated privileges as needed to complete specific tasks. Eliminating permanent privileged accounts significantly reduces the insider threat.
In addition, implement security procedures and controls like these:
- Remove access to resources promptly when users change roles or leave the company.
- Place controls around third-party access.
- Require multi-factor authentication (MFA) for access to critical systems and data
- Regularly look for and delete unused accounts.
- Harden Active Directory to reduce potential threat vectors.
Make threat detection a priority.
The longer an insider threat remains undetected, the larger its financial impact. The 2022 Ponemon Institute insider threat study showed that incidents that took 90 days to contain cost organizations $17.19 million annually, while incidents that lasted less than 30 days cost roughly half of that.
To detect insider attacks quickly, you need a comprehensive threat detection and response system that includes:
- The ability to detect specific tactics, techniques and procedures commonly leveraged by attackers, as well as the ability to define threat parameters based on your own unique requirements
- Comprehensive investigation capability to help aid forensic investigations on users and related activities
- User behavior analytics powered by machine learning and artificial intelligence to baseline typical access patterns and identify anomalous and outlier behavior
5. Maintain company-wide awareness of insider threats.
Conduct risk assessments of individuals working with privileged information. All users should regularly receive comprehensive security training about which data access and distribution activity are and aren’t allowed.
6. Respond quickly to detected threats.
The best way to minimize the damage from different types of insider attacks is to craft automated workflows using a catalog of response actions, such as:
- Temporarily blocking access to data
- Disabling compromised credentials
- Removing malicious files
- Alerting appropriate individuals or teams
- Blocking a process or application
For example, you might build a playbook that will automatically block access to data and disable credentials when unusual activity suggests an account has been compromised.
How Netwrix Can Help
Data access governance software from Netwrix provides an effective and scalable approach to insider threat prevention. Moreover, it will help you reduce the risk of cybersecurity incidents by enabling you to understand who has access to what and strictly limit access to sensitive data. You can:
- Audit activity across your IT ecosystem.
- Reduce access to sensitive data to the required minimum to reduce the risk of insider threats and minimize the damage from ransomware and other attacks.
- Streamline regular privilege attestations by data owners.
- Protect sensitive data whenever it goes with accurate and consistent tagging of content.
FAQ
What is an insider threat?
An insider threat is a cybersecurity risk that comes from within an organization. It usually occurs when:
- A current or former employee or business partner misuses their admin or user account, either accidentally or deliberately
- A legitimate user or admin account gets compromised by outside attackers
What are some examples of insider threats?
Examples of insider threats include:
- A user who is negligent about security protocols and opens an email attachment containing malware
- A malicious insider who steals data for a competitor (espionage)
- A hacker who uses a brute-force attack to steal user credentials, thereby gaining access to an organization’s systems and data
Why is it important to identify potential insider threats?
Failing to detect insider threats can lead to data loss and system downtime. As a result, companies can face steep costs, including fines, lawsuits, incident mitigation work and reputation damage.
What are some insider threat indicators?
Signs of an insider threat include repeated attempts to access or download sensitive data, unusual use of data or applications, and attempts to bypass security protocols or violate corporate policies.
How can I mitigate the risk of insider threats?
Start by educating all employees about insider threats. Organizations should also invest in tools and technology to classify their data and spot suspicious user behavior.
What is the most common insider threat?
One of the most common insider threats results from phishing — threat actors send messages purporting to be from reputable organizations to trick employees into revealing their credentials, enabling the adversaries to become insider threats.
What are the four types of insider threat?
The four types of insider threat are:
- The Pawn — An employee who is manipulated into doing malicious activities, such as disclosing credentials to fraudsters or downloading malware
- The Goof — A lazy, arrogant or ignorant user who bypasses security controls or leaves vulnerable resources and data unsecured, giving malicious attackers easy access
- The Collaborator — An employee who works with a third party, such as a nation-state or company competitor, to steal intellectual property or commit other cybercrimes
- The Lone Wolf — An insider who acts maliciously without external manipulation or influence



