How Traditional PAM Solutions Fall Short
Two decades ago, “PAM” stood for privileged account management because PAM software sought to secure privileged accounts with elevated access to critical assets, usually by using a password vault. Over the years, PAM software evolved to using proxy servers to handle those vaulted passwords, and “PAM” came to stand for privileged access management.
Despite this change in terminology, traditional PAM solutions still leave organizations saddled with dozens or hundreds of standing accounts that have admin or other elevated privileges. Indeed, we have analyzed thousands of networks and found that most have 3–5 admin accounts per physical admin user. That means an environment with 25 admins could easily have 75–125 standing admin accounts!
These standing admin accounts are ripe for misuse by their owners, and since they are the keys to your kingdom (i.e., your Active Directory and domain controllers), they are a prime target of attackers. What’s more, each use of a privileged account can leave behind artifacts (e.g., Kerberos tickets) in the memory of the computers they log in to, which attackers can use for lateral movement.
The only way to minimize these risks is to remove as much standing privilege as possible and clean up all artifacts left in the wake privileged account use. This is where ephemeral accounts come into play.
How Ephemeral Accounts Solve the Core Problem of PAM
Ephemeral accounts are accounts that exist for only a short time, while they are actively being used to perform an authorized task. In Netwrix SbPAM, these accounts are called Activity Tokens, and they are created just in time and with just enough privilege to perform the administrative task at hand. When the task is completed, both the Activity Token and any artifacts it created are deleted.
The beauty of Activity Tokens is that when they’re not in use, they’re not left “standing” in the environment, vulnerable to attack — which drastically reduces an environment’s attack surface area.
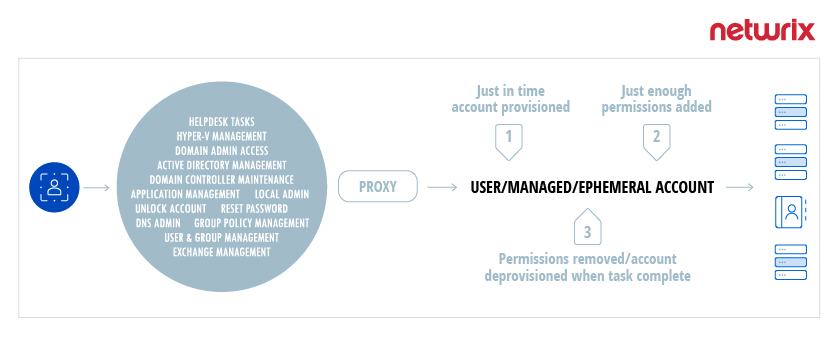
For day-to-day administrative tasks, Netwrix SbPAM provides a secure mechanism to give admins access to the resources they need without the overhead or complex access policies of traditional PAM solutions. Here’s how the process works:
- When an admin need to perform a task, Netwrix SbPAM creates an Activity Token.
- Netwrix SbPAM adds just enough permissions to the Activity Token to complete the task.
- The user is connected to the appropriate server to perform the task, and all activity is recorded and available for later playback.
- Once the task is completed, SbPAM deletes the Activity Token and any artifacts, such as Kerberos tickets, that the session created.
The goal of this approach is zero standing privilege — complete removal of all vulnerable privileged accounts except built-in accounts that cannot be removed.
How Ephemeral Accounts Dramatically Reduce Risk
Attackers seek to compromise privileged accounts because those accounts empower them to move laterally through the network in order to steal sensitive data and access key systems to plant back doors or launch attacks, including ransomware.
With zero standing privilege, attackers who manage to get into a network by compromising ordinary user credentials are stymied in their effort to escalate their privileges and move laterally. Therefore, the organization is at far less risk of suffering a data breach or ransomware infection.
Netwrix Privileged Access Management Solution – Netwrix SbPAM
Privileged Access Management tools have proven to be essential components of information security and compliance programs, yet privileged account compromise remains a nagging issue despite broad-scale adoption of password vaults.
Netwrix’ approach to Privileged Access Management (PAM) fills the gaps and overcomes the challenges of traditional PAM solutions, providing comprehensive visibility into an organization’s privileged account footprint, surgical control over privileged account usage, and the ability to effectively reduce the threat surface and lateral movement attacks privileged accounts allow.



