A brief history of PAM
The term is not as straightforward as most people think. It has evolved over the years in parallel with the ever-changing security landscape. To understand why vaults have taken such an unwarranted central position, let’s quickly review how the market has evolved over the last two decades.
- In the early 2000s, PAM meant privileged account A surge in compliance mandates in the first decade of this century forced organizations to improve their account password management practices. This was low-hanging fruit, since many organizations did not require complex passwords and did not rotate them regularly, which has become almost be unthinkable today.
- Around 2012, PAM began to mean privileged access As legislation started to require better segregation between user and server environments, the practice of using session proxies to connect users to servers gained mainstream acceptance. This approach offered multiple benefits: The user’s password never got exposed, the user did not have to have direct access to the server, and the activity through the proxy could be recorded and played back. Accordingly, the focus shifted from privileged accounts to privileged access.
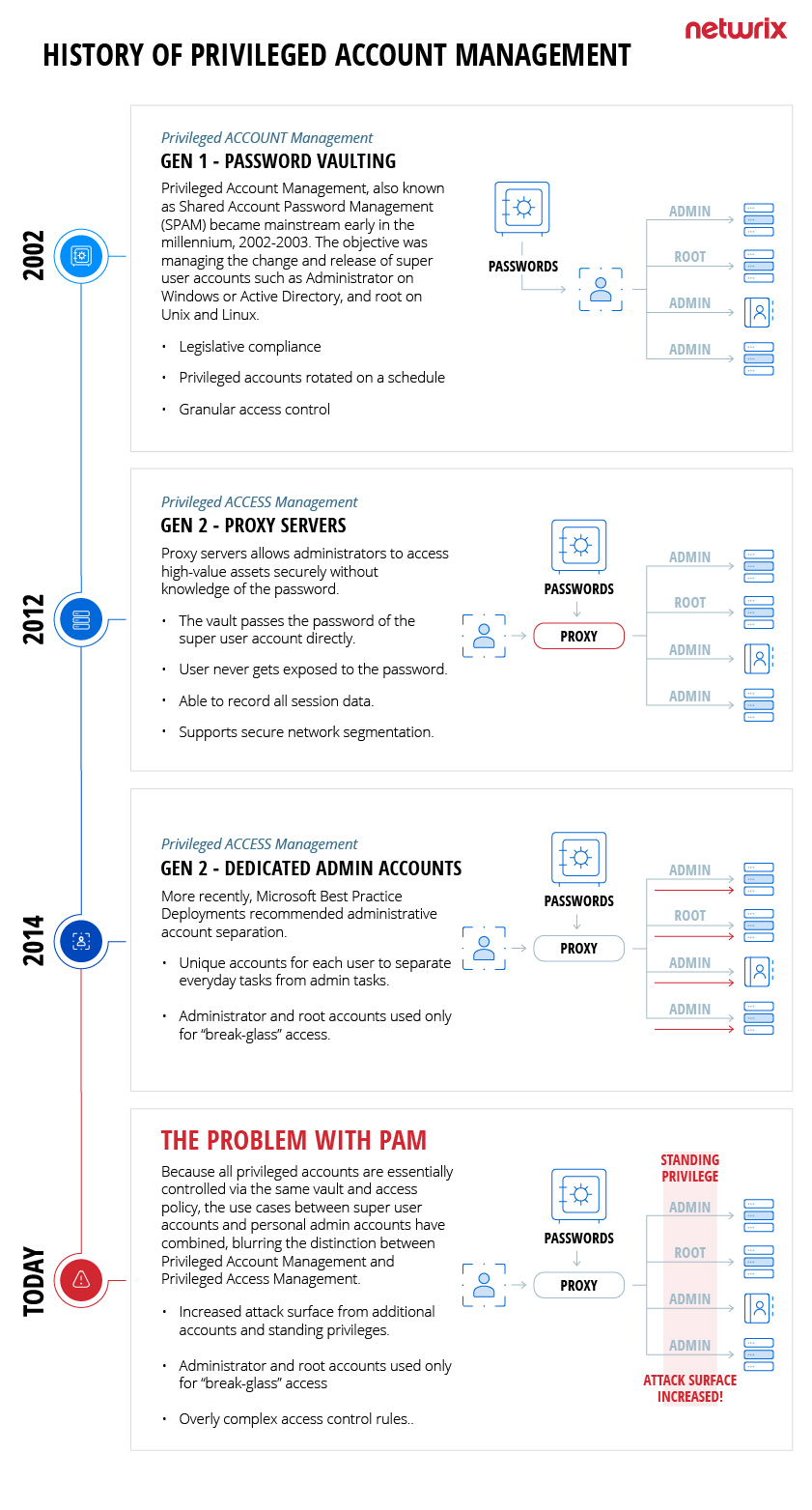
The problem with traditional PAM solutions
Indeed, the PAM market is still dominated by solutions that have a password vault at their core. But this approach adds layers of complexity to what is actually a very simple problem: Providing administrators with secure access to servers to do their job. Vaults map people to accounts, and accounts to systems, and systems to applications. This many-to-many-to-many approach makes implementation and use of the solution complicated and costly. Moreover, it actually fails to address the core security issue — each account under management still retains its privileges even when it’s not in use, leaving the organization with a large attack surface area that hackers are eager to exploit.
But the idea that a PAM solution must come wrapped around a password vault is actually a misconception. Today, there is a better way to deliver secure privileged access management.
A modern approach delivers security without all the cost and complexity
Netwrix Privilege Secure is a next-generation solution built from the ground up to solve the fundamental PAM challenge: enabling administrators to safely and securely access the systems and data they require to do their jobs. A patented 3-step process supports any access control use case, for any platform:
- Grant — Provide just enough permissions, just in time, to perform a necessary task
- Connect — Empower the admin to perform the task (for example, by logging into a server or automatically starting an application)
- Remove — Delete the account and all associated artifacts so that there are no elevated privileges for attackers to compromise
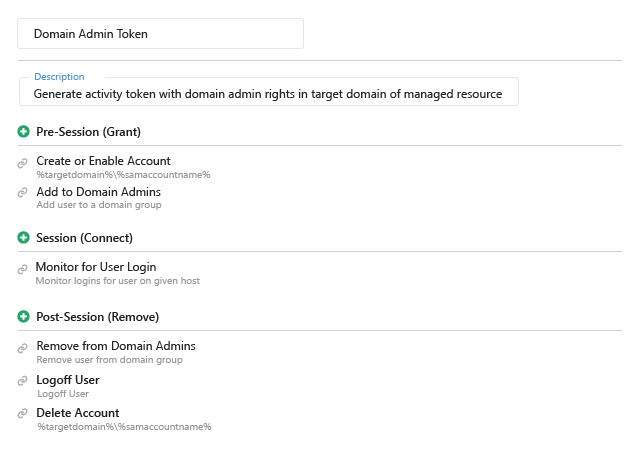
This approach enables organizations to remove nearly all standing privileges, which dramatically reduces their attack surface area. Moreover, there is far less complexity, since the solution does not rely on mapping privileged accounts to upstream security groups.
In short, Netwrix Privilege Secure enables administrators and helpdesk professionals to perform their day-to-day activities easily without the cost and complexity of traditional PAM tools.



