Privileged access management (PAM) solutions have been around in various forms for decades now. Whether you want a password vault, session management, reduced privilege or a combination of privileged management workflows, there’s been no shortage of vendors to choose from.
So why does the thought of PAM still make admins shudder? Surely, it should be enjoyable to have a PAM solution humming along, reducing your organization’s risk while you, the admin, focus on your other duties.
Unfortunately, that’s not what most admins experience. PAM solutions, while essential, have been a pain point for organizations looking to reduce their risk and attack surface area for as long as they’ve existed, and the issues have only grown over time.
Here are the top 5 things people hate about PAM — and how to overcome them.
1. Complexity
Most PAM solutions focus on controlling access to powerful credentials, rather than on the activities administrators need to perform. As a result, the solution is more properly called a privileged account management solution than a privileged access management solution.
Most solutions revolve around a password vault, which controls both superuser accounts and personal admin accounts. The vault maps people to accounts, accounts to systems, and systems to applications. This many-to-many approach increases complexity and risk. Moreover, it fails to reduce the organization’s attack surface area, since all those standing privileged accounts still exist and are vulnerable to compromise.
If that weren’t complicated enough, as regulations and security best practices evolved, more features were added on top of the password vault to provide session management, ensure least privilege, and so on. Over time, these incremental changes have piled up, and the solutions have become a complex web of moving parts. Often, they even require separate virtual machines — or even separate hardware.
2. High licensing, implementation and maintenance costs
IT pros know that the sticker price of any software solution may not be the only — or even the highest — expense involved. With traditional PAM tools, they have been burned not just by costly per-seat licensing, but all the hardware provisioning costs, IT time required to oversee the software and keep it running, and costs associated with updates.
Specifically, a traditional PAM solution often requires the organization to spin up additional servers to handle the various PAM services (such as privileged session management) required to be installed on separate machines. The number of servers may be much higher than first thought due to limits on the number of concurrent users (or sessions) per server enforced by the PAM software.
In a large organizations, multiple administrators might need to spend time overseeing the install, managing the day-to-day workflows and troubleshooting. When those admins are tied up working on the PAM software all day long, they can’t focus on other tasks — forcing the organization to budget for more admins to keep everything running.
3. Need for expensive professional services
The cost of a traditional PAM solution isn’t limited to the licensing, hardware, management and update costs. Often, these solutions are so complex that organizations need to pay for professional services to help with implementation, add new workflows, troubleshoot and assist with updates.
For example, after months of implementation effort, an organization might finally have its PAM solution up and running — only to discover a new use case, and then another one, and then yet another one. If it’s not clear how to integrate these new requirements into the PAM solution, each time, they’ll need to purchase additional professional service hours from the vendor.
4. Administration headaches
Because traditional PAM solutions have so many moving parts, a single administrator typically won’t understand how the entire solution works. Instead, different admins often have responsibilities for particular use cases, such as Windows, Linux and specific databases. This can result in confusion if users run into issues with their workflows: Where did the breakdown occur, and who should fix it?
In addition, it can take an enormous amount of the IT team’s time and effort to integrate a traditional PAM solution with other critical components of the IT infrastructure, such as a security information and event management (SIEM) tool. Today, such integrations should be plug-and-play.
5. Solution failures
With complexity comes more opportunities for software to fail. With services built on top of each other over time, the result is layered dependencies that can cause the whole thing to come crashing down when a single part fails.
In traditional PAM solutions, the password vault is the core component that the rest of the software has been built on for decades. If the vault experiences any downtime, then the rest of the software grinds to a halt — preventing admins from performing essential tasks. While high availability options are available for many traditional PAM solutions, they’re typically just as complex and difficult to implement as the rest of the product.
Netwrix Privilege Secure to the Rescue
Rather than centering on a password vault, Netwrix Privilege Secure is built around the workflows that everyday admins depend upon — gaining privileged access to the resources they need to complete a particular task. Everything else is built around it through modular microservices — session management, audit, federation, account management, password rotation and more.
Just-in-time PAM reduces your attack surface area
Netwrix Privilege Secure facilitates secure administrative access using third-generation technology that is intuitive and easy to deploy. When an admin needs to complete a task that requires elevated access, the solution generates an ephemeral, just-in-time account with just enough permissions for the task, and removes it as soon as the task is completed. This approach enables organizations to remove nearly all standing privileged accounts, dramatically reducing the attack surface area and removing the overhead of maintaining complex access control groups.
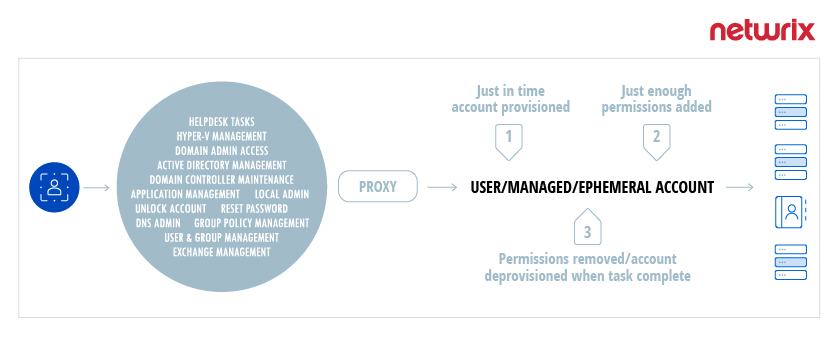
In addition, Netwrix Privilege Secure delivers:
- Approval workflows —An adaptive Zero Trust security architecture includes multi-tier approval capability to ensure all privileged access is authorized.
- Support for admin best practices —Administrators use accounts with elevated rights only for tasks that require them.
- Accountability —You can record and play back all administrative activity to spot improper actions, whether accidental or malicious.
- Flexibility —Permissions can be dynamically provisioned to an ephemeral account as detailed above, or to an existing user or service account.
- Cleanup of artifacts —Kerberos tickets are automatically purged after each session to mitigate the risk of pass-the-hash and Golden Ticket attacks.
- Real-time service account management — See updates and status changes as they happen, and get alerts on critical issues with the option roll back unwanted changes.



